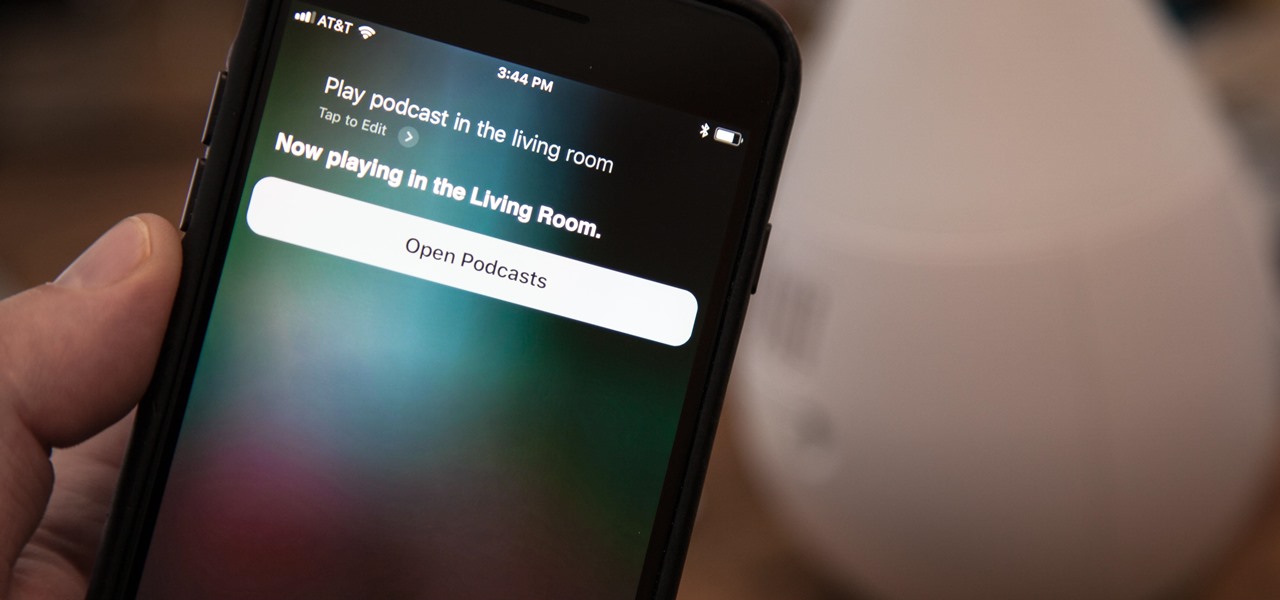
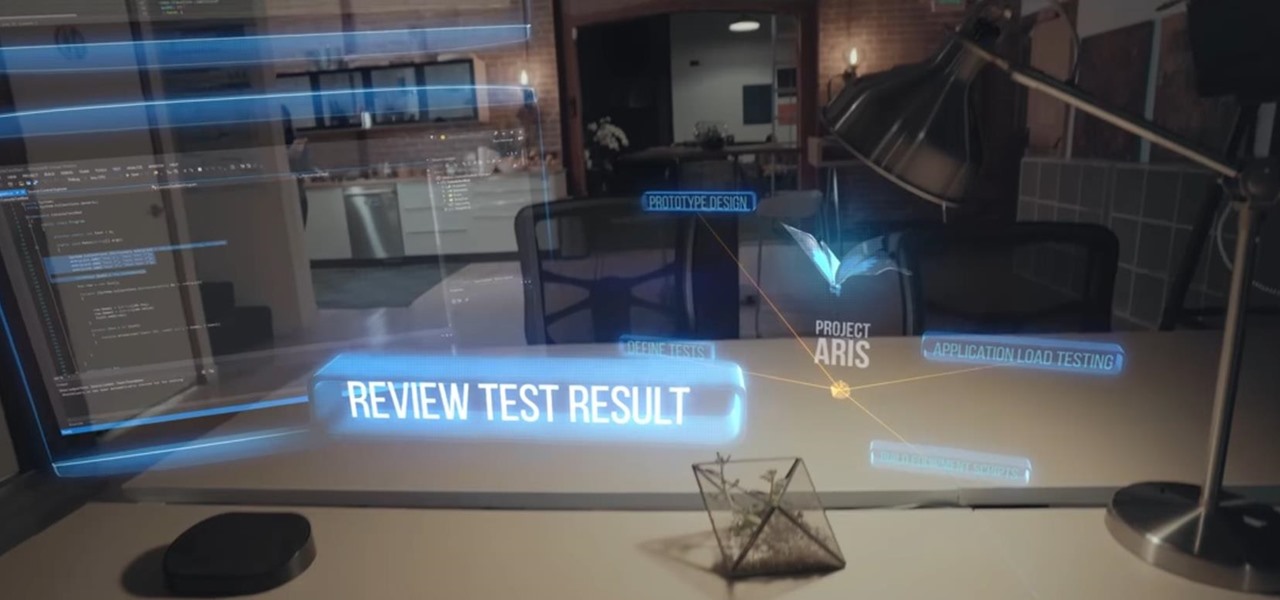
The hype train that left the station years ago has reached its first stop, and now we finally have access to the Magic Leap One, the device many have claimed would revolutionize the augmented reality space at launch. But is that really true?

