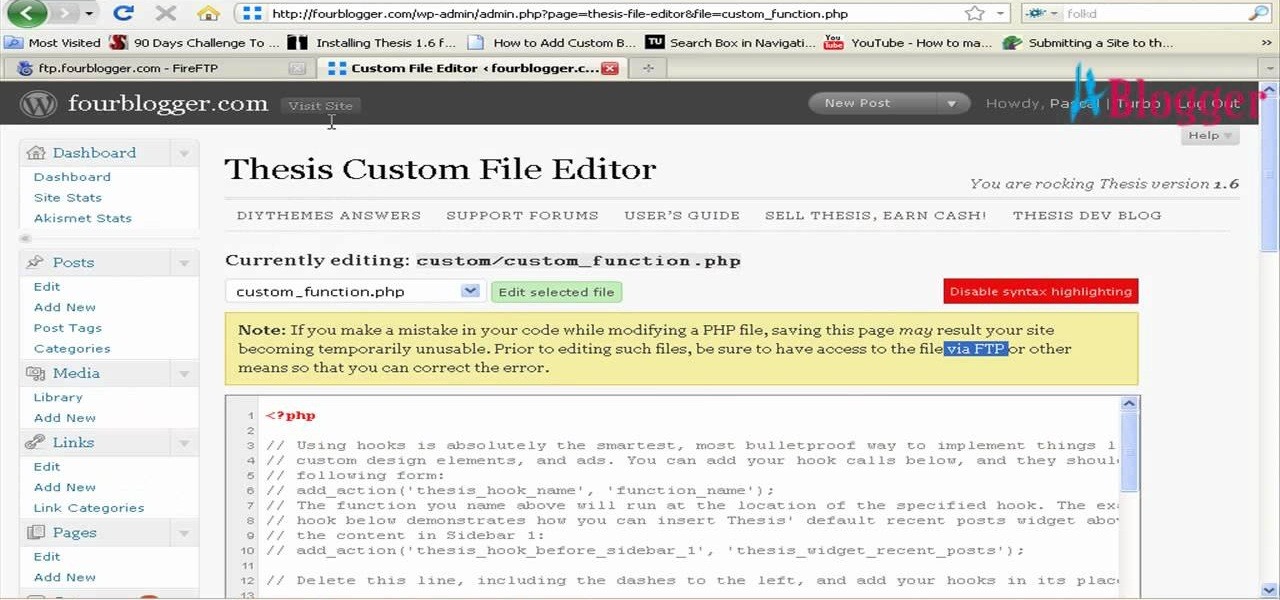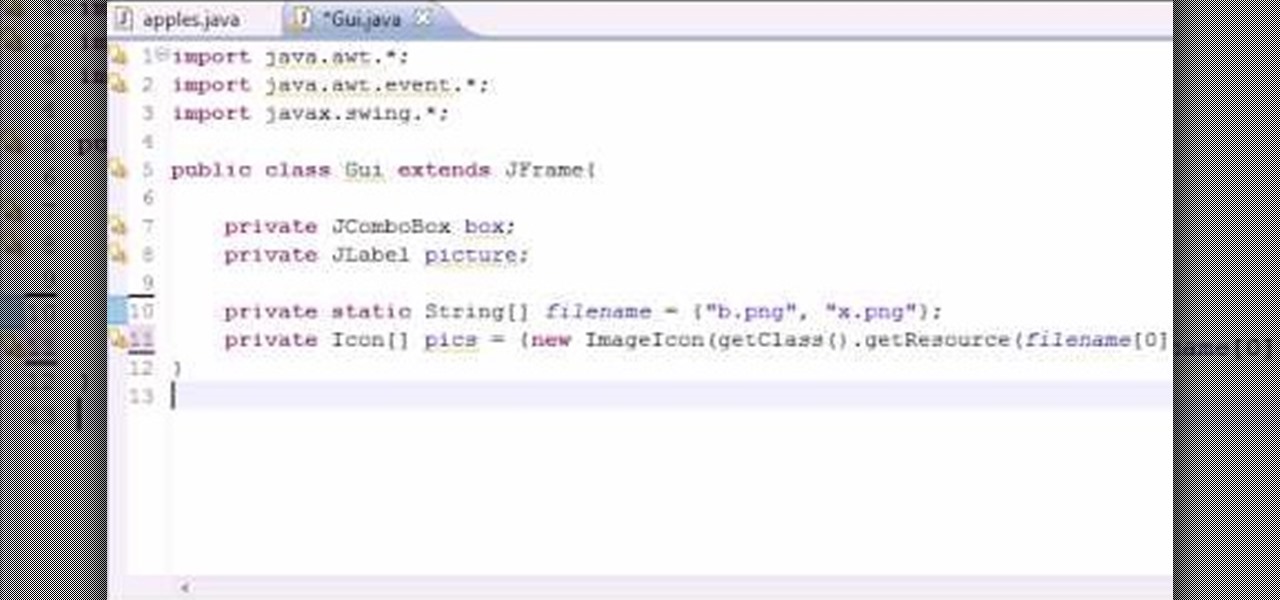
Want to program your own Java games and applications but don't know beans about object-oriented programming? Never you fear. This free video tutorial from TheNewBostonian will have you coding your own Java apps in no time flat. Specifically, this lesson discusses how to work with JComboBox dropdown lists to create GUI drop-down lists when writing code in the Java programming language. For more information, including detailed, step-by-step instructions, watch this helpful programmer's guide.
