
How To: Photoshop textures
Photoshop is a great computer software program designed to help people manipulate images and text. Learn a few easy steps for creating cloth, rock and wood textures from a Photoshop expert in this free video series.


Photoshop is a great computer software program designed to help people manipulate images and text. Learn a few easy steps for creating cloth, rock and wood textures from a Photoshop expert in this free video series.

Photoshop is a great computer software program designed to help people manipulate images and text. Learn a few easy steps about Photoshop image manipulation from a Photoshop expert in this free video series.

Photoshop is a great computer software program designed to help people manipulate images and text. Learn about creating glitter graphics in from a Photoshop expert in this free video series.

Photoshop is a great computer software program designed to help people manipulate images and text. Learn a few easy steps for creating sand text from a Photoshop expert in this free video series.

Nia is an exercise program that focuses on aerobic workout, and it incorporates the mind, body, and soul into creative healing moves. Learn how to do lateral step variations in Nia with this free exercise video series from a black belt instructor.

Photoshop is a great computer software program designed to help people manipulate images and text. Learn a few easy steps for creating "Matrix" text from a Photoshop expert in this free video series.

Add style to your Photoshop file with the program's advanced filters and tools. Learn how to use the creative text tools of Photoshop in this Photoshop tutorial from a professional graphic designer.

Watch this automotive video tutorial to see how to scan your automobile for diagnostic trouble codes.

This pilates how-to video illustrates the Lateral Flexion exercise of the Side Leg Series. It is obviously a great exercise for lateral flexion and balance.

Want to control a friend's cell phone remotely and make "free" calls from it? In this hack how-to video, you'll learn how to hack Bluetooth-enabled cell phones with your Sony Ericsson or Nokia phone and the Super Bluetooth Hack—or "BT Info"—, a free program easily found through Google. Once installed, Super Bluetooth Hack will enable you to control your friends' cell phones remotely.
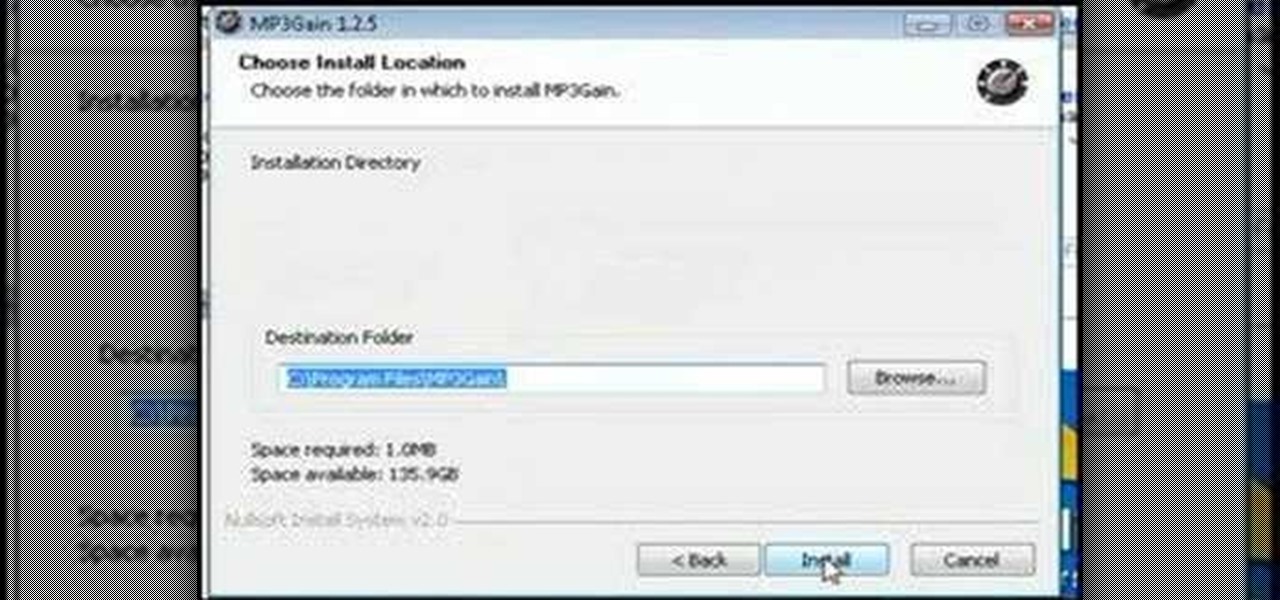
Tinkernut has all the answers when it comes to MP3 music files, and they're sharing a few of their favorite tips to help you build the ultimate MP3 collection! Watch all three of these videos for the best practices to manage your music files.

