Earlier this week, we learned that you can get people to put more money in a tip jar simply by drawing eyes on it. But what if you want to keep them away from something? Eyes can do that, too, especially when they're Putin's.

A couple of months ago at the Black Hat security conference, hacker Cody Brocious gave the hotel industry a nasty surprise when he figured out how to hack the locks made by Onity that are used in millions of hotels worldwide.

Over 2 million people are anxiously awaiting the arrival of their new iPhone 5, which has caused a few shipping problems, to say the least. There has been a considerable amount of confusion about when, exactly, the iPhone is going to ship, depending on where it was bought and how it's being delivered.

Whether you want to use it to keep your guests safe or just to see who's the most drunk, it's always fun to have your own breathalyzer at a party. We've seen DIY breathalyzers before, like this one by Craig Smith, but how about an Arduino breathalyzer?

As useful as they can be, 360-degree photos are a total pain to create. The process usually involves taking a bunch of pictures with expensive equipment or software, and not just anyone can do it. But a new iPhone app called CupChair changes everything—it lets you take 360-degree photos with nothing but your iPhone and a cup.

The worst part of moving into a new place is, well...moving. It's tedious, a lot of hard labor, and it can take forever, and don't even get me started on all those labels. It's also one of the only times in your life when everything you own can be stolen at once, since it's sitting in a movable container. Rather than risk losing everything, try this DIY Moving Truck Alarm System by Tim Flint that lets you know when the loading door is opened so you can catch would-be thieves red handed.

Most of us have given up our big, bulky stereos in favor of smaller, sleeker models, but how many of us actually get rid of the old ones? If you don't like the idea of throwing out or giving away electronics you spent good money on, you can always upgrade them instead!

Hate answering the door, but don't trust your friends with a set of keys? This RFID front door lock made by Steve Pomeroy will solve all your party-hosting problems. It reads the RFID tags in his friends' public transit cards and decides who's allowed in based on "groups" that Steve defines. And I have to say, it's also rather stylish. It's controlled by an Arduino serial console and a custom Android app to add and remove cards. The reader can store 50 or 100 tags at a time and allows 7 diffe...

If you're a steampunk enthusiast looking to give your bathroom an extra kick, this just might be the project for you. This stylish and functional "vintage" toothbrush timer knows when you've grabbed your toothbrush, and will visually count down two minutes before alerting you when you've brushed long enough. All you'll need to put one together yourself is a microcontroller (the designer used a ATmega328p), a weight sensor, light bulbs, brass cups and a tray, an alarm clock's chime, and some w...

You can hack into nearly any Facebook or Flash based game on the Internet - no cheat codes or special strategies needed. All you really need is the free game hack program Cheat Engine, and a compatible browser like Firefox.

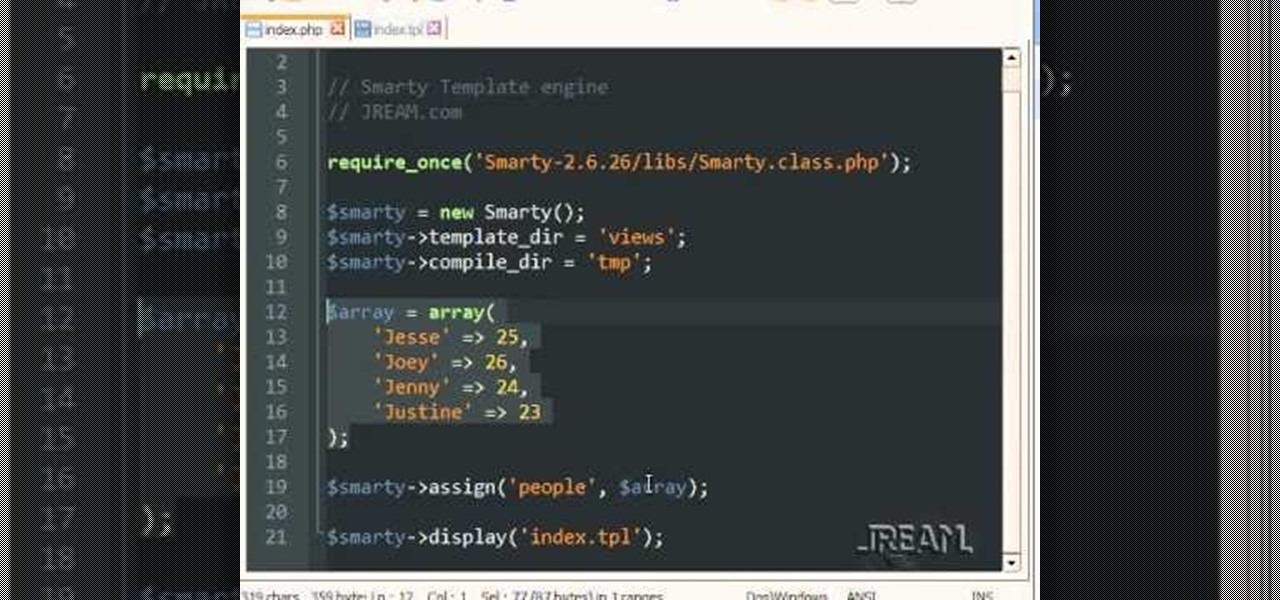
In this PHP how-to tutorial you'll learn how to get started using Smarty Template Engine for PHP. This is a basic intro for PHP coding newbies, so if you're a pro, move on. If you're not a pro, watch the vid and get a little closer.

