How To: Download streaming TV and movies with Joost and Miro
This video shows you how to download and play TV and movie files on your computer using two programs: Joost and Miro.


This video shows you how to download and play TV and movie files on your computer using two programs: Joost and Miro.

This tutorial explains how to use the free Hotkeybind macro. It allows you to open programs or insert text with a just a keystroke.
This Pamie Demo shows how to setup, install and run a simple automation script. It shows you: how to install Pamie, how to create a Pamie test script to Automate a form using PythonWin IDE, how to write the script and how to run the test. The volume is really low so crank your speakers way up and make sure you have the proper Python and programs downloaded.

We're glued to the news now more than ever, but our "free press" isn't necessarily free of charge. Cable news outlets like CNN and MSNBC are locked behind expensive cable TV packages and cord-cutting streaming subscriptions such as Sling TV and Hulu + Live TV. Luckily, there are plenty of alternatives to get your TV news fix, free of any payment, account, or commitment.

There is nothing more irritating than having a nice jam session interrupted by an ad selling B vitamins, and that's exactly what Spotify does to you if you don't pay up.
Welcome back Hackers\Newbies!
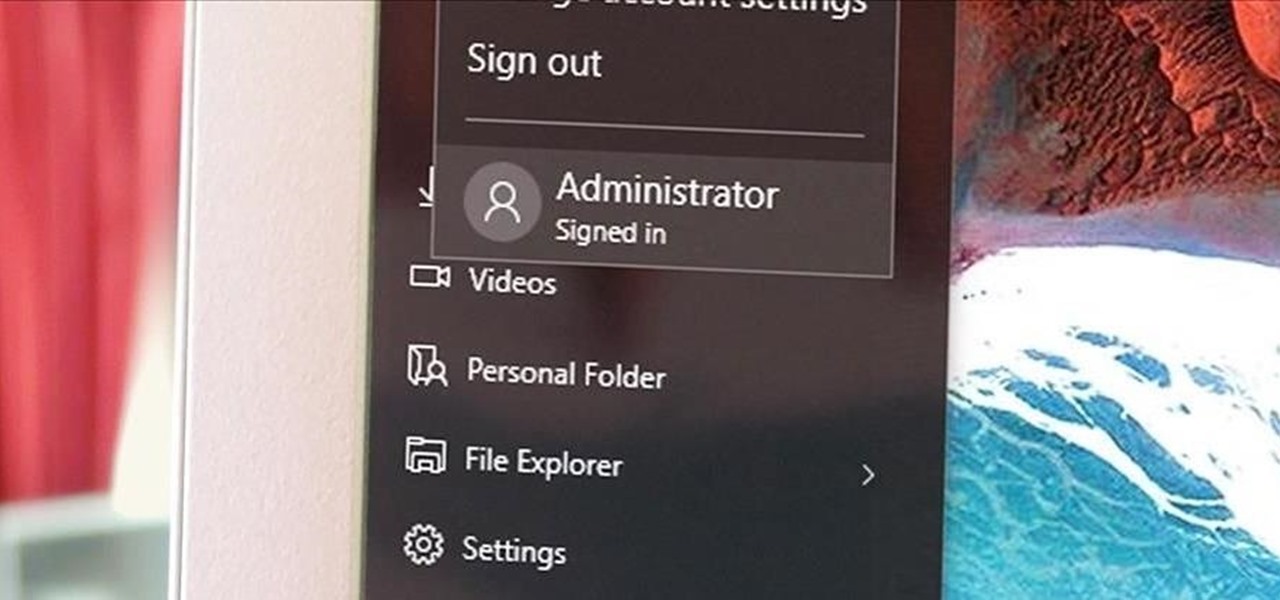
Windows has always had an "Administrator" account that allowed you to install programs and manage system files with elevated privileges. The difference between this account and a regular user account with administrator access was that you never got bothered by annoying User Account Control popups when you were logged in as Administrator.
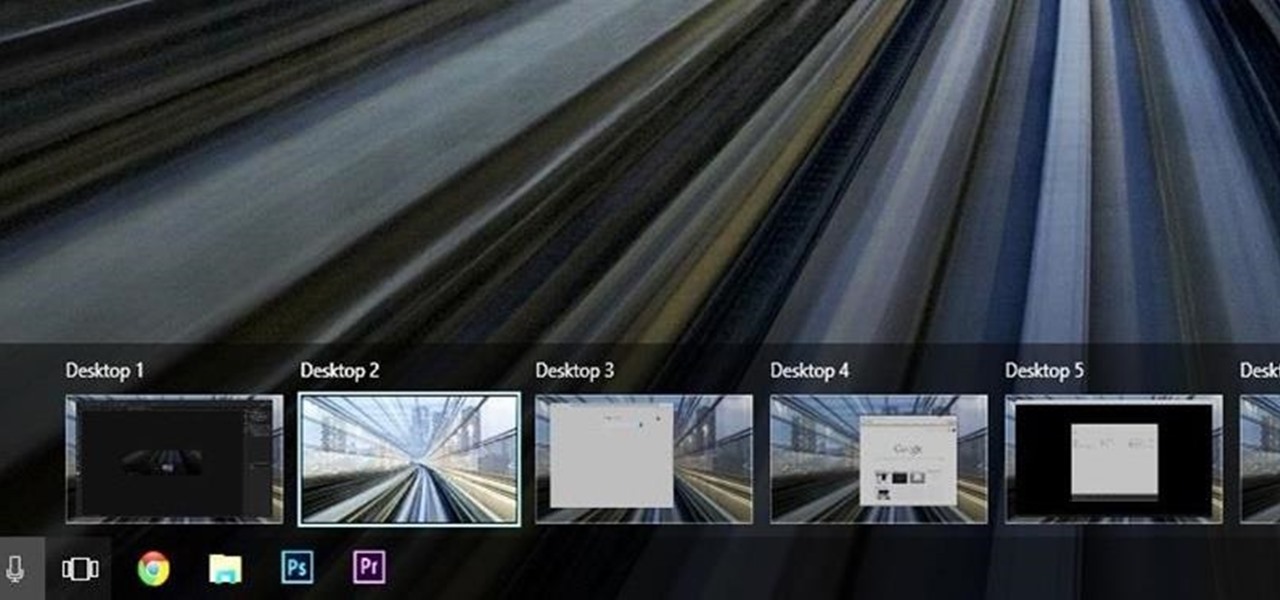
Linux and Mac users have long enjoyed the use of multiple virtual desktops to free up clutter on their home screen and keep individual workflow environments separated, but Windows users have always been stuck with one solitary desktop.

