While the iPhone XS actually comes with a smaller battery than the iPhone X, Apple claims it, along with the XS Max and XR, offer users longer battery life than last year's first Face ID model. While that may be true, your new iPhone still ships without meeting its full battery-saving potential. There are, however, steps you can take to make sure your X, XS, XS Max, or XR makes it from morning until night.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

If there's one strength of Apple's that iOS and Android fans can agree on, it's the company's dedication to user privacy. With each new iteration of iOS, Apple builds upon these foundations, enhancing and increasing each iPhone's ability to protect its user's data. In iOS 12, Apple has added many new features to Safari, most of which have their own unique way of keeping you safe online.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

It's no secret that Android has a messaging problem. iPhone users can turn to iMessage as a one-stop shop for all their messaging needs — features like read receipts and the ability to text from a computer have been standard with Apple products for quite some time. Android has no such solution, but Google's looking to fix that with a huge update to the Android Messages app.

With the macOS stager created and the attacker's system hosting the Empire listener, the malicious AppleScript can be designed and disguised to appear as a legitimate PDF using a few Unicode and icon manipulation tricks.

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be hosted locally and index results from over 70 different search engines.

Since starting as a simple messenger with self-destructing pictures, Snapchat has grown into a full-fledged social media platform. As features were added, new permissions were requested, and we're all probably guilty of just tapping "OK" to try out the latest and greatest. But at some point, it's a good idea to review your settings to see what personal data you're putting out there for all to see.

For some of you, whether or not to delete Facebook is a daily struggle. One reason you might not have pulled the trigger on your Facebook account yet could be because of Messenger, which provides millions of people with different devices an easy way to communicate with each other. But here's a secret you might not know: you don't need to have a Facebook account to use Facebook's popular chat app.

Buying an unlocked phone is usually the correct move. By doing so, you bypass a lot of bloat that carriers put on your phone, and you can also use that phone with another carrier should you decide to switch to a new one. However, a lot of carriers won't give unlocked devices access to their visual voicemail apps. For that, there's Google Voice.

Because of quirks with cell radios and how Android was previously set up, custom ROM support for Galaxy S phones has been sparse these past few years. It's been almost nonexistent for US customers, while international users would see some ROMs. Thanks to Android Oreo's Project Treble, this will all be changing soon.

As a developer, before you can make augmented-reality robots that move around in the real world, controlled by a user's finger, you first need to learn how to harness the basics of designing AR software for a touchscreen interface.

There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take camera snapshots, and even record with the microphone without the user knowing.

Not to be outdone by Apple and it's new line of flagship phones, Google has followed suit and finally announced the followup to their highly regarded Pixel line of handsets — the aptly named Pixel 2. Thankfully, the tech giant has also joined in on the trend towards more durable devices, and has engineered both the Pixel 2 and Pixel 2 XL to have a rating of IP67 under the IEC standard 60529.

In case you didn't catch the big event in Cupertino, Apple just unveiled two of the most cutting-edge phones ever made — the iPhone 8 and the iPhone X. Out of the many glorious specs that were rattled off on stage, one stands out for being just a little confusing: Both models are rated IP67 under the IEC standard 60529.

A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) toolkit. Unlike standard administration RATs, these tools are designed to be delivered stealthily and operate undetected.

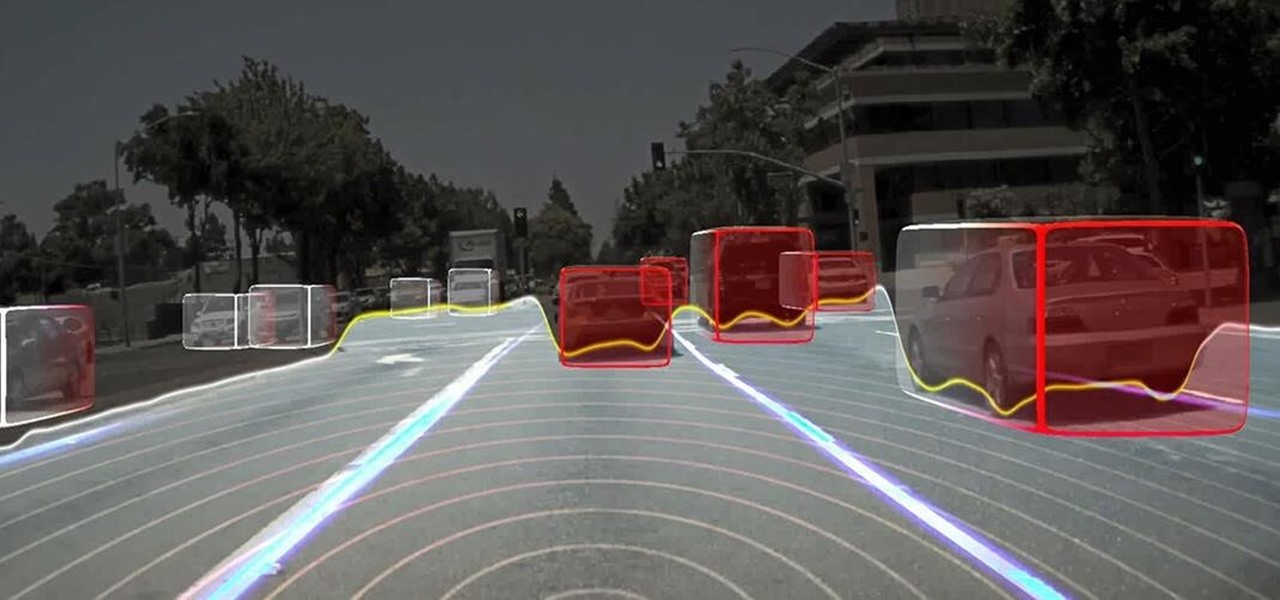
Long before Nvidia figured out how to embed neural networks in its graphics processor units (GPUs) for driverless vehicles, it and other chipmakers were already making the same kinds of devices for 3D games and other apps.