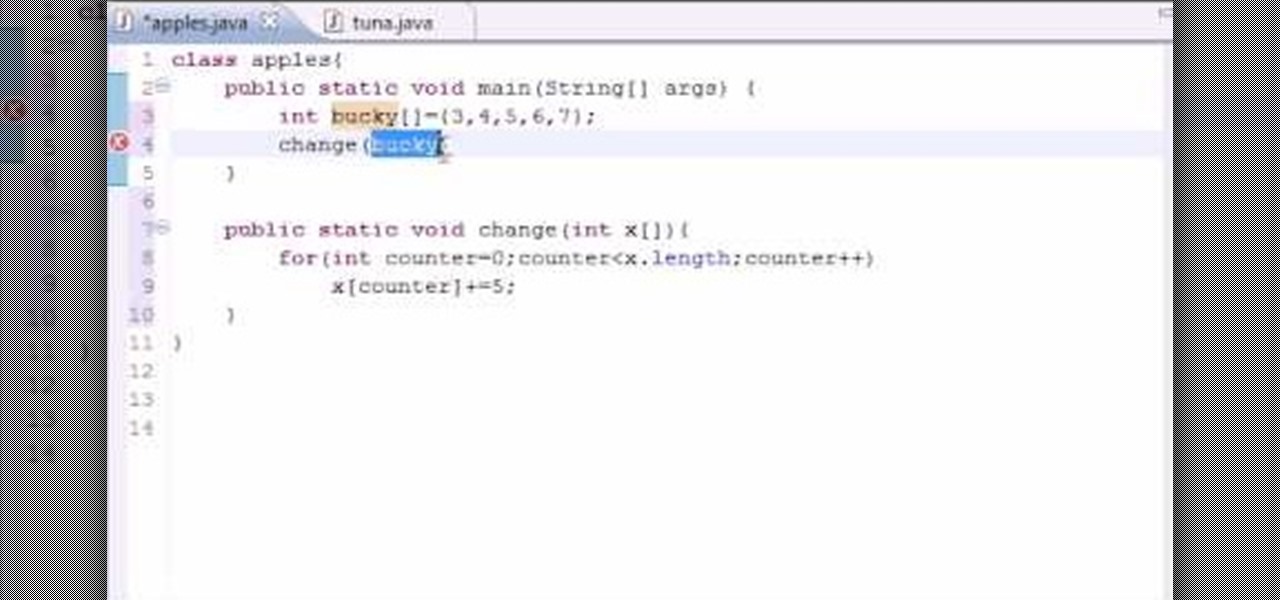
Want to program your own Java games and applications but don't know beans about object-oriented programming? Never you fear. This free video tutorial from TheNewBostonian will have you coding your own Java apps in no time flat. Specifically, this lesson discusses how to pass an array into a method when writing code in the Java programming language. For more information, including detailed, step-by-step instructions, watch this helpful programmer's guide.

