An iPhone's display can get seriously bright, whether LCD or OLED. When you're in bed at night or in a dark room where you don't want to disturb others visually, the brightness is even more noticeable. But there are a few built-in ways in iOS to reduce brightness below the default levels for less eye strain and other reasons.
When it comes to customizing Android, there's no better way to make it your own than by installing a custom ROM. You gain new features that were not accessible on the stock firmware that came with the phone, and you get complete control over how your system looks and feels. But there's definitely a learning curve.

The North remembers...that smartglasses are the future! Game of Thrones jokes aside, the smartglasses startup opened its doors, and we visited its Brooklyn store to get our hands the consumer-focused Focals smartglasses.

Samsung isn't known for its timely rollout of major Android updates, and Android 9.0 Pie won't be an exception. If we go by their Oreo update timeline, we can expect Android Pie to officially touch down for the Galaxy S9 and S9+ sometime around November, with the final version rolling out the around the first quarter of 2019. But a leaked version of the beta has already hit the internet.

Although the Galaxy Note 9 is an amazing phone, many members of the Android community won't even look at it. This isn't just because of the Samsung Experience skin, but the large amount of bloatware that comes with this device. However, with a little work, you can remove all of it.

Ever since Google CEO Sundar Pichai took the helms of the world's most valuable brand, he has made it his mission to bring smartphones to lower-income communities. Born in India, Mr. Pichai has created several programs to address the needs of the Indian market, particularly the lower income families.

Super Bowl LII will bring millions of football and non-football fans together to watch the big game on the big screen. But without a cable subscription, this process can be a little daunting. Luckily, the Google Play Store and the iOS App Store offer a few ways to accomplish this — no cable contract required.

The OnePlus 5T was just released, and it's packing several new useful features. While many OnePlus 5 buyers are feeling frustrated with the quick release cycle, lots of fans are still clamoring to buy the new device. Aside from the larger screen, most of the buzz around the 5T has centered around the new face unlock method. Thanks to a clever hack, you can now get this feature on almost any phone!

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

As more companies begin adopting augmented reality in the workplace, providers like Vuzix reap the benefits.

Bed bugs are brown and creepy. Could you spot one in your hotel room? A new study reveals most people are freaked out by bed bugs, but only about 35% could identify one.

Buying a smartphone used is an excellent way to save money, but those savings come with a risk that your seller isn't as forthcoming as they claim. You don't want to end up buying a stolen smartphone because it might not work correctly ... and, you know, it's wrong. Luckily, there's an easy way to check if the phone you're about to buy is legit.

Uber's driverless car program lead has quit after just one year working for the ride-hailing company.

We've all been there... admit it. You sent a couple messages, but your friend had the "Read Receipts" option turned off in WhatsApp, so after a few minutes, you start wondering if they're away from their phone right now or just flat-out ignoring you.

Some of the best Android apps are not hosted on the Google Play Store, and that means you have to sideload them if you want to get their awesome functionality. But without the Play Store, these APKs are never automatically updated, so your only choice has been to scour the internet for a newer version when you need a bugfix.

Android 7.0 Nougat has finally arrived—well, technically, it's in the process of arriving on Nexus devices across the globe. Google uses a staged rollout system to prevent excessive server load when issuing Android updates, which means even though Nougat has made its official debut already, you might not get that "Update available" notification for another few weeks.