Learn how to do seated dumbbell hammer curls. Presented by Real Jock Gay Fitness Health & Life. Benefits
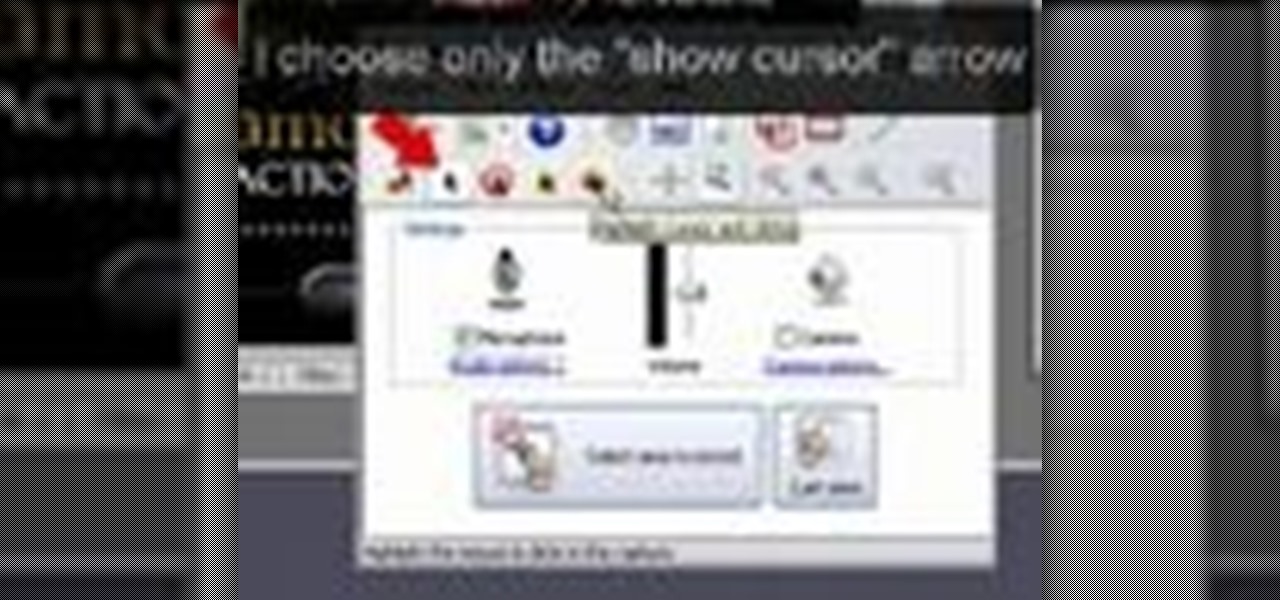
Photoshop Mama is here to make all your software tutorials you want to post on YouTube so much better! She shares info on the products and where to get them and also covers how shes produce vids and specifically her post production procedure for saving vids for upload to YouTube.

