One of the main goals of Google Wifi (and Nest Wifi after it) is to make managing your internet connections as simple as possible. A great example of this is how easy it is to prioritize one device and allot it more bandwidth when your network is bogged down with other traffic.

While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

Did Google CEO Sundar Pichai kill Google Glass for non-enterprise users? That's the obvious first question following news that non-enterprise Glass users will no longer have access to Google's core apps after February 2020.

Apple's latest updates to its operating systems add another security feature to its Find My service, so you have an even better chance at locating your lost iPhone, iPad, or Mac should it ever happen. As long as you have the option enabled, you can leverage other Apple users' devices to find yours on the map.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

Returning to the spotlight after its debut at last year's CES, augmented reality smartglasses maker Rokid is back with a new update.

One of the main reasons Authy was able to top our list of the best two-factor authentications apps was its ability to transfer access to a new device. This feature ensures that whenever you get a new phone, you don't lose all your tokens. However, if the process is done incorrectly, you can leave your account vulnerable.

As Android device partners ship new products, Google has been diligent in its efforts to ensure that users can enjoy ARCore apps once they boot up their new toys.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

A tethered version of the Vuzix M300 smart glasses, developed to pair with wearable computers from Toshiba Corporation, is expected to be available by the first quarter 2018, if not sooner.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

Cyanogen, Inc., the for-profit company that spun off from its CyanogenMod roots several years ago, has announced that they're shutting down all of their services. The company's impending demise shouldn't directly impact many Android users, but the announcement does have one major repercussion: The servers that used to host the popular CyanogenMod custom ROM have now been shut down.

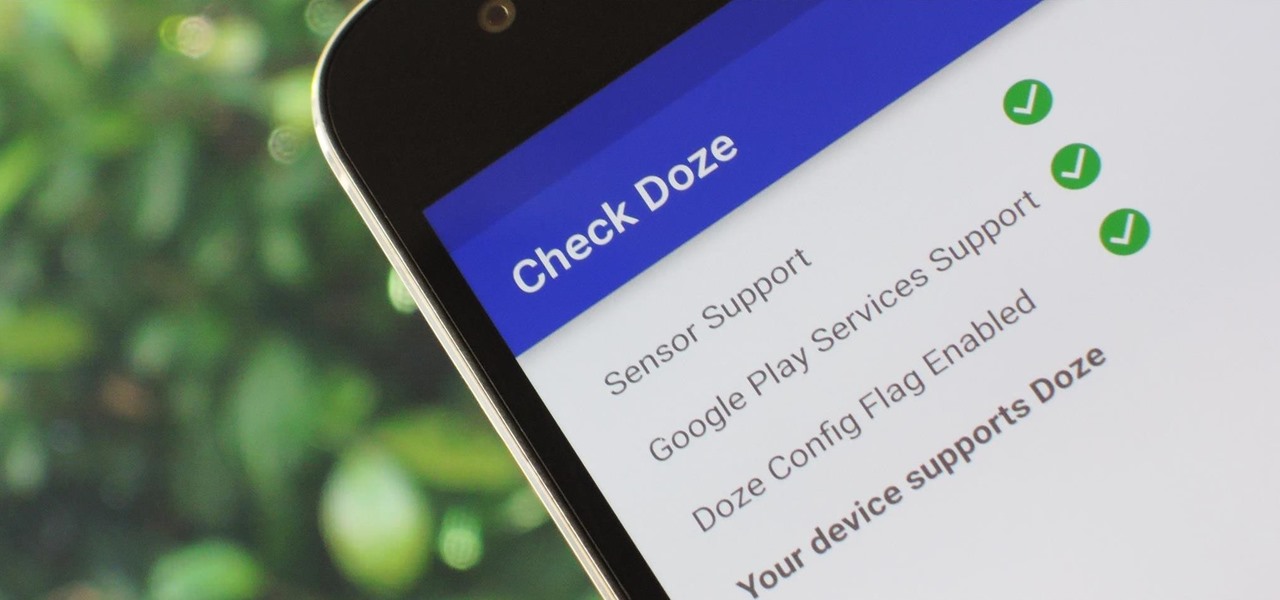
Out of all the new functionality introduced alongside Android 6.0 Marshmallow, a battery-saving feature called Doze Mode has been the biggest hit. Essentially, Doze waits until your device is laying flat and still, at which point it triggers an aggressive battery-saving mode that drastically increases standby time on your device.