When you first set up an iPhone, you'll be prompted to create a six-digit passcode to unlock your screen and access certain system settings. If you skip this step, you can always go back and create one, which we highly recommend. Without a passcode, everything on your iPhone is accessible by anyone who gets their hands on it — nosey friends, hackers, thieves, local law enforcement, the FBI — and you don't want that, do you?

There's nothing more fun than unlocking a hidden Snapchat filter or lens and beating everyone to that perfect first selfie. So when a new filter or lens comes out, like the current Uganda Knuckles one, it's always interesting to see how things will turn out.

In a disturbing turn of events, Uber has been tracking oblivious iPhone users even after they removed the application from their phone. Two years ago, the situation escalated to such an extent that CEO Travis Kalanick earned a slap on the wrist from Apple mogul Tim Cook.

Backdoors are convenient to leave behind once you've already found a way into a server, and they can come in handy for a variety of reasons. They're good for developers who want a quick way into machines they're working on, or for systems administrators who want similar access. Of course, backdoors are also a hacker's best friend, and can be added in a variety of ways. One good tool for doing this is Weevely, which uses a snippet of PHP code.

Hello people, I'm back for Part-3. In this part, as promised, we are going to create a client program and then we are going to test it with our server program made in Part-2.

The biggest corporation we know today is called Google, I bet you've heard of it yeah? How Google Tracks You:

It's been a while since I wrote up an article for this series but I did say that I'd be covering some WinAPI. So if you're interested in programming for the Windows platform, hop aboard and follow along.

Welcome back everyone. I apologize for the lack of training articles, but I've been rater busy lately. I've recently picked up a second job and my college courses are now back in session, so I'm a bit strapped for time.

Welcome back, my neophyte hackers! In the world of information security, the most common intrusion detection system (IDS) you will ever encounter is Snort. As you probably already know, an IDS works similarly to antivirus (AV) software on your desktop; It attempts to identify malicious software on your network and warns you of its presence.
Hey everyone. Only found the site a few days ago but really loving it. Been

In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus

Hello there! This will probably be the final tutorial on functions where we will be looking over a method called pass by reference. This technique allows us to modify large amounts of data without the overhead and return multiple values. Let's go!

Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay anonymous.

First of all, I would like to apologize for a week long absents for the tutorials of this newly series, Raspberry Pi. But obviously I'm back and I present all you guys a article on turning your Raspberry Pi into a hacking platform. I'm gonna use the platform Kali Linux for the Raspberry Pi. I should note that I'm not gonna go into detail on how to install Kali Linux since OTW already has done a tutorial on how to turn your Raspberry Pi into a Hacking Pi. The point of this particular tutorial ...

Welcome back everyone. As many of you know, reconnaissance is extremely important in any successful hack. Without proper reconnaissance, we won't know what we're about to get into, literally.

Welcome to a tutorial explaining functions. This article will help clarify some things we have already been exposed to such as function prototypes, function calls, return values, etc.

Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show.

Welcome back! In the last training session, we covered logical and membership operators. We're going to switch gears and expand our knowledge of lists.

Hey there, reader! In this tutorial we are going to explain how values are stored in variables as either signed or unsigned. Try to not get lost!

Hello again, reader! In this post, we are going to cover some data types and how to declare variables. It shouldn't be too hard so just sit back, relax, grab some popcorn and enjoy the ride (while you still can!).

As one of the most powerful Android apps for connecting your phone or tablet to your other devices in various ways, Pushbullet had always been a fan—and Gadget Hacks—favorite.

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .