
Promo Codes Search Results

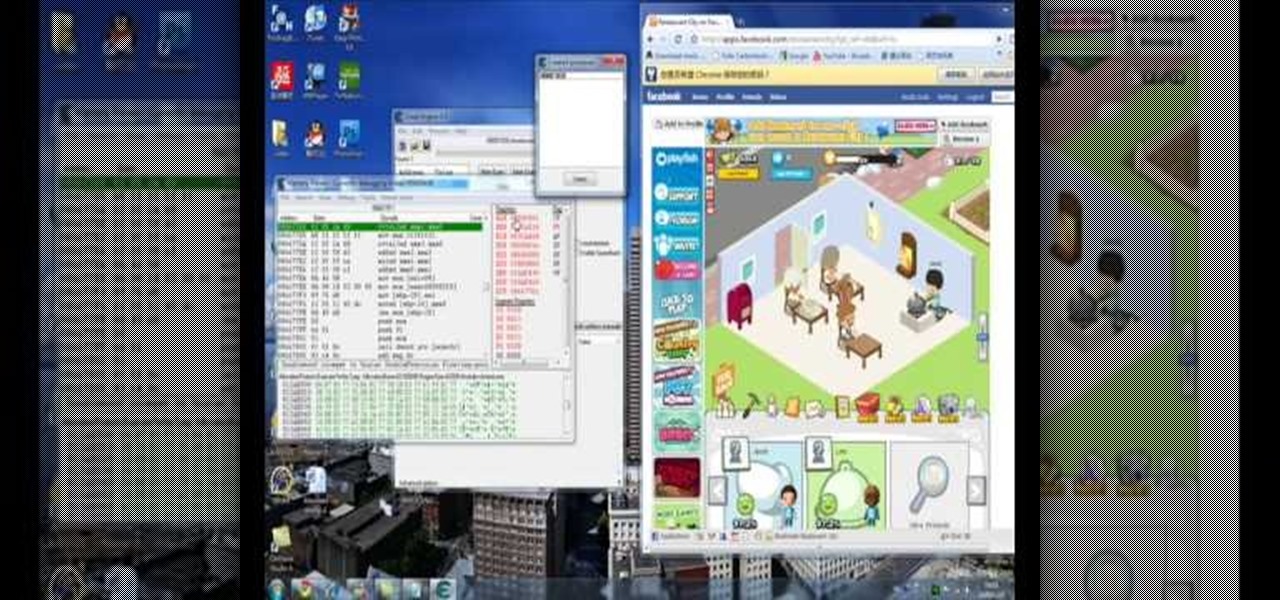
How To: Hack levels in Restaurant City (12/05/09)
Open up Cheat Engine and be prepared to hack Restaurant City! This is a new level hack that will help you gain levels fast.

How To: Set Up Contact Key Verification for the Highest Level of iMessage Security
Your iPhone is fairly secure by default, but Apple's Lockdown Mode takes it to Fort Knox levels of protection. If you're a high-value target for spyware, phishing attempts, and other sophisticated cyberattacks, it's an essential feature. But for almost everyone else, it's an extreme move. If you simply want to verify someone's identity when chatting, Contact Key Verification is a more practical option.
How To: Lock Down Your DNS with a Pi-Hole to Avoid Trackers, Phishing Sites & More
The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.
How to Hack with Arduino: Tracking Which Networks a Mac Has Connected To & When
A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

News: Snapchat Smile Rater Lens Helps You Work on the Perfect Selfie Smile
For Snapchat users wondering if that selfie is ready to send to their crush, independent Lens Studio creator Andrew Mendez created a handy tool called the Smile Rater.

How To: Safely Launch Fireworks Over Wi-Fi with an ESP8266 Board & Arduino
Fireworks are the best part about the Fourth of July and other celebrations, but they can easily cause accidental injuries. It's both safer and more fun to set them off remotely, so we'll hack some standard fireworks with nichrome wire, a relay, and an Arduino to ignite remotely over Wi-Fi using any smartphone or computer.