Luxury automaker Mercedes-Benz has joined the growing list of automakers adopting augmented reality to provide an assist to its manufacturing operations, in this case, via the Microsoft HoloLens.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

On Wednesday, the tech world woke up to fairly shocking news with the announcement that AT&T would be the exclusive wireless carrier for the forthcoming Magic Leap One, as well as an investor in Magic Leap.

When you receive a photo or video from a contact in WhatsApp, after you load it, it's automatically saved to your phone's local storage. That means all received content from WhatsApp is visible to anyone who gains access to your default photo gallery. Luckily, there's a new feature available for the Android version of the app that can prevent this from happening.

Every once in a while, we find ourselves in a predicament where we need an inexpensive smartphone. Whether we're finally upgrading from that feature phone we held onto too long or we dropped our current smartphone, sometimes we need a quick replacement to get back on track. That's where Android One comes in.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

Magic Leap shows up in the weirdest places. Last week, right at the start of World Cup fever, for some reason, the Magic Leap One appeared on a Brazilian television show.

Earlier this week, we told you about the new DreamGlass augmented reality headset from Dreamworld, a company started by a former Meta executive. The device looks great, and the features sound good, but is it worth your hard-earned cash? I recently took it for a brief spin to find out.

Samsung Experience (better known as TouchWiz) can take some time to get used to when you switch to a Galaxy from another Android device. It's a bit heavy-handed with the features, and many consider the UI theme to be a little over the top. Thankfully, there are several stock settings that can dial this back.

To quote MKBHD, cheap phones are getting good. Each year we are seeing manufacturers start to offer more for much less. This not only translates to cheaper flagship phones, but better budget phones. The latest example of this is the Alcatel 3V, which is redefining what you can get at $150.

China-based virtual reality headset maker ANTVR has decided to enter the augmented reality space, and to do so it's launching its headset on Kickstarter. The company claims that its new Mix AR device has a field of view that surpasses the Meta 2, the HoloLens, and others within a smaller form factor and at a fraction of the price. But there's a catch.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

A few long-awaited iOS 11 features that Apple had promised way back in June 2017 have finally made their way to iPhones with the iOS 11.4 update. Aside from finally delivering on those, there's not a whole lot new in iOS 11.4 as a whole, though, there are a few things you'll definitely want to know about.

If you've ever connected your iPhone to a computer before, you know iOS prompts you to "Trust" the computer and enter your passcode to confirm. According to Apple, trusted computers can "sync with your iOS device, create backups, and access your device's photos, videos, contacts, and other content." That's a lot of permissions to hand off, especially if the computer's not your main laptop or desktop.

