In my last article, I explained why text adventure games are some of the most Steampunk computer games out there. I even shared a free Steampunk text adventure game that I'd made myself!

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

Influencers of augmented reality demonstrate expertise in their fields and outline a strong vision for the future that they evangelize to others. They help define the direction of the industry and identify others who foster and create innovation in the field.

One of Android's most glaring weaknesses is its lack of an iMessage equivalent. That is, of course, until now. There's one app that will allow Android users to experience iMessage on their non-Apple phone, complete with end-to-end encryption, message effects, and group messaging.

Throughout this NR50 series, we have talked about the incredible growth the augmented and mixed reality space has seen in the last year. More devices, software, developers, and use-cases seem to arrive daily. For this growth to have occurred, it took the work of many people, from many different backgrounds and skill sets — and Next Reality wants to recognize them for all that they have done and are doing.

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

This holiday season, give yourself a gift that will keep on giving: a new web development skill. Whether it's to secure lucrative freelance work in the new year, bolster your résumé, or have fun with some frankly outrageous discounts on online course bundles right now (up to 99% off), there's nothing better you can do with your free time. Your future (pro coder) self will thank you.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

Apple's Calculator app received a massive redesign, making it so much more than a simple calculator with built-in scientific functions. There's a new Math Notes feature that ties in with the Notes app, it can keep a history of your calculations, and you can even convert over 200 currency and measurement units.

Downloading content from TikTok is relatively easy, even if the video is protected, but the same can't be said of Reels, Instagram's version of short-form videos. Instagram doesn't make it easy to download content unless it's your own, and that's especially true with Reels. However, there is a way to bypass Instagram's restrictions on your iPhone and save videos locally without ever leaving the app.

It's already been a banner year for mergers and acquisitions in the augmented reality industry, with WaveOptics and Ubiquity6 among the notable companies acquired. Two of the more active M&A players, Snap and Epic Games, continued their respective buying sprees this week with major deals supporting their AR strategies.

If you've recently built a Wi-Fi spy camera out of an ESP32-CAM, you can use it for a variety of things. A baby monitor at night, a security camera for catching package thieves, a hidden video streamer to catch someone going somewhere they shouldn't be — you could use it for pretty much anything. Best of all, this inexpensive camera module can perform facial detection and facial recognition!

Although the Clock app in iOS has undergone some design changes over the years, you still can't set more than one timer on your iPhone. Oddly enough, Apple's own HomePod speaker added this feature, mimicking the timer on Amazon's popular Echo smart speakers. Fortunately, through Apple's Shortcuts app, there's a clever hack to set multiple timers — without using a third-party timer app.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

This is a video in the Adobe Flash family advances the Flash Action script from 2.0 to 3.0. This video teaches you how to make a flash action script 3.0 button using frames and adding the flash action script coding. Starting with a box and adding text and adding flash coding events, specifically a mouse event and an indication that the button was clicked. Then the programmer adds a variable to the button. She also gives us a hint for the next tutorial which includes a target.

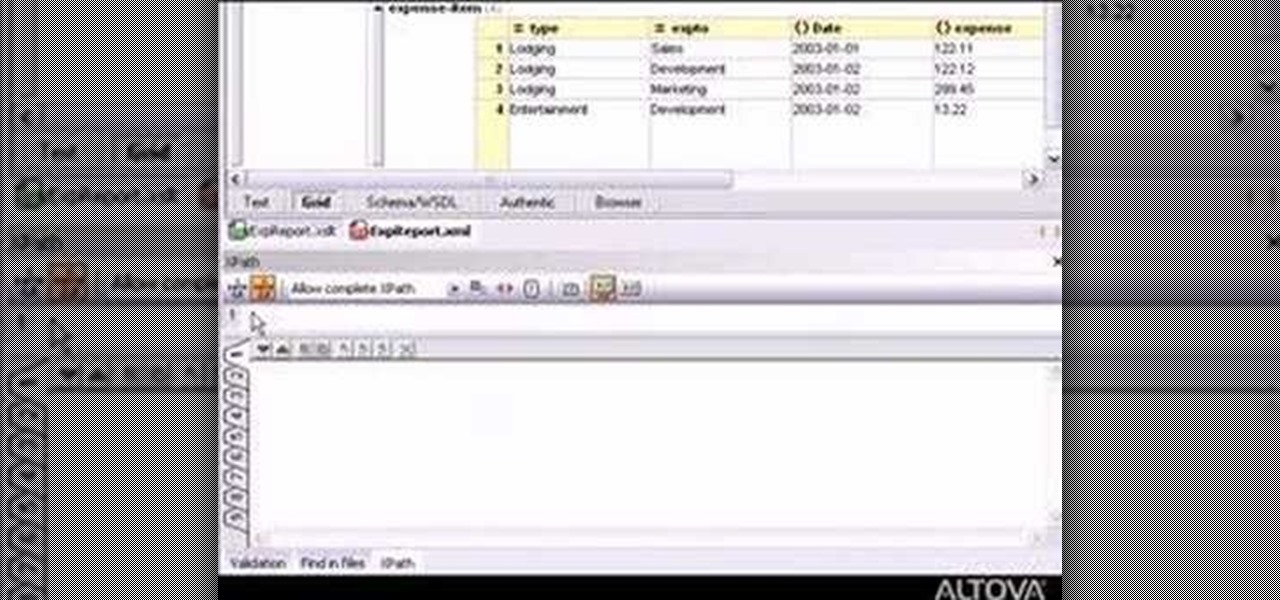
Desire to be an XML editor/programmer? This video will help you. You'll learn how to edit, analyze, and debug XPath expressions with XMLSpy.