In this how to video, you will learn how to convert DVD movies to AVI or any other type of file for free. First, you will need to download DVDx 2.1 and the install it. Next, open the program and insert the DVD disc you want to copy. Go to file and click DVD root. Find the video and select the video_ts folder. You will see the IFO files. Look for the one with the longest time. Click on this one and press select. If you have a DVD already ripped on your hard drive go to file and click open IFO....
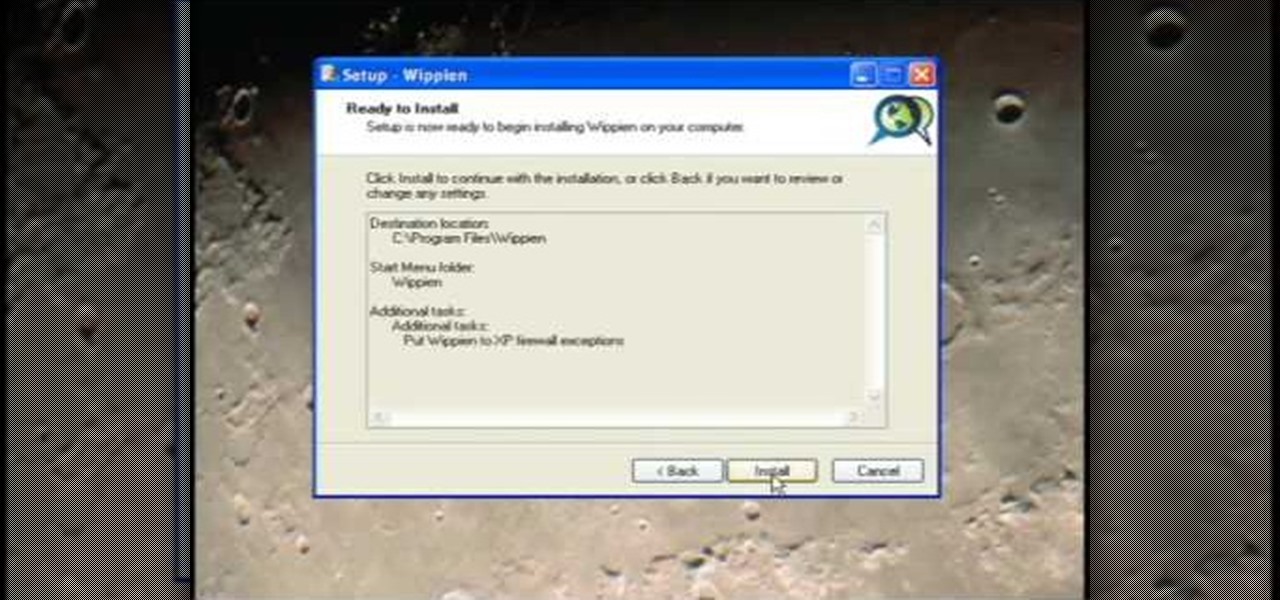
This video tutorial from ruralgeek shows how to set up and use Wippien VPN on Windows XP. First, download Wippien client from here: www.wippien.com.