Want to program your own Java games and applications but don't know beans about object-oriented programming? Never you fear. This free video tutorial from TheNewBostonian will have you coding your own Java apps in no time flat. Specifically, this lesson discusses how to build and compile a simple "Hello, World" program writing code in the Java programming language. For more information, including detailed, step-by-step instructions, watch this helpful programmer's guide.
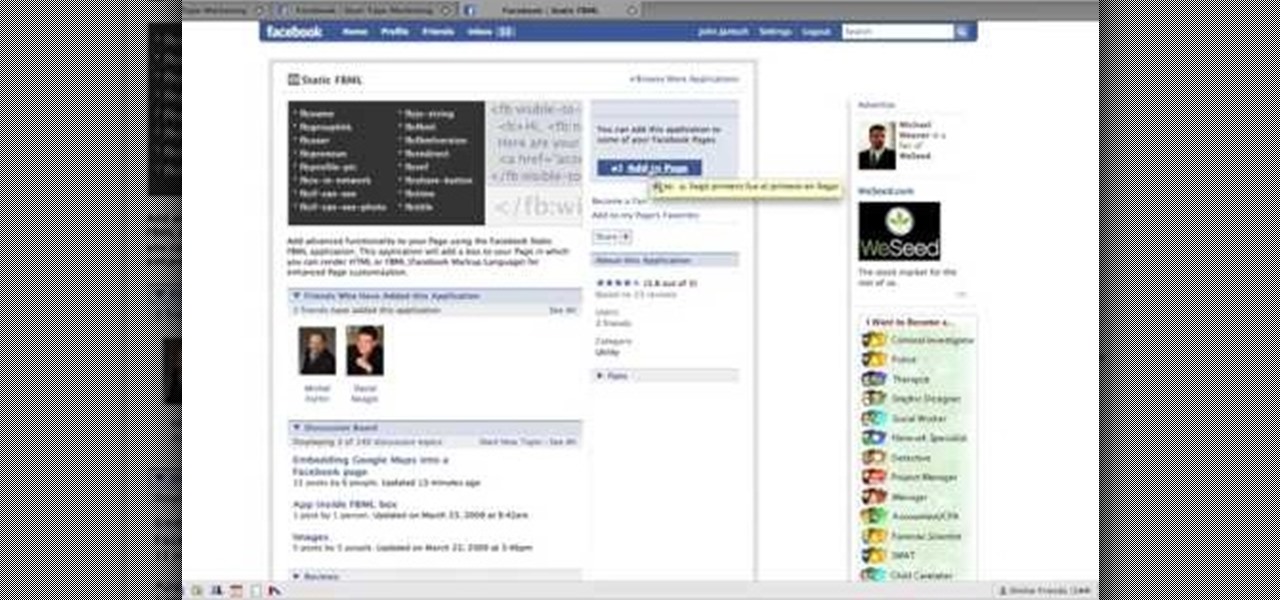
To create custom HTML elements to your facebook fan page or business page, first create a new fan page, and then click on the "boxes" tab. Now, right on the top of the page there's a grey bar, click on the button that says "fbml". Search for the application called "static fbml" and add it to your page. Go back to the homepage of your fan page, and click on "edit page" Find the fbml application and click edit. You'll now have a section where you can put html codes in to create custom web pages...