It turns out that the government of Saudi Arabia has managed to do something last month's Game Developers Conference couldn't — give us a few new glimpses of the Magic Leap One being worn by someone other than Shaq.

MLB.TV is a great service that lets you watch most Major League Baseball games in North America, as long as you're a subscriber, of course. While I personally love it, blackouts can ruin the ability to watch my favorite teams. Fortunately, MLB At Bat Android users have an easy way to bypass blackout restrictions — and with no root required.

As the week of the Game Developer's Conference hits the mid-point, we've already had some major announcements hit the AR space. The specific timing of these announcements are thanks in part to a conference within a conference called VRDC, aimed at VR, AR, and MR developers. And while the week is hardly over, the announcement that is still having a big effect on the developer population is the reveal of the Creator Portal for the long-awaited Magic Leap One device.

Setting up a new Android phone can be a pain. Although Google has some automated features, it does not restore everything. When it comes to transferring certain types of data like files and SMS logs, it's even trickier. By following our steps, you can be sure that you all your data will follow you to your new device.

If you installed Android 9.0 Pie, you might have enjoyed trying out some of the new features in the latest version of Google's OS. However, change isn't always a good thing, so you might be wishing you could downgrade back to Oreo right about now. Good news — you can.

With the S9 and S9+ upon us, you maybe wondering if it's time to retire your aging Galaxy and either sell it or do a trade-in to get Samsung's latest flagship. Before you do, however, it's important to make sure that all its components — most notably the sensors — are working fully in order to avoid potential headaches.

After two years of poor sales, LG decided to shake up its mobile division. New executives are at the helm, and changes to their flagship lineups are already underway. Specifically, the V series is expanding, as LG announced the second new device in the series, the LG V35 ThinQ.

Last year, OnePlus released not one but two excellent flagship devices with the OnePlus 5 and 5T. While the 5T released sooner than expected, it brought some worthwhile upgrades, such as a near bezel-less display and a much-needed camera enhancement. Now, that the OnePlus 6 has arrived, it's time to see what OnePlus has in store for 2018.

Because of quirks with cell radios and how Android was previously set up, custom ROM support for Galaxy S phones has been sparse these past few years. It's been almost nonexistent for US customers, while international users would see some ROMs. Thanks to Android Oreo's Project Treble, this will all be changing soon.

Samsung and Apple are the two titans of the mobile phone industry. After Apple deployed the iPhone X in November, Samsung had three months to brood until Mobile World Congress, where they unveiled the Galaxy S9. Now that both phones are out, it's time to put them head-to-head.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay secure, there are a few steps you can take.

The augmented reality industry made great strides in 2017, but its apex is not even in sight. In terms of software, augmented reality is approaching meaningful mainstream awareness, thanks mostly to Apple and ARKit. Meanwhile, on the hardware side, AR is very much in its infancy, with headsets mostly limited to enterprise customers or developer kits and the majority of smartphones lacking the sensors necessary to achieve much more than parlor tricks.

