In this video tutorial, Scott Golightly shows how to create an ASP.NET HttpModule to “rewrite” the URL when a request for a web page comes in. You may want to rewrite URLs to create friendly URLs or to direct an old URL to a new URL. We will look at the code needed to implement URL rewriting and also how to handle page post back events.

Check out how to read a binary clock in this how to video. You'll see how to read the BCD (binary-coded decimal) format like so many can't. Just watch this if you have trouble determining the hours, minutes, or seconds on your binary clock. You can read it in standard or military time if you'd like.
This shows how to bypass youtubes block on certain characters in video descriptions.. something thats very annoying, especially in How-to/DIU videos that require some codes in the description using nothing more but some simple HTML.

This video explains how to read a tape measure. Discover how tape measures are divided into different fractions. Color coding is also used to help with spacing things 16 inches on center.

Ask the Builder host, Tim Carter, shares a quick lesson to help you out of a tough spot when working with plumbing vent pipe. If you're installing a sink, and need to follow the codes, then just work around it with this trick.

Watch this video to get set up with C++. The video covers creating a project, what to do with the console window, hello world code, and the debugging process.

This tutorial explains how to setup the gps cell phone app. Go to http://www.websmithing.com for the full explanation and source code, you'll find it on the programming menu tab.

Members of the Chicago area gang the Latin Kings explaining their language of symbols and codes expressed through graffiti.

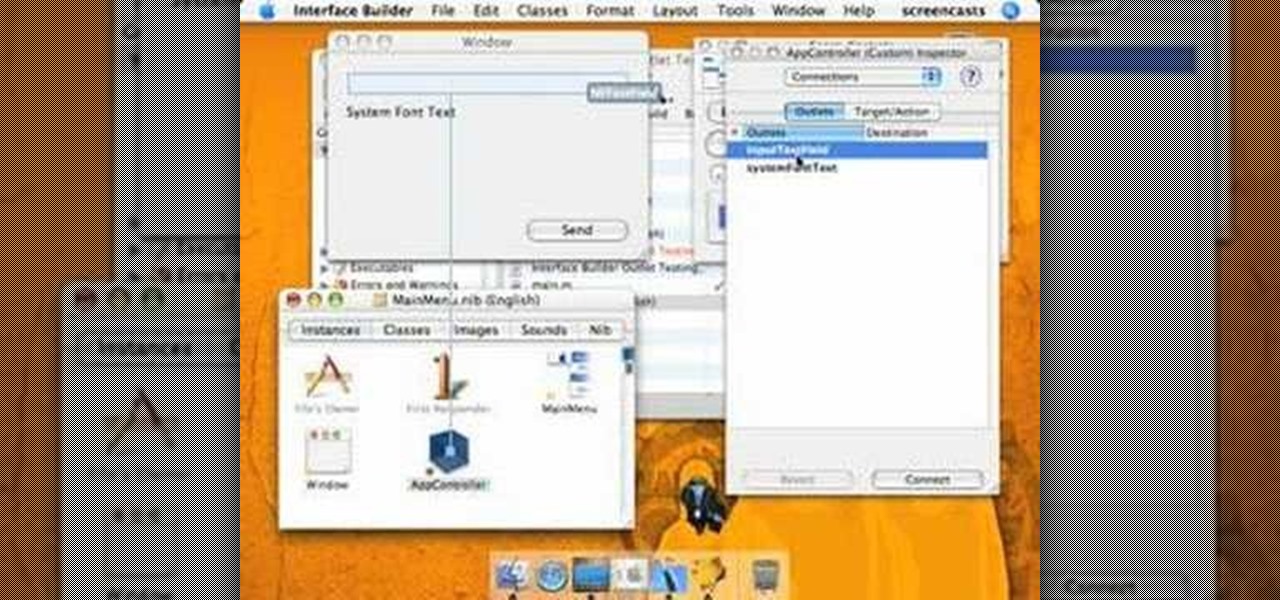
This Xcode video tutorial will help beginners learn how to use Interface Builder to use Objective-C code to interact with UI elements implemented in their Mac OS X applications.

Microsoft Visual Studio 2008 is an integrated development environment that lets you develop websites, web applications, and web services. It requires a bit of computer coding to run (C#, Visual Basic, ASP, C++) and will work on any web server that supports Microsoft.

Austin Chau does a short tutorial about how to use the JavaScript Client Library with the Google Calendar Data API.

This is Anthony Caporale's version of the bloody mary, made in honor of the Da Vinci Code fans. You'll need pepper vodka, citrus vodka, tomato juice, salt, pepper, Worcestershire sauce, olive juice, a squeeze of lime, and garlic stuffed olives for garnish.

In the embed code for a video, you can change certain numbers for the width and height of your video in HTML.

Get closer to God with a hot chick.

Make a getaway from the cops, with a hot chick by your side.

Try some gender bending in Elder Scrolls IV (4): Oblivion and flip the sex of your character. To do so, enter the code ~sexchange.