So you need to find the p-value for your hypothesis test. To do so, employ the spreadsheet program Microsoft Excel. Using a simple formula, you can easily determine the p-value for your tests and thereby conclude strong or weak support of the null hypothesis.
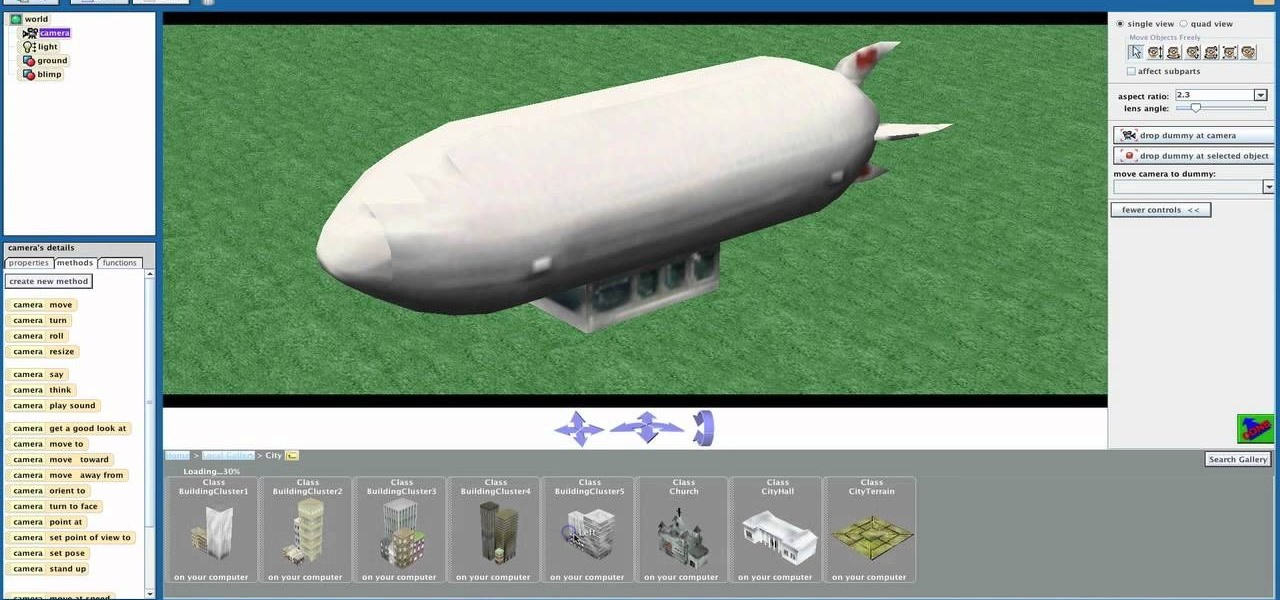
Shaun will teach us how to create a 3D video game compatible with MAC or PC with no prior programming knowledge. First download Alice, a 3D World program that can be turned into a video game. Open Alice, click on "add objects", click on "more controls" and select your choice of aspect ratio such wide screen. Now you can import your own 3D models that Shaun will show you at the end of the tutorial or choose from a wide selection that comes with Alice. In addition, if you click on "home," "web ...
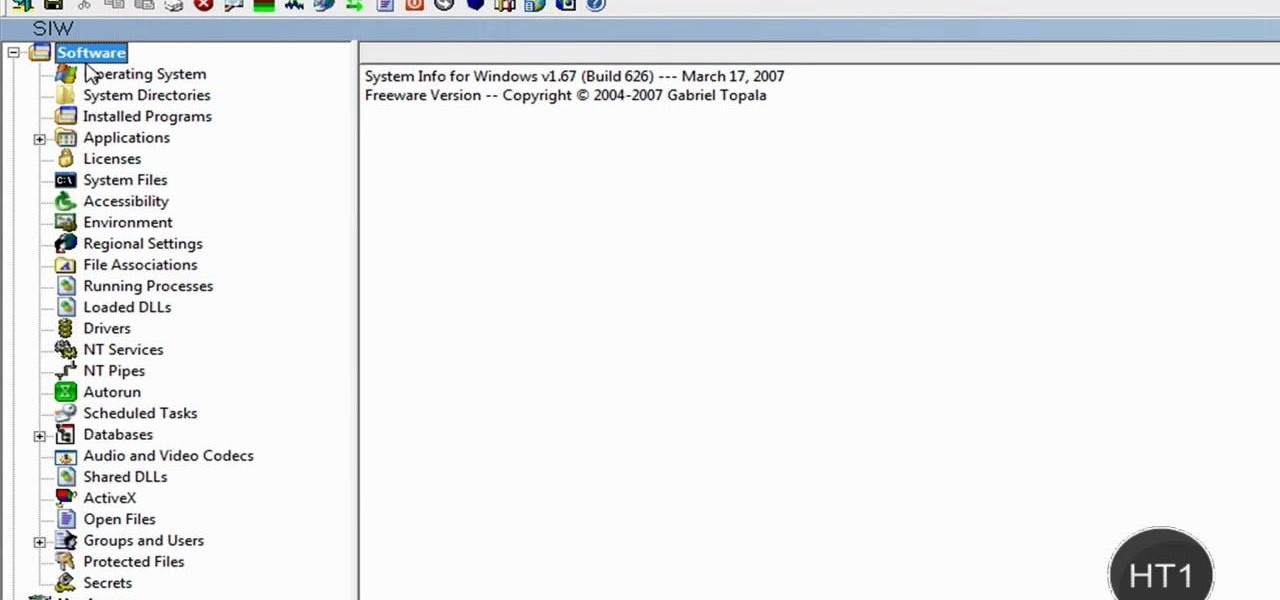