How To: Create Packets from Scratch with Scapy for Scanning & DoSing
By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.
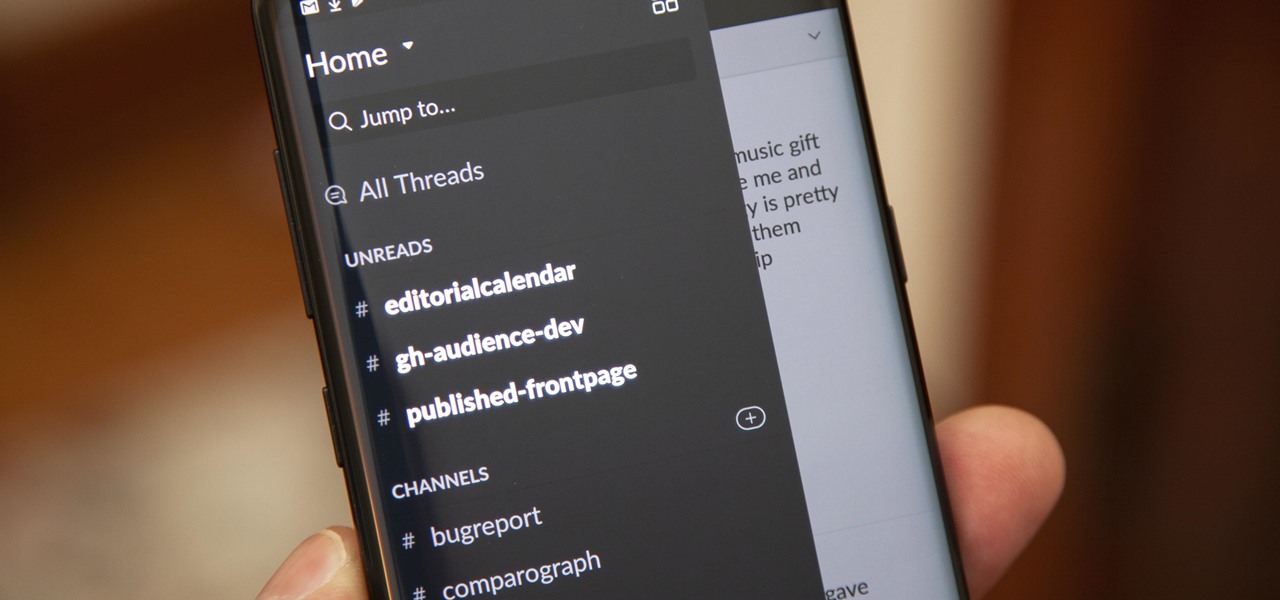
How To: Get Slack's Sidebar to Work with Dark Mode on Your Phone
Slack recently released a dark mode for its Android and iOS apps, and for the most part, it works great. Super dark gray backgrounds and light gray fonts, which is much easier on the eyes than blinding white backgrounds and black text. But there's one thing that is not affected by the new night mode setting — your sidebar.
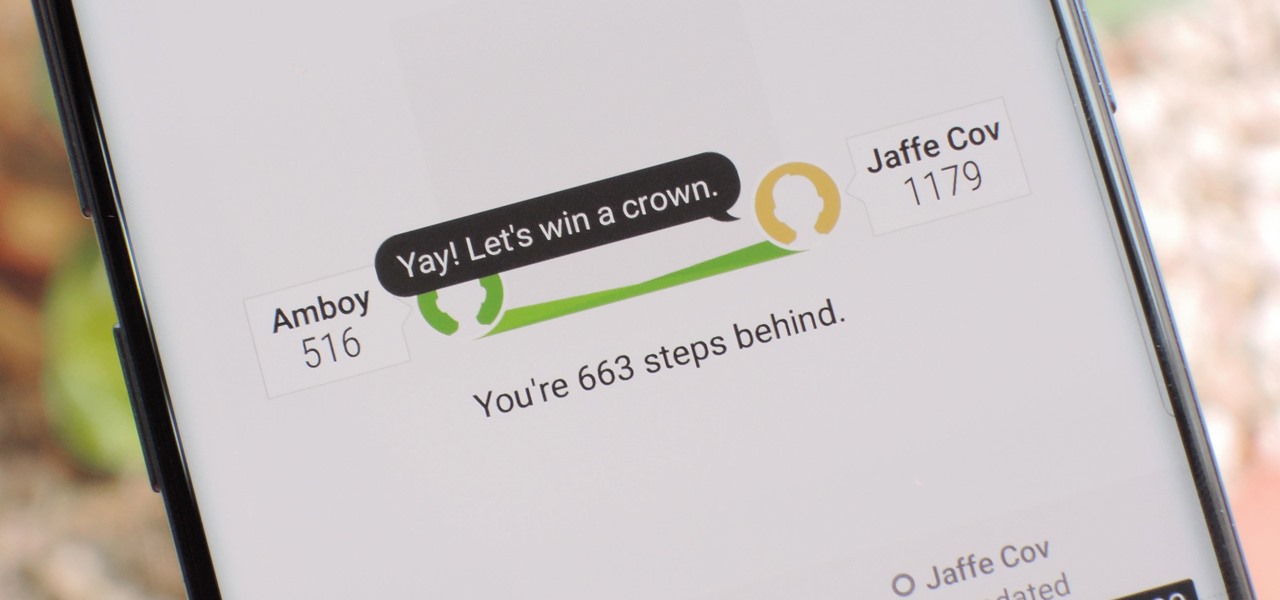
How To: Start a Fitness Competition Among Friends with Samsung Health
When you're trying to get fit, friendly competition can go a long way towards keeping you motivated. Samsung Health has a great feature for just that, letting you challenge your friends or even complete strangers to bring some excitement to an otherwise routine workout experience.
News: 4 Ways the OnePlus 6T Makes Rooting Easy
With the same starting price as its predecessor and a nice list of improvements, the OnePlus 6T is a great buy for a number of reasons. But for many Android users, the main selling point for the latest OnePlus flagship is how easy it will be to root and mod the device.

