Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

Defcon is the largest hacker conference with something for everyone, whether it be the talks, parties, villages, or any of the hundreds of events. In this guide, we'll take a holistic view at everything that goes into attending the con for the first time, from securing your electronics and making the most of your time to the logistics of getting there and finding the right place to stay.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

Web applications are becoming more and more popular, replacing traditional desktop programs at an accelerated rate. With all these new apps out on the web comes various security implications associated with being connected to the internet where anyone can poke and prod at them. One of the simplest, yet the most prevalent types of security flaws found in modern web apps are SQL injections.

After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vulnerability.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

For all those times when an app either isn't available or simply won't cut it, your phone's internet browser provides access to your favorite websites and services. But some browsers are flat-out better than others, and chances are, the browser that came pre-installed on your phone isn't the best option out there.

All fields of study have their own language. For people interested in learning about microbes, the language can sometimes be downright difficult — but it doesn't need to be. From antibiotics to xerophiles, we have you covered in an easy-to-understand glossary.

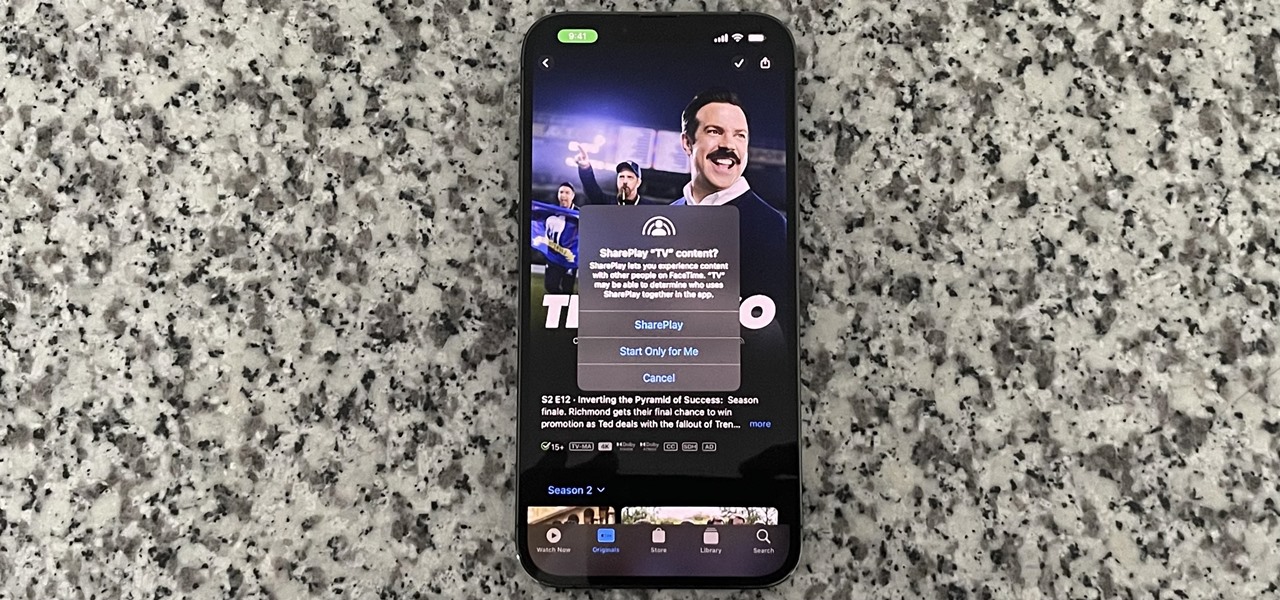
SharePlay is arguably one of the most significant features to hit FaceTime since group calls, and it's still hard to find apps that support shared experiences in FaceTime. Apple does list a few apps, but there is no official index of all the apps with SharePlay integration. That's where we come in.