How to find out information / details about your computer? To find out the information about your computer, you need to download software from the website PC World. The following are the steps to download the software:
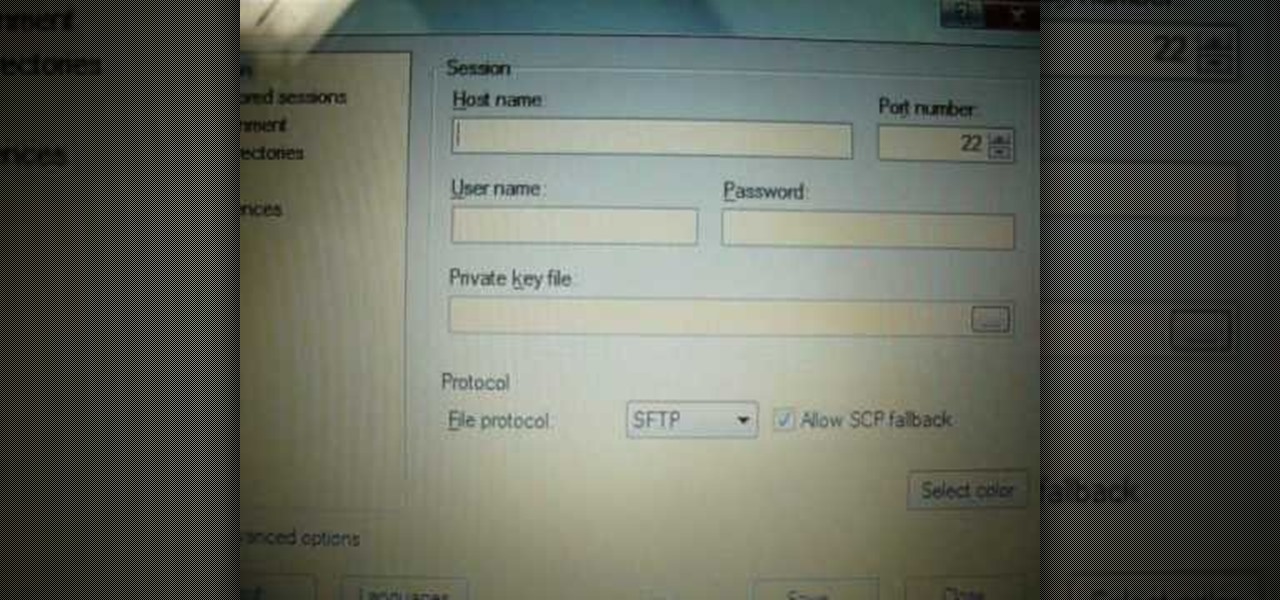
iPodTouchedMaster shows how one can easily SSH into their iPod Touch with all firmware! To SSH is the ability to hack into your iPod Touch's file system. First, your iPod Touch must be jailbroken. Next, you'll have to open Cydia. Click "Featured Packages" or search for the terms "Open SSH" (it will be listed under Console Utilities & Daemons). When you have OpenSSH click on it and click 'Install' and 'Confirm'. After this is finished, click return to 'Cydia'. This may take a lot of battery po...
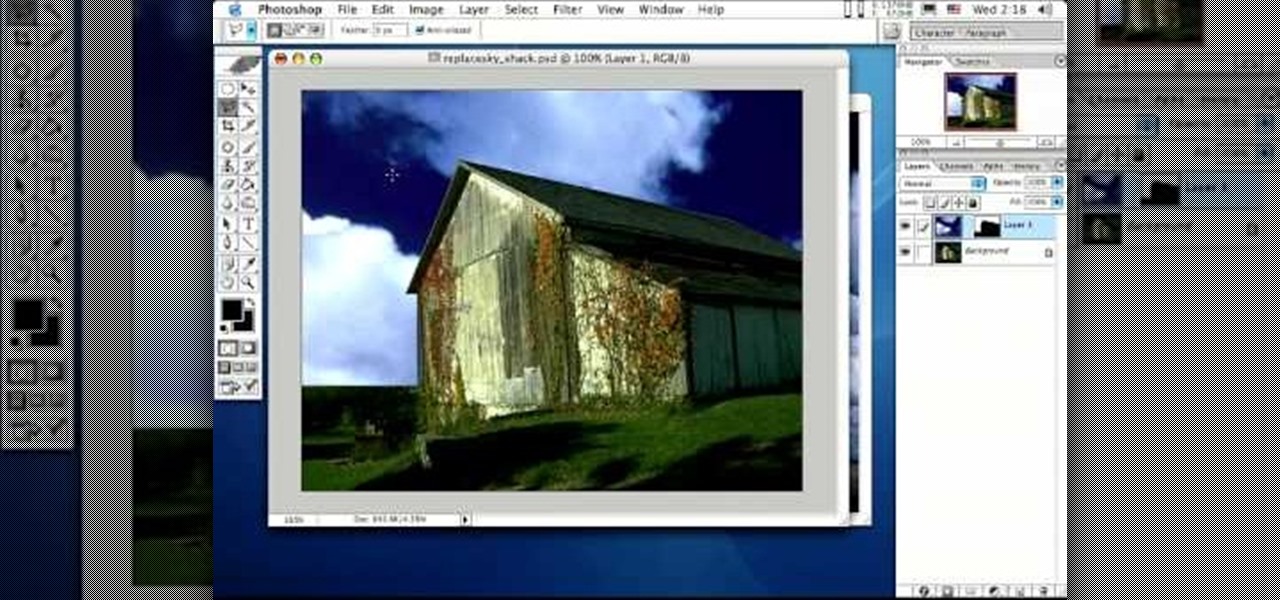
Photoshop is the perfect program to use when you want to make adjustments to photos you have taken. You can really make a sky pop in any of your pictures by using Photoshop to manipulate the color by following this tutorial.