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

Hashes are commonly used to store sensitive information like credentials to avoid storing them in plaintext. With tools like Hashcat, it's possible to crack these hashes, but only if we know the algorithm used to generate the hash. Using a tool called hash-identifier, we can easily fingerprint any hashes to discover the right Hashcat mode to use to retrieve a password.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

In a previous tutorial, we were able to measure horizontal surfaces such as the ground, tables, etc., all using ARKit. With ARKit 1.5, we're now able to measure vertical surfaces like walls!

The road to becoming a skilled white hat is paved with many milestones, one of those being learning how to perform a simple Nmap scan. A little further down that road lies more advanced scanning, along with utilizing a powerful feature of Nmap called the Nmap Scripting Engine. Even further down the road is learning how to modify and write scripts for NSE, which is what we'll be doing today.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

Locating and abusing files containing unsafe permissions is an easy and surefire way to elevate shell privileges on a backdoored macOS device. This time around, we'll be more aggressive and attempt to phish a user's login password by prompting a convincing popup message merely asking the target for their password.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

While Huawei smartphones haven't always been the best choice when it comes to custom ROMs, one thing that has always been accessible is the ability to unlock the bootloader. An unlocked bootloader is the first step into the magical world of rooting, but after May 24, Huawei will stop offering this service.

Hello, budding augmented reality developers! My name is Ambuj, and I'll be introducing all of you Next Reality readers to the world ARKit, as I'm developing an ARKit 101 series on using ARKit to create augmented reality apps for iPad and iPhone. My background is in software engineering, and I've been working on iOS apps for the past three years.

An awesome new feature appeared in iOS 11 that lets you easily share your Wi-Fi password to anyone else with iOS 11 or higher just by tapping "Share Password" on your iPhone when they try to connect to the same network. However, if your friend is using Android or another mobile OS, this feature doesn't help at all — but there's still an easier way than dealing with long, complicated passwords.

If you want to automate tasks with your smartphone, IFTTT is a great app. It does a tremendous job of helping you find applets or creating your own from scratch, so it's easy to connect your favorite online services and make them react to each other. With all this personal information, though, you should ensure that your data is secure by enabling two-step verification.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

If you've received a spam message in Signal Private Messenger, you know that anyone can contact you as long as they have your linked phone number. But when it comes to the people you're actually trying to have a private conversation with, how do you know it's really them?

Containers are isolated software instances representing applications, servers, and even operating systems—complete with all of their dependencies, libraries configuration files, etc.—and they're taking over the corporate world. The ephemeral, portable nature of containers help them stay current and speedy, and they can work on pretty much any computer, virtual machine, and cloud.

With some of the groundwork out of the way in getting a Mac set up for hacking, it's time to start looking at toolboxes. Our first toolbox is Git, which will be used throughout future tutorials.

Taxi drivers and cab companies across the globe are in an uproar over Uber, and for good reason, too—you just can't compete with the low fares and ease of use that Uber brings to the table. The only downside is that the groundbreaking ride share service usually requires a smartphone—but that shouldn't be an issue anymore with one simple tip that I'll outline below.

Boasting over 800 million users a month, WhatsApp has quickly become one of the most popular messaging services available today. Thanks to its low price, ease of use, lack of ads, cross-platform functionality, and great features, its popularity is well-deserved.

Sometimes specs aren't everything, especially if you prefer value over the bleeding-edge. Enter the ZTE ZMAX, an Android phone that you can get right now for less than $200—cheaper than even the Nexus 5 or OnePlus One. If you're looking for a cheap high-end phone, it's hard to go wrong with one that sports a 5.7-inch display, expandable storage, and a massive 3400mAh battery that'll easily get you through a full day of use.

Band bios have a cherished place in the world of band promotional material. A killer one can do wonders for cultivating your image among your fans and potential employers. This video will give you tips for writing a killer band biography that will get you noticed.

First go to your Wordpress admin and click the "custom file editor" in thesis options. Now copy that code which is showing in the video and paste it in the custom.css file and click on the big green save button. Now select

The Craft ROBO is a machine that lets you cut and score paper with precision and repetition. This is really handy if you're into scrapbooking or want to make shipping boxes, envelopes or promos for your Etsy shop. Perhaps you want to take it to the next level to create unique paper sculptures, pop-up books or custom vinyl stickers.

No downloads or extra programs needed! This video is pure cheat codes, all for playing on Poptropica! You can do fun things like change your skin color, change your hair color and even get the elusive pumpkin hat to wear!

This tutorial for PHP beginners introduces the viewer to the concept of class inheritance. As your coding career takes off, you'll need to know as many ways to work efficently and code with speed to save time and money. Check it!