I love cryptography. It is like a great gigantic puzzle for me to solve. However, it is more important than that. It is also how we keep secrets safe. Not just sorta safe either, but really safe.

Keyboard shortcuts are super useful for multitasking and saving time on the computer. But if you're like me, you might only know a few of the million of keyboard shortcuts that are out there. I pretty much know the most basic of basic shortcuts: copy, cut, paste, save, select all, and screenshot.

Thanks to Flutter, it's now possible to control the music on your computer simply by making a few hand gestures. The app is available for both Windows and Mac and uses your computer's webcam to monitor your hand movements. Through the use of a few simple hand movements, you can play, pause, forward or replay your music. Flutter works with iTunes, Spotify, Quicktime, MPlayerX and a few other programs.

In this article, I'll be explaining the basics of how microcontrollers work, physically and virtually. First off, microcontrollers are no simple thing, so don't be discouraged if you find it mind-boggling! The world of microcontrollers is fascinating, engaging, and an awesome hobby; it never gets boring. I'll be focusing more on I/O and analog based microcontrollers, such as those running Arduino, and using Atmel chips as examples (these are most commonly available, and easy to program).

A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).

Java is one of the world's leading programming languages thanks to its virtually endless array of applications. Since Java's initial release in 1998, this Open Source platform has become beloved by coders for its speed, flexibility, and dependability.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

The de Blasio Administration of New York City has announced that the NYU Tandon School of Engineering will be hosting the country's first publicly funded VR/AR facility.

Welcome back, reader! In this tutorial, we will be covering our first program! So let's get to it. We all know the unspoken tradition of the first program when learning a language and of course, here we will respect and complete it. Fire up your favorite text editor (be it vim, emacs, gedit, it's all the same to me, no h8) and try to keep up.

