A common problem on bumper covers is that the tabs that attach the bumper to the car get broken. This is critical, as this is what secures and aligns the bumper cover. Many times, a broken tab is all that is wrong with the bumper cover. With the cost of these plastic parts $200 to $700, the replacement cost can break the bank.
Free trials are a great way to test out products before a purchase, or simply for the exploitation of free stuff for that limited amount of time. Some trials last a few days and some last even a month or two, but no matter what—these trials will always expire. But like most things in life, there is a way to get around such limitations.

Over the past few years, indie game developers have gathered together to release their products in the widely popular Humble Indie Bundle, a collection that gamers can purchase for whatever price they want. It's a win-win for both. Developers get more exposure for their games, and customers get tons of games for whatever they could afford. Heck, charities even get a little piece of the pie.

In the first part of this two-part guide, I covered cutting, grooving, beveling, making holes, and stamping/tooling. I hope you enjoyed that part, because we're pushing the accelerator to the floor and moving ahead at full speed!

Timely costumes for Halloween are awesome—especially really obscure ones—because they're indicative of social awareness. In 2010, I remember seeing several Chilean Miner costumes, which I thought were great. 2012 brings new stories, new characters and more importantly...new Halloween costumes.

What I'm going to do in this tutorial is, as the title implies, teach you how to make nearly anything look like metal. This can especially come in handy in Steampunk, as most of us don't have the ability to machine brass. We do, however, have access to wood, PVC, and spray paint. Not to mention that, as a costumer, I can speak from personal experience when I say that things made of brass are really, really, really heavy!

If you don’t have any little children to blame for an inadvertent or misguided app, book, or music purchase from Apple, you might still have a fighting chance. Apple has a very strict return policy, specifically stating that all sales and rentals of products are final for purchases made in the iTunes Store, Mac App Store, App Store, and iBookstore. But if you play it carefully and do a little digging, a return and full refund may still be possible.

RFID chips are everywhere. They're in passports, credit cards, and tons of items you've bought in the last 5 years or so. Big retailers like Walmart started using tracking products with RFID as early as 2004, and today, they're used in everything from mobile payments to hospital record systems. Chances are, unless you're a hermit (in which case you wouldn't be reading this anyway), there's an RFID tag within a few feet of you. Photo by sridgway

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...

It’s called Urophagia—the art of consuming urine. There could be any number of reasons for having the desire to drink your own urine (or somebody else’s). There’s the so-called term “urine therapy,” which uses human urine as an alternative medicine. In urine therapy, or uropathy, it’s used therapeutically for various health, healing, and cosmetic purposes. There’s also those people who drink urine as sexual stimulation, where they want to share every part of each other. And then there’s the o...

The engine of your car isn't something you'd expect to clean regularly, but it can get dirty. This video will show you how to use several products in order to clean your Suburban's engine, or any engine for that matter.

Learn how you can achieve this purple and white eye shadow look with this how to video. This tutorial uses MAC cosmetic products.

Learn how you can achieve this gold, bronze and dark red brown eyeshadow look, with this how to video. This makeup tutorial uses MAC cosmetic products.