The first day of Hanukkah is here, the day you start lighting the candles of the menorah. So, why not ditch the wax and light the "lights" this year?

Inception may not be the lead contender for the 68th Golden Globe Awards, honoring the best movies and television from 2010, but Christopher Nolan's film still collected four nominations— Best Motion Picture, Best Director, Best Screenplay and Best Original Score.

A short video going over the basics of creating the character with which you will explore the remarkable fantasy world in EverQuest. The video is hosted by EverQuest lead programmer Terry Michaels. Create An EverQuest character.

Dreams are like an internal human holodeck. Inside your mind, anything is possible, from your grandest wishes to your worst nightmares. This is all well and good, but what if you could control your dreams and become the omniscient god of a handpicked reality whenever you go to sleep? Inception took this idea to the logical extreme by invading other people's dreams.

When you first become interested in learning how to program, it can be difficult to find a place to start. A lot of questions come up, especially if you're new to the idea of programming entirely. After you pick which language you want to learn, you have to worry about how you're going to write the language.

All hail artist, programmer and human electrocution music-machine, Daito Manabe. He's back, and better than ever: Read more about his process.

Last night we saw Red Nights in TIFF's MIDNIGHT MADNESS program, and we even talked to programmer Colin Geddes about his awesome job..

+Tyler Neylon, a programmer and mathematician currently specializing in iOS app development, recently posted a fun project to his Google+ profile: 50 designs with 50 LEGO pieces, a set of 51 photos. Given a small 50-piece Lego set this past Christmas (well, Tyler admits: "...58 [pieces], actually, but many of them are very small, as you can see"), he craftily stretched his imagination to create 50 different models, though the kit included instructions for only 3.

Most employed in the game industry have two-word job titles that start with “game”—game designer, game producer, game critic, game tester, etc. Usually, they’re one or the other, even though some can be both a game designer and a game tester or game critic and game tester. And rarely does one person get to call themselves a “game everything”. Ben “Yahtzee” Croshaw is the exception.

Japanese artist and programmer Daito Manabe uses the face as an instrument. He makes the human face involuntarily dance using electric stimulators (which, by the way, look like the same kind used for electroshock therapy). The stimulators are taped to the face, and each musical beat delivers a shock, resulting in disturbing face contortions in time to the music.

People sometimes ask me about the IT industry here in the states. These folks are usually either trying to get into a certain field, or looking to switch or move into another one. Right now, you may currently be a Computer Science major that will be graduating shortly and are interested in the current state of IT security.

If you haven't participated in this week's Math Craft project on the platonic solids, maybe this will inspire you to do so.

Age doesn't matter in the world of programming, only skills, and recent high school grad Jack Eisenmann definitely has them. He recently built a homebrew 8-bit computer from scratch, calling it the DUO Adept. A worn television makes up the monitor and speaker system, an old keyboard acts as the input controller and the actual computer itself is housed inside a clear Rubbermaid container, consisting of 100 TTL chips and a ton of wire.

It's more addictive than Angry Birds, perhaps as relaxing as transcendental meditation, and satisfyingly simpler than GarageBand. It's Otomata, a newly programmed generative sequencer designed by Batuhan Bozkurt, a Turkish sound artist, computer programmer, and performer. But really, it's best described as an audio/visual music toy that anybody can play online—with beautiful results.

Matt Reed, a web developer at Nashville interactive ad agency Redpepper, built a massive, real life Facebook Like "button" out of Legos, which lights up whenever someone clicks Like on his Facebook page. The programmer loves LEGOs, and draws an affinity between the legendary building blocks and engineering: "[Legos] are great for prototyping physical objects. I don’t manufacture things, but I do click blocks together. Plus, most things I deal with on a daily basis are pixelized. Legos are som...
Warnings this only for educational use i dont take responsiblety for any use of this article if you want to use this for use at a school plz contact me at sebzy4@hotmail.com hi im a computer enginer/programmer (NOT games) but i am good at hacking and i want to help. notise that this is just a help site not hacking site but this will help firstimers

Have an old-school tabula recta lying around? No? Then just print out the chart below. Nothing ensures better password security than this centuries-old cipher technique. Here's how it works, via Wikipedia:

Keyloggers are a must-have tool in your arsenal. Hardware keyloggers have the advantage of being undetectable through anti-virus or other protection programs. They also capture keystrokes before the OS even boots up, so they are pretty handy tools.

"How do I install Arch Linux?" That question was bound to come up eventually. And with me using Arch, it's no coincidence that all of you want to use it as well. Arch is arguably the best Linux distro available. Distros that come close are Gentoo and some aspects of Ubuntu, but Arch is meant for building your OS from the inside out. Arch is built around minimalism, so you won't get anything by default. It doesn't even come with sound!

One of the biggest advantages iOS has over Android as a mobile platform is how readily and fully it has embraced mobile gaming. There are over 200,000 games available in the Apple store, compared to approximately 100,000 in the Android Marketplace. As an Android-using gamer, this has always bothered me.

By "God," I mean Morley Davidson, John Dethridge, Herbert Kociemba, Tomas Rokicki and about 35 CPU-years.