Want free Xbox 360 games? Well, join the club. But you can actually do something about it and download and burn Xbox 360 games with a few programs and a little knowhow. If you want the keys to the Xbox kingdom, just watch this video tutorial that shows you how to burn Xbox 360 games perfectly every time. This only works for the Windows Vista OS and works more smoothly if you have a great DVD burner.
Ever wanted to become a programmer? This Delphi Training Series: Programming 101 is a sequence of training videos designed to teach the complete beginner how to become a programmer using Delphi.

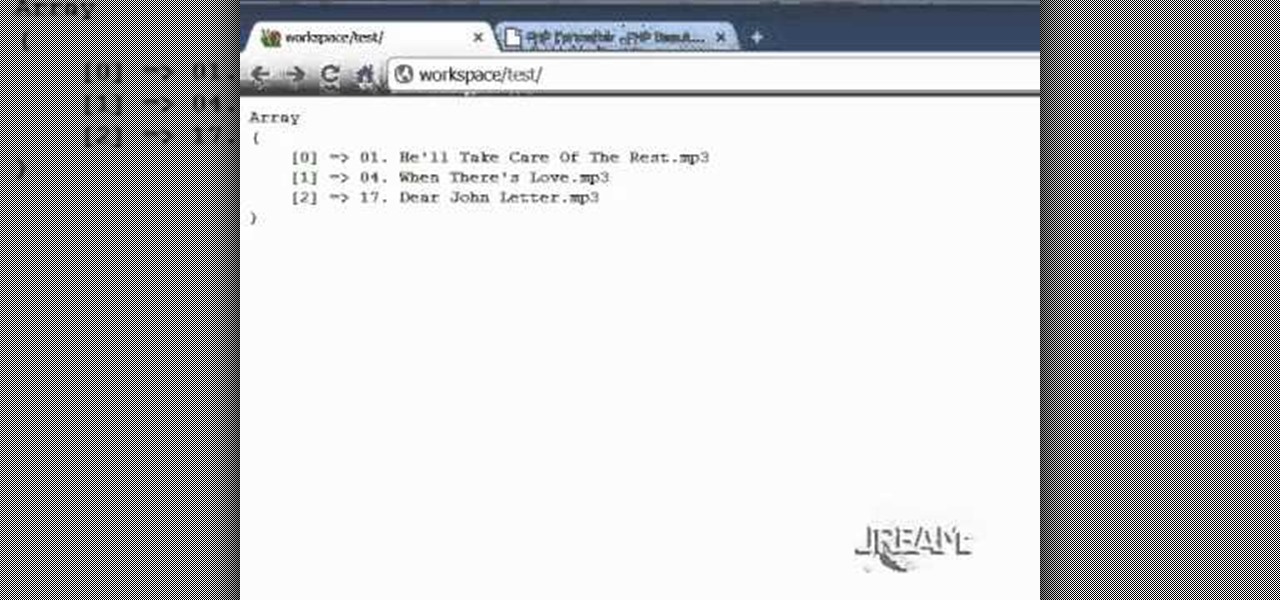
A PHP Tutorial about the basics of creating mathematical function.