Google has a lesser-known Android app called Device Assist that might just be one of the most useful programs the company has ever published. It offers interactive guides and general tech support for Android, plus it can diagnose your device and help you fix any issues it finds.

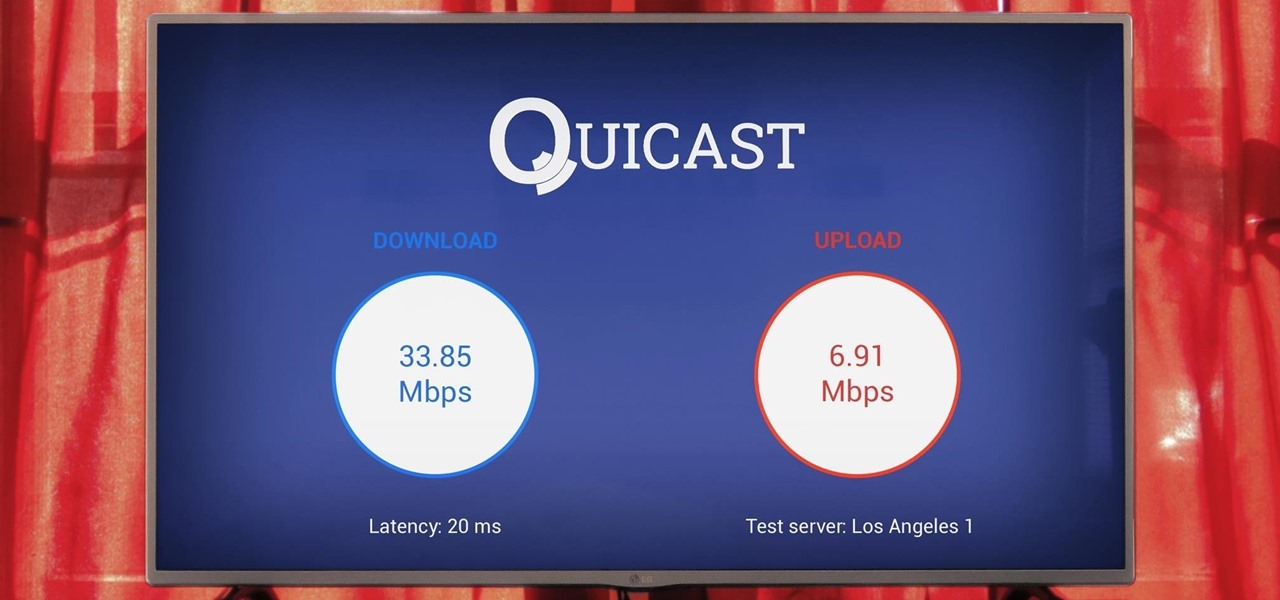
The Google Cast feature that serves as the primary interface for the Chromecast and comes bundled with Android TV devices like the Nexus Player is a marvel of modern technology. But as these things go, troubleshooting issues can be difficult with something so groundbreaking, especially when you consider that there are two parts to the equation—the casting device (your phone, tablet, or computer) and the receiver.

