Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

So cute, so furry, and so chock full of parasites. While raccoons are fun to watch, they are neither friendly nor clean — and they can make you sick in more ways than one.

OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time-consuming. OpenVAS is also helpful for administrators who need to identify potential security issues on a network.

Nintendo's Super NES Classic system, a pint-sized version of the iconic Super NES from the '90s, is highly anticipated in the gaming world. The retro system has already met its fair share of controversies and it's been a long journey to preorder. Finally, the Super NES Classic is officially available for preorder, but it's selling out fast.

The USB Rubber Ducky comes with two software components, the payload script to be deployed and the firmware which controls how the Ducky behaves and what kind of device it pretends to be. This firmware can be reflashed to allow for custom Ducky behaviors, such as mounting USB mass storage to copy files from any system the Duck is plugged into.

Like humans, cats can suffer infections caused by ticks, and too often, the disease is fatal. Learn about tickborne diseases that affect cats and what you can do to protect Fluffy from an untimely demise.

Bed bugs are brown and creepy. Could you spot one in your hotel room? A new study reveals most people are freaked out by bed bugs, but only about 35% could identify one.

Apple's been hard at work adding new features and finishing touches to iOS 11, and there's evidence of it everywhere. But there's one place where these changes are more noticeable than perhaps anywhere else — Safari.

While it is easy to create and maintain your compost pile, you can enjoy it more knowing a few basic tips.

Microsoft has always been pretty good with customer service, especially from the developer's end point. In recent years, since Satya Nadella took over as acting CEO, the level of customer and developer care has become something much more. This software giant has gone out of their way to learn about what works and what doesn't and to adjust.

The '90s were a great decade to be alive. Before the internet became a high-availability service, we were untethered from the bombardment of media present in today's culture. Children ran through the streets with levels of physical exertion beyond what's required to capture fictional creatures found in Pokémon GO. However, there were some video game consoles that kept kids indoors, such as the Game Boy, SNES, and more importantly—the first ever PlayStation.

You can get eggs and high-quality compost from backyard chickens—but you can also get Salmonella.

Exposed to hormones, pharmaceuticals, and other chemicals, the beautiful wild fish in Canada's Grand River have taken on some pretty odd characteristics—they're turning into females. A long-term study suggests using bacteria to manage polluted water could turn the tide for feminized fish.

The search for the causative agent of colony collapse—the mass die off of honey bees throughout the US and Europe—has escalated with increasing confusion lately. Everything from pesticides and stress to viruses and mites have been implicated, and some researchers think that many of these environmental factors work together to take down hives.

And so it begins... CES 2017 is upon us! This is a very exciting time for those who are looking out for the newest innovations and releases from the world of technology. I said this was going to be a fun week, and here we start it with a bang from smartglasses developer Osterhout Design Group (ODG).

Reading through various internet forums, it certainly sounds like the Google Pixel and Pixel XL are attracting more iPhone users than any of Google's previous Nexus devices. The sales figures seem to back that up, too, as the Pixel is outpacing last year's Nexus 6P, and pre-order demand has exceeded Google's expectations, causing delays in shipments. (We reached out to Google but they wouldn't give us any specifics on sales numbers or numbers of switchers.)

Google is on a mission to bring a better messaging experience to Android users. We've seen them try and fail over the years with various messenger apps, but this time, they're taking a different approach by working with industry leaders to create a new messaging standard. The result is RCS Universal Profile, or simply Chat, and it's finally catching on.

Harry Potter fans got a treat last week when Pottermore, a site created by Harry Potter author, J. K. Rowling, released a test that let users learn what form their Patronus protective charm would take.

An average user's smartphone tinkering doesn't go much further than taking their phones out of the box, signing into their account, and installing apps. But some of us want more functionality and customizability than the basic experience provided by Android and iOS.