Download .net framework and install it if you do not already have it. Download DevKitPro from here and install as instructed.
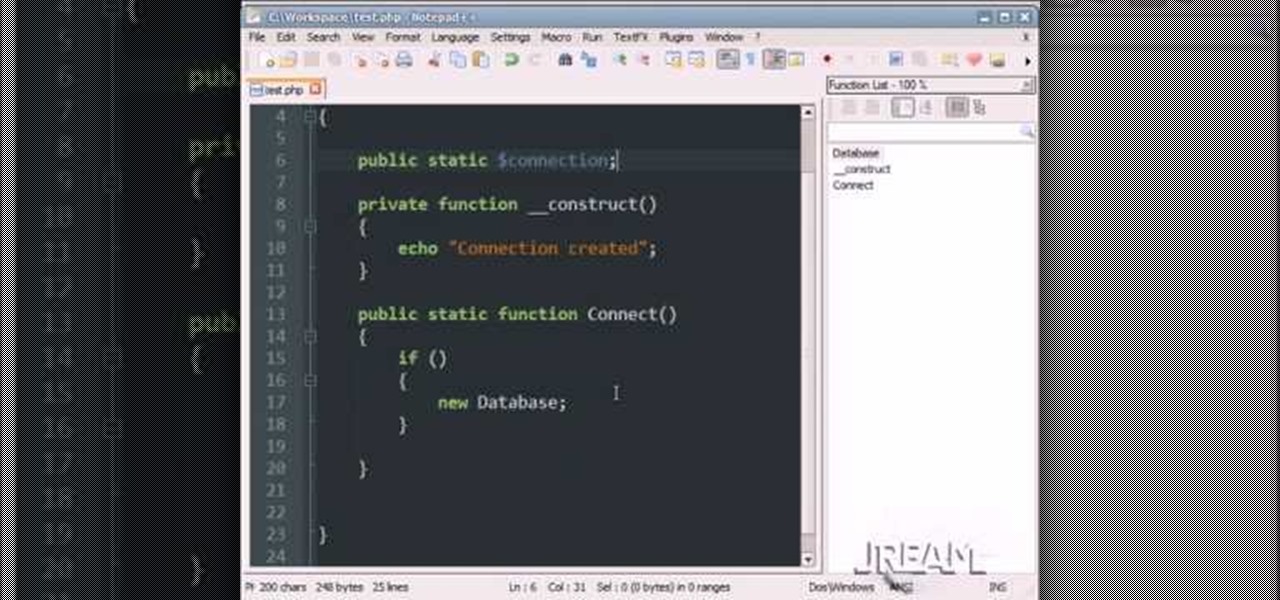
This PHP newbie video with teach you what a Singleton Pattern is and how to use it in your PHP programming. PHP OOP Singleton is great for a database connection when you only want one consistent connection in your application. So, to prevent wasting space accidentally by calling it twice in different areas, this is good way to protect it. Singleton is very popular and used often in Database Connections.
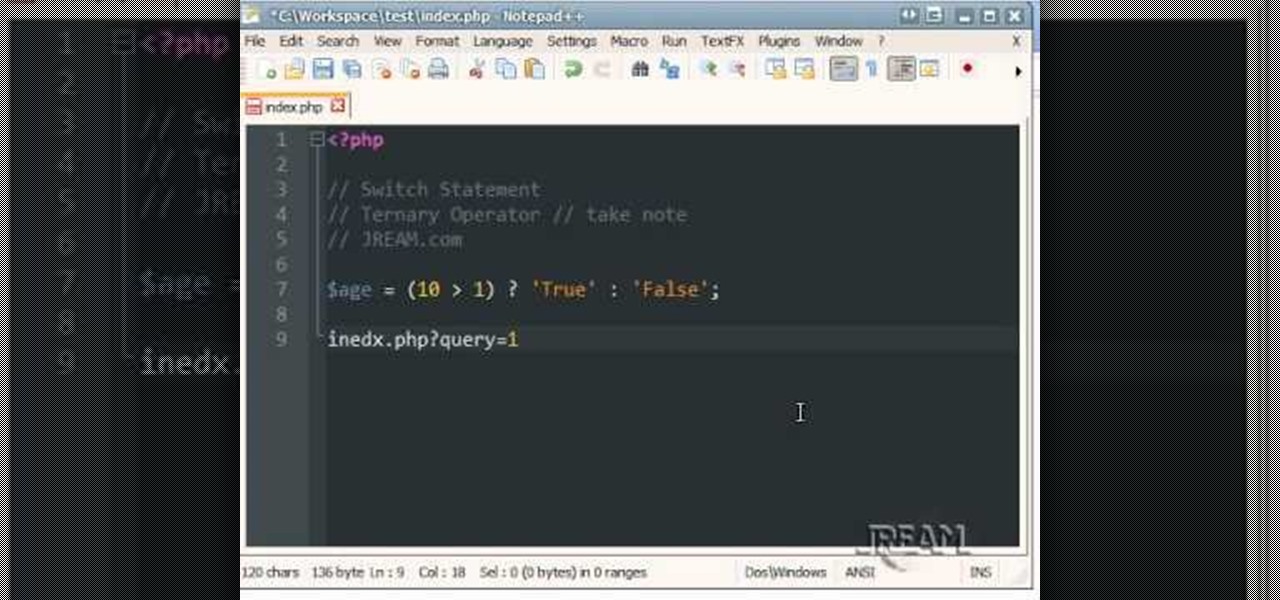
This quick little video teaches you about the switch statement and ternary operator for use with your PHP programming. It's quick so you may want to take notes to ensure it's all sticking in your gray matter hard drive. Go!

