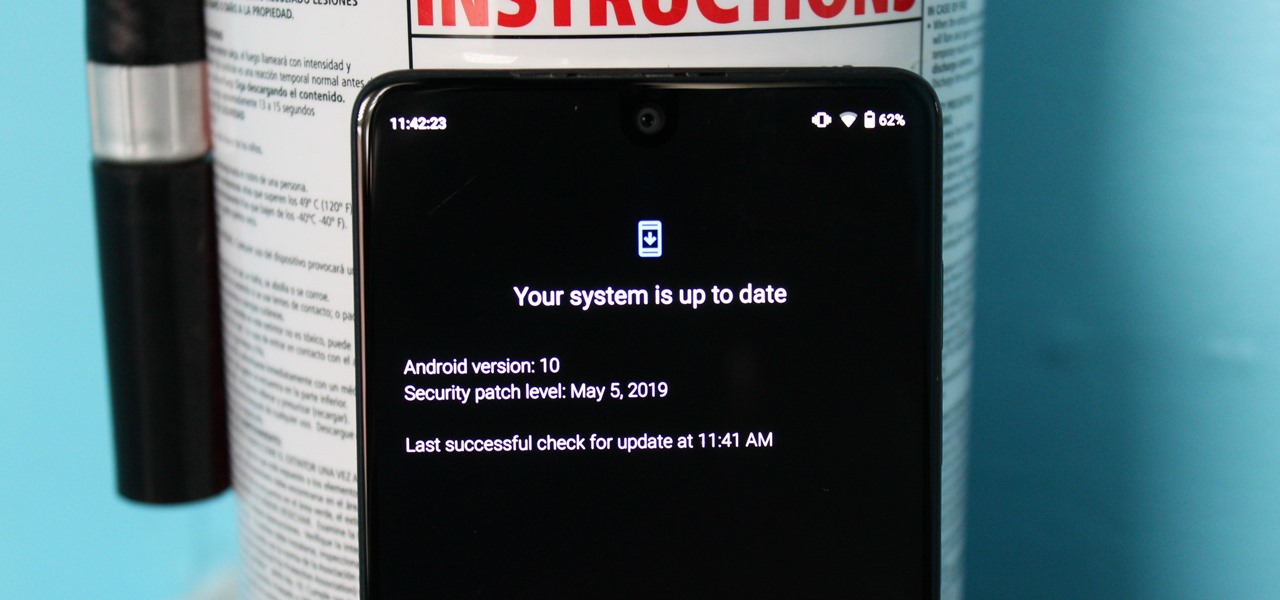
Like last year's beta release of Android Pie, Google has allowed the Android Q Developer Previews to support some non-Pixel devices. Announced at Google I/O 2019, there are 15 non-Pixel smartphones eligible for the Android 10 Beta, including 2017's Essential PH-1.

With $100 million in grant funding already available to developers via its MegaGrants program, Epic Games is sweetening the pot with some gear for Magic Leap developers.

Ten days after Magic Leap declared that it had selected the winners of its Independent Creators Program, the company has officially released an almost full list of grant recipients.

When flashing files through TWRP, ADB, or Fastboot, there's a slight chance for things to go wrong. Whether it's user error related or something else entirely, it's always good to have a backup plan. In most cases, you'll be dealing with a semi-brick or soft-brick, which can usually be solved by wiping the data of the device using TWRP. However, it can be more severe than that in some cases.

The march towards mainstream adoption of eSIM technology got a massive boost with the arrival of the iPhone XS, XS Max, and XR. We're now one step closer to ditching physical SIM cards altogether. If you're on the fence about this new technology, you may be surprised by the benefits it brings to the table.

Apple's new iPhone XR, XS, and XS Max are sure to be hits this year. Of course, that means plenty of hungry customers are looking to sign up for a model once preorders begin on Friday, Sept. 14, for the XS models, and Oct. 19 for the XR. Luckily, there are preemptive actions you can take right now to avoid waiting outside an Apple Store overnight or getting kicked out of the preorder queue online.