Starbucks last big hit was definitely their Vanilla Sweet Cream Cold Brew, which became a permanent menu item—not just a summer fling—on May 31, 2016. It's the perfect blend of 20-hour cold brew and vanilla sweet cream; The result not only tastes great, but the cream makes is visually mesmerizing as it floats down through the brew.

If you spend a lot of time reading about food, chances are you've heard about bone broth. It's all the rage these days, from high profile chefs like Marco Canora building menus around it, to celebrities like Salma Hayek using it as self-prescribed beauty regimens.

"It just ticked me off," he said. In March 2011, Neil Singh paid $50 to back the Hanfree iPad stand on Kickstarter. The project was funded at $35,000, but production stalled, and the delivery estimates kept getting pushed back.

Welcome back, my tenderfoot hackers! Generally, you will want to perform a vulnerability scan before doing a penetration test. Vulnerability scanners contain a database of all known vulnerabilities and will scan your machine or network to see whether those vulnerabilities appear to exist. If they do, it is your job to test whether they are real and can be exploited.

One of our favorite kitchen items, hands down, is a good old-fashioned wooden spoon. It's practical, versatile, and can last for decades if cared for properly. There are specific ways to nurture wooden utensils in order to keep them from cracking and to help them maintain their glossy sheen.

Welcome back, my neophyte hackers! In the world of information security, the most common intrusion detection system (IDS) you will ever encounter is Snort. As you probably already know, an IDS works similarly to antivirus (AV) software on your desktop; It attempts to identify malicious software on your network and warns you of its presence.

Make delicious candy for Easter from the comfort of your kitchen with copycat versions of your favorite classics: Marshmallow Peeps, Cadbury Creme Eggs, Reese's Peanut Butter eggs, Almond Joy bars, and chocolate bunnies. The best part is that you get your sugar fix without the preservatives.

A slow cooker can be both your culinary companion and your go-to gadget in the kitchen. That's right: the idea of slow cooking is no longer for Southern housewives or purveyors of the Ladies' Home Journal anymore. The times, they are a'changing!

Making sure you have the best gallery app available for your Android device used to be as easy as just installing QuickPic. But late last year, Android's top photo-viewing app was sold to a company who is notorious for permission spamming, so QuickPic quickly lost everyone's approval.

Everyone and his mother (and grandmother) has a chocolate chip cookie recipe that he swears is the absolute best recipe, guaranteed to produce a chocolate chip cookie so good it will make you weep with joy. The problem with that is that everyone—relatives included—has a different idea of exactly what constitutes a perfect chocolate chip cookie.

Welcome back, my novice hackers! One of the most common questions that Null Byte readers ask is: "How can I evade detection by antivirus software on the target?" I have already talked about how AV software works, but to obtain a deeper understanding, what better way is there than opening up and dissecting some AV software?

It's truly amazing how far smartphone camera hardware has come in such a short period of time. It took roughly 5 years to advance the image processing capabilities from a pixelated mess to the crisp and clear photos we can take today. This reaches well beyond the megapixel spec race, since camera modules these days sport vastly improved optics, wider aperture, and even larger pixel sensors that capture more light.

Apple's special September event just wrapped up with the company unveiling several new products, including the iPhone 6S, iPhone 6S Plus, iPad Pro, and the new Apple TV set-top box. In addition to hardware, Apple also discussed a couple of its latest software platforms, iOS 9 and watchOS 2. Check out everything that Apple unveiled below.

Sangria... the elixir of summer. When properly prepared, there are few things more refreshing and magical. If you're looking for a way to mix things up and "get out of the bottle," try one of these lovely libations before the warm weather ends: peach-mango sangria, pineapple-basil sangria, watermelon-raspberry sangria, or blueberry-plum sangria.

If you've ever turned on an episode of Iron Chef or Top Chef, chances are you've seen a contestant in gloves and goggles, yielding a canister that looks far more fit for a chemistry lab than for a kitchen. Wonder what's in the canister? Liquid nitrogen, the go-to tool/ingredient of molecular gastronomy, and one of the trendiest items in many gourmet chefs' kitchens.