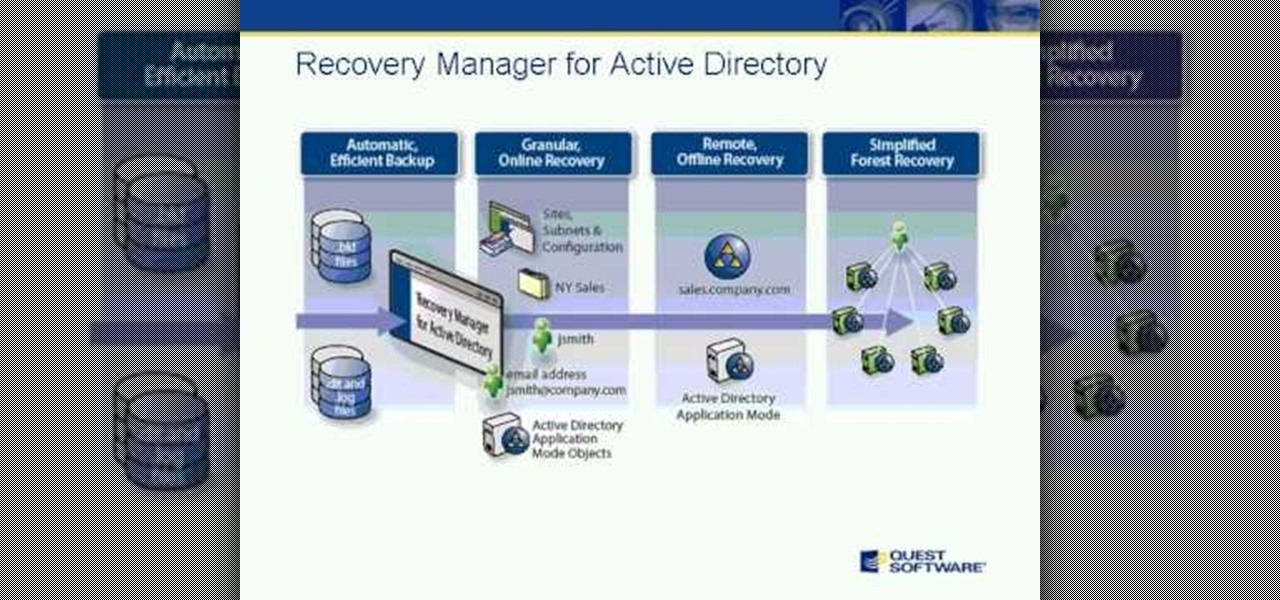
View our webcast to learn about the advantages of using a comprehensive Active Directory recovery solution -- and view a product demo. With Quest Recovery Manager for Active Directory, recovery time can be reduced from hours to minutes!

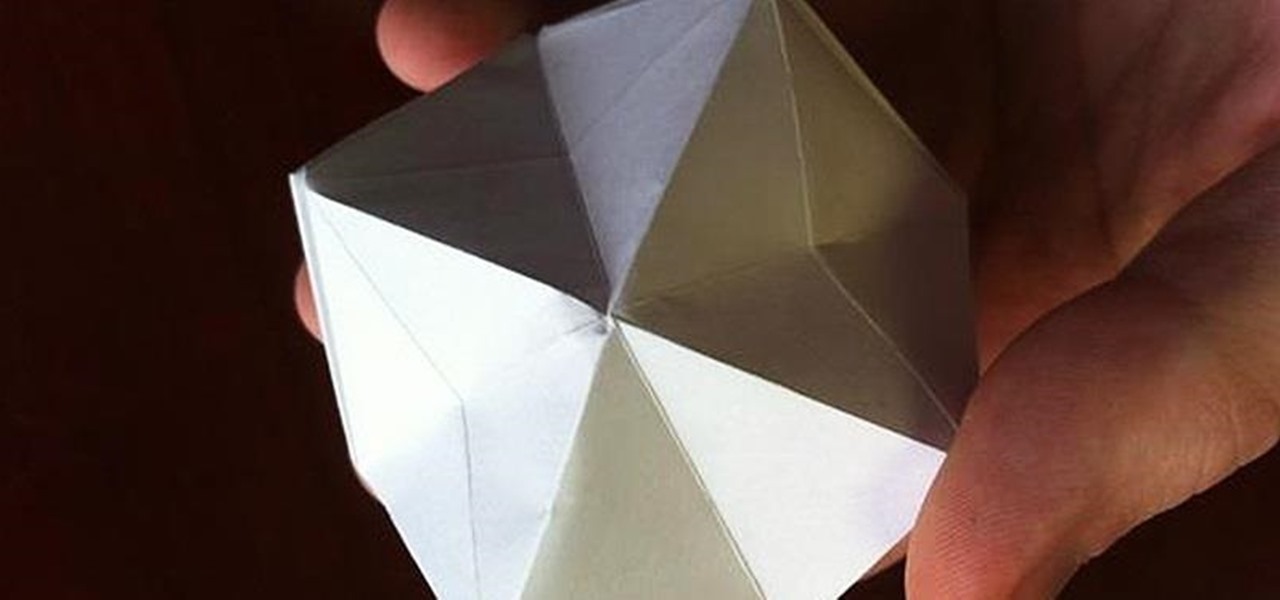
One of the most popular and basic origami geometric shapes is the "water bomb," which is a simple inflated cube. With a few extra folds and only a minor shift in approach, a more complex geometric shape can be achieved.

What's the easiest way to keep track of your website passwords? Maybe in a password-protected document on your computer? Makes sense.