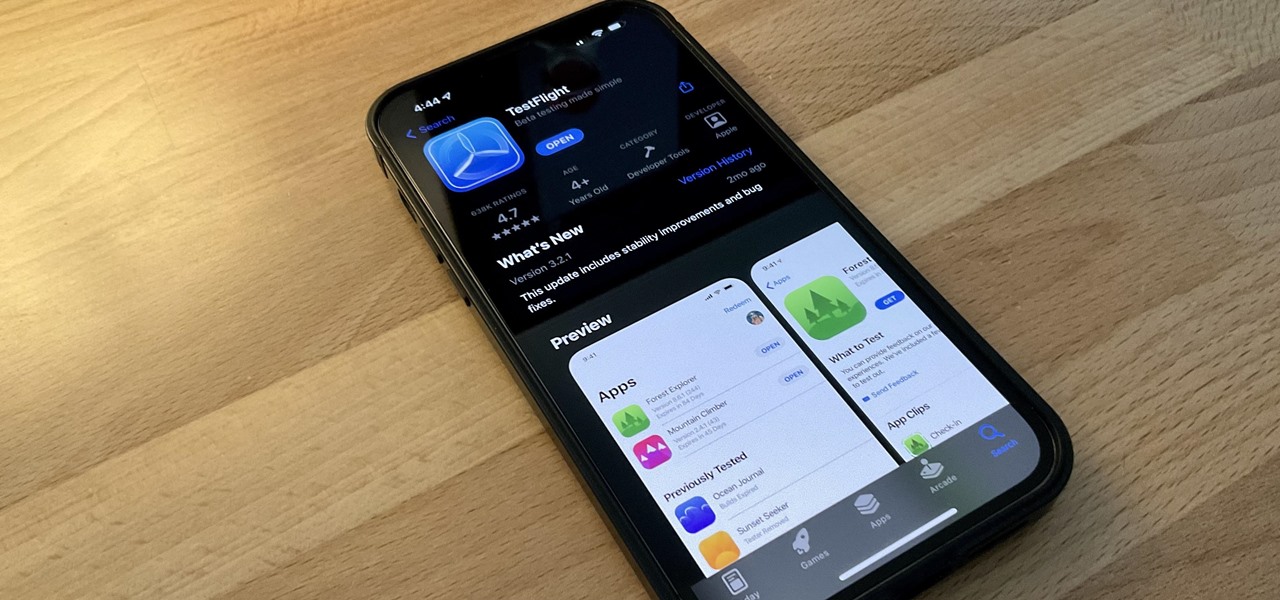
Believe it or not, there are legitimate iOS apps beyond the App Store that you can install on your iPhone. Some of them even work for iPad, Apple TV, and Mac, and there are also benefits to using them over apps found in the App Store.

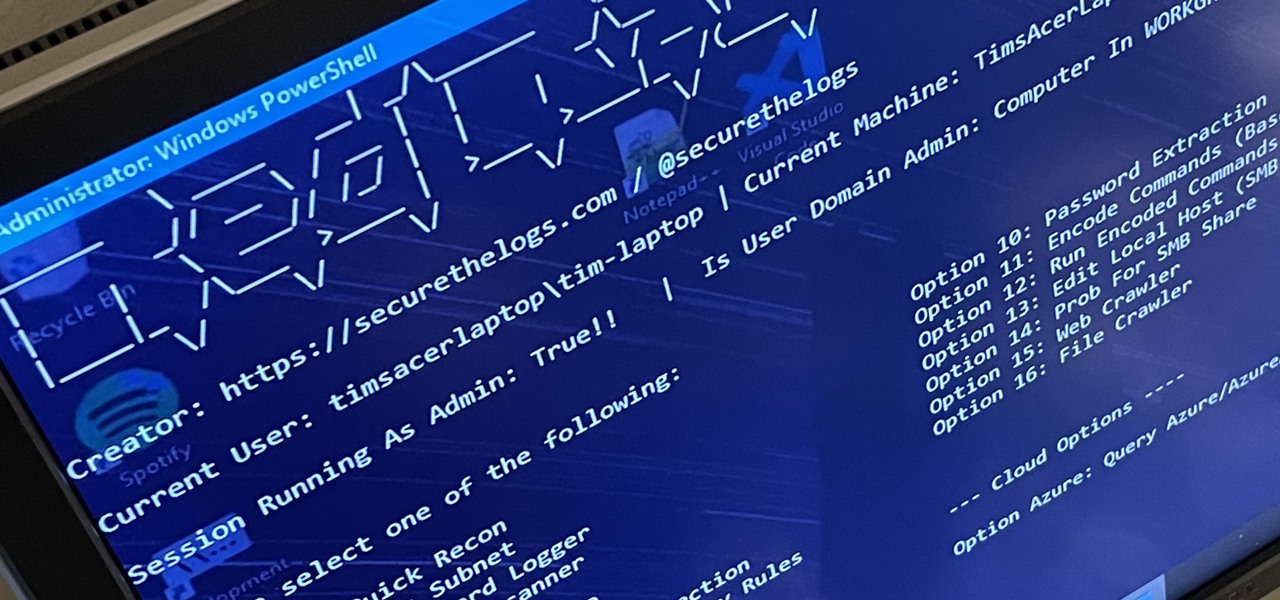
RedRabbit is an ethical hacking toolkit built for pen-testing and reconnaissance. It can be used to identify attack vectors, brute-force protected files, extract saved network passwords, and obfuscate code. RedRabbit, which is made specifically for red teams, is the evil twin of its brother, BlueRabbit, and is the offensive half of the "Rabbit Suite."