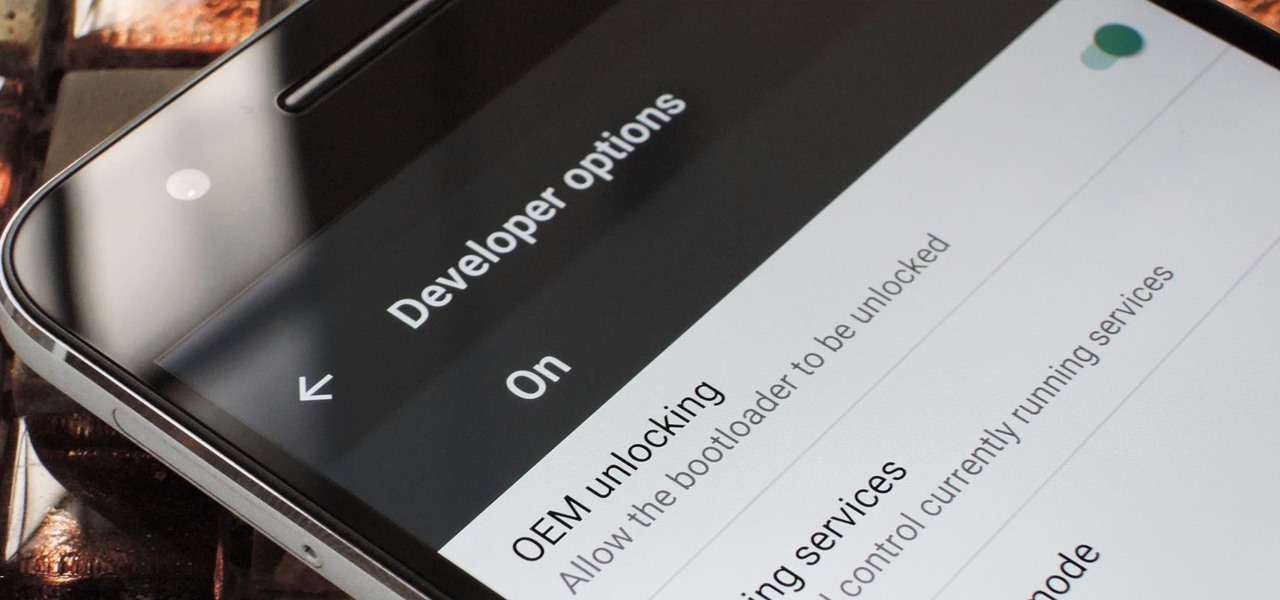
If you've ever rooted an Android device in the past or installed a custom recovery, you're surely familiar with the term "unlocked bootloader." But if all of this sounds like gibberish to you, some major changes in Android have made it to where you should definitely get familiar with the concepts.

With Touch ID on iOS devices, it's a little more difficult to lock yourself out. However, it can still happen if you don't use it, have a busted fingerprint scanner, or use an older device that doesn't have Touch ID, which means you're passcode dependent (unless you have zero lock screen security).

If you're completely new to Android, you're in for a treat with all of the software tweaks and customization options that your smartphone or tablet offers out of the box. But if you really want to take things to the next level, the ability to mod your device expands exponentially when you're rooted.

Cheap Chinese knockoffs have been around for ages, but recently, skyrocketing demand has led to a massive influx of counterfeit smartphones. Sellers on Craigslist seem to have no trouble getting ahold of these fake devices, then passing them off as the real deal and turning a solid profit before vanishing into thin air. This type of scam tends to happen even more frequently after Apple launches a new iPhone or Samsung debuts a new Galaxy.