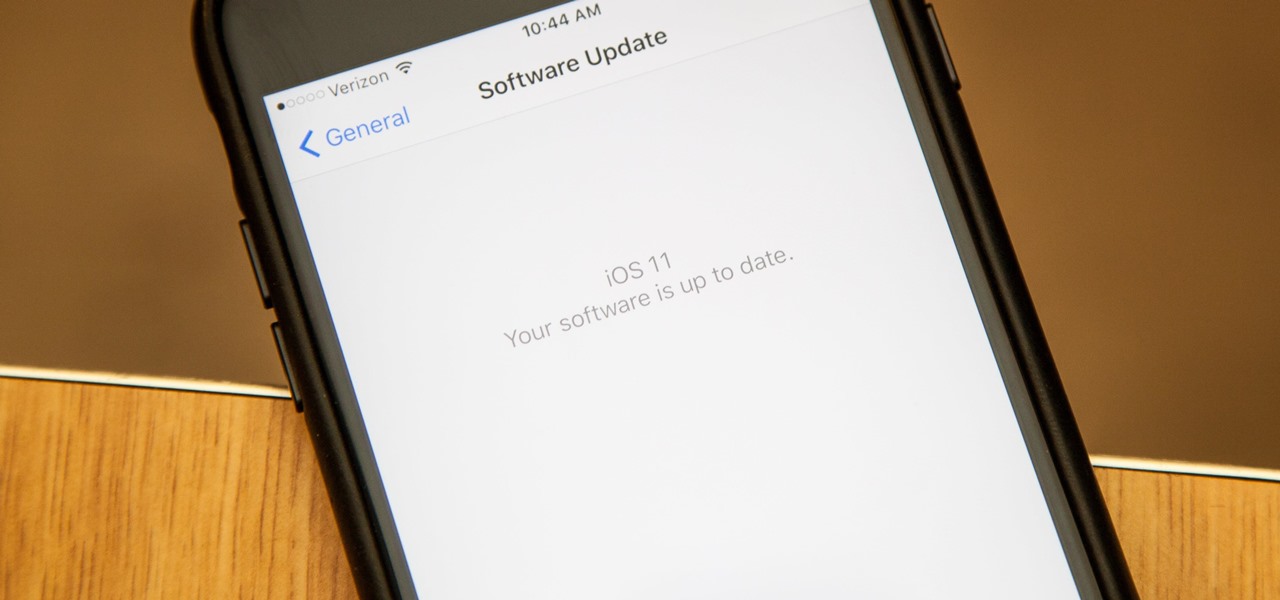
Hours after iOS 11.4.1 beta 4 was released on Monday, June 25, Apple's webpage for its public beta software programs was unavailable because of an "update." Sure enough, that meant the public beta for iOS 12 was being prepped to drop shortly thereafter, which is exactly what happened. In other words, you can now install iOS 12 on your iPhone without a developer account!

In January, ZTE announced they would be conducting an Oreo beta program for Axon 7 users to test Android 8.0 before the masses. Since then, no additional information was released — until today, when ZTE finally opened up the Oreo beta to US customers.

As demand for AR and VR developers continues to increase, particularly with the advent of Apple's ARKit platform, Unity has partnered with online learning company Udacity to help developers sharpen their skills for these jobs.

While the iMovie application for Mac has a few more bells and whistles, Apple's mobile version of its video-editing program is jam-packed full of features and more intuitive than its big brother. Still, before you dive right in to become a movie editor on your iPhone, it's good to know the basics first.

The status of Uber's driverless program remains a big unknown amid the company's recent woes, but a reported multibillion-dollar shot in the arm by Japanese tech giant Softbank could change all that.

Former Google employee Tristan Harris claims there's an easy way to combat phone addiction without installing any new software. By enabling grayscale on your phone, checking your apps and notifications will be less appealing and thus stop you from obsessively checking your phone.

Apple introduced their new mobile operating system for iPad, iPhone, and iPod touch at WWDC on June 5, 2017, and there are a lot of great new features to try out. While the official version of iOS 11 was released to the public on Sept. 19, you can still sign up either as a developer or with the iOS Beta Program to get new versions of iOS 11 before anyone else does.