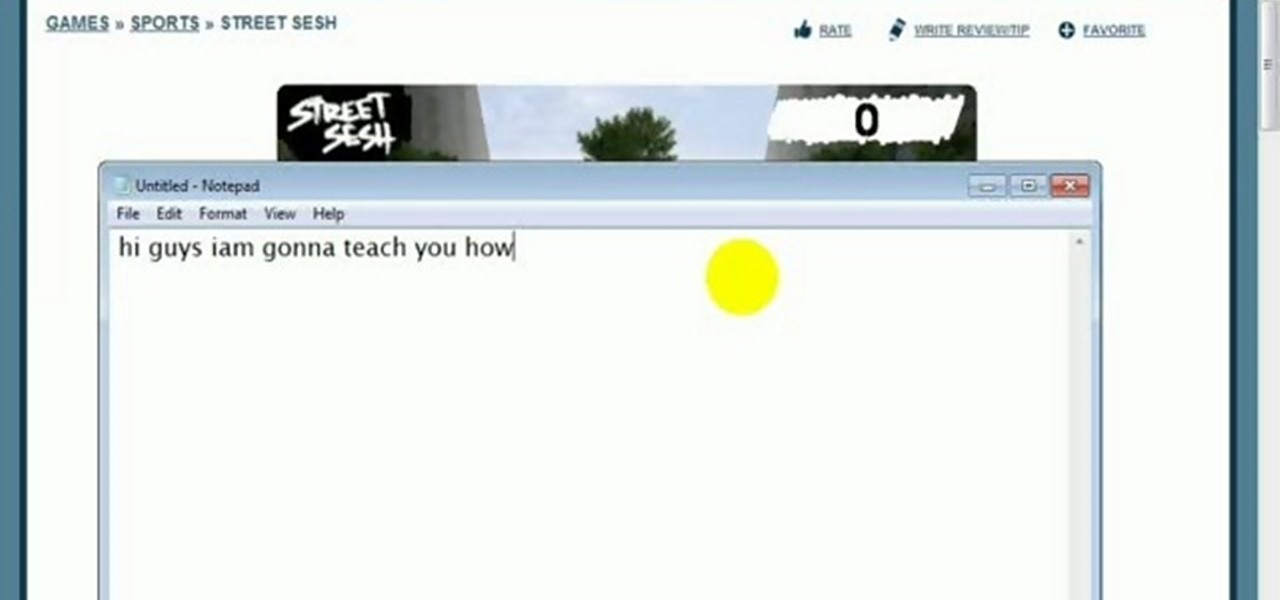
Turn the unmarked and unlined moleskine notebook into a productivity tool! All you need are a few small multi-colored Post-It tabs, a Hi-Liter and a regular pen. By color coding the separate sections of the notebook, you can easily flip to needed sections.