If you're programming with PHP and you generate a list of music files, you'll want to find a way to play them. This video shows how to use the Yahoo Media Player to play the list of mp3s you've created, with your PHP coding.

In this video, you'll use Scope and create a simple calculator while learning a little about private, public and protected properties in OOP programming. If you're looking to bone up your PHP coding skills you'll want to check this video out.

View all your installed applications on your Mac quickly and easily using the HimmelBar. This free program adds a new icon to your menu bar which provides instant access to all those programs with a simple click of a button.

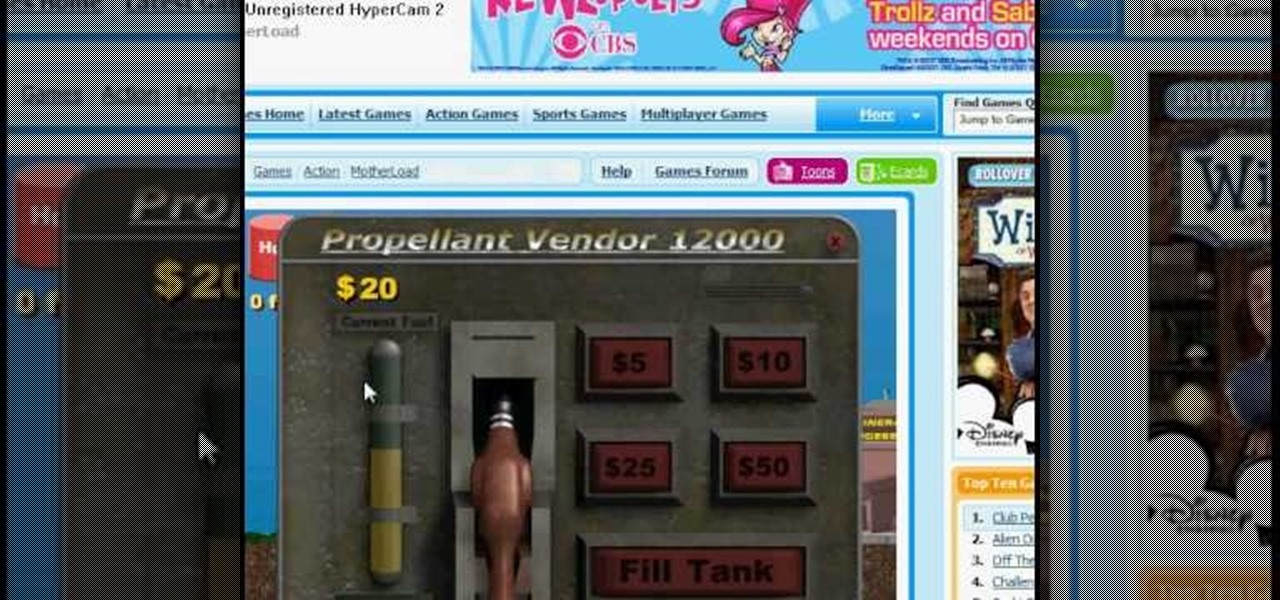
Cheat Engine is a program you can use to cheat at many different games, especially online, browser based or Facebook games. This tutorial shows you how to use Cheat Engine to cheat at the onilne game Mother Lode, but you can use it for many games.