For companies wary of the temperature, PTC just made it easier for them to dip their toes in the waters of augmented reality.

If you want to make some money from catching bugs and are sick of pentesting Facebook, Google, and Microsoft's products, Uber may be your new favorite playground.

I'm back! We're learning Java WhileLoops today.

Alright, this will be my first tutorial in C. Note that this guide is written for Linux.

How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implications which come along with it. I will show you using an example from the wargame IO Smash The Stack.

This video will show you an easy way to check the front disk brakes wear on your Honda TRX 250X.

How To Check The Rear Brakes on a Honda 250X Using Wear Indicator

Welcome back, reader! In this tutorial, we will be covering our first program! So let's get to it. We all know the unspoken tradition of the first program when learning a language and of course, here we will respect and complete it. Fire up your favorite text editor (be it vim, emacs, gedit, it's all the same to me, no h8) and try to keep up.

You need a good microphone on your computer in order to make audio recordings, voice chat, or use speech recognition. However, not every computer comes with a built-in mic, and not every built-in mic works great.

This tutorial will show you how to check the transmission fluid level on a Honda TRX 450R ATV

Hi there, nullbytes :) I've recently seen many questions regarding VMs with Kali, and personally I prefer using a Live Boot USB to get Kali without removing my system (and for many reasons).

