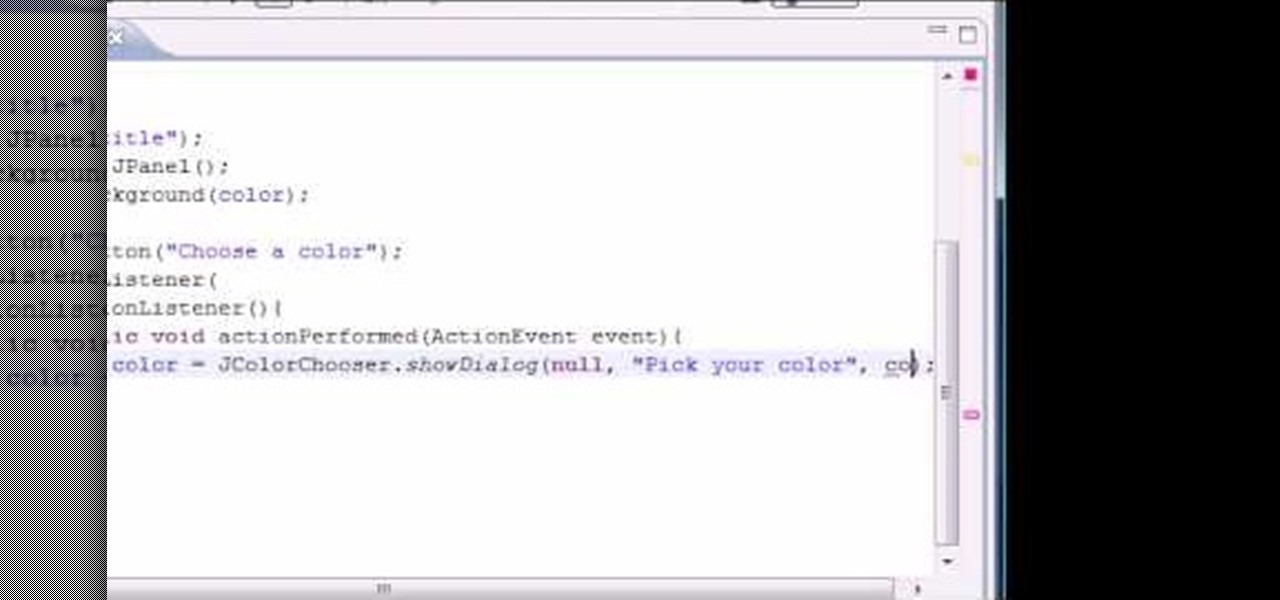
Want to program your own Java games and applications but don't know beans about object-oriented programming? Never you fear. This free video tutorial from TheNewBostonian will have you coding your own Java apps in no time flat. Specifically, this lesson discusses how to implement and use the JColorChooser control pane when writing code in the Java programming language. For more information, including detailed, step-by-step instructions, watch this helpful programmer's guide.
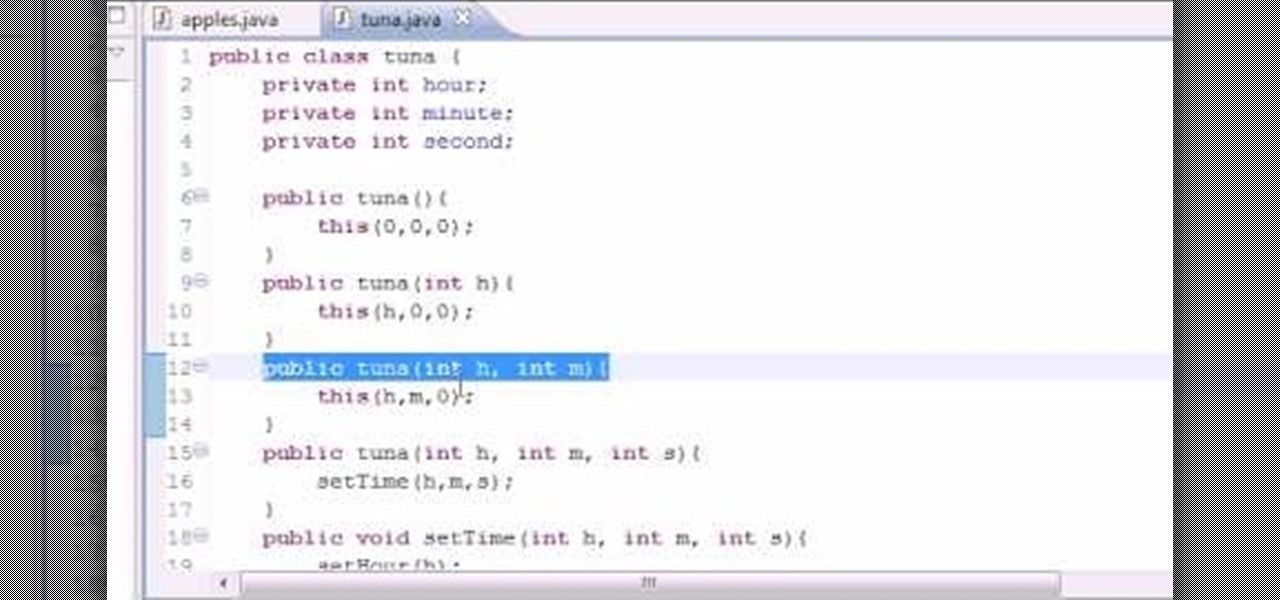
Want to program your own Java games and applications but don't know beans about object-oriented programming? Never you fear. This free video tutorial from TheNewBostonian will have you coding your own Java apps in no time flat. Specifically, this lesson discusses how to build objects for multiple constructors when writing code in Java. For more information, including detailed, step-by-step instructions, watch this helpful programmer's guide.
Managing your busy schedule just got easier in Entourage 2008 for Mac. Using the powerful Entourage Calendar feature lets you organize your time wisely. The Microsoft Office for Mac team shows you just how to organize your schedule with the calendar in this how-to video.
Make sure you use FLASH Player 9 First: Deinstall Flash Player 10
Mike Lively of Northern Kentucky University shows you how to build an interactive Molecule Viewer in Papervision3D and Flex 3. This is a fun application building project for anyone learning Adobe Flex Builder 3 and a great resource for molecule viewer for students, educators, and researchers in chemistry and biochemistry.