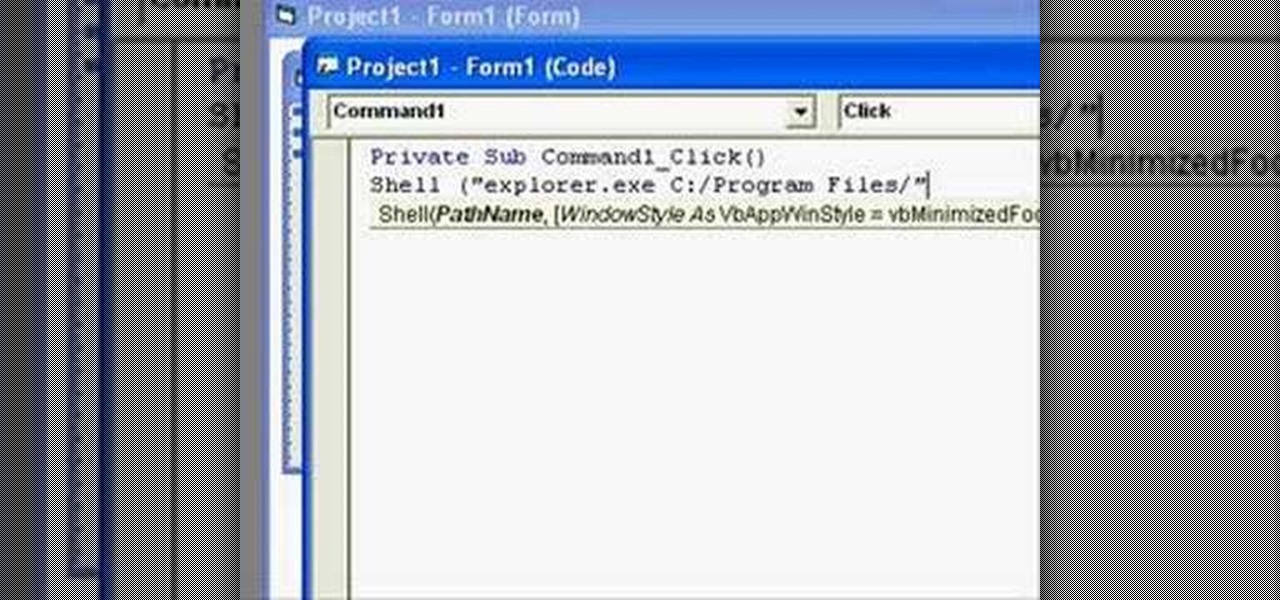
In this clip, you'll learn how to use the shell function to use the shell function to open folders. Whether you're new to Microsoft's popular event-driven program language & IDE or a seasoned developer merely looking to improve your chops, you're sure to find benefit in this free Visual Basic programming lesson. For more information, including a complete demonstration and detailed, step-by-step instructions, take a look.

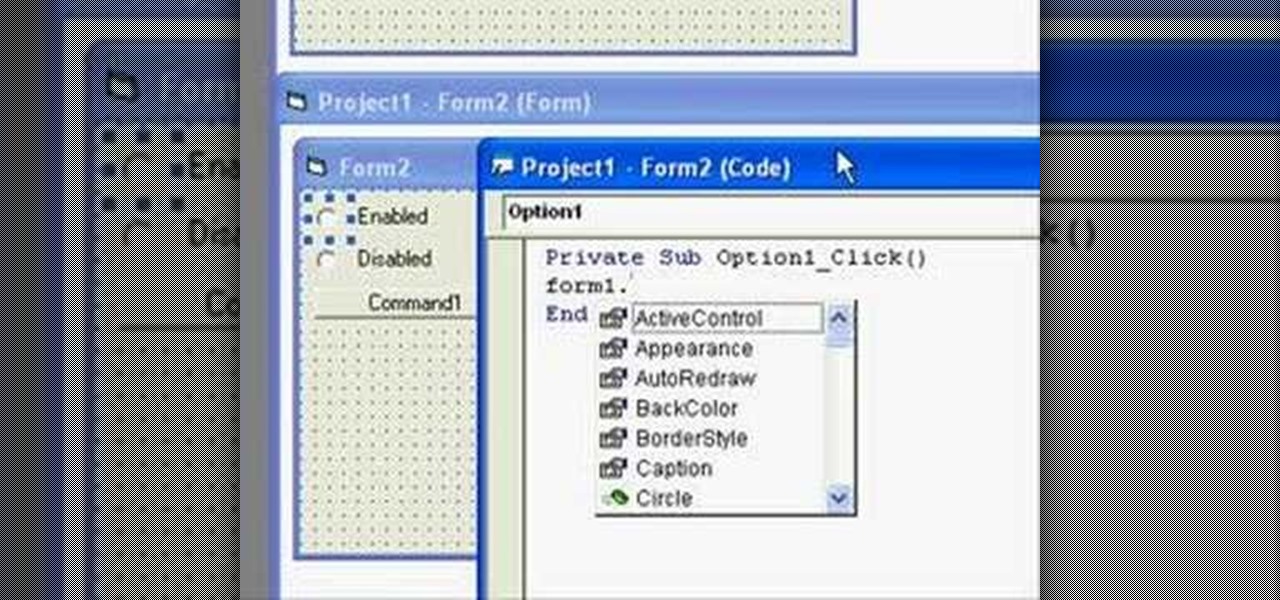
In this clip, you'll learn about basic form control within Visual Basic 6. Whether you're new to Microsoft's popular event-driven program language & IDE or a seasoned developer merely looking to improve your chops, you're sure to find benefit in this free Visual Basic programming lesson. For more information, including a complete demonstration and detailed, step-by-step instructions, take a look.