Hacking macOS: How to Spread Trojans & Pivot to Other Mac Computers
It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

How To: Use Maltego to Fingerprint an Entire Network Using Only a Domain Name
Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

News: Renault Uses Shazam AR to Harness the Latest Star Wars Movie Hype
French automaker Renault is tapping into the promotional machine for Solo: A Star Wars Movie by deploying an AR experience through Shazam that's triggered via synergistic advertising.
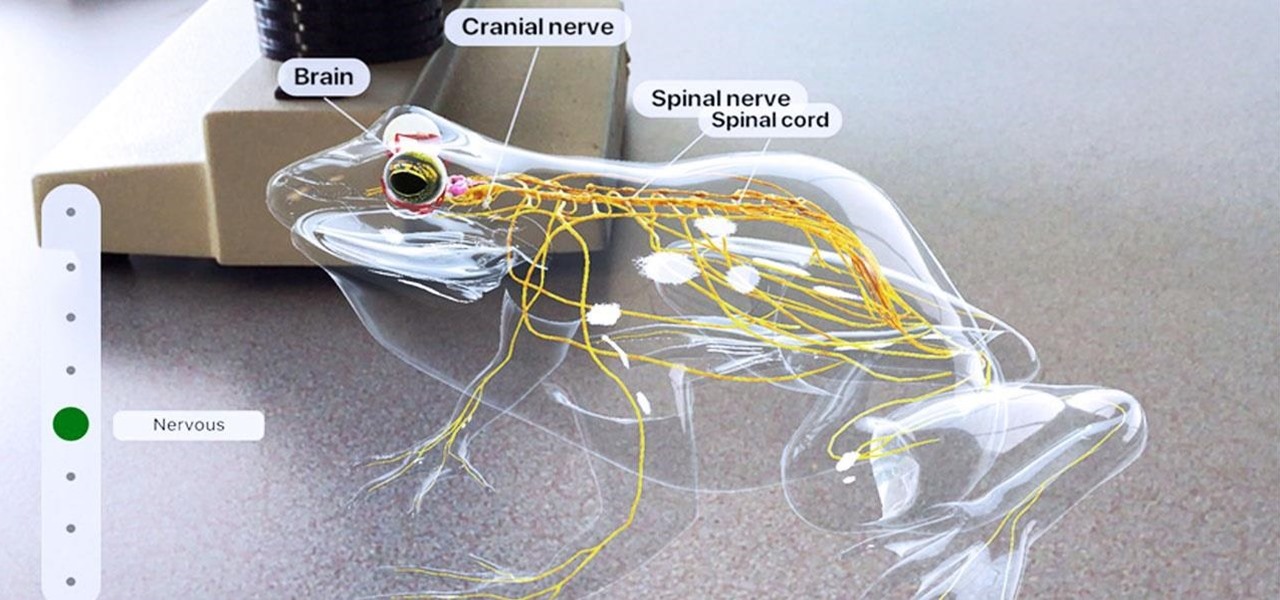
News: Apple's Education-Focused iPad Event Pushes Augmented Reality Further into the Classroom
At Apple's education event in Chicago on Tuesday, augmented reality stood at the head of the class among the tech giant's new offerings for the classroom.