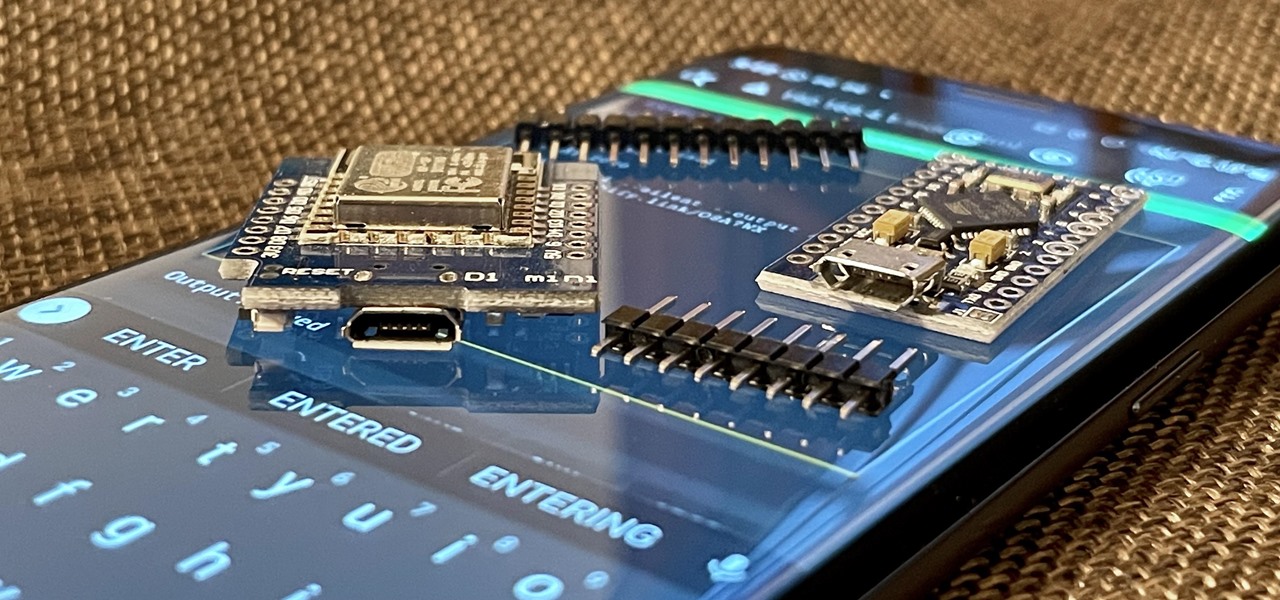
With just two microcontrollers soldered together, you can inject keystrokes into a computer from a smartphone. After building and programming the device, you plug it into a desktop or laptop, access it over a smartphone, and inject keystrokes as you would with a USB Rubber Ducky.

