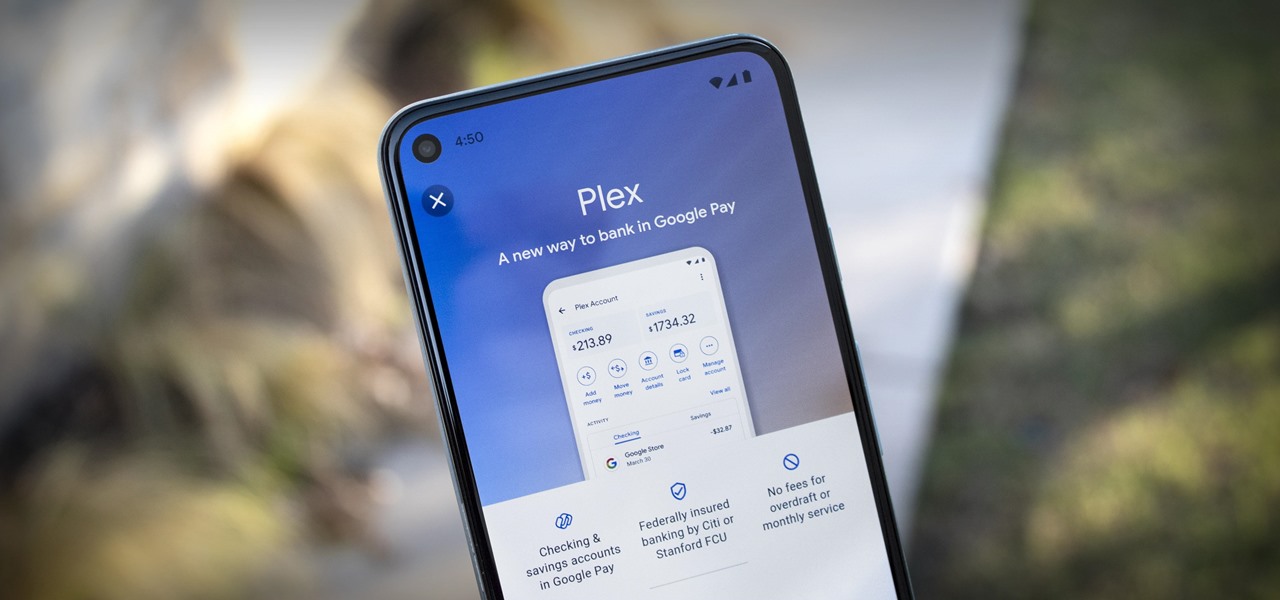
Not only has Google released a completely new Google Pay app for US users on both iPhone and Android, but the've also minted a new mobile banking service. Called Plex, it provides online bank accounts at one of 11 partner banks and credit unions, with no minimum balance requirements, overdraft charges, or monthly fees.

Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the organization being tested can fix any potential issues. In a professional penetration test, there are six phases you should know.

The landscape of the augmented reality space is broad, diverse, and constantly shifting, perhaps more so than any other vertical in technology. At the same time, major players are attempting to standardize various hardware designs and delivery methods, while still others are rushing to claim their piece of virtual property through AR clouds and application stores.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

If you're using a mobile device, it's a pretty safe bet that your apps are sending lots of information back and forth from their servers. To make sure there is no inappropriate data collection going on, it's worth setting up a web proxy to spy on this traffic, so you know exactly which apps are "phoning home" and when.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

As unappealing as it sounds, transplants with fecal material from healthy donors help treat tough Clostridium difficile gastrointestinal infections. Researchers credit the treatment's success to its ability to restore a healthy bacterial balance to the bowels, and new research has shown that the transplanted bacteria doesn't just do its job and leave. The good fecal bacteria and its benefits can persist for years.

On April 7, 2017, residents in Dallas, Texas, woke to the sound of emergency sirens blaring all over the city. No one could shut them off, and after repeated efforts to contain the situation, the city had to shut down the entire system. While the media reported a sophisticated computer hack was responsible, the truth was much less high-tech.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

In a new update, the iPhone 16 lineup is finally getting Visual Intelligence, a feature that lets you instantly gather information about anything around you just by snapping a picture.

Siri has long relied on basic sources like Google and Wikipedia for answers, but with iOS 18.2 and iPadOS 18.2, Apple is taking its virtual assistant to a new level by integrating ChatGPT. Now, you can use Siri to generate text and images with ChatGPT — and that's not all. ChatGPT is deeply integrated into Apple Intelligence and goes beyond just Siri.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

The beginning of autumn has delivered a number of new augmented reality developments, and we're on top of it.

Amazon really wants to make itself at home in your home. Like, everywhere in your home, from your doorstep to your kitchen, your kids' rooms, and everywhere in between.