How To: How Hackers Use Hidden Data on Airline Boarding Passes to Hack Flights
Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

News: Metaverse Lets Anyone Program Their Own AR Games
Thanks to Metaverse, it has never been this easy to create your own AR game.

How To: Exploit DDE in Microsoft Office & Defend Against DDE-Based Attacks
In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.

How To: Fully Anonymize Kali with Tor, Whonix & PIA VPN
Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

News: Zappar Pitches Baseball AR Mini-Game for Wise Snacks
Wise Snacks wants baseball fans to reach for potato chips instead of peanuts and Cracker Jacks, and it's calling augmented reality out of the bullpen to close the deal.
The Clone Wars: The Russians Flirt with Instagram & Fake Follower Vending Machines
From Instagram bot farms in China all the way to vending machines in Moscow that promise to sell you fake followers — the Facebook-owned empire is attracting the attention of the world around. When it comes to Russia especially, the country seems to be developing a little crush on the glorious IG queen.

News: Google Allo's Latest Update Adds Chat Backups & Group Incognito Mode
Google's Allo is still a work in progress, but the innovations to the chat and messaging app just keep on coming. The latest update rolling out now includes chat backups and a group incognito feature that we're very excited about.

How To: Set Up Kali Linux on the New $10 Raspberry Pi Zero W
In five short years, three generations of ultra-low-cost Raspberry Pi devices have challenged the boundaries of what a person can do with a $35 computer — especially with Kali Linux.

News: Project Halium Could Open the Floodgates for Non-Android Custom ROMs
Rooting a phone lets us install custom operating systems, known as ROMs, which replace the device's preinstalled OS. Most custom ROMs are based on code from the Android Open Source Project (AOSP), which gives them a look and feel similar to Google's version of stock Android. But every now and then, you'll see a ROM that isn't based on Android, though these are few and far between — at least, until now.

News: Project Zero Finds iPhone & Android Open to Bugs in Broadcom's Wi-Fi Chips
No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks.

News: Shazam Sets Sights on AR Advertising with iPhone & Android App Updates
The company that pioneered music scanning for mobile devices is moving into the augmented reality advertising arena. Included in an update of their iOS and Android apps last week, Shazam can now scan special codes to immerse users in 3D animations, 360-degree videos, mini-games, and other AR content.

News: Snapchat Continues to Find Fun New Ways to Turn Ads into Enjoyable Experiences
Snapchat has already found a compelling way to create advertisements in augmented reality with their branded filters, but they continue to experiment with new ways to monetize the bridging of the real and digital worlds. Their latest idea, which requires users to "snap" an image to unlock content, could succeed where QR codes haven't.

News: Google's New Home Assistant Is an Amazon Echo Killer
Google first introduced Google Home, its latest smart product in the works, at the company's I/O conference in May 2016. It will directly compete against Amazon's Echo, which has so far been a success with over 3 million devices sold, and it was even featured as FBI Agent Dom's only real friend in the second season of Mr. Robot. Google may have their work cut out for them, but we're betting Home will knock Echo out of the water. Google Home is a personal assistant with a built-in speaker and ...

PHP for Hackers: Part 1, Introduction and Setting Up
In this series you will learn how to use PHP to perform attacks, gather information, and setup backdoors. Along with performing attacks you will learn how to protect yourself from them. In this part you will learn about PHP as well as install Apache and PHP. What you'll need for this series
News: Night Mode Is Coming to Android!
For years, users have been clamoring for a "dark mode" theme in Android, but it has always seemed like Google is so committed to the white motif from their web services that such an option would never become a reality. But in a stunning turn of events, Google is finally embracing the idea with a night theme that will work in any app, and I'll cover all of the specifics below.

Raspberry Pi: WiFi Analyzer
It has been a while since my last Raspberry Pi tutorial , but now I am back with another tutorial. This one I should note isn't your typical tutorial, but as always lets boot up our Pi and wreck havoc.

News: Next iPhone Could Be Li-Fi Compatible, Up to 100 Times Faster Than Wi-Fi
A few lines of code in the iOS 9.1 library cache found by Chase Fromm (@uloshe) indicate that Apple could be working on making iPhones that are Li-Fi compatible.