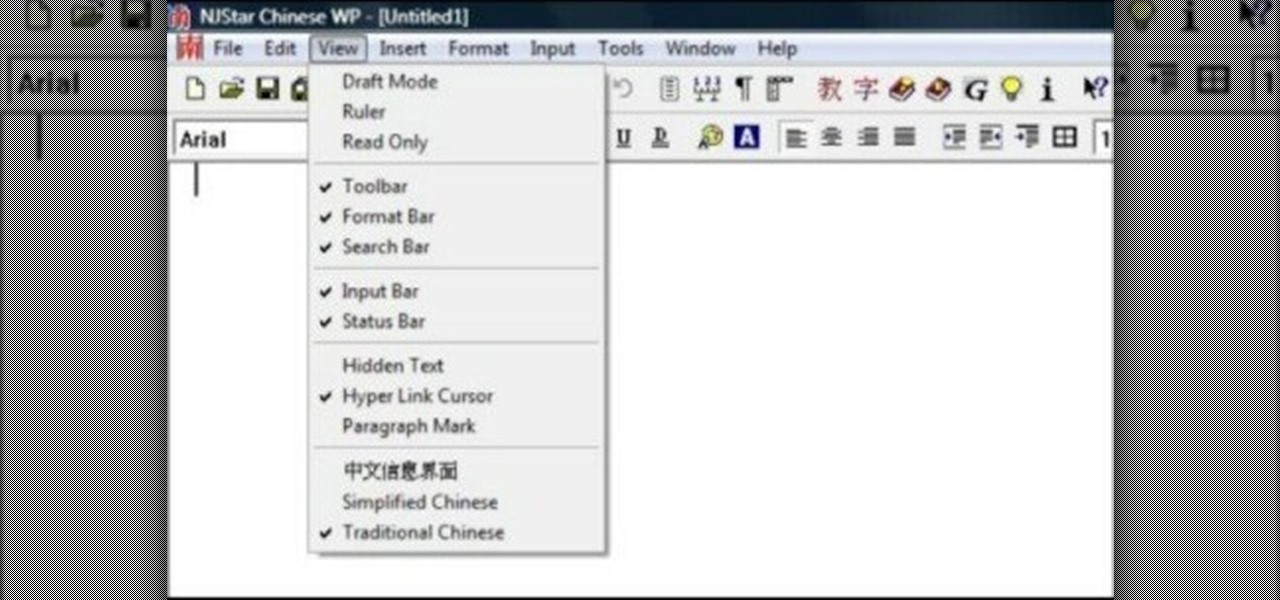
NJStar is a program which you may purchase online, and which will allow you to translate individual Chinese characters. This tutorial shows you how to use the software, and explains the limitations of the progam (it cannot translate whole paragraphs, for instance).

Before you can work in Adobe Flash CS3, you'll need to know how to work with it. Learn how with this clip. Whether you're new to Adobe's popular Flash-development platform or a seasoned web developer looking to better acquaint yourself with Flash CS3, you're sure to benefit from this free software tutorial. For more information, including detailed, step-by-step instructions on how to use the program's draw tools, watch this video guide.

As many of you stop-motion animation practitioners out there have probably realized, Legos are a great material for that medium, allowing for great diversity while being relatively easy to work with. Can they fly though? This video features a British boy explaining how to use a free computer program called Bafran to make Lego characters appear to be flying in an animated video.

Big business is on the web these days and you don't have to build a shopping website or blog to get involved.