If you remember last time, we successfully uploaded picture with a small hidden PHP command executer embedded in it onto a server. Now, our goal is to take this a step further and get an interactive shell. To do this, we need to upload another file that either binds a port for us, or connects back. For this tutorial, we will use a Python reverse Meterpreter shell.
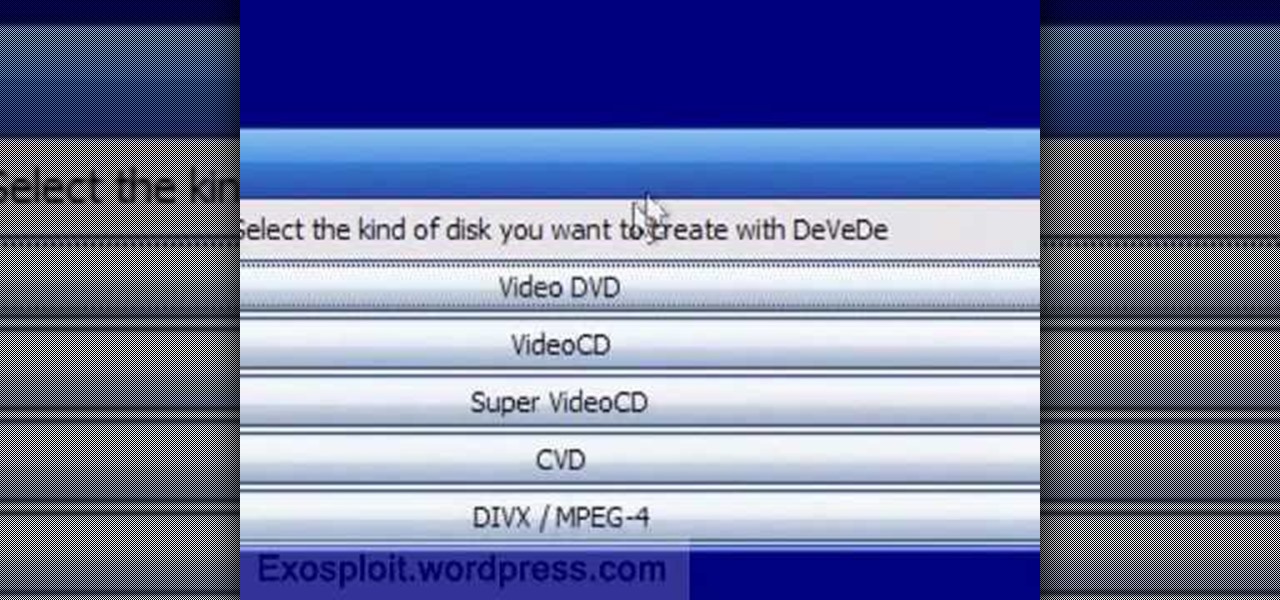
This video explains how to burn DVDs that will play on a standard DVD player in Windows. The programs needed to complete this project include IMG Burn and DeVeDe which has been modeled for Windows. The final burn product created with this program will allow the DVDs to play on computers and actual DVD players. The first step is to hit open to select the file you wish to burn. You must then select burn ISO or Bin file in IMG Burn or DeVeDE. You can then select a title for your burned disk leav...