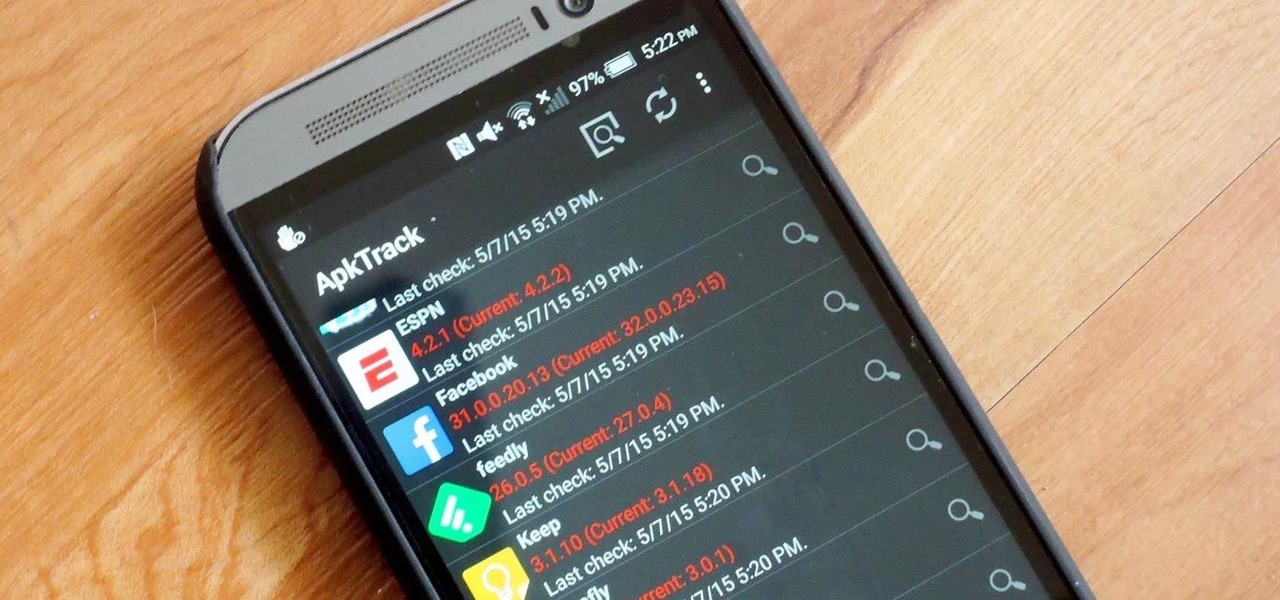
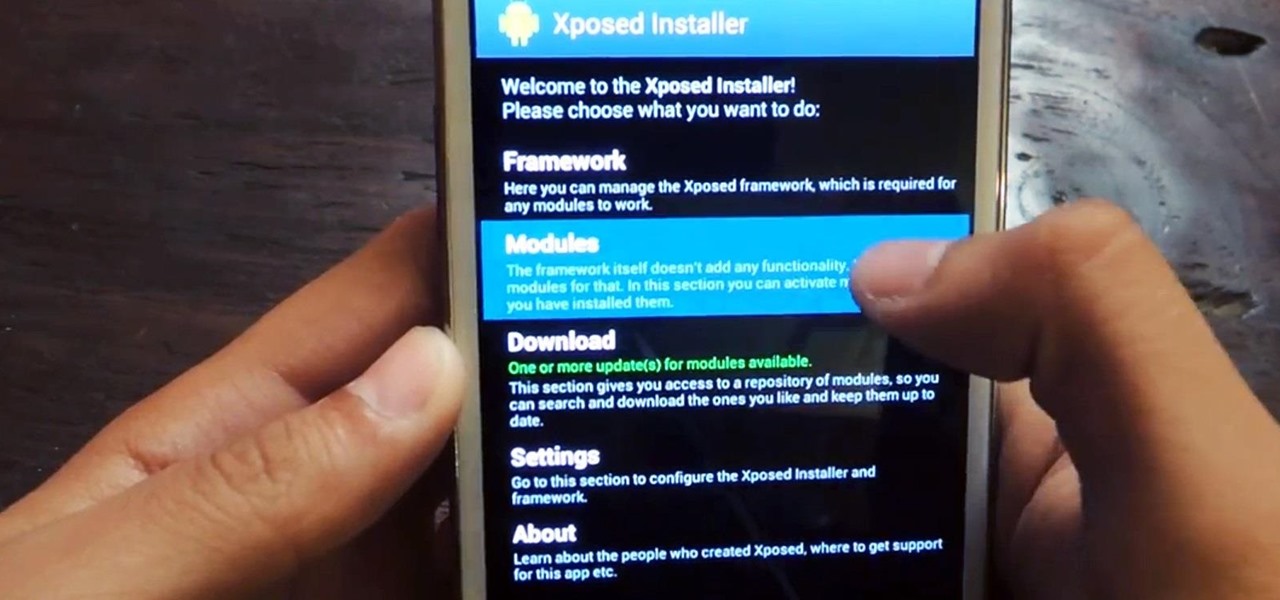
The Google Play Store may have fewer restrictions that its iOS counterpart, but that doesn't mean that all apps make the cut. Ad blockers and Xposed modules that bypass paywalls have never had a place on the Google Play Store, which makes tracking their app-updates a painful process.

If you're ever worried about your bObsweep's well being, you can always do a home check-up test to make sure all of bOb's parts are in working shape. As long as bOb has some charge, you can diagnose any potential issues by following the video guide for performing bObsweep Standard's check up test.

In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

This is finding some of your vulnerability using Lynis. This tool Lynis is used on Unix and Linux type operating systems (sorry windows). So lets get started

In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' computer systems in order to gain a strategic advantage and to spy.

We're living through the technological revolution, and while devices like the iPhone 6 or Galaxy S5 have made life easier and more entertaining, it's possible that sometimes our smartphone usage can become uncomfortably excessive. In your own experience, think about how anxious and off you feel when you leave your phone at home—Cell Phone Separation Anxiety or Phantom Phone Vibrations shouldn't be a real thing that we deal with.

Unless you're waiting in line for your iPhone 6 or iPhone 6 Plus, it's a sure bet that you'll be sitting by at home for your new device to get delivered today.

T-Mobile continues to make waves in the U.S. wireless market behind CEO John Legere's UnCarrier program. At the latest installment in a series of industry-challenging announcements, Uncarrier 5.0 unveiled Test Drive. The new program is set to allow would-be customers to try out the "latest generation" iPhone for seven days on T-Mobile's network without any financial commitments.