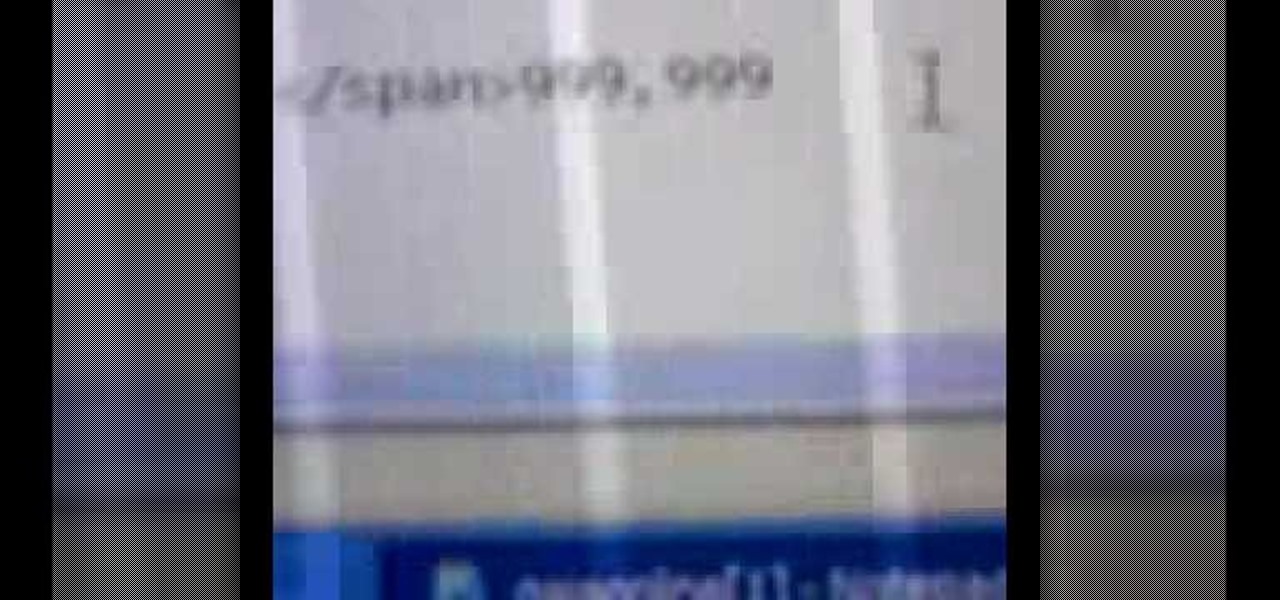
If you're wondering how to hack Gaia accounts, the solution may be simpler than you expect. By viewing the page's source code, one can hack their gold to 999,999 by changing a few lines of code.

In this automotive repair video you will learn how to fix the ABS and speed sensor in a Dodge Dakota truck. Learn how to read diagnostic trouble code to evaluate trouble indicators and fix broken sensors. So if your speed sensor or ABS brake system are on the fritz in your Dodge Dakota truck, watch this video and learn how to check and fix them.

This short, instructional video seeks to demonstrate how go about unlocking your own 2003-2005 model Infiniti G35 coupe with a Sprint PPC-6700 PC phone through use of the phones in-built IR, or infrared, capabilities and a provided code.

This short video tutorial seeks to demonstrate how you can unlock your own 2006 Toyota Corolla with a Sprint PPC-6700 PC phone through use of the phone's in-built IR, or infrared, capabilities and a provided code.

A long series of code is required to hack any JavaScript web page. Watch this video to learn how to hack a Java website to edit it for your pleasure.

This video shows you how to edit an existing window in MEL code for Maya. You may want to watch the tutorial on creating a MEL script for a window if you don't already have one.

Keep your projects organized and find what you need quickly by color coding nodes in Houdini.

This tutorial explains how to list files in a recursive manner within C#. It expands upon the code for writing a program that lists files, so if you can't do that yet, watch that tutorial first.

SQL injection is a type of code injection that takes advantage of security vulnerability at the database level. It's certainly not the easiest form of hacking, but if you're serious about turning a website upside down then this is the way to do it.

A little demonstration of the power of wxPython, showing how to get a titled window up and running with five easy lines of Python code. This video is great for those who may be interested in learning Python.

Ian Ozsvald walks you through installing and testing Python 2.5 downloaded from Python.org. This includes how to start Python from the Start Menu and writing your first (Hello World) line of Python code.

The IPython interactive Python shell allows the use of an external editor for editing multiple lines of code. Here Ian Ozsvald shows how to replace the default (Notepad in Windows) with your favorite light-weight editor and how to use it from within IPython.