This sexy chick has all the right moves in Tiger Woods PGA Tour 08 for the Nintendo Wii. Learn a cheat code to unlock all of the clubs in the game.

This busty beauty shows you how to bust out a tiny skater in Tony Hawk's Proving Ground using a code.

To get the girl, you need a hot ride. So here's a cheat code to up your ride in Juiced 2: Hot Import Nights.

Learn how to write a simple prank program that will make someone think that their hard drive is being formatted and completely erased.

Send a little dose of system shutdown to your friends or foes using these codes!

This tutorial will teach you how to make a simple Flash app that uses the microphon using the ActionScript code:

Following the proper electrical code for installing electrical outlets will be shown in this video.

In this video you'll learn how to play "Mr. Jones" by Counting Crows. It's a good song for blending open chords with your bar code F.

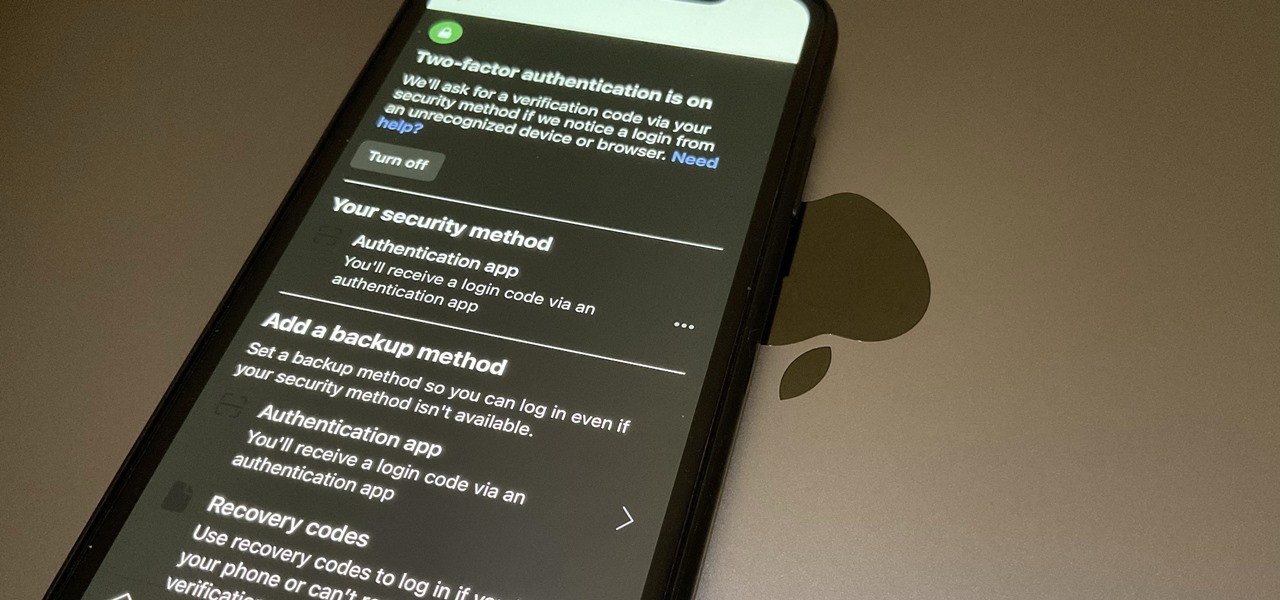
Most websites and apps support two-factor authentication (2FA), which adds an extra layer of security to your accounts by requesting another form of identification beyond username and password. The second factor can be a recovery code, physical security key, or one-time password (OTP) that only you can access, even if someone else has your password. This process is easier than ever thanks to iOS 15.

One of the hardest parts of entering the IT and computer science field — other than the difficult material and intense competition — is the time and financial cost of learning everything you'll need. Learning to code isn't just learning one language; you have to learn a variety of languages used for different purposes, and then you have to get experience using them.

Malevolent hackers can divert your incoming calls and texts to any number they want, and they don't need to be a criminal mastermind to do it. Even friends and family members can reroute your incoming calls and messages so that they know exactly who's trying to reach you, and all it takes is seconds of access to your iPhone or wireless account. These secret codes can help uncover them.

It can feel hard to find time for just about anything these days. But if you really sit down and think about it, you likely have a little more free time in your day than you might actually imagine. The average person has about 4.5 hours of total leisure time over the course of a week.

You're on your computer a lot, so it only makes sense that you download the best apps and software for it. The Official Cyber Monday Mac Bundle Ft. Parallels Pro & Luminar 4 is available for only three weeks at an additional 40% off the sale price of $69.99. Just use the promo code CMSAVE40 at checkout.

PirateBox is a great way to communicate with others nearby when cellular and Wi-Fi networks aren't available. With it, you can anonymously share any kind of media or document and even talk to one another by voice — without being online. However, it needs a Raspberry Pi, which is more expensive than ESP32 boards, and if you only need a text-based chat, there's a much simpler option.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called "Cast All the Things," we can hijack a Chromecast to play nearly any kind of media with a single command in terminal.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.