It's easy to run Kali Linux from a live USB on nearly any available computer, but many publicly accessible laptops and desktops will be locked down to prevent such use. School, work, or library PCs can be secured with a BIOS password, which is often an easily recovered default password. Once you have access, though, you can use a USB flash drive to run Kali live on any PC you find.

Electronics maker Epson is courting developers to its Moverio smartglasses with an updated software development kit (SDK) and integration with a web-based tool for publishing augmented reality experiences.
Thanks in large part to our phones, many of us don't get the recommended eight hours of sleep. In Android Pie, Google introduced a feature called "Wind Down" that aims to help combat this. However, thanks to a creative app developer, we don't need to wait for Android 9.0 to enjoy this feature.

To name just a few companies, VK, µTorrent, and ClixSense all suffered significant data breaches at some point in the past. The leaked password databases from those and other online sites can be used to understand better how human-passwords are created and increase a hacker's success when performing brute-force attacks.
In late-2017, Snapchat debuted Lens Studio, a way for anyone to create their own augmented reality "world lenses" that can be shared to anyone with a Snapchat account. If you don't mind spending money, you can even create custom face lenses and basic overlay filters for special events. And while making lenses and filters have gotten pretty easy, distributing them is another matter entirely.

Every dollar that comes your way is a blessing, especially when it comes to trading in the volatile world of bitcoins. Thankfully, Coinbase rewards you for sending much valued customers their way, giving you more money to feed your cryptocurrency trading needs.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

With all the hype surrounding meteoric rise of Bitcoin (BTC), Litecoin (LTC), Ethereum (ETH), and Bitcoin Cash (BCH), it's easy to overlook the fact that you can send and receive cryptocurrencies as a form of payment. And thanks to Coinbase, sending and receiving digital coins couldn't be any easier.

With the big reveal of the Magic Leap One: Creator Edition in December 2017, and now the update on Feb. 13, 2018, we no longer have to speculate as to what the augmented reality headset will look like or when (in general) it will be available.

While hackers adore the command line, working with the GUI (graphical user interface) of an operating system has some advantages. This is especially true when it comes to post-exploitation. When we can control the mouse and keyboard of a remote computer, we can truly say we have complete control over the device. Today, I'm going to introduce to you the PyAutoGUI module, which does just that, and just how much fun you can have with it!

If you're following the classic Halloween playbook closely, you've already got a costume or three picked out, you've binged-watched your favorite horror movies, and you've likely visited a haunted house. But it's 2017, so how about trying something new, like a haunted house that's not actually there?

To revise a line from the Blues Brothers, when it comes to ARKit apps, we've got both kinds — home utilities and games. As such, two more candidates for each category have made their way to the app store.

Using either iMessages or FaceTime on the iPhone is a great alternative for coworkers to stay in touch in the event that messaging services like Slack go down. They're also a handy means of communicating between buyers and sellers, as it provides a more intimate way of either checking out or showcasing a product. But you're not always going to want to give out your real number to everyone.

In the first part of this series, we looked at the surface detection that is provided by the ARKit. We looked at how it worked and covered some of the tools that could help us determine what is not working; when it doesn't. Now let's take this to the next step.

Aspiring engineers, your challenge, should you choose to accept it, has been issued by Jaguar Land Rover.

The world is full of vulnerable computers. As you learn how to interact with them, it will be both tempting and necessary to test out these newfound skills on a real target. To help you get to that goal, we have a deliberately vulnerable Raspberry Pi image designed for practicing and taking your hacking skills to the next level.

In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hear in the radio spectrum, it's time to explore the possibilities of broadcasting in a radio-connected world.

WhatsApp sneakily made some security changes to iCloud backups without your knowledge, ladies and gents. Not that strengthening security is a bad thing, but still!

Your Android phone could be listening to ultrasonic ad beacons behind your back. The unwelcome news comes year after app developer SilverPush promised to quit using its (creepy!) eavesdropping software.

UPDATED 5/4/17: SI has stated that they won't be augmenting its Swimsuit Edition. Although, this could be a sign that the company may do so in the future. If they already have all the tech set up for the latest feature, then they are already half way ready to augment other SI editions. So get ready SI fans and download the designated Life VR app, because you are going to need it to point it at these specially marked SI pages.

