If you have an Android device, you most definitely have the Google Play Store. It's the main hub for finding and downloading apps, games, music, movies, and more, as well as updating them. It's where all the magic happens, but you're not getting the full effect unless you're running the latest and greatest version of the Google Play Store app.

This tutorial is about how to create the floating bar with social media buttons on a weebly website. Weebly has change its layout on the dashboard. Its a new video of new layout of weebly dashboard. I found many quesiton regarding 4 different HTML files instead of one index.html. Users were asking about in which they have to change the code so here is the solution. Watch the video, drop your comments and feel free to ask.
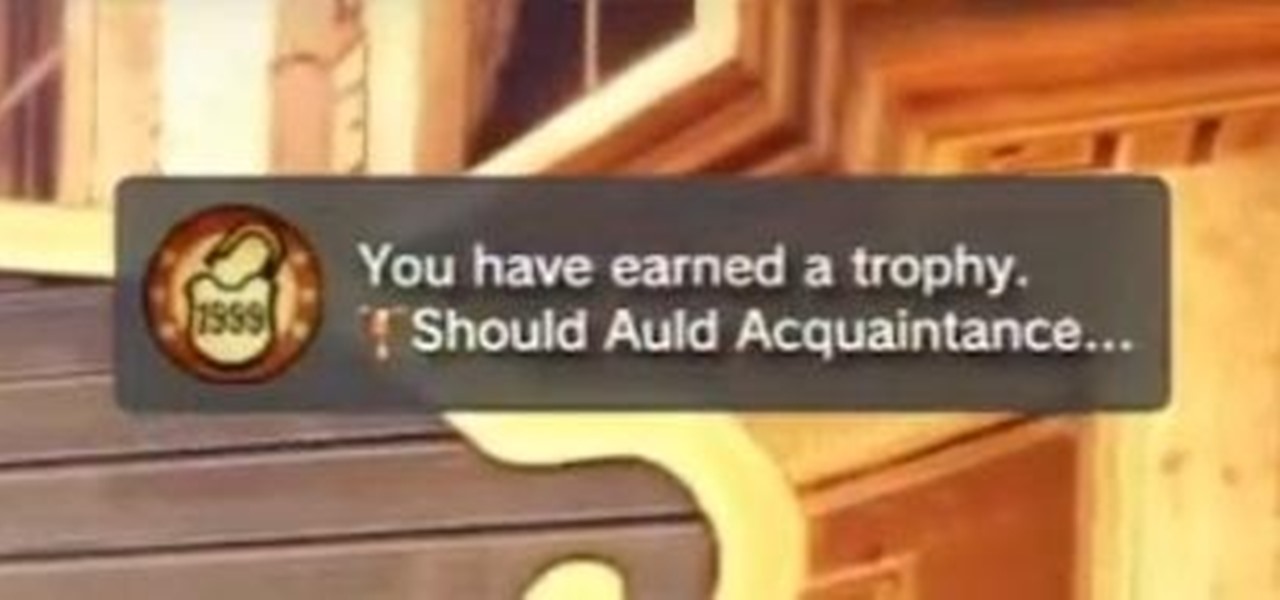
Is there anything better than finding a couple dollars sitting in your coat pocket that you forgot about? Well, after checking my trophy list for BioShock: Infinite, I realized that unlocking 1999 mode is actually an achievement. Hooray me. The achievement trophy is called "Should Auld Acquaintance", and instead of beating the game in easy, normal, or hard difficulty, you can just use the Konami code (found here) to skip right to 1999 mode and get that trophy.

This is a super cute girly pink punk nail design that is done in the backdrop of pink and black gradient - ombre nail art style!

You can make Siri do all kinds of things it was never designed to do. From installing it on older jailbroken iDevices to using it to bypass an iPhone's lock screen, people have managed to come up with some interesting hacks—and that's only the beginning.

Welcome back my fellow hackers! In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms.

Skype is a great way to stay in contact with friends and family over the internet, and people tend to share a lot in their chats, so why not try and find a way to hack it! Once a Skype account is hacked, you can view all conversations within the last three months, see how long each video call was, and even access files that were shared through chat.

You've had your Xbox 360 for a few years now and your game collection is pretty extensive. Maybe it's not that extensive, but it's still substantial. Now imagine that you live in Europe and you're moving to the United States. I don't know why—maybe your dad got a job offer. Don't ask me, ask your parents. They're the ones that are making you move. Anyways, as most Xbox users know, games are coded by region. Games that work in Europe might not work in the United States. Does this mean you shou...

If you've ever wished you could keep tabs on the fish in your aquarium, Justin of Antipasto Hardware Blog has just the mod for you! He created this DIY "shark detector" that sends out a tweet whenever Bruce the shark breaches a perimeter that he set up in the tank.