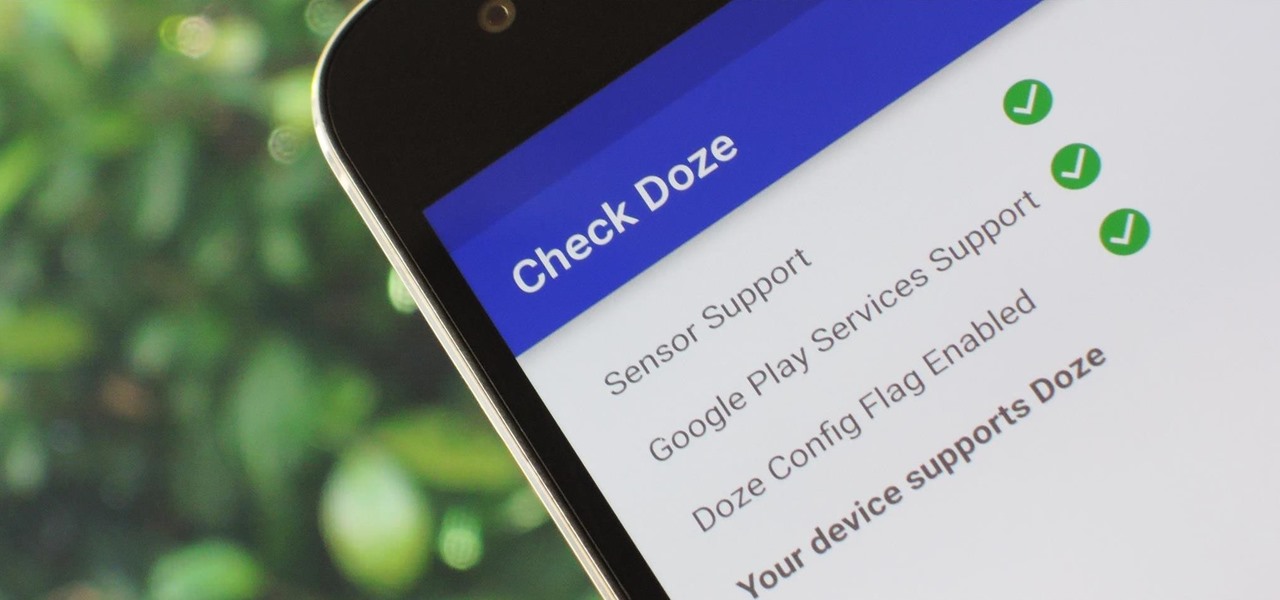
Out of all the new functionality introduced alongside Android 6.0 Marshmallow, a battery-saving feature called Doze Mode has been the biggest hit. Essentially, Doze waits until your device is laying flat and still, at which point it triggers an aggressive battery-saving mode that drastically increases standby time on your device.

Greetings comrades! Great leader has ordered that we gain intel on a website owned by the opposition. For all general purposes we will be scanning nmap.org because they really don't care if Big Brother decides to perform a whois on their IP. We will be using Dmitry for the scanning.
Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain.

Welcome back everyone. I apologize for the lack of training articles, but I've been rater busy lately. I've recently picked up a second job and my college courses are now back in session, so I'm a bit strapped for time.

Apple has finally addressed and issued a fix for Error 53, a "safety" mechanism that would prevent your iPhone from booting if you had certain repairs done outside of Apple's official channels.

Hello there, reader! If you've clicked on this How-to then it means you are interested in learning some C programming or just generally curious about what this page has to offer. And so I welcome you warmly to the first of many C tutorials!

Windows 10 has so many new features that we couldn't even cover them all with one article. From keyboard shortcuts to revamped search functions and all-new window gestures, Microsoft definitely piled on the fresh functionality in the latest version of their operating system.

Unless you've been living under a rock or ignoring recent news headlines, Ashley Madison, the dating site for married people (or individuals in a committed relationship) has recently been hacked. Millions of their users are shitting their pants, and for good reason, as all of those accounts have just been leaked.

Programming is an essential thing in hacking/pentesting, and at times, I do not feel that it is being addressed enough here, at Null-byte. I understand that this is a forum dedicated for hacking, but I'll address some of the stuff I feel is muy importante about programming. I am not a professional programmer, but I do have experience and I do want to share some of the stuff professionals have taught me.

When security firm Zimperium discovered Android's biggest security risk in years, it sent shock waves through the ecosystem. As a result, Google, LG, and even Samsung decided to change the way they issue updates to their devices, by pledging to release monthly security patches to plug up loopholes exactly like this one. Yeah, it's that big of a deal.

So, we all probably know that when you run a trojan made by Metasploit, nothing will appear to happen. This is a sign for me to immediately check my Task Manager, but for an unsuspecting victim, it will just seem like a broken file. It is likely that they will delete this "broken file" once they see that it "doesn't work." In order to prevent this, we need to disguise the trojan.

Hi everyone! In the previous part of this series, I introduced one way to hijack a program's execution flaw, though I only showed you how to crash the program and left you with a little mystery to solve. Today we are giving the solution of that and then introducing shellcode usage and remote command execution.

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!

Welcome to the sequel to the latest post on writing 64 bit shellcode! This tutorial will assume that you are aware of everything mentioned in the last one, as I will try to make this tutorial void of formalities and straight to the point! If you have not read the last one, I suggest doing so unless you are familiar with basic assembly programming and system calls. This is by no means rocket science, so therefore I will simply repeat my TL;DR from last time before we get started, so that the a...