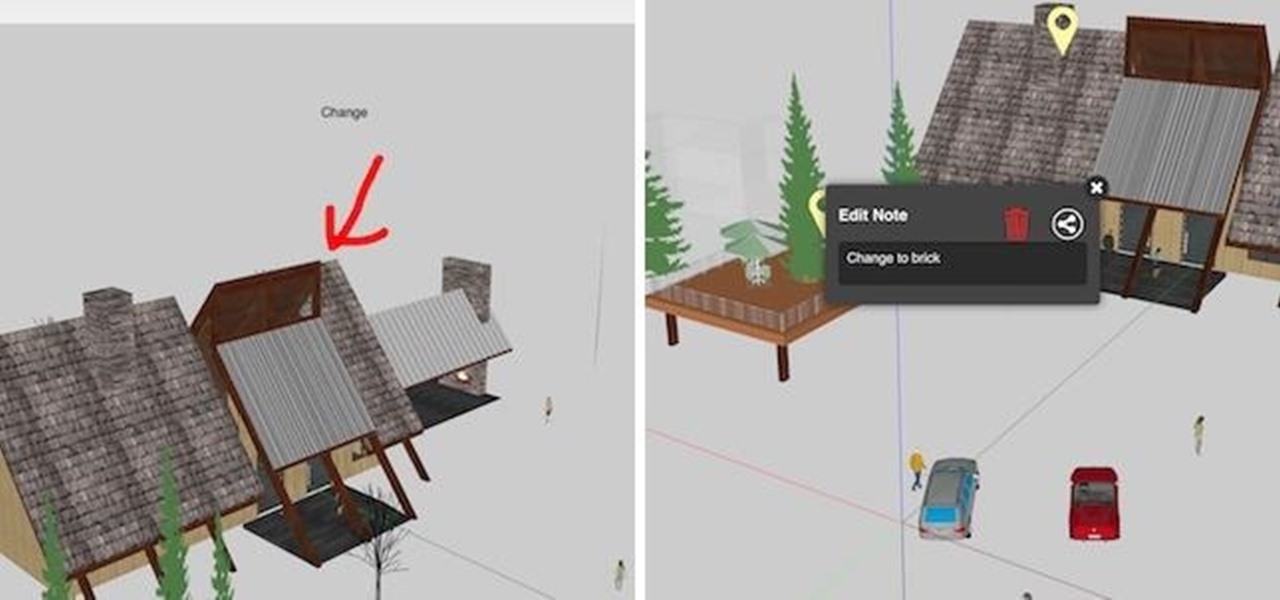
When making a convincing mixed reality experience, audio consideration is a must. Great audio can transport the HoloLens wearer to another place or time, help navigate 3D interfaces, or blur the lines of what is real and what is a hologram. Using a location-based trigger (hotspot), we will dial up a fun example of how well spatial sound works with the HoloLens.

Before the release of the Galaxy S8, Samsung quietly uploaded one of their core TouchWiz apps to the Google Play Store as a beta. Samsung Internet, as it's called, has been a staple on all Galaxy devices for years now, but you can now try the browser on any Android phone.

If you've ever wondered why the pictures and videos you share with Snapchat on your Android device seem to look grainy with low resolution, you're not alone. We all know it, and we've come to accept it as a plain fact: Snapchat image quality sucks on Android.

When you're driving, the last thing you need to be doing is messing around with your phone. But these days, people expect you to be available at all times, so the text messages continue to flow in while you're on the road. It's a terrible distraction, and one that is responsible for 25% of all car wrecks in the United States.

Prior to this year's WWDC, there were lots of rumors that Apple might finally be making a version of iMessage for Android. While that never came to fruition, a few big updates to a very useful app have now ensured that we can seamlessly send and receive Android texts in Apple Messages on our Macs.

Gmail has been the email standard for quite some time now, and for good reason: it's a free service provided by one of the largest tech companies in the world that offers users an amazing feature set to manage, send, and keep track of all their important emails.

Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of your private life, encryption has become our last line of defense.

This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

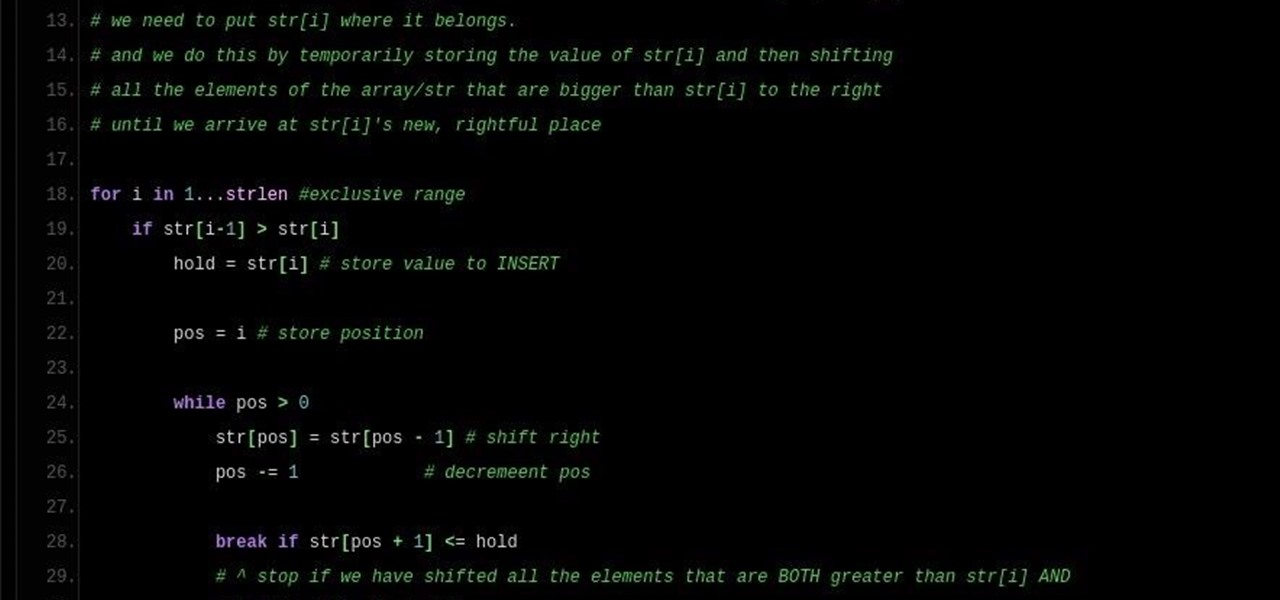
Note: a bug was found in the Insertion Sort implementations. The bug was corrected in each language. Please refer to the pastebin links for the most up-to-date versions of the sample code. Any screenshots may be behind. More about the bug can be found here.