How To: Program Your Own Little RAT (Part 1) Getting the Server Working
I saw many people asking for a Tutorial about writing their own Remote Administration Tool, so I now introduce you in a basic kind of RAT. This program is not for real use, but for learning how you could write this kind of tool. It will be basicly coded and not very refined. I used Python 3, so you have to install it if you want to use this program unchanged. Also this RAT is for Windows and almost all features won't work under Linux.

How To: Security-Oriented C Tutorial 0x13 - Pieces of a Puzzle
Before we begin learning about another vulnerability, we are going to explore printf in a bit more detail. This will be quick little tutorial.

Don't Be a Script-Kiddie part2: Building an Auto-Exploiter Bash Script
Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.

How to Train Your Python: Part 1, Introduction
Recently I've been looking around our wonderful community and I've seen some absolutely hands-down fantastic python scripting articles. But, in the end, these series weren't very extensive. I've been wanting to do a series on teaching python for a while now, and I don't mean just the basics, I mean to make an extensive series that takes it all the way from "Hello, World!" to popular third party modules, and everything in between!
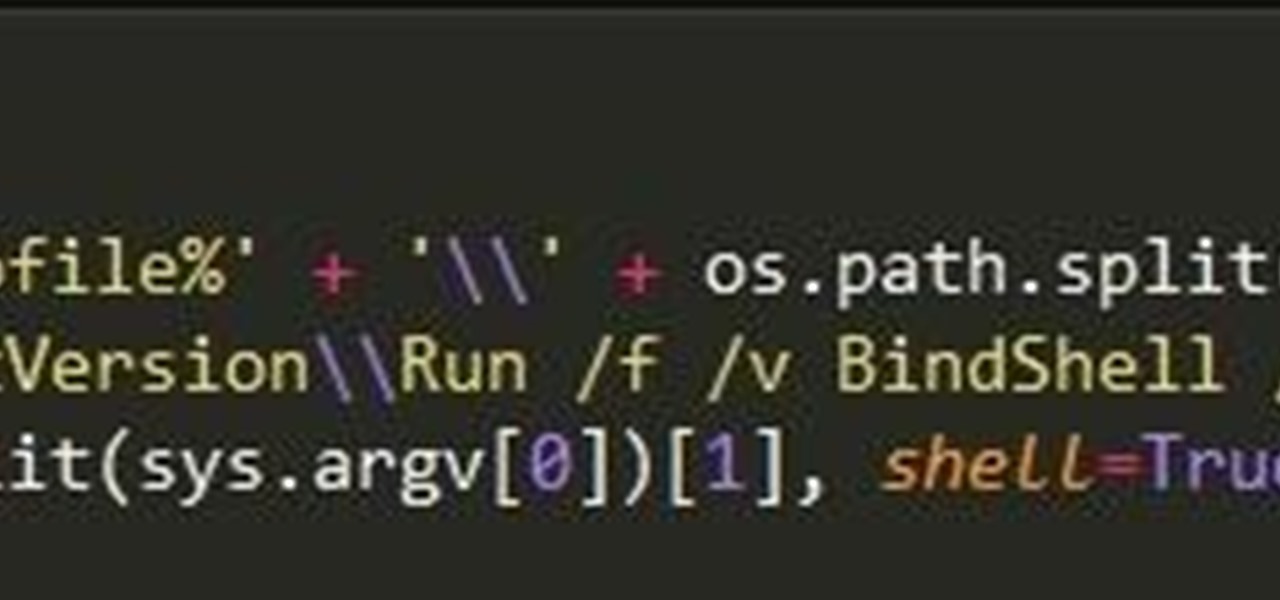
How To: Create a Bind Shell in Python
Hi guys, I'm gonna keep this short because I got assignments and a lot of notes to study and also other how-tos and forums to reads. lol...Since I'm keeping this short...no story time just scenario. And I want to thank n3stor for giving me the idea to post this.

How To: Send Anonymous Emails with Python
Hello fellow grey hat hackers, as hackers it becomes necessary for us to be able to send emails anonymously. Whether for whistle blowing or pranks or social engineering or whatever, it just is necessary for us to do that.

How To: Set Up & Use Apple Pay on Your Apple Watch
As you're probably well aware by now, the Apple Watch isn't just for sending text messages and checking Instagram—you can also use it as your wallet. With Apple Pay compatibility, you can use your Watch to make purchases at any retailer that accepts the payment service.

How To: Make iPhone Navigation Prompts Play Over Your Car Speakers When Listening to the Radio
Maps is great for making sure you always get to your destination, until you miss that critical turn because you couldn't hear the turn-by-turn directions.