Looking for some fun cheat codes to get some extra fun out of your game of Grand Theft Auto: San Andreas? These codes are specifically for Playstation users. Make cars fly or float away when they get hit, or enter into Chaos Mode!

If you have created a product that you want to sell, getting a UPC code for it will allow you to track purchases and give your business a more professional air. This video will explain how you go about getting a UPC code and using it to help your business.

Google loves their little Konami Code Easter eggs. The Konami Code is famous among gamers for letting you cheat in video games. The latest one they come up with lets you try it out on Google Docs. All you have to do is open up Google Docs, and type in with the following keys: up, up, down, down, left, right, left, right, B, A, and then enter!

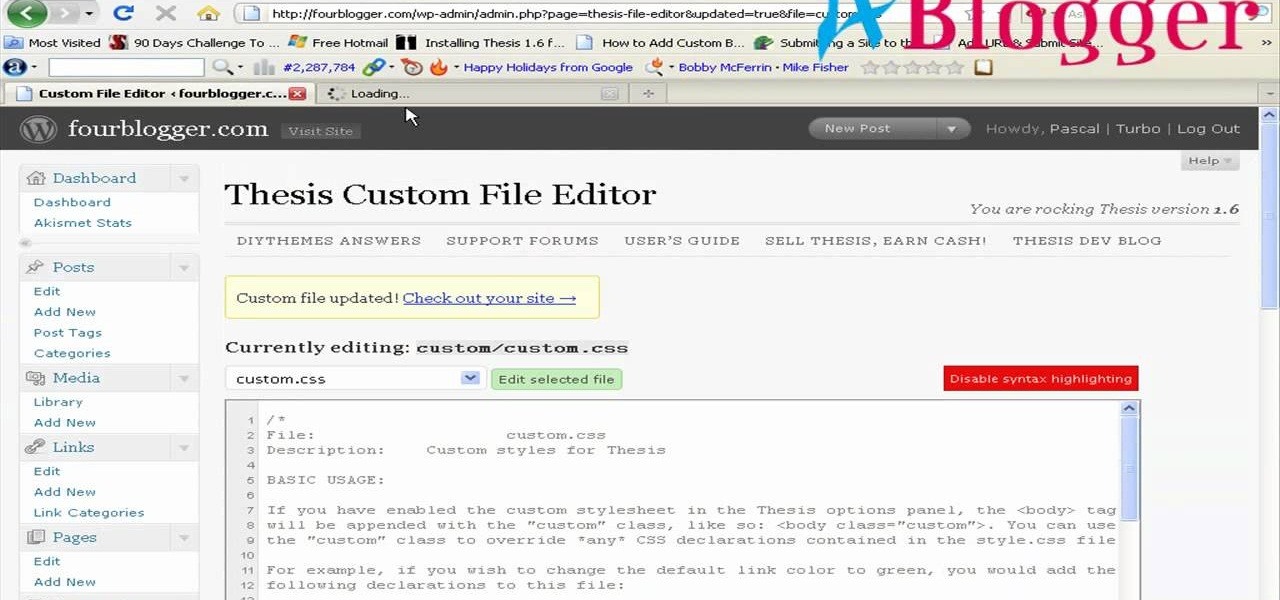