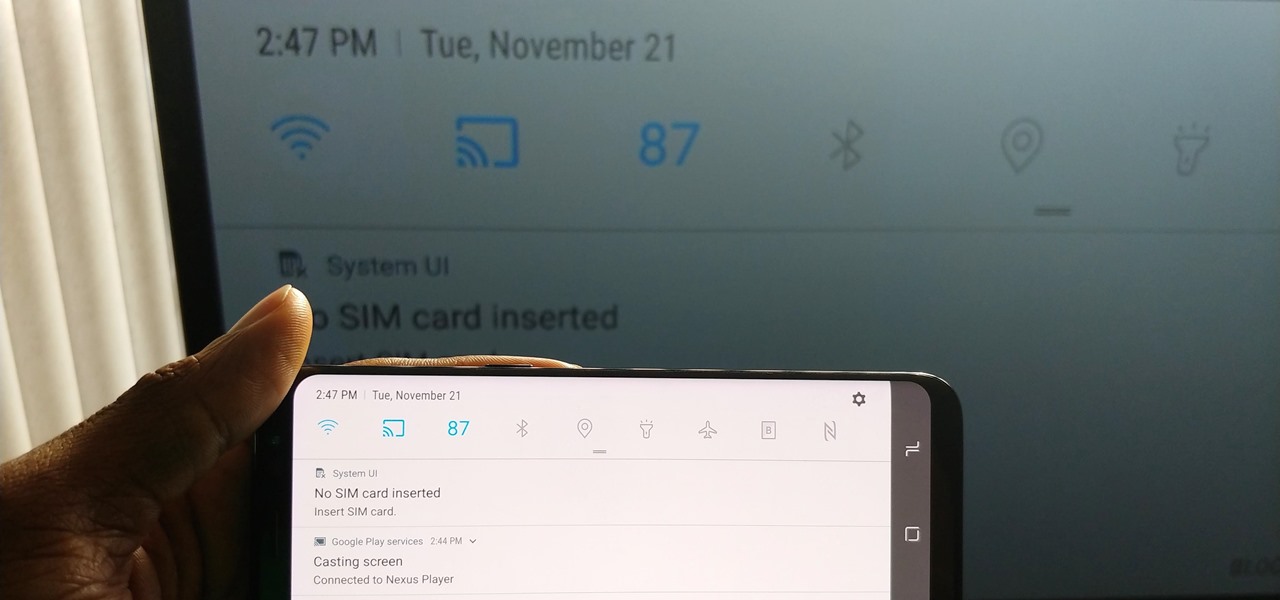
Android's Quick Settings menu gives you easy access to certain actions from any screen, but the tiles available are largely dependent on your phone's OEM skin. For instance, the Google Cast button that can cast your entire screen has been exclusive to Nexus and Pixel devices, even though other phones have the requisite software to use it. Fortunately, there's a way to add it on any device running Nougat or higher.

Up until now, experiencing augmented reality through Vuzix's next-generation Blade 3000 smartglasses would have required a trip to a tech conference where the company has an exhibition booth.

So after being teased last Christmas with an email promising that the Meta 2 was shipping, nearly a year later, we finally have one of the units that we ordered. Without a moment's hesitation, I tore the package open, set the device up, and started working with it.

The Pixel 2 and Pixel 2 XL were built by different manufacturers. This is pretty common knowledge among Android fans at this point — Google's smaller Pixel 2 was built by HTC, while the larger Pixel 2 XL was built by LG. What would the Pixel 2 XL look like if HTC had followed through and delivered on the larger phone for Google? Today we have some answers.

Razer, the company known for PC peripherals and laptops, is joining the smartphone industry with a new device. Rumors have been swirling since they announced an event on November 1 at 4 PM EDT, but now, we have our best look yet with a leaked promotional video before the actual announcement.

If you're in the market for a new smartphone, you'll likely scan spec sheets and read reviews of the top phones, compare display size and technology, RAM amount, and processors. But one factor that is often overlooked is cell reception — and for T-Mobile subscribers, there's only one device that has flagship specs and an exclusive antenna that will actually improve your signal.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn a Raspberry Pi into a router running through PIA VPN, which will ensure every connected device gets the VPN treatment.

While ARKit and ARCore are poised to bring AR experiences to millions of mobile devices, one company is poised to anchor those experiences anywhere in the world with just a set of geographic coordinates.

After learning that you'll need to spend at least $74 on a special charger and a USB Type-C Lightning cable to enable fast charging on the new iPhone X and iPhone 8 models, you may be wondering why you can't just use the standard Lightning cable. While we can't answer why Apple didn't include the USB-C cable in the box with their new phones, we can explain why you need USB-C to enable fast charging.

Apple officially unveiled the long-awaited iPhone X, its tenth-anniversary edition iPhone, on September 12. With preorder and release dates just around the corner, you'll want to brush up on all things iPhone X to make sure you get your hands on one as soon as possible. After all, preorders start Friday, October 27.