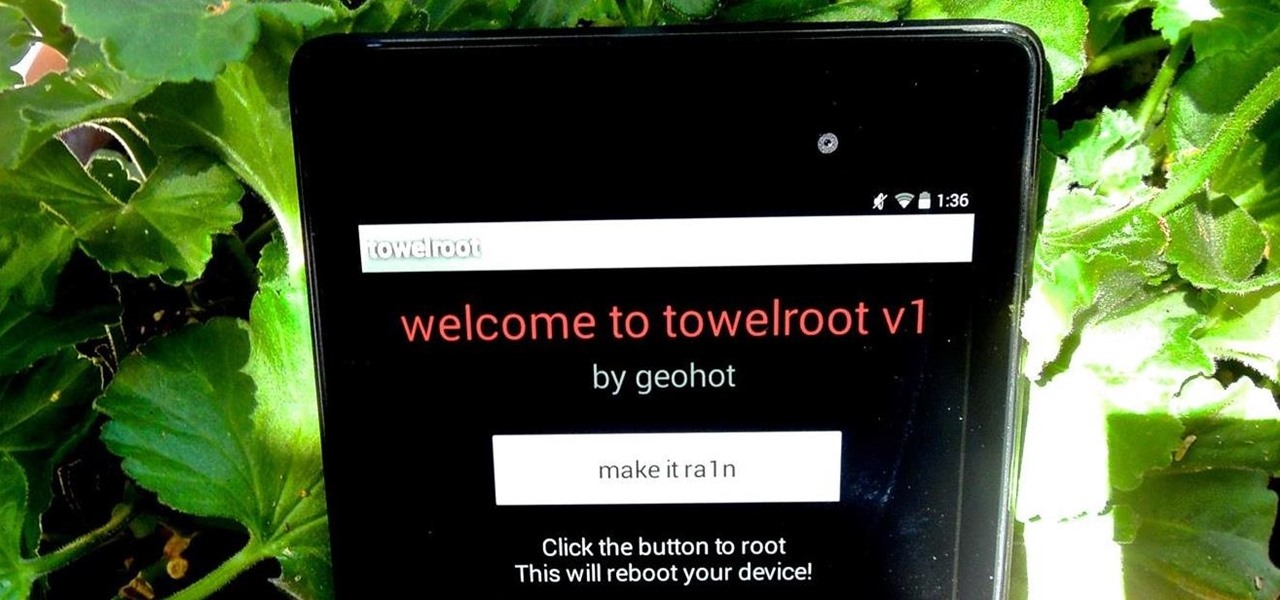
Rooting your Nexus 7 tablet is now easier than ever. Previous rooting methods required connecting your tablet to a computer and using any one of a number of programs and/or ADB commands. Now, it's as easy as downloading an app on your phone and tapping one button.

This video will show you how to use the site glass that Honda has on the TRX 450R for a quick check of your engine oil level.

The in-fighting between the major US carriers just got a little more interesting. In July of last year, T-Mobile introduced their JUMP! plan, letting customers upgrade their devices after just six months, up to twice a year. Buy a device, split up the price into monthly payments, and pay an additional $10/month to enroll in the service.

Like insurance, it's always better to have a computer mouse and not need it than to need it and not have it. Honestly, I don't want to carry around a clunky mouse with my laptop, so I don't. I do something else, something more convenient. I use my Nexus 7. If you want to give it a try, I'll show you how it's done right now. All you need to is a Wi-Fi network and a specific Android app to control your computer with your Android tablet.

Android's deeply customizable platform has long been the attraction for those of us looking to make our smartphones more unique, but that doesn't mean that it's always easy. Flashing mods and installing custom ROMs can be difficult at times, as well as dangerous.

Communication is the key to any healthy relationship, and when I say any, I mean human and non-human. Previously, one of the biggest culprits for not understanding what you meant was Siri, but now it looks like it has some competition with the new Kinect system, which can control practically everything on your Xbox One—if it can understand you.

If you're new to Android phones, one of the first things you've probably noticed is how notification alerts differs from Apple devices, especially in regards to getting a text message.

How to check for a worn or loose carrier bearing on your snowblower.