First you need to go to your site and click any post you want and see the simple heading and now you want to change the background. To do this, first you need to go to your word press admin and then click custom file editor in thesis options it will open your code window and here you will have to paste the code which is showing in the video. you will have to paste it in custom.css. After pasting the code you have to click the green save button.

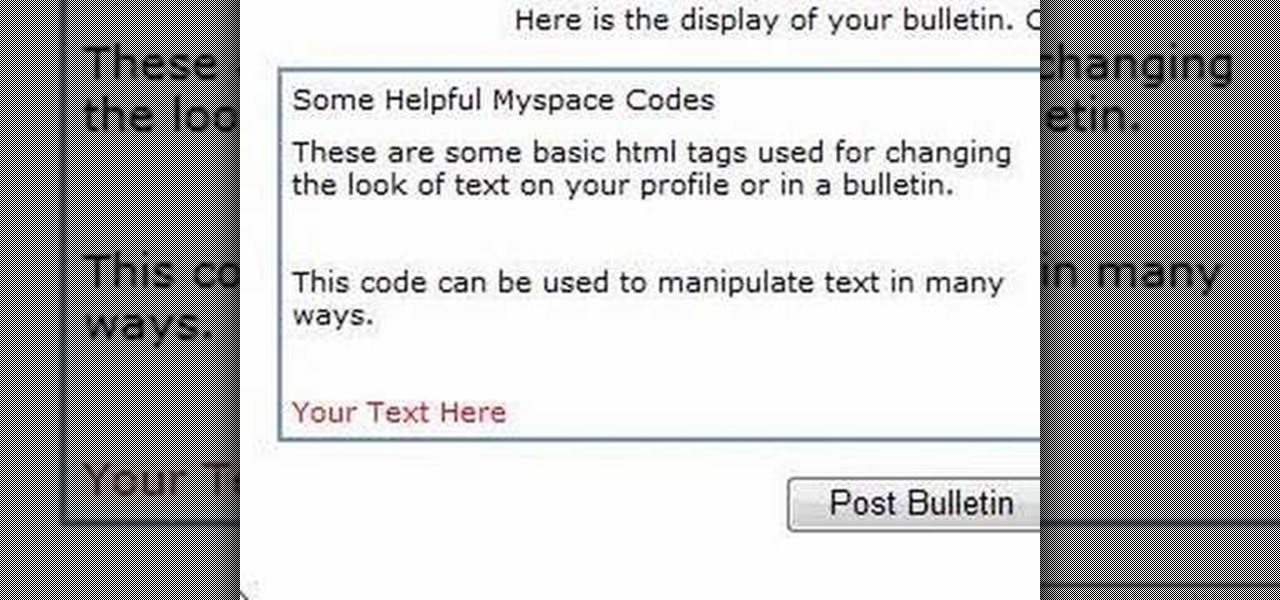
In this Computers & Programming video tutorial you will learn how to alter text on MySpace using HTML codes. Here are a few basic html codes used to change the look of text on your profile or in a bulletin. <b> for starting bold text and </b> for ending bold text. <i> this text will be italicized</i>. For underlining text use the code <u> </u>. <b><i><u> This text will be bold, italicized and underlined </b></i></u>. To change color of your text to ‘red’ use the code <font color=”red”> </font...