Proud new papa Gjoci wanted to make sure he never had to worry about whether or not his baby girl was breathing, so he built this amazing breath-detecting baby monitor using a Wii remote, a printed circuit, and a laser. First, he opened up the Wiimote and took out the camera, then used an Atmel Atmega88 microcontroller to make a printed circuit. Low-power infrared lasers shine on the baby's clothing and the Wii camera detects the motion of the baby's breath, activating an alarm if the motion ...

This is OSCAR, the Overly Simplified Collaboratively Actuated Robot. He's built from an old Roomba and an Android tablet, and he's about to make Google+ a lot more interesting. The robot is controllable by users in a Google+ Hangout, allowing the audience to interactively explore OSCAR's environment via his on-board camera.

I love robots. They have the potential to evolve into Asimovian destroyers of the human species, but have only just mastered the art of cleaning my rug. They have an ever increasing cool factor and a growing number of cheap and simple components that let the hobby roboticist reach for the burning miasmas of plasma. But to get to the stars, we need to start with the basics.

How is everyone else getting cool clothes and skin in Poptropica? Cheat codes! This video shows you a list of common cheat codes you can use to change the appearance of your avatar, as well as a few other goodies, when playing Poptropica.

Now that everyone has an Android or iPhone in their pocket, there's no excuse for being late to an appointment or job interview. Thanks to that GPS receiver in your smartphone, navigating your way through city streets and highways is a cinch, in or outside of your vehicle. But once you get inside a building, that fancy GPS feature doesn't know what to do. Which direction is the elevator? How do you get to room 819? Where's the nearest fire exit? The bathroom?

As a hacker, the final stage of exploitation is covering their tracks, which involves wiping all activity and logs so that they can avoid being detected. It's especially crucial for persistence if the target will be accessed again in the future by the attacker.

Did you know that you could learn all the fundamentals of web development for less than $35? Set yourself up for your new coding career in 2021 with The Ultimate 2021 Web Developer & Designer Super Bundle, which is on sale for just $34.99 right now — a huge 98% off the regular price of $1,886.

Privilege escalation is the technique used to exploit certain flaws to obtain elevated permissions relative to the current user. There are a vast number of methods out there to go from user to root on Linux, and keeping track of them all can be difficult. This is where automation comes into play, and a privilege escalation script called Linux Smart Enumeration is one to take advantage of.

The art of fuzzing is a vital skill for any penetration tester or hacker to possess. The faster you fuzz, and the more efficiently you are at doing it, the closer you come to achieving your goal, whether that means finding a valid bug or discovering an initial attack vector. A tool called ffuf comes in handy to help speed things along and fuzz for parameters, directors, and more.

When you don't have a steady cellular signal or immediate Wi-Fi access but need to communicate with others around you, you can set up an off-the-grid voice communications network using a Raspberry Pi and an Android app.

Those of us who've taken the time to learn how to code are relatively well-suited for shakeups in the economy. Despite the recent and notable disruptions caused by the COVID-19 outbreak, demand for talented and trained programmers and developers is still high, and it will likely keep rising as companies in every industry adapt their business models to a more remote world.

There are countless ways in which you can turn your love of tech and coding into a full-fledged career — from developing apps and websites as a freelancer to working in the IT departments of small startups or major tech companies. But one of the best ways that you can put your programming skills to good use is to join the increasingly important world of cybersecurity.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

It's nearly impossible not to be at least somewhat familiar with Microsoft Excel. While it's needed for many office jobs and data analysis fields, hackers could also benefit from improving their spreadsheet skills. Many white hats already know some of the essential Excel hacks, such as cracking password-protected spreadsheets, but there's so much more to know from an attack standpoint.

Samsung's new line of Galaxy S20 flagships have a water resistance rating of IP68. This means you don't have to worry as much about getting the phones wet, but there's a limit to that.

Individually addressable LEDs, also commonly called "NeoPixels" after the popular Adafruit product, are a bright and colorful way to get started with basic Python programming. With an inexpensive ESP8266 or ESP32 microcontroller, it's easy to get started programming your own holiday lighting animations on a string of NeoPixels with beginner-friendly MicroPython!