In this tutorial, we learn how to clear the ARP cache. First, go the command prompt on your computer and type in "C:/>netsh interface ip delete arpcache Ok". Press 'enter' on your keyboard and then it should be cleared out. If you want to view your ARP cache, type in the command "C:/>arp -a". If this fails, then you will need to use Microsoft Windows to repair the network connection. If this doesn't work, talk to the person that manages your connection. If successful, this will help make your...
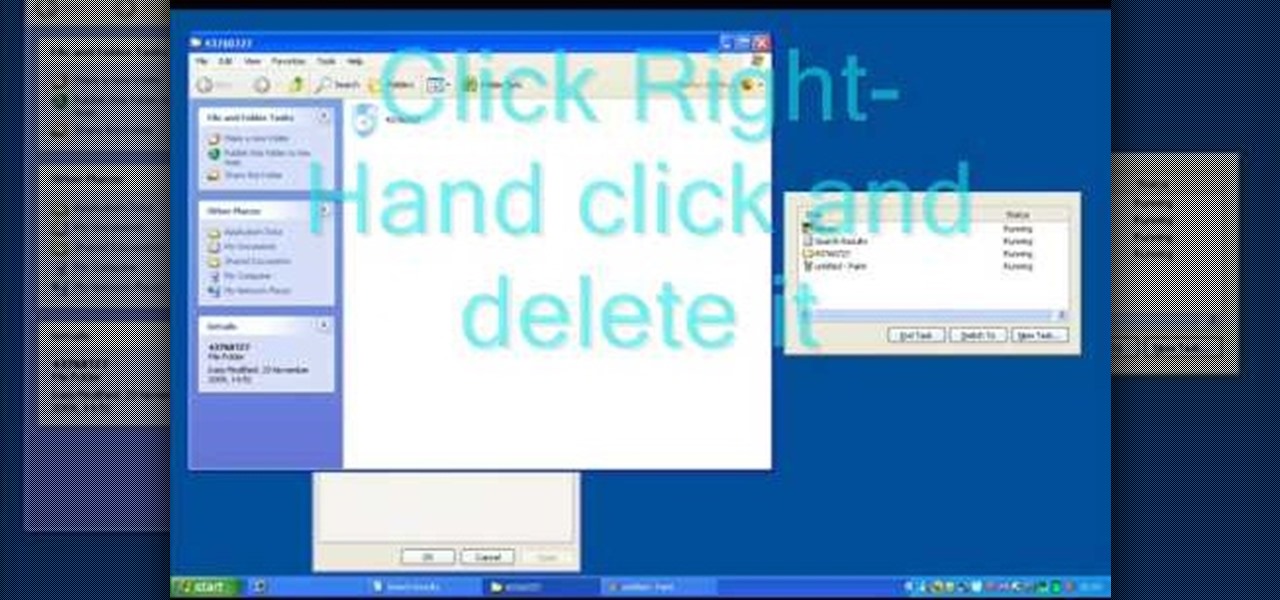
In this tutorial, we learn how to remove security tool in less than one minute. First, restart your computer, then press "ctrl+alt+del" when your new window starts up. After this, wait for a few seconds, then if you see the security tools pop up, end the task for it. Then, go to the start menu, then all programs, then look for any security tools. Right click, on "find target" then delete it! After this, your security tools will be deleted and will stop annoying you. You will be able to delete...
In this video, we learn how to remove Security Tool the simple way. Most ways will not remove this from your computer, but this way will. To start, you will need to restart your computer. After this, press ctrl+alt+del the moment Windows shows up. Then, go to the Task Manager and look through the programs that are open. When your security tool opens, press the same buttons to get the mouse free. Then close the security tool from the Task Manager. Now, go to your desktop and press on the icon ...

In this tutorial, we learn how to remove pop up screens when Avira Antivirus updates. First, locate the installation folder for Avira, this should be in your computer programs. After this, locate the file "avnotify.exe". Next, right click this and go to the preferences option. Now, go to security, then edit, then click on the system option. Click "deny" on all the boxes in the bottom section, then save these. Now, the next time your Avira updates, you will not get a pop up box that tells you ...
If you need to use a file or two on your work computer from your home PC, Remote Desktop in Windows 7 makes it completely possible. You're no matter limited to laptops and flash drives. This video form Microsoft shows you the overall use of Remote Desktop.

Where do you get all of those cool apps for you Android mobile device? There's one place to go to find all of the latest apps for your mobile phone, so what is it? Best Buy has answers. The Best Buy Mobile team explains how simple it is to add a contact to your Android enabled cell phone.
This video tutorial from butterscotchcom shows how to change icon arrangement on your Blackberry phone.