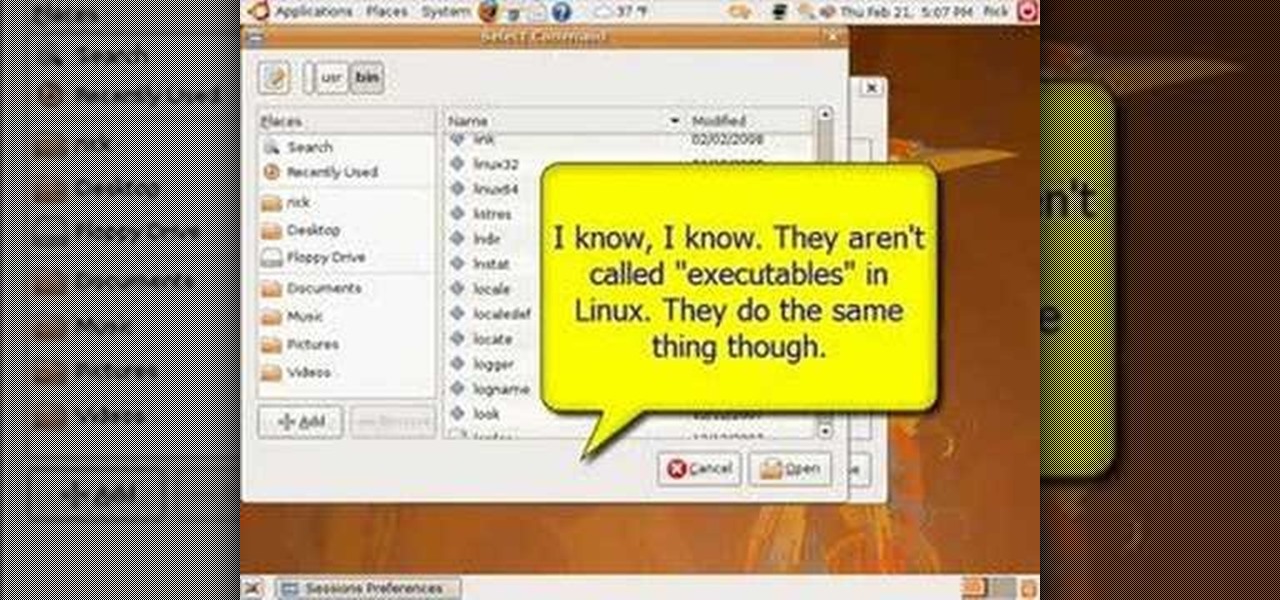
New to the Ubuntu Linux distribution (or one of its derivatives) and looking for a way to start programs automatically when you boot up your machine? Take heart: This video tutorial will show you how to accomplish just that using your system preferences. Take a look!

New to OpenSceneGraph and not quite sure where to begin? If so, you're in luck. This tutorial will walk you, step-by-step, through the creation of your very first OpenSceneGraph program for the Mac OS X platform.

Don't let a bunch of programs run in the background and hog your Palm Treo's resources! Watch this electronics tutorial video to learn how to close them out. This how-to video makes maximizing your Palm Treo 750's power easy.

Watch this software tutorial video to learn how to quickly unzip archived files using the program WinZip. WinZip makes unzipping and unarchiving archived files quick and easy, and this how-to video provides helpful tips on how to use the program.

This computer programming tutorial screencast teaches programming tips and tricks on Ruby on Rails. This Ruby on Rails how to video covers basic string manipulation.

To avoid sports-related injuries, it is essential to warm-up before a race or a game or even before a training or practice session. Watch this video tutorial to learn how to warm up before running by doing side steps from Gilbert's Gazelle training program. This how-to video is a must watch for all track and field athletes.