Welcome back, NB community, to my series on sorting. I introduced in my last article the concept of complexity. When I say complexity, I'm talking about time complexity.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implications which come along with it. I will show you using an example from the wargame IO Smash The Stack.

Hello again, and welcome back to another tutorial on functions, this time, covering recursion. What Is Recursion?

So you want to create a meterpreter virus, but you keep getting caught by AV. How do you create one that will go undetected? In this tutorial, I'll teach you how to code your own simple virus that will download a powershell payload from an apache webserver and execute it - bypassing antivirus.

Hello readers, in this tutorial, we will be discussing how to perform file operations such as reading and writing.

Hello again! In this tutorial, we are going to go over something called "operators" which will help us build upon conditions of control structures and also some variable manipulation. Without further ado, let's dive in!

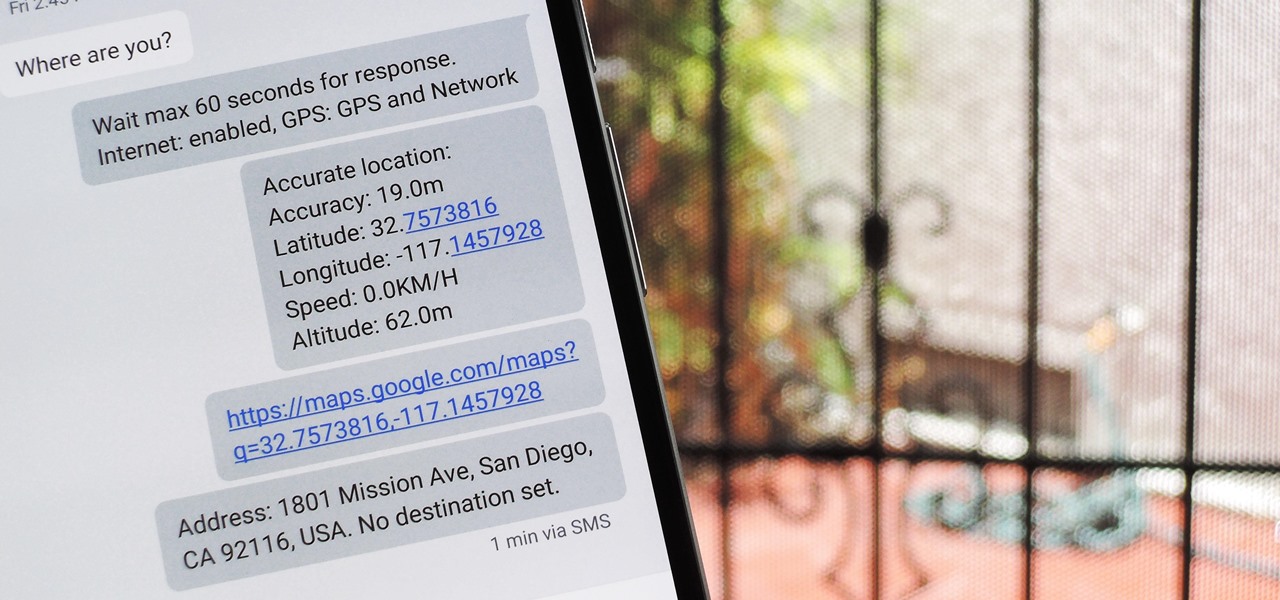
If your smartphone is ever lost or stolen, it's a terrible experience. If you file a police report, chances are the responding officer will need your device's IMEI or MEID number if you want to stand a chance of getting it back. Same goes for making an insurance claim on a lost or broken phone, so it's definitely important to have this unique identifier handy.

Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post.

Microsoft's "Fall Update" to Windows 10, code named Threshold 2, has a lot of new tricks up its sleeve. It's the biggest update we've seen since Windows 10 was released this summer, and it's rolling out to all users right now.

Want the next level security? Well then take a read here because this is some next level stuff. Heard of It?