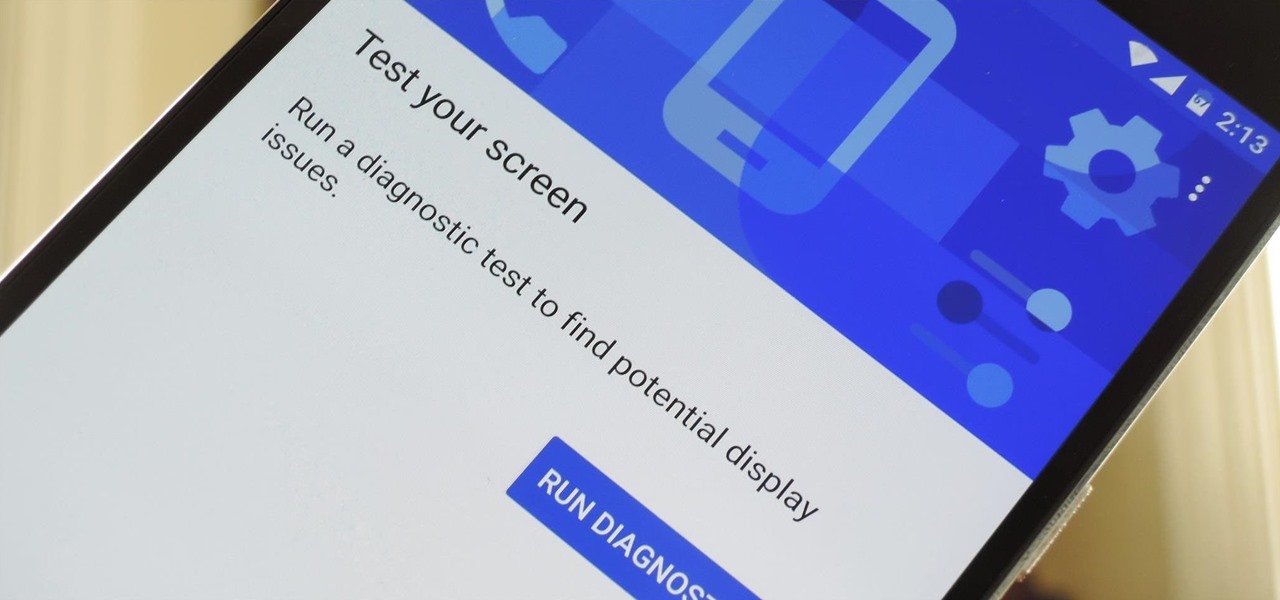
If you ever need help troubleshooting an issue that you're having with your Android device, one of the most useful tools you have available to you is the screenshot. Essentially, this is an exact copy of everything that is showing on your screen at any point in time, which you could use to capture the issue you're having, then share the screenshot with your tech support.

Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is just one of the many hacks we will explore in the series.

One of the coolest features in modern smartphones is their Bluetooth connectivity. This is how two digital devices can communicate with one another—sending data like your phone call audio or your favorite song—all while using up minimal battery life.

Whether you are sending your phone in for repairs or finally selling it to upgrade to a new flagship, you are going to need to make sure all of your personal data is removed from your device.

Last week, NowSecure security researchers revealed that nearly 600m Samsung mobile devices are vulnerable to a type of MitM attack.

We previously showed you how to make your Android's LED notification light dance to music, but the app itself was limited in customization options, the devices it worked on, and the music apps and services it worked with. Now we'll be showing you a similar app that supports more music services and lets you select which colors will display through the LED.

Apple's Touch ID, introduced on the iPhone 5S, has definitely made my life a little easier. Not only can I unlock my device, I can use the tech to log in to websites, make purchases through iTunes, and buy groceries at Walgreens using just my fingerprint. Still, as awesome as Touch ID is, it's pretty limited as to what it can do on native apps.

With only a month left until Samsung's highly-anticipated Galaxy S6 and Galaxy S6 Edge are released to the general public, it's only natural that some of the devices' features slowly trickle out, like Edge notifications, the new Smart Remote app, and, of course, wallpapers.

These days, using the power button to lock your Android seems a little old-fashioned. Thanks to third-party apps and mods, you could seamlessly lock your device using a double-tap, a swipe, and even gravity, or you could just throw it in your pocket, all of which help prevent additional wear and tear on your power button. Now, we've got another method for you—just shake.

UPDATE 11/17/15 The Xposed Framework now officially supports Android 5.1 through 5.1.1 Lollipop devices as well. Everything will still work the way it has with Android 5.0 through 5.0.2, but there are a separate set of files for the newer Android version. I'll cover both below, but make sure to download the proper file for your particular version of Android.