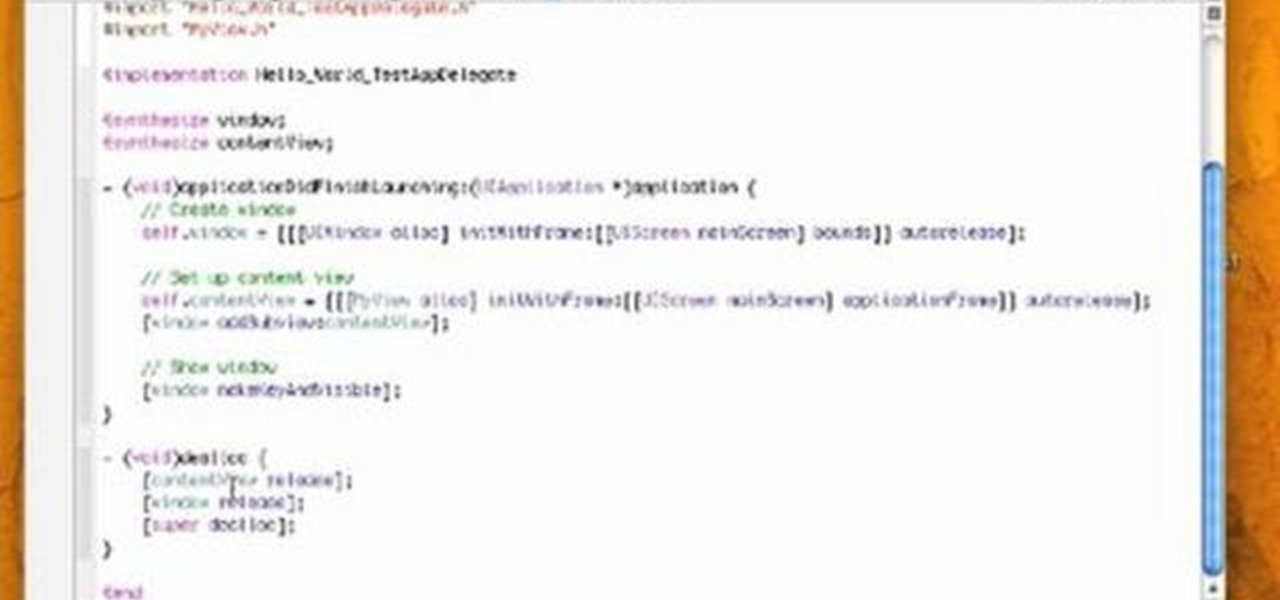
Check out this video screencast tutorial to help beginner iPhone programmers get started. This tutorial shows how to draw "Hello World!" text on the screen of the iPhone in Mac OSX with the help of Objective C (ObjC) in Xcode for Cocoa programming on your Mac OS.

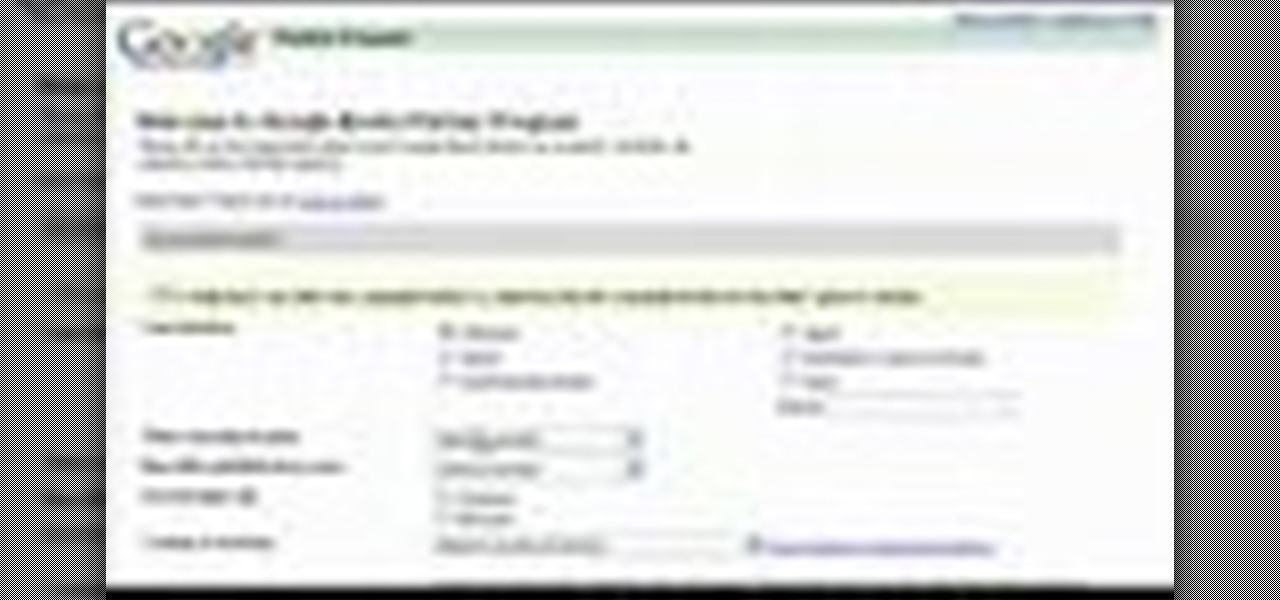
Learn how to apply for a Google Books Partner Program account, which allows you to submit your content for display on Google Book Search.

A VB.Net 2008 tutorial on how to make a program that can count cards in a blackjack game.