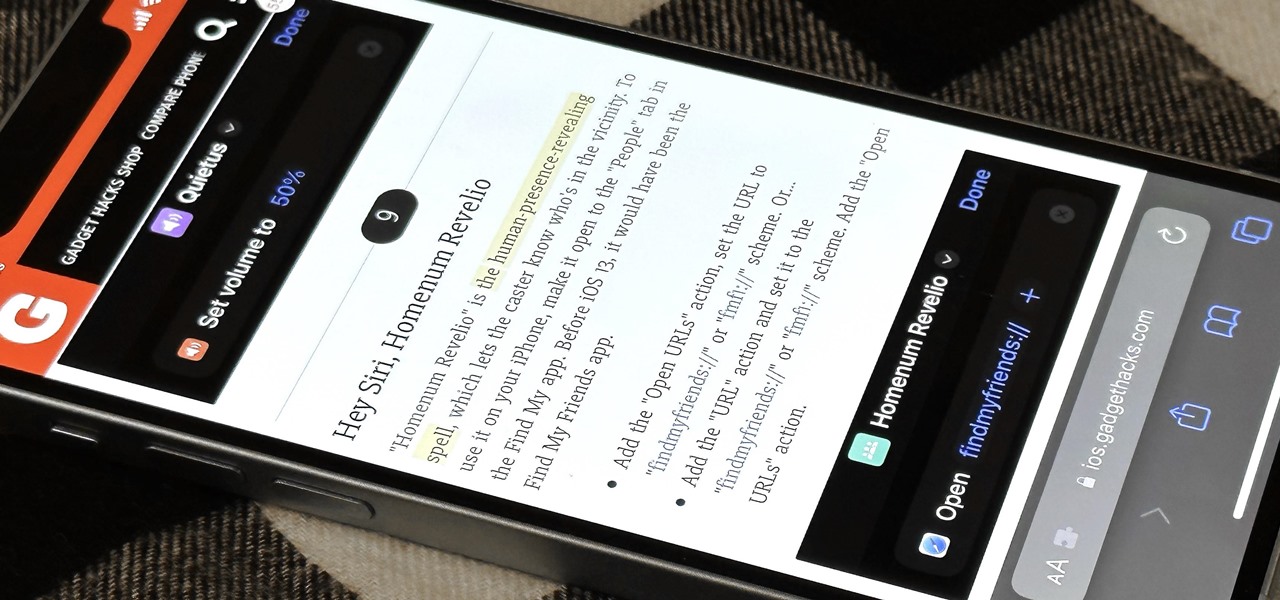
Whether you're wielding an iPhone, iPad, Mac, Android phone or tablet, or even a Windows PC, this little-known secret holds the key to effortless assistance and unwavering obedience. Intrigued? I thought so.

Safari has a major new feature for your iPhone, something that will change how you share, receive, and interact with links — and nobody is talking about it. The feature works on the latest iOS software, as well as the latest iPadOS and macOS versions. Still, you won't find any information about it in Safari's app or settings, so it's pretty hidden if you haven't seen it by accident yet.

Apple finally unveiled the iPhone 14, 14 Plus, 14 Pro, and 14 Pro Max, and there are a lot of improvements that'll make you want to trade in your current iPhone stat. But I wouldn't be so quick to upgrade because there's one "feature" that will make many of you rethink getting a new iPhone 14 series model.

Bash scripting is a convenient way to automate things on any Linux system, and we're going to use it here to automate certain tasks we use all the time.

While obvious, it's a lot more difficult to hack into a locked computer than an unlocked computer. As a white-hat hacker, pentester, cybersecurity specialist, or someone working in digital forensics, there's an easy solution — make it so that the computer won't fall asleep and lock automatically in the first place.