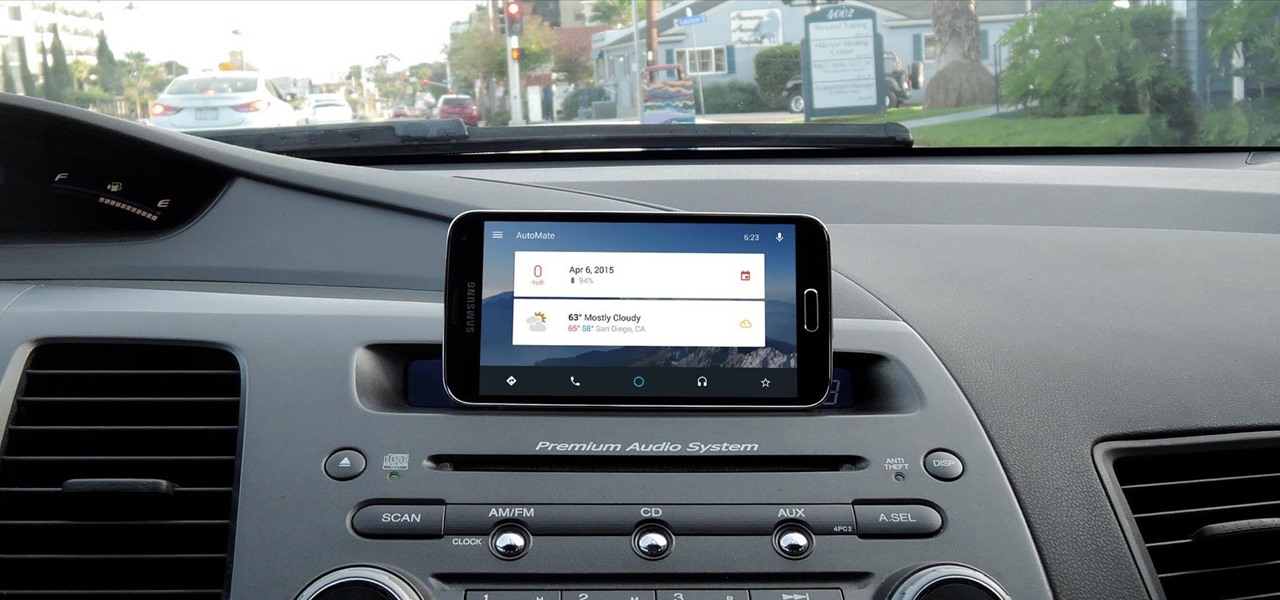
Auto manufacturers are slowly starting to debut models with Google's new Android Auto software baked into the dashboard console. Starting with the 2016 model year, we should see vehicles from Honda, Ford, Chevrolet, and many others sporting the new software.

When it comes to getting your computer and smartphone to work well together, there's no service more robust and capable than AirDroid. For years, it's been the go-to tool for users looking to transfer files between their devices or access contact lists and call logs from their computer.