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

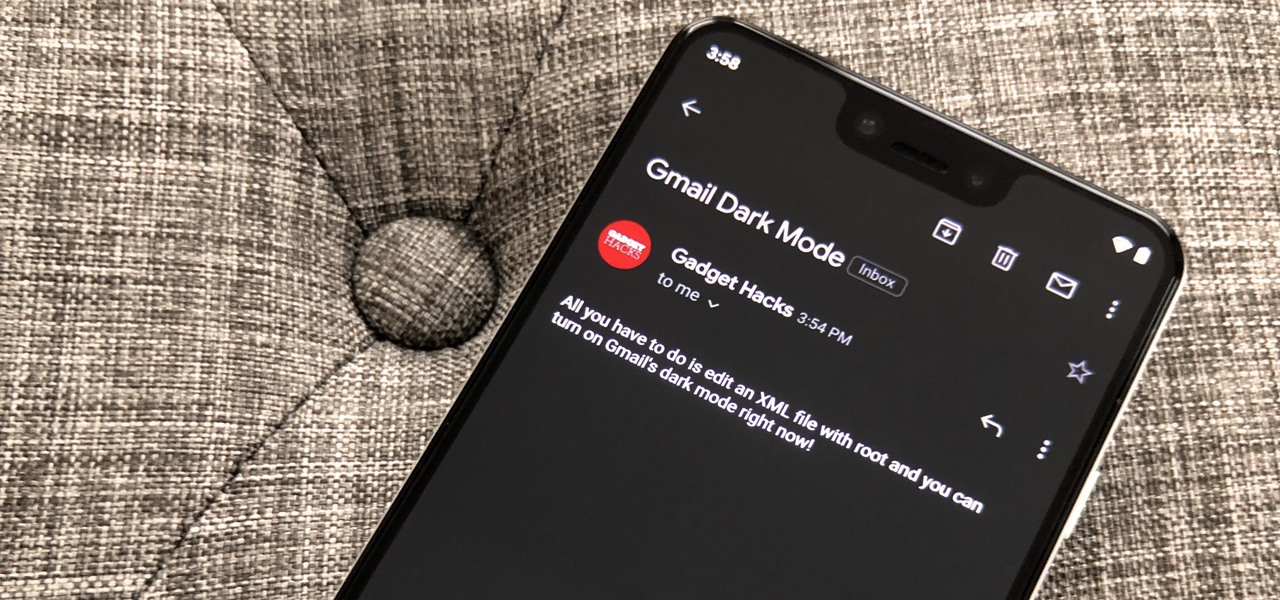
Dark mode is finally rolling out for Gmail on Android. But this is a Google product, so you already know it'll be a while before the server-side update hits most devices. Sideloading the newest APK doesn't work, neither does switching accounts. But if you're rooted, you can enable dark mode by modifying a simple XML.

Scanning pictures and uploading them to Google Photos is a great way to digitize your collection. With unlimited high-quality storage and text recognition capabilities, it's hard to pass up. And for your older family pictures, Google Photos will soon even colorize black and white images.

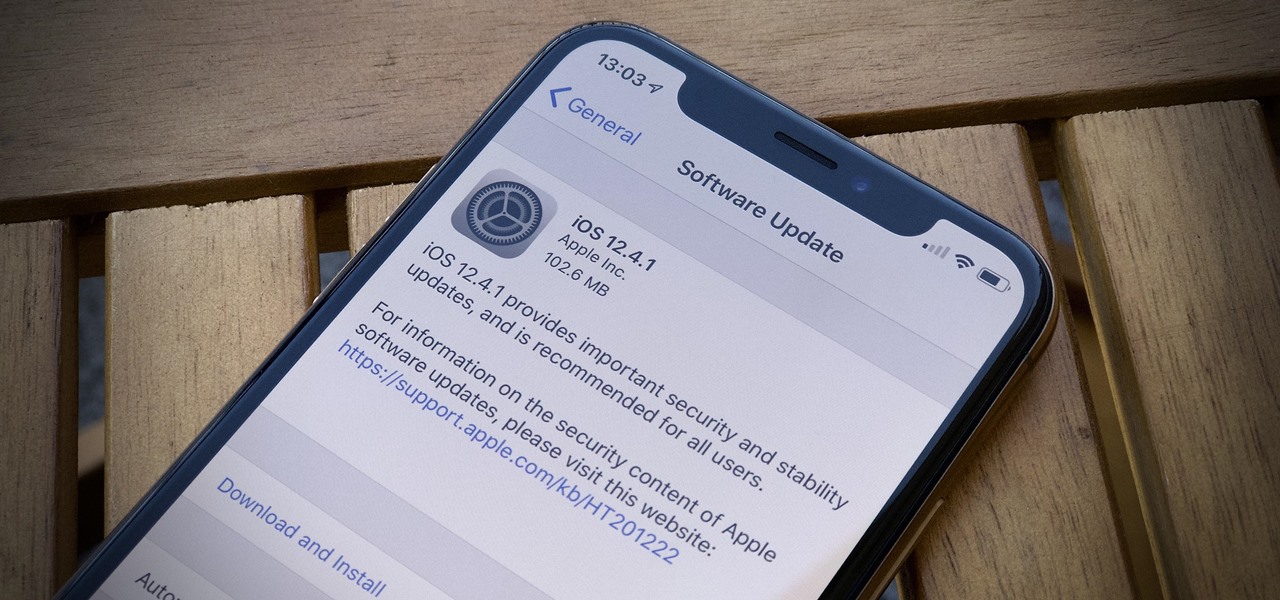
While all eyes might be on the next beta release for iOS 13, Apple is still pumping out updates for iOS 12. The company released iOS 12.4.1, the first update since iOS 12.4, on Aug. 26. The latest update includes a patch for the jailbreak vulnerability recently discovered in 12.4. One month later, on Sept. 26, iOS 12.4.2 came out for older iPhone models.