As we've seen with other tools and utilities, administrators typically use certain things to do their job more efficiently, and those things are often abused by attackers for exploitation. After all, hacking is just the process of getting a computer to do things in unexpected ways. Today, we will be covering various methods to perform banner grabbing to learn more about the target system.

Privilege escalation is the technique used to exploit certain flaws to obtain elevated permissions relative to the current user. There are a vast number of methods out there to go from user to root on Linux, and keeping track of them all can be difficult. This is where automation comes into play, and a privilege escalation script called Linux Smart Enumeration is one to take advantage of.

Everybody knows not to store sensitive information in unencrypted files, right? PDFs and ZIP files can often contain a treasure trove of information, such as network diagrams, IP addresses, and login credentials. Sometimes, even certain files that are encrypted aren't safe from attackers. That's where Zydra comes in — a tool for cracking RAR files, ZIP files, PDF files, and Linux shadow files.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

Apple's already gone through iOS 13.0, 13.1, 13.2, 13.3, 13.4, and 13.5 betas, and now it's time for iOS 13.6. If you want to try out new features on your iPhone before the masses, install either the developer or public beta.

If you have a modern iPhone, you have an excellent video recorder at your disposal. Every iPhone since the 6S has the ability to shoot in 4K resolution, and each new iteration has brought new capabilities to the table. But even the best mobile shooter can use a little extra help. That's where these video recording apps come into play, to ensure the footage you capture is as good as can be.

Flight disruptions can cost billions of dollars, but most modern commercial flights rely on air traffic control systems that harbor serious vulnerabilities. The Federal Aviation Administration uses an infrastructure called NextGen, which relies on Automatic Dependent Surveillance – Broadcast, or ADS-B for short.

Airgeddon is a multi-Bash network auditor capable of Wi-Fi jamming. This capability lets you target and disconnect devices from a wireless network, all without joining it. It runs on Kali, and we'll cover installing, configuring, and using its jamming functionalities on a small, inexpensive Raspberry Pi. When done correctly, it will deny service to a wireless network for up to several blocks.

Apple pushed out its iPadOS 16.6 update for iPad on July 24, with iPadOS 16.7 following on September 21. While the company is currently working on improving iPadOS 17, we may still see an iPadOS 16.8 update. If that happens, you can try out all the upcoming new features as long as you're OK with running beta software on your iPad.

Apple's iOS 16.6 software update for iPhone was released on July 24, with iOS 16.7 following on September 21. While Apple is currently focused on improving iOS 17, we may see iOS 16.8 pop up. When it does, you can try out all the upcoming new features as long as you're OK with running beta software on your iPhone.

Rumors about the 2022 iPhone series stirred well before the iPhone 13 models were even released. While Apple remains quiet on the next big iPhone, as it always does, we're seeing more and more leaks and reveals for the iPhone 14 series as we lead up to a likely fall release.

Apple officially unveiled iOS 14 on June 22 at its first all-virtual WWDC. After months of beta testing, iOS 14 hit iPhones on Sept. 16, but that doesn't mean that Apple is done beta testing iOS 14. There will be new features to try out right up until iOS 15 comes out next year.

Greg French talks to us about the different ways to reboot a computer to resolve issues in the computer. The first way is by pressing F8 key while startup after rebooting the system. When you insert a wrong driver for video card or something, sometimes when you boot the computer, it gives a black screen. Now he says you can resolve this problem by rebooting the computer and pressing the F8 key while startup. This will take you to a menu selection where you should select 'Safe Mode' and hit en...

You don’t have to be satisfied with the graphics that are on your computer. There are great graphics out there and with a little time and a screwdriver you can install killer graphics on your very own computer.

In this video tutorial, viewers learn how to turn off the system firewall without admin privileges. Begin by clicking on the Start menu and open he Run program. Type in "system.msc" and click OK. Scroll down the Services list and look for Windows Firewall. Double-click on it and under the General tab, click on Stop. Then click Apply and OK. This video will benefit those viewers who use a Windows computer and would like to turn off the firewall, even if they are not running the administrator a...