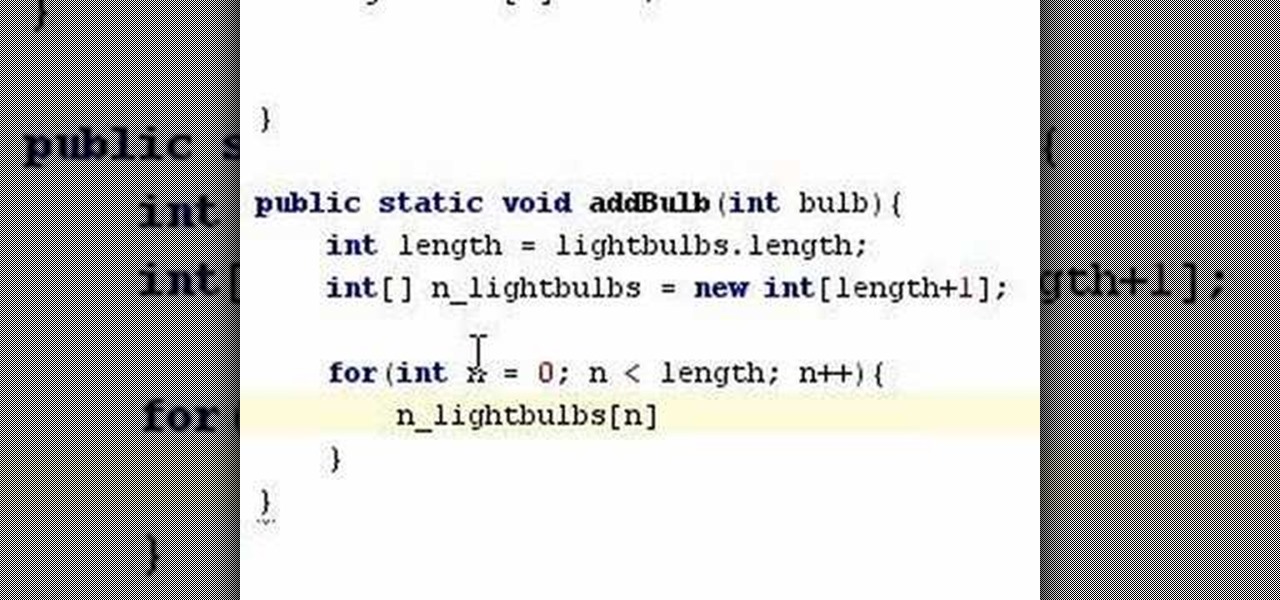
A tutorial on how to unroll and append elements to an array when programming in Java.

Learn to program If & Switch Statements in Java. This tutorial uses Java 1.6 with NetBeans 5.5.1 beta

Delphi controls have an owner and parent property, find out what the difference is and how to use them when programming in Delphi.

You can connect your Nintendo Wii Wiimote to your PC using GlovePie input emulation software and a bluetooth connection. Learn how to program your PC to detect motion from dual input the Wiimote using GlovePie. You'll be able to connect two Wiimotes to your PC.

In this tutorial you will see how to use Jimmy's speed math program that he wrote in Flash. A download to the program is included. This is a GREAT way to help your kids or students (or maybe adults?) get better at math.

Whether you're looking to add a substantial coding foundation to your hacking skill set or want to get a job in programming and development, knowing one or two programming languages just isn't going to cut it.

Augmented reality gaming pioneer and Pokémon GO mastermind Niantic is putting the pieces on the gameboard to prepare developers and gamers for the launch of its AR cloud platform.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

Google just released Android 7.0 Nougat, and as usual, they're doing a staged rollout. This means that most users won't actually get the update on their Nexus devices for a few weeks—that is, unless they take matters into their own hands.

Out of nowhere, Google released a preview build of the upcoming Android N release back in March—a full two months early. As if that weren't enough excitement for one day, they topped themselves by following up that announcement with the debut of a new "Android Beta" program that allows users with eligible devices receive preview builds as a regular OTA update, meaning no losing data or manual installation.

Hello, this is my first post on Null-Byte. This is made for those who have an interest in writing into another processes memory. Why would you want to do this? Who knows, personally I just wanted to mess around with games on my computer(have unlimited health).

Welcome my aspiring hackers and programmers! Today i will introduce you to a programming language that as a hacker you should have in your set of hacking/programming skills (except if you're only interested in web hacking/programming...then you should go learn some html or PHP instead of C#).

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.