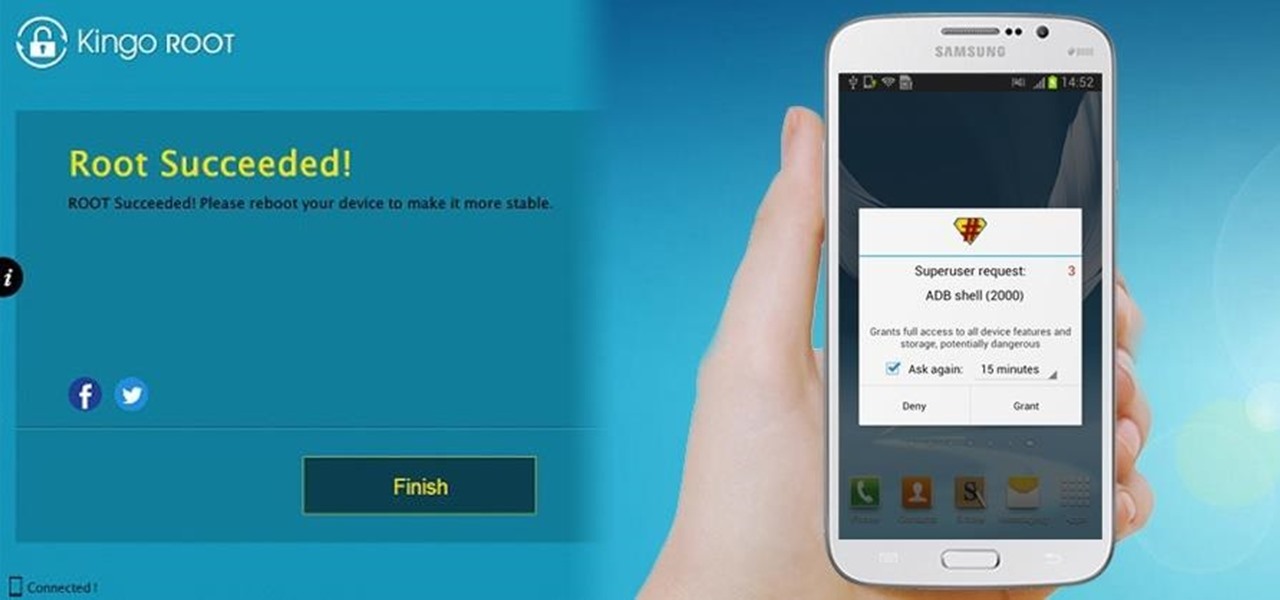
To Android users, especially advanced ones, rooting their phones or tablets is becoming a necessity. Rooting Android could be complicated, if you do it all by yourself, even with a step-by-step tutorial. However, what Kingo Android Root offers you is a true one-click experience when rooting your Android.

Unless you're sporting an LG G3 or a mod that allows tap-to-sleep and/or tap-to-wake functionality, you're probably hitting the power button to sleep and wake your device. But that button may be awkward to hit, may be worn down, or may just stop working due to a manufacturer's error or a device drop. In any case, it is possible to end reliance on the power button, opting instead for a simple swipe gesture that will instantly lock your device.

I may not be a parent just yet, but I've dealt with enough worrisome mothers to know that keeping a watchful eye over your child is of the top-most importance. Since most people cannot afford to stay right by their child's side 24/7, developers are always looking for ways to make the pain of stepping away a little less stressful for parents.

I don't know of a pain greater than of the one felt after cracking the screen of your phone. After I managed to crack my screen, rendered unusable, I immediately began to panic as to how I was going to recover all of the photos, videos, and documents stored on my device. After a few hours of searching, I came upon a thread by Mohamad Sabra that showed exactly how to alleviate my problem.

Without a comprehensive root method for all Android phones and tablets, a device-specific approach is needed. And since we always cover new rooting methods for all the popular phones here at Gadget Hacks, we've built this always-updated guide to rooting many mainstream Android devices.