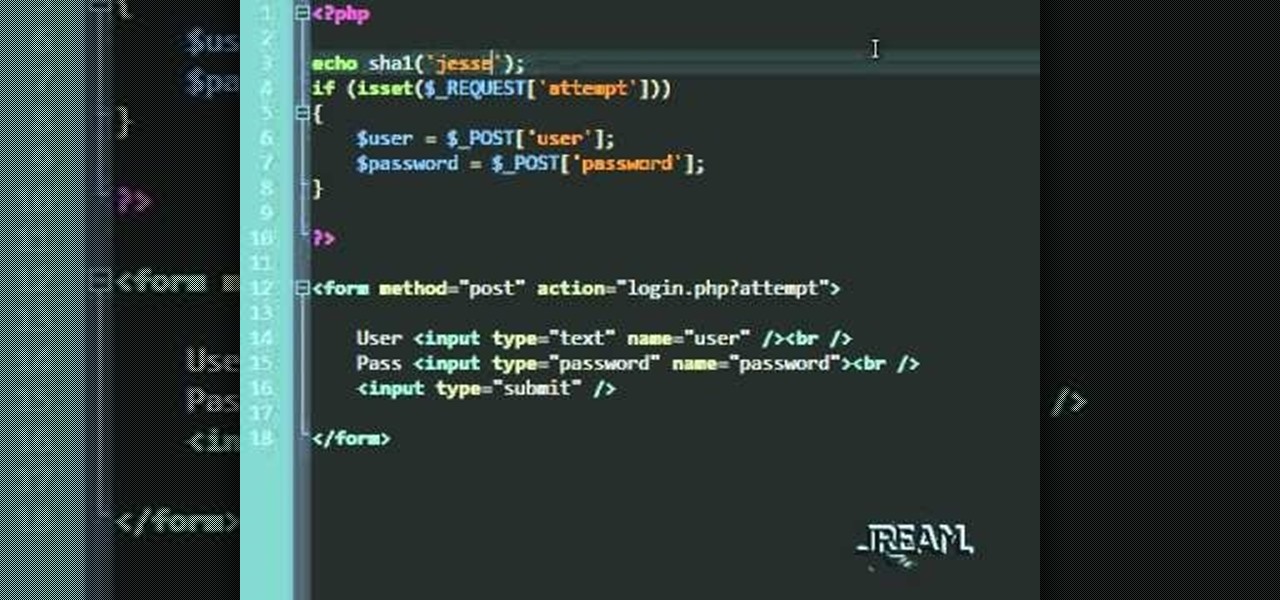
In this tutorial you'll learn about a simple PHP login script that serves to check your MySQL database against a user/password. The code in this video is a quick and dirty procedural code, but it's enough to get you going so you can try it out yourself.

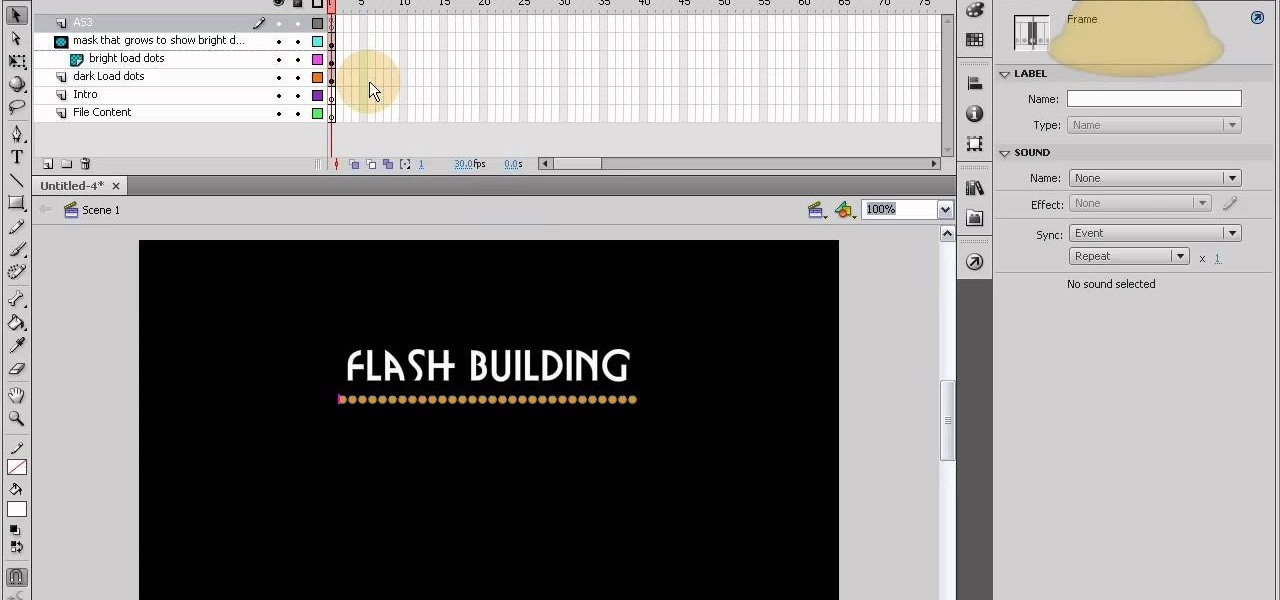
This tutorial shows you how to code an intro sequence for the first page of your Flash-based website. You're also shown how to code a dynamic loader bar, so visitors can easily tell how long the content will take to load in their browser.