This video demonstrates how to import XML code from the Internet into Movie Maker. The video shows you how to find the XML code on the Internet, how to download it, and how to import it into Movie Maker.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a tool called Arjun can be used to discover hidden HTTP parameters in web apps.

Being stuck inside for the near future is less than ideal, but at least you have the world of eLearning to sharpen your skills while you kick back on your couch. Case in point, The 2020 Premium Learn To Code Certification Bundle has all the training you need to start coding like a pro right at home, and it'll only cost you $39 today.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

For anyone interested in using cheap, Wi-Fi-connected microcontrollers like the ESP8266, the Arduino programming language can be a barrier to entry. Based on C++, Arduino requires knowledge of more computer science than languages like Python. Fortunately for beginners, setting up MicroPython on an ESP8266 allows anyone to write Python on affordable microcontrollers in a matter of minutes.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

One of the first steps in attacking a web application is enumerating hidden directories and files. Doing so can often yield valuable information that makes it easier to execute a precise attack, leaving less room for errors and wasted time. There are many tools available to do this, but not all of them are created equally. Gobuster, a directory scanner written in Go, is definitely worth exploring.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

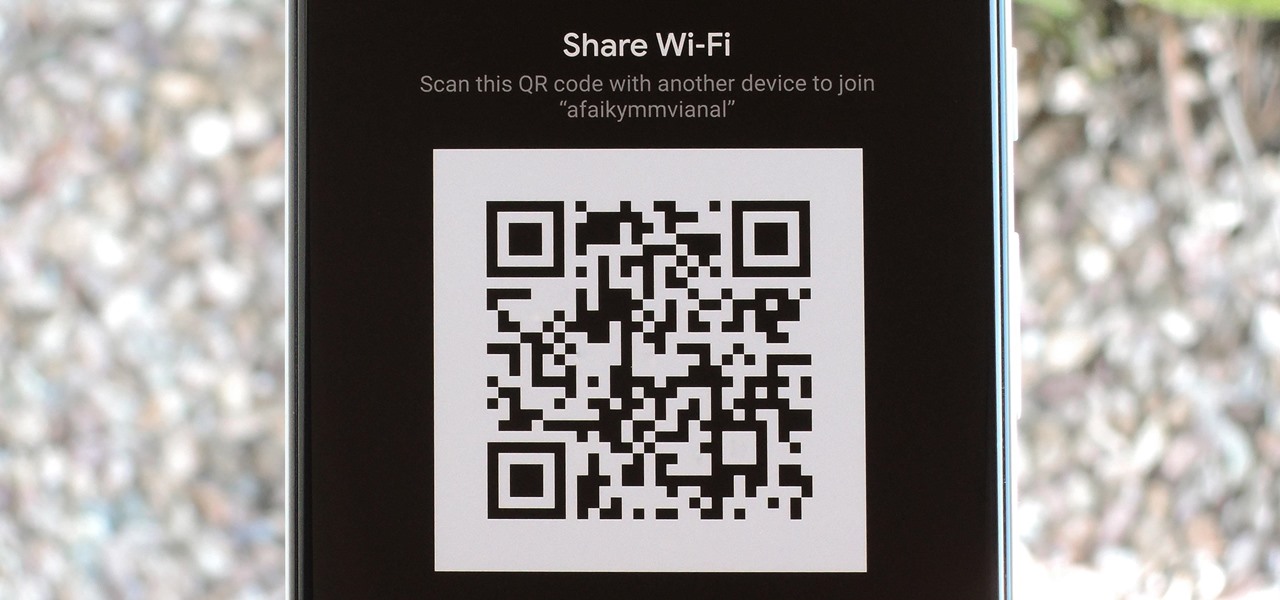
If your phone is running Android 10, you can now share your Wi-Fi network with friends using a handy QR code. The other person doesn't have to be running Android 10 — in fact, you can even share this code with iPhone users. In most situations, this is now the fastest way to share your Wi-Fi password.