For developers and makers getting started with augmented reality, Intel is lowering the barrier to entry for its RealSense line of sensors.

It's no secret that the enterprise sector is hot for augmented reality, but the move into the enterprise AR software market by one of the biggest names in industrial engineering announces the technology's arrival loud and clear.

Months ago, we showed you some of the powers of Spatial, the HoloLens app that allows groups of workers to collaborate in augmented reality using 3D avatars.

A rainbow table can be thought of like a dictionary, except instead of words and their definitions, it holds combinations of characters on one side and their hashed form on the other. What is a hash and why would you want to know what random combinations of characters are hashed into?

You don't need an obsessive ex stalking you to benefit from the ability to record calls on your iPhone in a pinch. Besides protecting yourself from nefarious intent, recording important conversations like verbal contracts and agreements can help you cover all your bases and ensure you're insulated from any potential liabilities that may appear down the road.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

Not content to let NFL's official pizza sponsor corner the market for feeding football fans, 7-Eleven has taken a page out of Pizza Hut's playbook with a promotional augmented reality game.

A new app for iPhones and iPads gives developers a sandbox for testing their AR experiences and sharing them with the world.

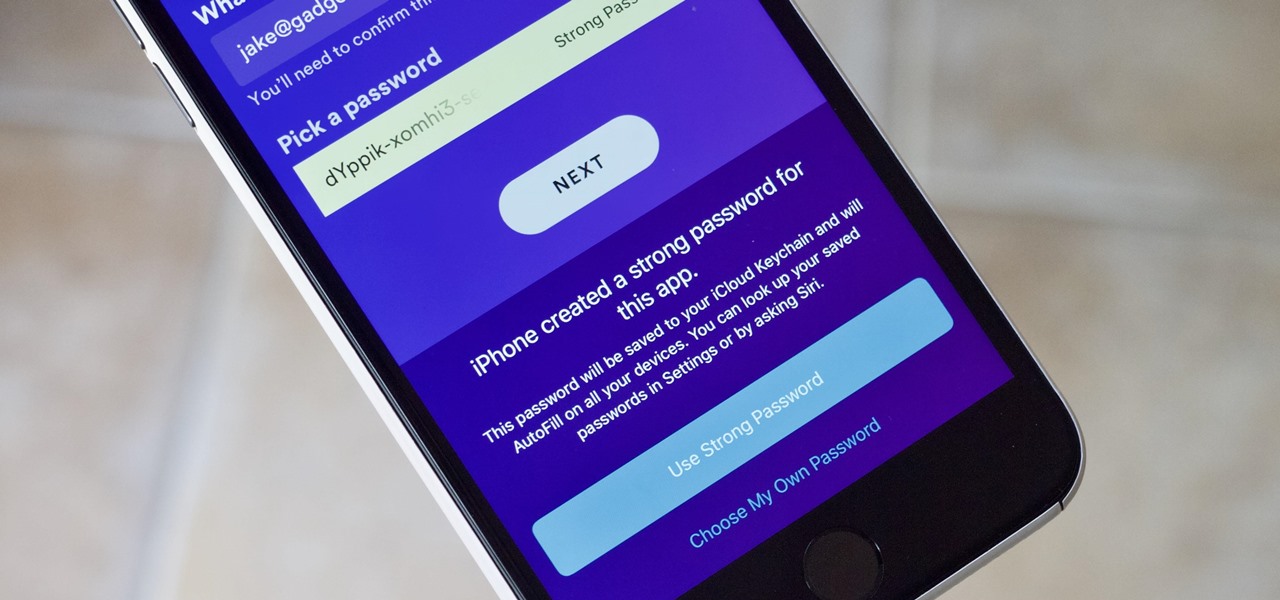
Maybe you prefer writing passwords in a notebook. Maybe you like creating your passwords yourself. Whatever the case, you don't like iOS 12's new automatic password generator, and you don't need it to pop up every time you enter a new password in Safari or a third-party app. Lucky for you, iOS 12 lets you disable the feature altogether. Unfortunately, that perk comes with a catch.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Amazon Web Service's do-it-yourself tool for building augmented reality experiences and VR has graduated from beta and is now available to all interested users.