A snippet is a piece of code which you may want to repeatedly use (like a login code). Snippets can also be global, which you can apply to every website you have. This tutorial shows you how to store and use snippets in Dreamweaver.

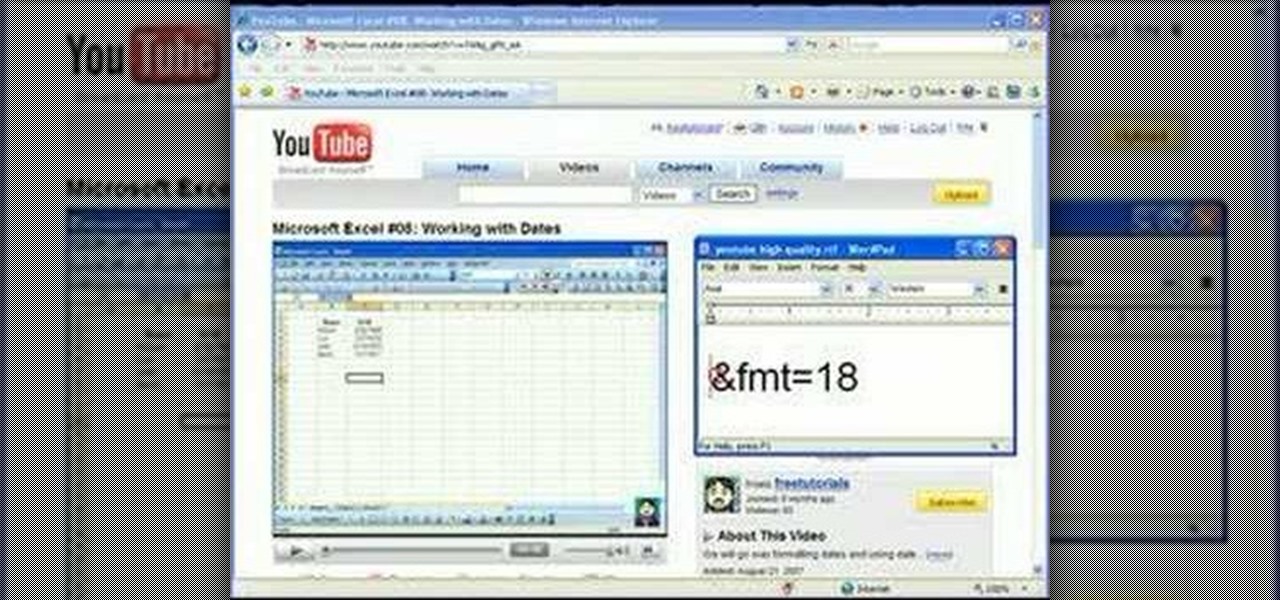
You can improve the quality of the video you watch on YouTube. Sometimes when you watch the video in YouTube, probably you will have notice that the video is little blurry or text which is being shown in that video is blurry like low quality video. So you can improve it by just adding a little code in the url of that video. So put that code "&fmt=18" in the end of the url of that video and press the enter key and that's it. Now you can see the difference between before and now. The video qual...

First go to your word press admin and click on "custom file editor" in thesis options. Select custom_function.php in file selected menu and click on "edit selected file". Because of warning, we need to do it via ftp. So go to that ftp path which is showing in the video and open up the launch.php. Now copy that code which is showing in the video and past it in there, close and save the file. Now to change the style of your search box, go to your custom file editor, select the custom.css and cl...

After running a diagnostics test on a 2002 Jeep Liberty, if you get the code P0442, that means you have an Evaporative Emission Control System (EVAP) leak detected, which is just a small leak, but a leak nonetheless. This video will show you how to smoke test the EVAP leak to find the problem spot inside the vehicle.