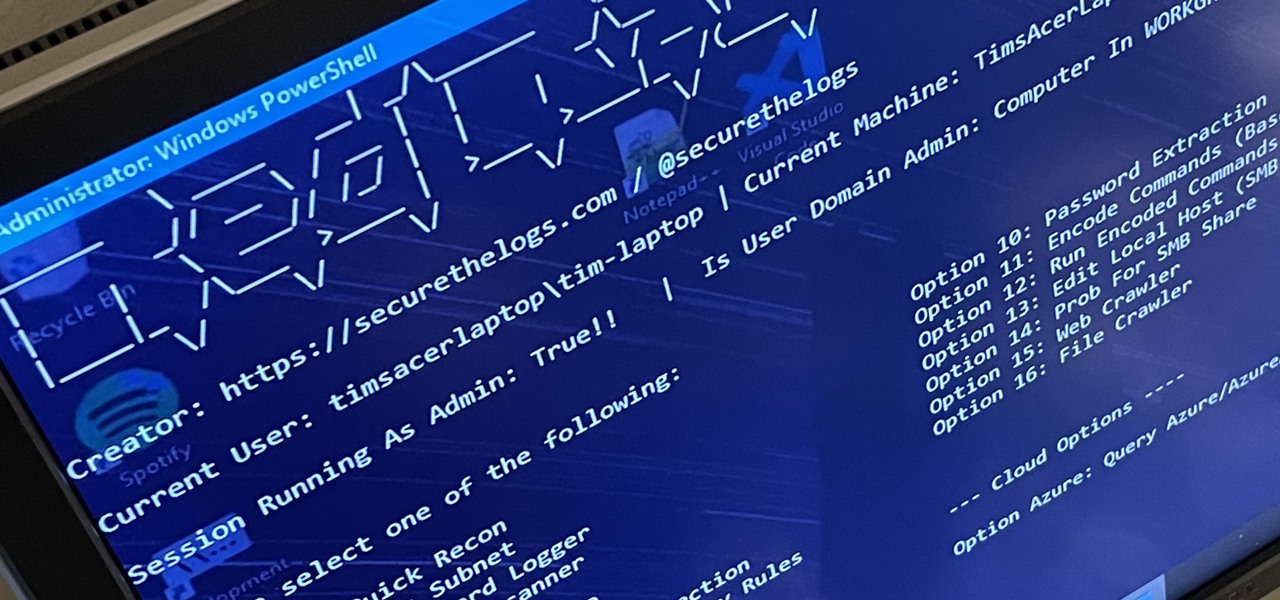
RedRabbit is an ethical hacking toolkit built for pen-testing and reconnaissance. It can be used to identify attack vectors, brute-force protected files, extract saved network passwords, and obfuscate code. RedRabbit, which is made specifically for red teams, is the evil twin of its brother, BlueRabbit, and is the offensive half of the "Rabbit Suite."

Microsoft's built-in antimalware solution does its best to prevent common attacks. Unfortunately for Windows 10 users, evading detection requires almost no effort at all. An attacker armed with this knowledge will easily bypass security software using any number of tools.

PowerShell is an essential component of any Windows environment and can be a powerful tool in the hands of a hacker. During post-exploitation, PowerShell scripts can make privilege escalation and pivoting a breeze, but its execution policy can put a damper on even the best-laid plans. There are a variety of methods, however, that can be used to bypass PowerShell execution policy.

It's a common misconception that iPhones are impervious to cyberattacks and "more secure" than Android. And when an iPhone does get hacked, it's nearly impossible to tell that it happened.

Hackers often find fascinating files in the most ordinary of places, one of those being FTP servers. Sometimes, luck will prevail, and anonymous logins will be enabled, meaning anyone can just log in. But more often than not, a valid username and password will be required. But there are several methods to brute-force FTP credentials and gain server access.

TWRP won't be ready for the Pixel 4 and 4 XL until months after release. But since you can already root with Magisk and tinker with the OS, you might find yourself in a situation where your phone won't boot, yet you don't have a custom recovery installed to fix it. Luckily, there's still a way around this.

Spam calls are one of the most annoying things to happen in the world of smartphones for more than one reason. Not only are they bothersome, but they can also be dangerous to people who don't know any better. Google has come up with a crafty solution known as "Call Screen" to let the Google Assistant handle the call for you while you listen in on the caller like a stealth ninja.

The Pixel 3a runs smoothly out of the box already, but installing a custom kernel can supercharge your experience even more. From fine-tuned CPU tweaks for boosting performance or battery life to adjusting the display colors for your screen how you want, ElementalX kernel can provide you with a ton of new features you didn't know you were missing.

One of the issues with rooting your device is the inability to update your phone via OTA. Any security patches or software updates pushed out by the OEM are lost because your bootloader is unlocked. However, you still can update your device, it just a take a bit more effort.

Back in July, Google rolled out a new design for the web version of Gmail. The rollout included new features alongside the visual changes, one of which being Confidential Mode. This new privacy-centric feature has now finally arrived on the mobile app version of the service, and here's what you need to know.

Think back to when you last wanted to transfer some music or videos to your friend's smartphone and how difficult and slow it was. As powerful as our phones are, the default file sharing options are limited. There are, fortunately, some better options which make moving files easy, secure, and painless.