Two-factor authentication (2FA) is a great way to add another layer of security to sensitive third-party apps and websites like Venmo. However, before iOS 12, to log into a particular 2FA-secured app or site on your iPhone, you'd have to memorize or copy the SMS code from Messages, then jump back in a timely manner to log in. Apple's latest iOS version streamlines this process.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

There's a feature in the Gboard keyboard that enables people who cannot talk, type, or swipe normally to still have a way to communicate in the digital age on their smartphones. While it's mainly an accessibility feature for those who actually need it, it's a good way for anyone to learn or brush up on their Morse code skills — and it works on both Android and iOS.

Using Hydra, Ncrack, and other brute-forcing tools to crack passwords for the first time can be frustrating and confusing. To ease into the process, let's discuss automating and optimizing brute-force attacks for potentially vulnerable services such as SMTP, SSH, IMAP, and FTP discovered by Nmap, a popular network scanning utility.

The first question people ask me when they come to my apartment is usually "What's your Wi-Fi password?" While I'm happy to give my friends free access to the internet, it's hard to walk each person through my secure password. Luckily, there's a way to create a QR code that will let people easily connect to a Wi-Fi network.

In the last tutorial, we learned how to make functions and how they work on the high level. This time, we will take a peek under the hood again, stare deep into its soul and see its ugliness face to face to see how it works in the lower level.

This is my first ever how-to so I apologize in advance for any grammar mistakes or spelling errors. Introduction

This is the first installment in a new series that I am calling "Hacker Hurdles." These are things, methods, techniques that make our job as hackers more challenging and difficult. Don't misunderstand me, these items don't make our task impossible, but rather more challenging and, therefore, more gratifying when we are successful. One of the most important new hurdles for hackers is DEP and ASLR. Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) are designed to pre...

As great as the Internet is, it is not without its dangers. Hackers at any time may be breaking into your online accounts and compromising your sensitive information. Last year, hackers broke into Facebook, Gmail, and Twitter and made off with 2 million stolen passwords.

If you want to embed a video on your website and customize the player so it doesn't look like crap, you've come to the right place:

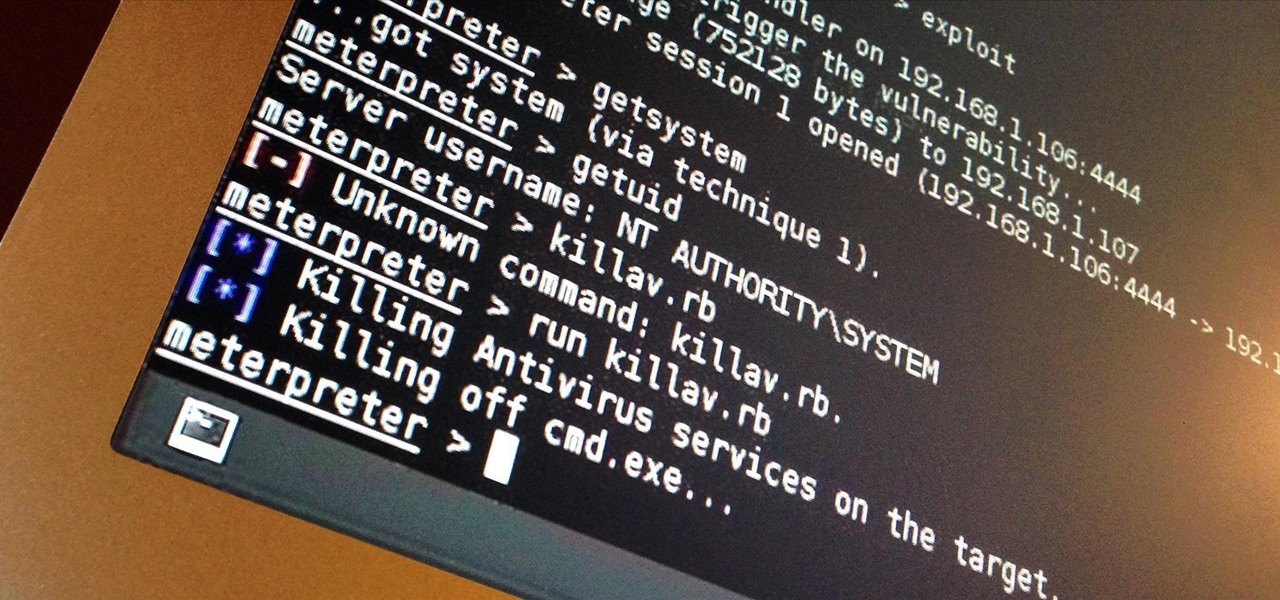
I've done numerous tutorials in Null Byte demonstrating the power of Metasploit's meterpreter. With the meterpreter on the target system, you have nearly total command of the victim.