Only three things in life are certain: death, taxes, and getting a dent in your car or truck. Even if you're as careful as possible, you can't always account for runaway shopping carts, wrongly thrown footballs, out-of-nowhere light posts, and other real-life annoyances.

Barbecue season: it's the perfect time to play with fire, produce your best burger ever (until next year, that is), and find even more ways to make beer a part of your daily life. However, even a grilling badass occasionally gets stumped by minor BBQ problems. No worries: We've got solutions!

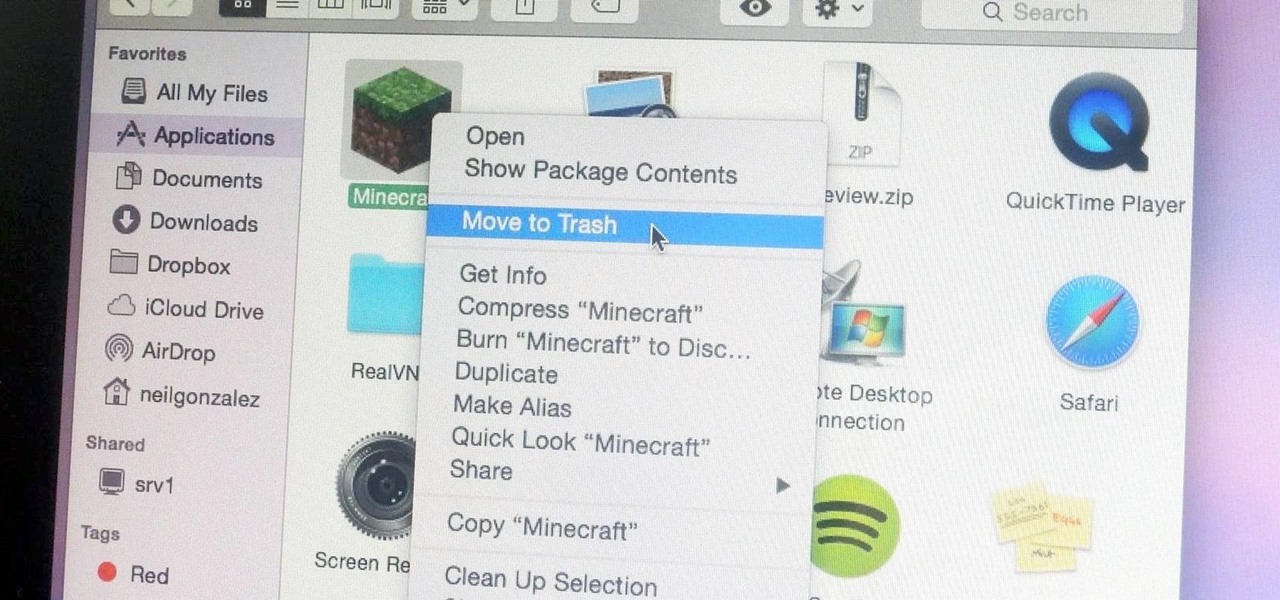
Uninstalling an app on your Mac isn't as straightforward as you would think. When you drag and drop an app into the Trash, then empty it, the main app itself may be gone, but many associated files and folders are left behind. So how do you get rid of them? There are a couple of ways.

Welcome back, my greenhorn hackers! One of the most important issues any hacker must address is how to get past security devices and remain undetected. These can include antivirus software, intrusion detection systems, firewalls, web application firewalls, and numerous others. As nearly all of these devices employ a signature-based detection scheme where they maintain a database of known exploits and payload signatures, the key is to either:

All of Apple's products are praised for being extremely easy to use. So much so, that your grandma can pick one up and be a "pro" within a few hours. However, this isn't necessarily a good thing for us real power users who want more granular control of our devices.

These instructions are applicable to both bObsweep models. Follow the video or text descriptions to replace the disinfecting UV lamp on your automatic vacuum.