The year leading into fall is turning out to be packed with a flurry of augmented reality activity. Most notably, TikTok is adding another major weapon to its AR arsenal. Also on deck are the powers of Hollywood horror in the form of an innovative approach to AR marketing that uses sounds.

The march to the mainstreaming of augmented reality can sometimes seem slow, but this week things picked up in earnest.

Over the past week, practically every major tech company working on augmented reality has held their quarterly earnings calls with investors, and each addressed or at least mentioned the role of AR during their prepared remarks. However, Facebook's earnings call had some of the spicier commentary on the technology.

It's already been a banner year for mergers and acquisitions in the augmented reality industry, with WaveOptics and Ubiquity6 among the notable companies acquired. Two of the more active M&A players, Snap and Epic Games, continued their respective buying sprees this week with major deals supporting their AR strategies.

A pair of properties from the soon-to-merge Warner Media and Discovery companies chose different platforms for their augmented reality marketing, with Warner film Space Jam: A New Legacy opting to go with Facebook and Discovery Channel publishing an AR experience through Snapchat.

Brands are increasingly adopting augmented reality to promote their products and services, and they have multiple paths for bringing AR experience to their audiences.

The close of the second quarter of 2021 brought about a flurry of merger and acquisition and financing activity in the augmented reality industry, headlined by the acquisition of Ubiquity6 and JigSpace's new multimillion-dollar funding round.

While Snap may eventually compete with Apple and Samsung in selling smartglasses to consumers, today it is helping them achieve their business objectives via augmented reality.

The makers of arguably the two most important mobile AR apps, Niantic and Snap, both had good news this week, with the former preparing to replicate its success with Pokémon GO for another franchise and the latter notching another popular augmented reality Lens for Snapchat.

Over the past few weeks, Google, Snap, and Facebook have all taken their turns to show off their new augmented reality technologies. This week, it was Apple's turn, with new AR features for iOS 15 along with new capabilities for developers.

It's (virtual) developer conference season, and this week was Facebook's turn with F8 Refresh. Like Google and Snap, Facebook had some new AR capabilities to show off.

We're still basking in the afterglow of the HUGE Snap Partner Summit last week, where Snap made Snapchat a much stronger augmented reality platform while also unveiling the AR smartglasses version of Spectacles. This week, we got a peek at how Spectacles AR started and got our hands on Lenses from Lego and Disney featured during the keynote.

Google and Snap held their annual conferences this week, and both companies managed to upstage their new AR software features with fantastic new AR hardware.

Sure, Microsoft has mostly marketed its HoloLens headsets towards enterprises and developers, but we learned this week that, like every other tech giant, the company is working on a consumer-grade AR wearable. Speaking of consumer smartglasses, Apple made another strategic investment this week that has implications for Apple's AR future.

Apple has a sterling reputation when it comes to managing its supply chain; it's where CEO Tim Cook proved his mettle to succeed Steve Jobs. Now, the company has made a strategic investment with a supplier that will be crucial to its future plans for AR wearables.

There's already some fierce competition between Snap and Facebook in the AR space, but it's about to heat up even more, with Snap snatching up a 3D mapping startup that could add some new AR capabilities to its arsenal.

As a company, Facebook is not shy about talking up its AR smartglasses plans. The latest missive comes from two executives in charge of developing AR software and hardware.

The Metaverse, or AR cloud, has been a sci-fi dream for decades, but only recently have companies begun to actually develop the technology to build it. With its latest funding round, Epic Games is suddenly a front-runner in this pursuit.

The race for the future of AR wearables gained steam this week with several pivotal developments. First, Apple, the subject of numerous reports and rumors regarding its purported AR headset, is reportedly eyeing an in-person unveiling of the device for later this year, rather than introduce it at its upcoming virtual Worldwide Developers Conference, which would usually be as good a time as any to make a big AR hardware announcement.

Microsoft believes its Mesh platform can help developers build immersive AR apps more easily. We spoke with a member of the Microsoft team to learn more about the platform.

Snapchat may trail Facebook and Instagram in terms of daily active users, but a new partnership with Samsung may get those innovative AR Lenses onto the mobile devices of a lot more users.

The augmented reality industry has grown steadily over the past four years, but now it is on a collision course with uber-popular non-fungible tokens technology, with Looking Glass and music artist Reggie Watts among the latest to strike while the iron is hot.

The year is still off to a roaring start, with augmented reality at the center of nearly everything, from enterprise solutions, to entertainment, to safety.

The Lens Studio creators have published more than 1.5 million AR effects to Snapchat. One of them is Audrey Spencer, who shared her story with us and provided her insights into Lens Studio as a storytelling device. Meanwhile, Snap has added new capabilities to the platform to stoke more creativity from its creators.