One of the first things most people ask for when staying with a friend is the password to the Wi-Fi network. Even if you trust your friends to the end of the earth, a super secure password can be a pain to share with them, especially if it's just a bunch of random characters.

While becoming the next Mark Zuckerberg may be out of reach for someone just getting introduced to code, the skill has never been more valuable. Just understanding basic programming language is a great thing to put on your resume, and if you know how to code, you’re golden. Software developers and programmers have been the most resistant to the recession, as jobs in the tech industry continue to grow.

How to draw Lelouch from Code Geass. Follow step by step tutorial of Lelouch from Code Geass. Lelouch's trademarks are his ebony hair, and violet eyes, which he inherited from his mother, and father respectively. Hope you enjoy watching this tutorial! For the full tutorial with step by step & speed control visit: how to draw.

Bettie Page was the ultimate pin up girl. Naturally curvaceous and blessed with batty eyes and full lips, Page was adored by men all over and had women copying her every hairstyle and makeup look. It's no wonder, then, that we still see so many interpretations of her signature pompadour hair look today.

Make a Spark frame ripper

Error code P0401 on a 2004 Ford Focus indicates EGR Insufficient Flow, which usually means your DPFE sensor needs to be replaced. If you're not sure though, and you shouldn't be, watch this video to learn how to perform a test that will make sure your DPFE sensor is actually broken before you replace it.

Facebook has provided developers with a whole library of code usable for creating applications. This tutorial shows you how to get the code, and then how to use it so you can start developing your own Facebook apps using Adobe Flash and Action Script

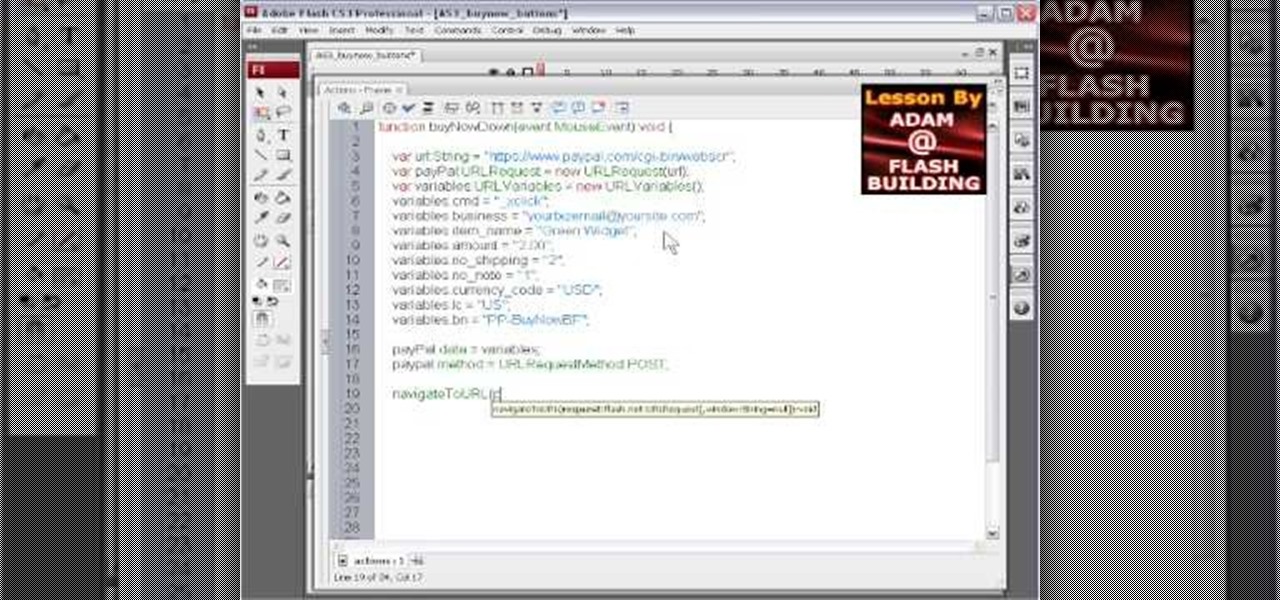
Add an extra level of security to your website by creating your own dynamic 'Buy It Now' button for PayPal-using visitors to your website. Coding this button is very easy, and you can even animate it to draw more attention to your webstore.