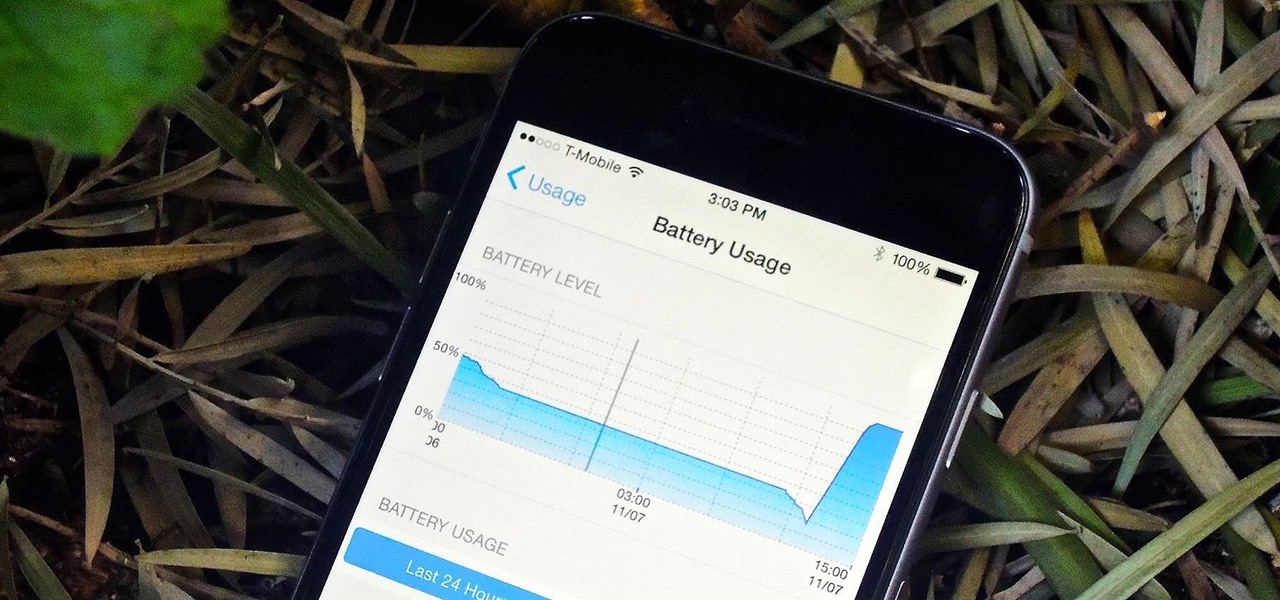
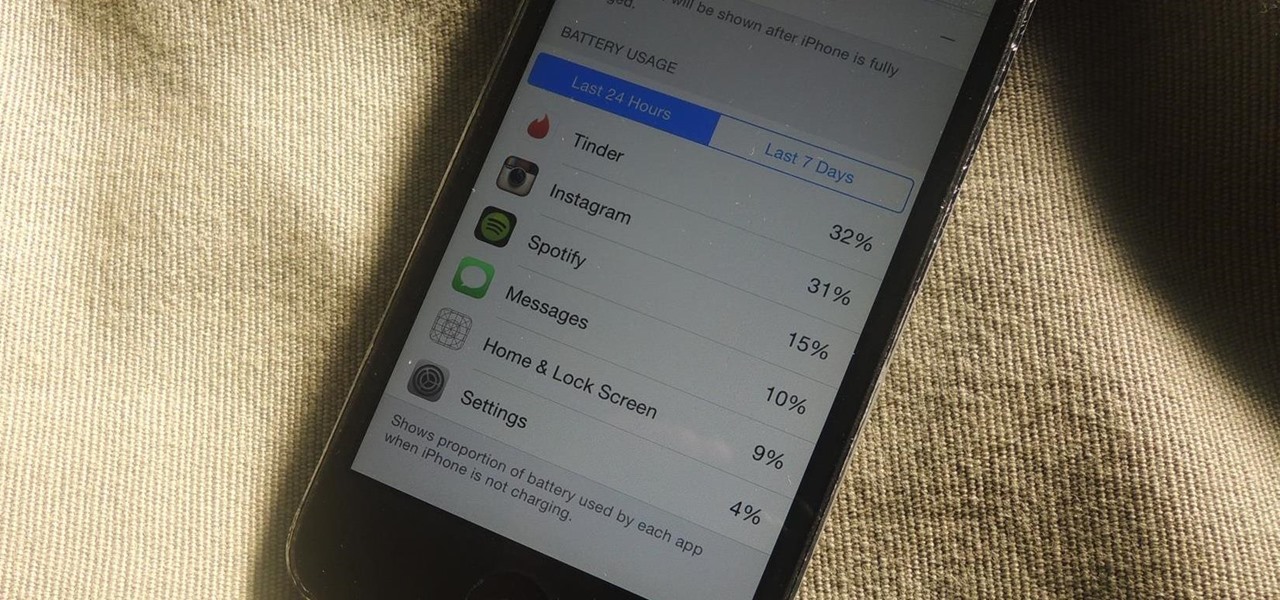
One of my favorite new additions to iOS is the ability to view battery usage stats on a per-app basis, which is helpful in knowing exactly which apps are taking up all of my iPhone's battery life. If you jailbreak iOS 8 on your device, you can take Apple's stock battery stats feature even further to give you details on how those apps are actually using the battery.

Are you one of those people that waits until the last minute to come up with a costume for Halloween? Unless you're a makeup artist, have a ton of money, or are ultra-crafty, coming up with a good Halloween costume is always a low-priority task. That is, until it's Halloween and you're having a panic attack.

The problem with striving to be on the bleeding edge of what's new for your smartphone, or really anything else in life, is having to constantly check websites and forums for new content. And with lots of that browsing happening on our phones, the aimless page loading and refreshing is not just annoying when there isn't new content, but can lead to wasted data usage, not to mention time.

If rapid battery drain is something that's been an issue for you in the past, Apple is now making it easier to monitor what might be the problem. In the new iOS 8, you can now check battery usage for every app on your device.

As you may have already heard, the worst bug in OpenSSL history went public yesterday, dubbed Heartbleed. While we can go deeper into the technical details of it later, the short version is that OpenSSL, the library used to encrypt much of the web running on Linux and Apache has been vulnerable for up to two years.

Just because you have a Mac doesn't mean you can't root your Nexus 7 tablet. In fact, rooting Android 4.4 KitKat on both the 2013 and original 2012 N7 models is easy, if not easier than rooting it using a Windows PC.

This is about how to make a rabbit become less wary of you and more trustful with you also. I myself have a Dutch that was released by its previous owner, then I rescued it. She never wants to be took out of her cage, but now she doesn't mind as long as I'm gentle and nice.