Google's Android Device Manager makes it extremely easy to track down your phone or tablet, but while it's simple to set up and use, it does require your device to have an active data connection, which can be an issue in some areas.

It happens to everyone: you set a lock screen password in a hurry and cannot remember it the next day. To unlock your device again, you need to reset the password (or PIN, pattern, etc). There are two official methods of doing this.

Welcome back, my aspiring hackers! In recent tutorials, I have made reference to the name and location of the Linux devices in the file system, such as sda (first SATA or SCSI drive). Specifically, I have mentioned the way that Linux designates hard drives when making an image of a hard drive for forensic purposes.

Audibly, from iOS developer Nick Frey, allows you create playlists and sync your music across other iOS devices. Like the Samsung-exclusive Group Play or the older Seedio app, you can connect a slew of compatible devices to create a surround-sound stereo of sorts when playing your music.

It started in Australia, and now seems to have made its way statewide—hackers are remotely locking iOS and Mac devices, holding them for a $100 ransom. Users awoke to the loud "lost iPhone" ringtone, with a message on their lock screen stating that "Oleg Pliss" has hacked their device, and that "they" will unlock it after being sent $100 through PayPal.

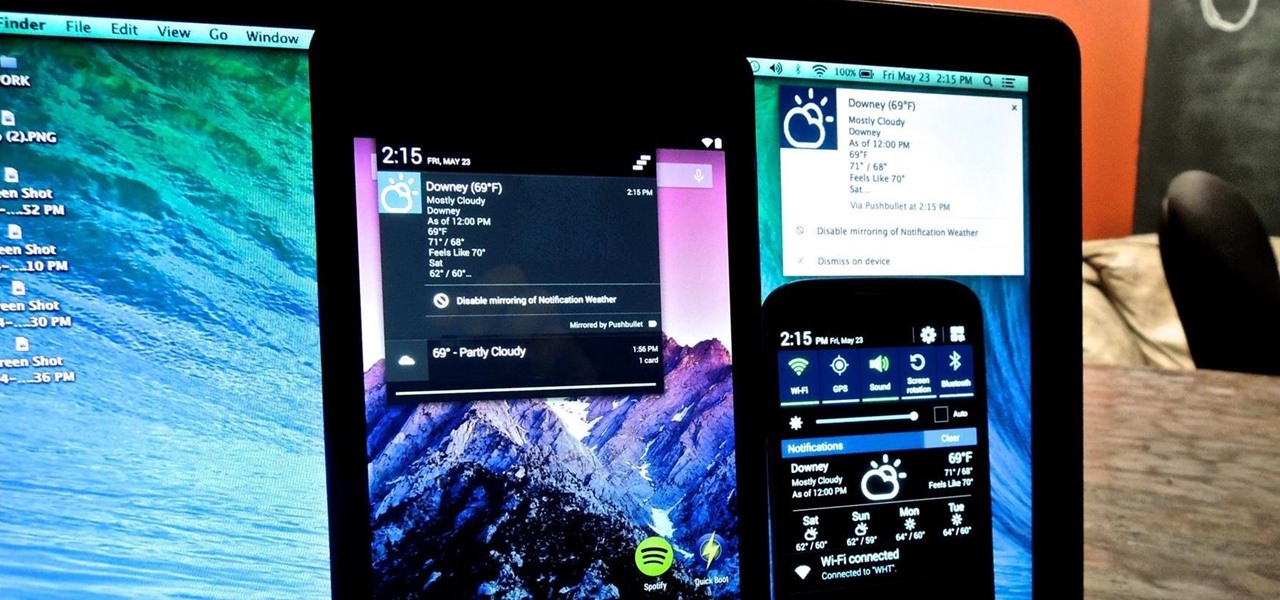
We're not always near our phone, so Pushbullet made it easy to get your phone's notifications straight to your computer, like calls and text messages. But with their latest update, you can also sync alerts with other Android devices using their new cross-device mirroring feature.