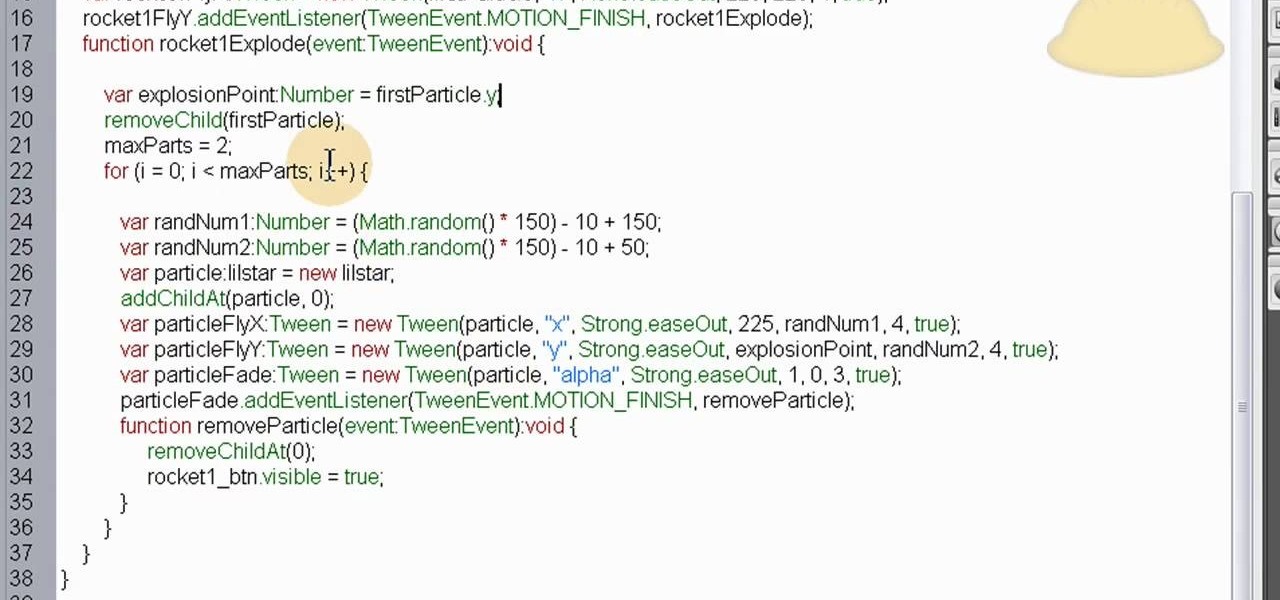
This is a custom particle effect, coded using ActionScript 3, that will recreate the effect of a rocket and fireworks explosion. The effect is also randomized, so you'll never get the same animation twice. This tutorial shows you how to code this effect using Fireworks.