In this video, viewers learn how to use foil to apply patterns on nails. Viewers learn how to create great metallic designs. Other nail art products can be used with the foil to create even more sparkly nails! This video lists all of the required materials. The materials required include: foil, foil adhesive, base coat, nail varnish, top coats, and optional nail gems. The video provides easy step-by-step instructions that allows viewers to easily follow along. This video will benefit those vi...

This is a Halo Interactive Strategy Game 'Tabletop' tutorial. We've seen this before. It's like Warhammer, but for Halo. With an accompanying DVD that's more Nightmare than Bungie. So, is this a good idea? With Halo Wars on the way and better board games on the market we'd have to say no, but then, who are we to tell hardcore Halo fans what they can and can't blow their money on.

In the great smartglasses race, component makers, such as those that supply the crucial waveguide displays that make visualization of virtual content possible, have a vested interest in pushing the industry forward in order to ship units.

With everything the last year has thrown at us, the odds are good that you've had to start working from home, complete with all-new challenges both for you and the technology you use.

Just as the augmented reality industry grows, so too does the segment dedicated to creating experiences for the tools becoming available.

To assist developers and researchers in their efforts to create apps and services for automobiles, Volvo Cars has launched a new Innovation Portal with useful new tools and assets.

The year 2021 is already promising to yield a number of major shifts in the augmented reality landscape, and Snap is signaling that it has every intention of being an aggressive part of that narrative.

There's a lot of talk about 5G these days. You might even think your iPhone is 5G-ready, since, well, it says so right in the status bar. 5G E, right? Sorry to burst your bubble, but no iPhone is capable of connecting to 5G networks yet, no matter how much you pay for that 11 Pro.

It feels like just yesterday Apple unveiled iOS 13 to the world, introducing game-changing features like system-wide dark mode and enhanced editing tools in Photos. But WWDC 2020 is rapidly approaching, which means iOS 14 is as well. As it turns out, we don't need to wait for an official announcement to get an idea of what new features and changes are coming to iPhone this year.

Facebook recently hit a snag in its quest to take augmented reality face effects to its millions of users.

Beta testing Apple's mobile OS has never been more interesting. After eight seeds of iOS 13.0, Apple unexpectedly released the first beta for iOS 13.1, a whopping 23 days before iOS 13.0 made its public debut. Since 13.1, however, we haven't had any betas to sink our teeth into. That is, until now, as Apple just released the first developer beta for iOS 13.2 today, Wednesday, Oct. 2.

What if, back in 2013, Google Glass had launched not as a Star Trek Borg-like eyepiece, but as a pair of seemingly normal shades, with the augmented reality lens and camera hidden within the frame?

This week, while Apple was the subject of thinly sourced reports that it had canceled development of its oft-rumored smartglasses, the Cupertino was actually laying the foundation for its AR hardware future with a new initiative focused on mentoring Chinese developers in mobile AR development.

While Apple's smartglasses development reportedly moves forward behind-the-scenes, the company continues to build on its AR software foundation in its mobile ecosystem with further iterations to its ARKit platform and the introduction of new AR development tools.

In recent months, the Magic Leap One has frequently tied promotions to groundbreaking entertainment properties, but the latest may be the startup's biggest coup yet.

During Huawei's P30 smartphone launch event on Tuesday, the China-based company unveiled a surprise addition to its line-up: smartglasses.

Apple CEO Tim Cook has said that augmented reality (or, AR for short) will "change everything." But what, exactly, is augmented reality?

Every step in the evolution of computing brings an in-kind leap forward in user input technology. The personal computer had the mouse, touchscreens made smartphones mainstream consumer devices, and AR headsets like the HoloLens and the Magic Leap One have leveraged gesture recognition.

Despite its status as a hot commodity amongst emerging technologies, the augmented reality industry is not immune to the ebbs and flows that occur in every industry.

If you ever looked at Apple's Peek and Pop feature on Safari and said "I want that," Google has kinda-sorta delivered. A new hidden Chrome feature brings similar functionality to Android despite the lack of 3D Touch, and while it's a bit redundant and nowhere near as polished, it does make navigating the web easier.

While there were a ton of features added in iOS 12, one that Apple had been bragging about since June was nowhere to be seen. Until now. With the iOS 12.1 update, your iPhone gets a huge feature, as well as a few smaller ones to boot.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

By now, you already know that the Magic Leap One ships with an array of apps to immediately get you accustomed to operating in your new spatial computing reality. The first one we're going to focus on is Screens, an app we told you about previously, but only now have managed to try for ourselves.