In this how-to video, you will learn how to free up disk space on your Windows Vista computer. First, go to my computer and right click the drive that you want to free up space on. Next, click on properties. Click disk cleanup on the new window. Select which files you want to delete by checking the appropriate boxes. Once this is done, click okay. You can also select clean up in the other tab to free even more space. The first section will allow you to remove programs you do not need, while t...
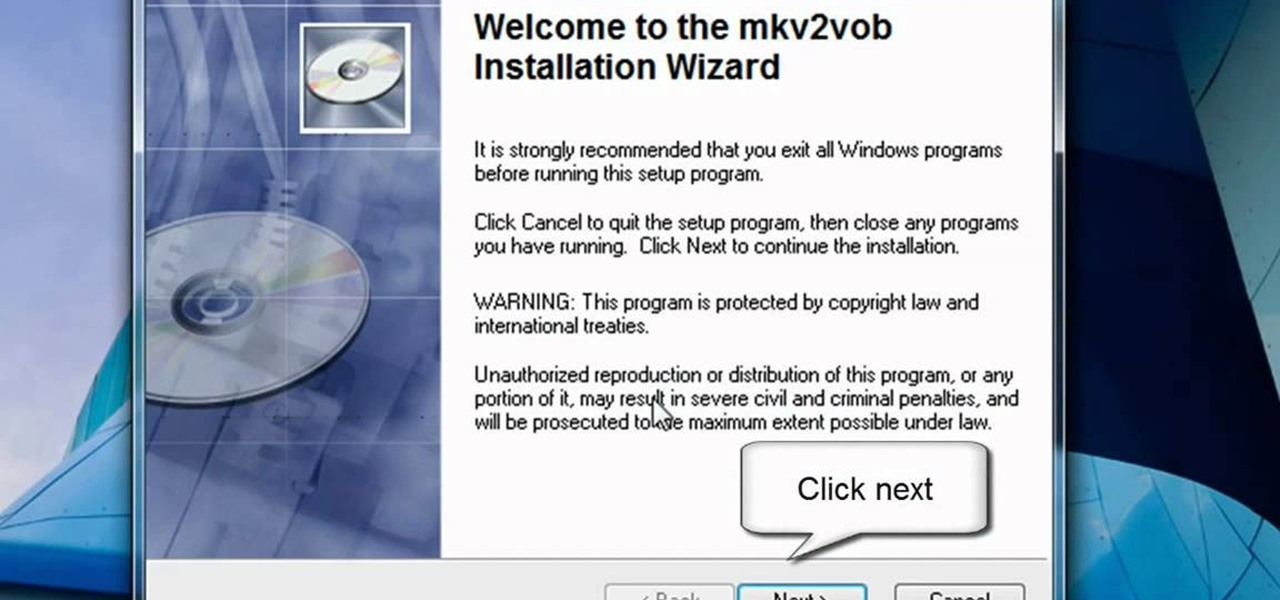
In this video tutorial, viewers learn how to play MKV videos on the PS3 using the MKV2VOB software. Begin by downloading the MKV2VOB programs from the link in the video description. Once downloaded, install it on your computer. Now open the program. Go the Configuration tab and change the setting to the same as the video. Then click on the Add File tab and select Browse under Source File. Find your MKV file and select Open. Then under Destination Directory, select where you want your file to ...

This video from CNET Insider Secrets tells you how to recover deleted files from a data drive. If a disk is still readable by the computer, files may be recovered. Files may be recovered using the PhotoRec program, PC Inspector or other programs that may be available. An example is shown where mp3 files are deleted from a flash drive. We are then shown how files are recovered using the PhotoRec program, including how to select the correct file system. The mp3 files are recovered along with va...