Got ballet tickets? Learn to appreciate and enjoy the performance with these steps. You Will Need

Step 1 Launch the Adobe Flash program and select “Flash File (Actionscript 3.0)” under the “Create New” menu. Change the workspace layout to “Essentials” by clicking on the drop-down menu in the upper left of the top menu bar.

Step 1 In the Adobe Flash program, select “Flash File (Actionscript 3.0)” from the “Create New” menu. Switch the workspace layout by clicking on the dropdown menu in the upper left of the top menu bar, and selecting “Designer.” You can adjust the size and color of the document by adjusting the settings in the Properties panel.

Learn how to exercise your dog. Follow a regular exercise routine together with your pet. It will benefit you both!

So you've been given the slip -- the pink slip. Take a deep breath, and do the following. You Will Need
If you’re having trouble getting games on your memory stick, this video will walk you through the steps of just what you will need to do to compress files onto a thumb drive. There are a variety of steps you will have to follow and you’ll have to have a little bit of time to wait for your game to compress but the effort is well worth it.

While last year's revelation that Apple slows down iPhones with aging batteries left a bad taste in users' mouths, the company's $29 battery replacement program was a step in the right direction. However, all good things must come to an end; Apple will soon shut down the program, leaving users to pay the full $79 to replace their faulty batteries.

If you want to make some money from catching bugs and are sick of pentesting Facebook, Google, and Microsoft's products, Uber may be your new favorite playground.

How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implications which come along with it. I will show you using an example from the wargame IO Smash The Stack.

Welcome back, reader! In this tutorial, we will be covering our first program! So let's get to it. We all know the unspoken tradition of the first program when learning a language and of course, here we will respect and complete it. Fire up your favorite text editor (be it vim, emacs, gedit, it's all the same to me, no h8) and try to keep up.

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

Apple just showed off iOS 9 and its new features at WWDC 2015, including multitasking support for iPads (finally!), a new Low Power Mode to save battery, local area search and transit directions in Maps, a highly improved "Proactive" Siri, a better Spotlight search, new apps, and so much more.

Apple is widely known for keeping a tight grip on iOS, disallowing open-source and third-party downloads. While there are many reasons for this, the three most frequently referenced are quality control, malware prevention, and of course—money.

Big business is on the web these days and you don't have to build a shopping website or blog to get involved.
A quick video showing how to get free music online. May take a couple minutes per song. To prove quality I used the song i download in the video as background music. "I Wish" by Skee-Lo

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

What if the code you are trying to reverse engineer is obfuscated or somehow corrupted? What if no way is left? Here comes what I like to call (wrongly and ironically) the "brute force of reverse engineering".