In this Software video tutorial you will learn how to use Daemon Tools Lite to mount an image or ISO file. This is a software that takes ISO files and puts them on a fake hard DVD drive. This is really very easy and simple to do and takes practically no time. Go to start > all programs > daemon tools > daemon tools lite. Now the ‘mount n drive manager’ window will come up. Here you click ‘add’, browse to the ISO file and open it. Alternately, you can drag and drop the image in to the ...

How to make your computer run faster is very easy to understand. The steps involved are as follows:

Wouldn't it be great to create a list of all of the songs on your Music Folder and then be able to print it? Wouldn't you love to have a list of files and folders burned on a CD?

Remote desktop in windows is set up with these easy to follow steps. First go to your start menu this is in the bottom left corner of your desktop. In the start menu locate your control panel. In the control panel open up your systems folder. Once this is open click the remote tab at the top right of this folder. In this tab you will have the option to check “allow user to connect remotely to this computer.” From here press ok to exit out of the systems folder.Again click the start menu, navi...

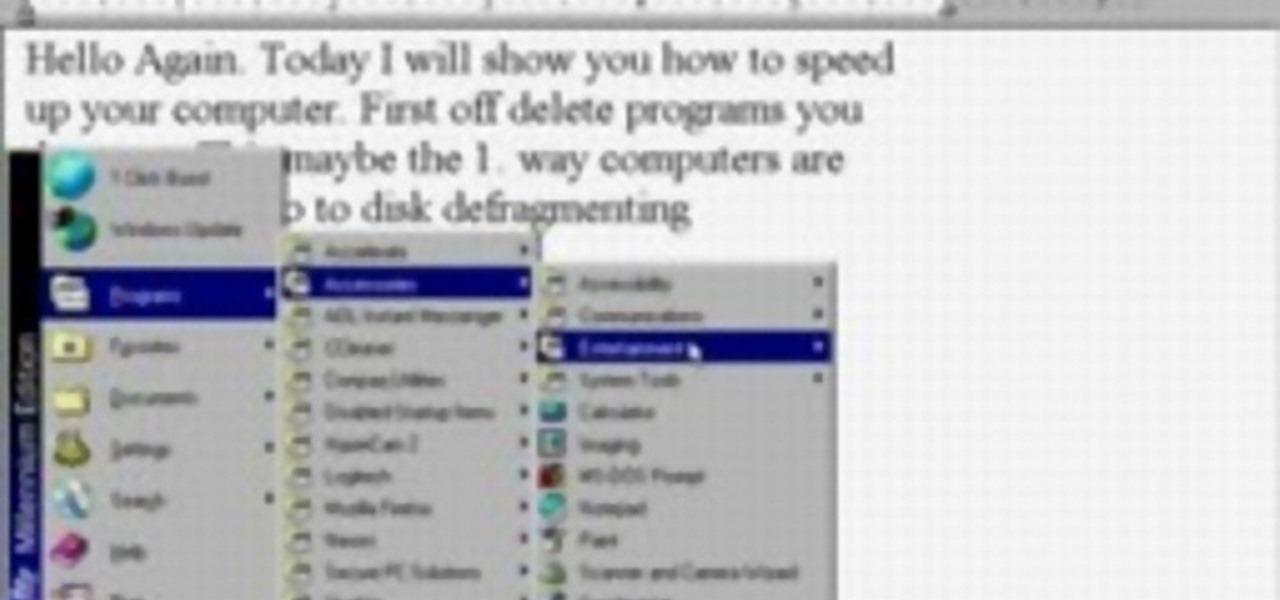
This video shows how to easily record your voice and insert a sound podcast to your WebQuest or webpage using Dreamweaver. It shows how to have the sound play on the same page without auto starting. The tutor initially goes to the Start button and in All programs selects Accessories. Next he selects Sound Recorder from the Entertainment option and records his voice reading out the content of the page. He then saves the file in the folder called websites creating a subfolder in the name of ‘so...