This video teaches you how to open .zip files with a just few easy steps. First, you need to download a program Winrar. The download can be found at http://www.rarlab.com/download.html and the download should start immediately. Once the download is complete, open the program.
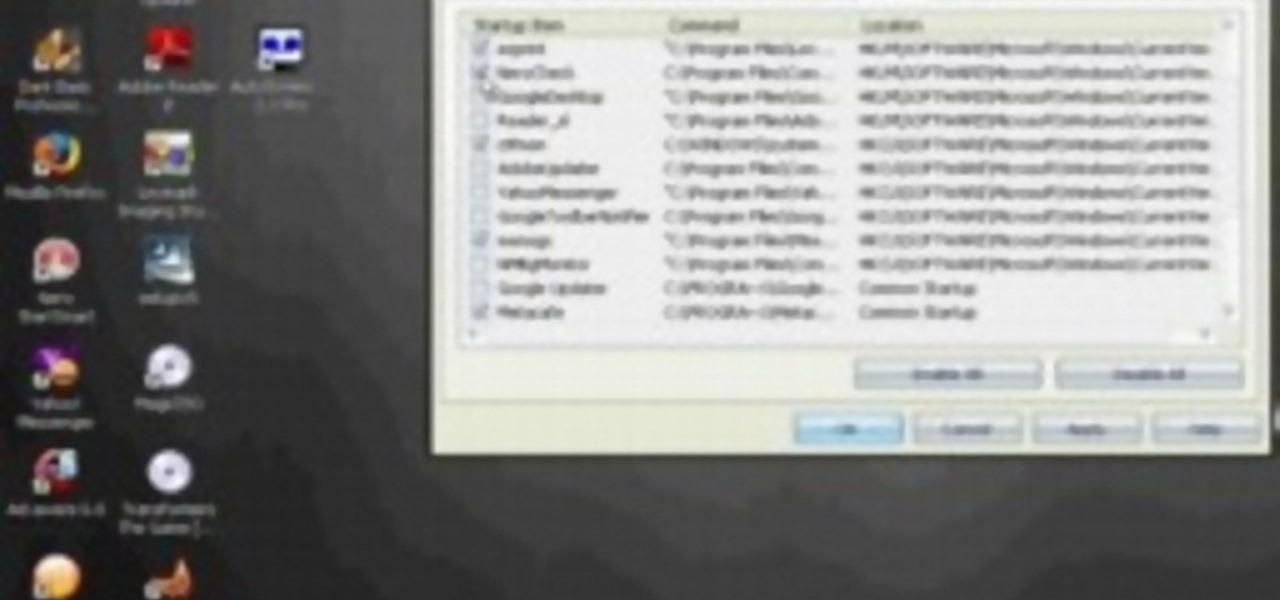
If you want to speed up Windows XP boot time with simple steps then you need to watch this video. To speed up Windows XP boot time: Type msconfig in Run textbox and click OK. You can see run textbox if you click Start menu and select Run. System Configuration Utility appears. Uncheck all programs in Startup tab that you don't want to load during boot then click Apply button. Tips: If you want all to be unchecked, click Disable All. Check hide all Microsoft services in Service tab. Uncheck all...

Is your Mac running slow? If yes, then the instructor in this video shows just how to diagnose and fix it. It is not an uncommon problem that a Mac begins to get slow with time. Though there are a million different things that can slow down a computer and it is never easy to pin point the problem, there are a few things that you can do to try and get it fixed. The first thing that you should do is check the free space in the hard disk drive. If it is less than 10 percent then you better start...

On this YouTube video the user Vvistacomphelp shows you how to print screen and crop pictures. The first thing that the user shows is where the Print Screen button is located at on most keyboards so that you can press it on yours. The second thing is go to the start menu in Windows Vista and type in "paint" in the search box on the bottom left then open Paint under Programs. The third thing that is shown is how to make an image appear inside of the paint program so you can crop it. After foll...

Computer forensics expert Steve Burgess gives a highly informative tutorial on how to recover deleted emails in Outlook and Eudora. The most critical factor affecting the recoverability of deleted web-based emails, according to Steve, is whether the PST file, which stores all the emails, has been compressed after the mail was deleted. If this hasn't been done it is possible to hack into this file and recover the deleted email. Text-based emails, like those one creates on programs like Eudora,...

This is a directional video of how to increase the speed of a Windows Vista PC. The first step is to uninstall programs that you do not use. Then you want to go into MSCONFIG and remove unnecessary start up entries. You can also configure the performance options of your computer in the computer's properties. The next step is to go to the system tools and run Disk Cleanup. It is also important to run the Defragmentor from the system tools.

IMVU is a 3D avatar chat, instant messenger, and dress up game. Get help with all of your IMVU avatar needs with these IMVU tips and tricks! Watch this video tutorial to learn how to make a catalogue picture for IMVU. This will show you all about making your catalogue picture using such programs as Paint and Photoshop.

Feeling calmer and happier is at the tip of your nose: It’s just a matter of using your common scents. Check out this Howcast video tutorial on how to use Aromatherapy's Essential Oils to improve your life.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

It's nearly impossible not to be at least somewhat familiar with Microsoft Excel. While it's needed for many office jobs and data analysis fields, hackers could also benefit from improving their spreadsheet skills. Many white hats already know some of the essential Excel hacks, such as cracking password-protected spreadsheets, but there's so much more to know from an attack standpoint.

Since its release back in 1988, Microsoft Office has been the top client and server software suite for businesses around the world. Office's domination is thanks to both Microsoft's extraordinary foresight and their continual updates and innovations to ensure that companies always get what they need.