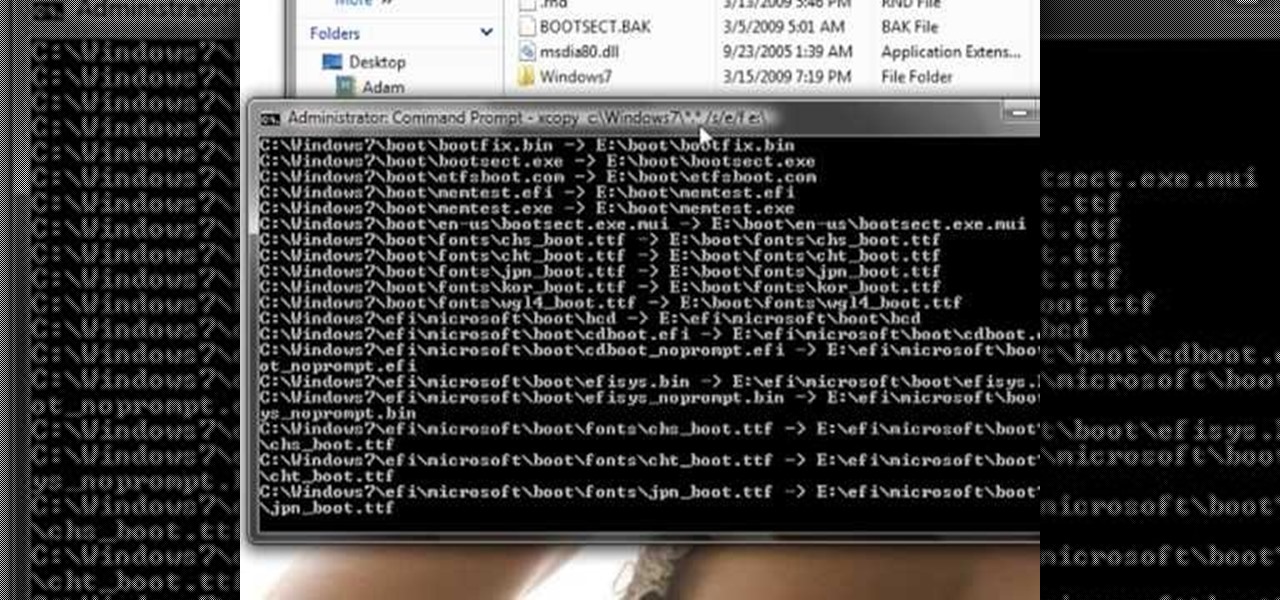
This guide works 100% for Vista & Windows 7, unlike most of the guides out there. The method is very simple and hassle free. Needless to say, your motherboard should support USB Boot feature to make use of the bootable USB drive.

What is a cataract? A cataract is the clouding of that internal lens of the eye which is normally clear. That internal lens helps focus light as it comes through the pupil that when a lens starts becoming a little cloudy, patients sometimes complain that their vision seems a little foggy. There are certain risk behaviors that you can avoid to reduce the risk of getting cataracts. Get professional tips and advice on cataracts in this medical how-to video.

Check out this quick video with Bill Myers showing how to create a 3D box shot or ecover image of a DVD case. Bill uses Trueboxshot but you can use other programs as well.

Watch this how-to video and learn some tricks and hacks that you can do with Google. Google has a pretty good sense of humor, so there are a lot of hidden programs to play around with. Watch this video tutorial and learn how to hack, play tricks, and find Easter Eggs on Google.

A brief video on how to mod Halo 2 for the XBox using the PC programs DOtHalo or H2Edit.

Continuity is an underrated and more importantly, overlooked aspect to multi-cut scenes. Many films, television programs and internet videos forget its importance. So this week, The Shirtless Apprentice give his tips on the subject as he sits down and has a romantic candlelit dinner with continuity.

Have you ever wanted to add animated pictures or GIFs to your website or blog? Two free software programs, GOM Player and GIMP, both allow you make your own GIFs. This tutorial shows you where to get them and how to use them.