You gotta love Android—not only can you replace your default home screen entirely, but there are tons of options that provide alternative methods for launching apps with ease. We've covered some of these options in the past, including an app called Bar Launcher that lets you launch apps from your notification tray—but that one's starting to look a little dated these days.

The first time a friend or family member asks if they can borrow your phone or tablet, you probably just hand it over without a second thought. But the second, third, and fourth times? Now it's starting to become a habit, and something probably needs to be done about it.

A couple days back we told you about the 30-day free trial for people interested in YouTube Red, and now Google is running a concurrent promotion that really sweetens the deal, especially if you're a first-time subscriber and own or plan to buy a Chromecast.

When you hand your unlocked iPhone to somebody so they can use the internet real quick, check out some cool photos, or do whatever, there's a possibility that they could snoop around where they don't belong. If you have some secret recipes, login credentials, intellectual property, or other sensitive information in your notes, you'll want to add some protection to them.

Last month, it was revealed that Juniper Networks' routers/firewalls were hacked. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all confidential communications by U.S. government agencies and officials could have been compromised over the last three years.

Before we begin learning about another vulnerability, we are going to explore printf in a bit more detail. This will be quick little tutorial.

When they were purchased by Google back in 2011, Motorola underwent a sweeping change in software philosophy. All throughout the UI on their flagship devices, edgy design patterns were replaced by clean, minimalist interfaces akin to vanilla Android. This philosophy has continued on as Motorola's signature, even though they have since been sold to Lenovo.

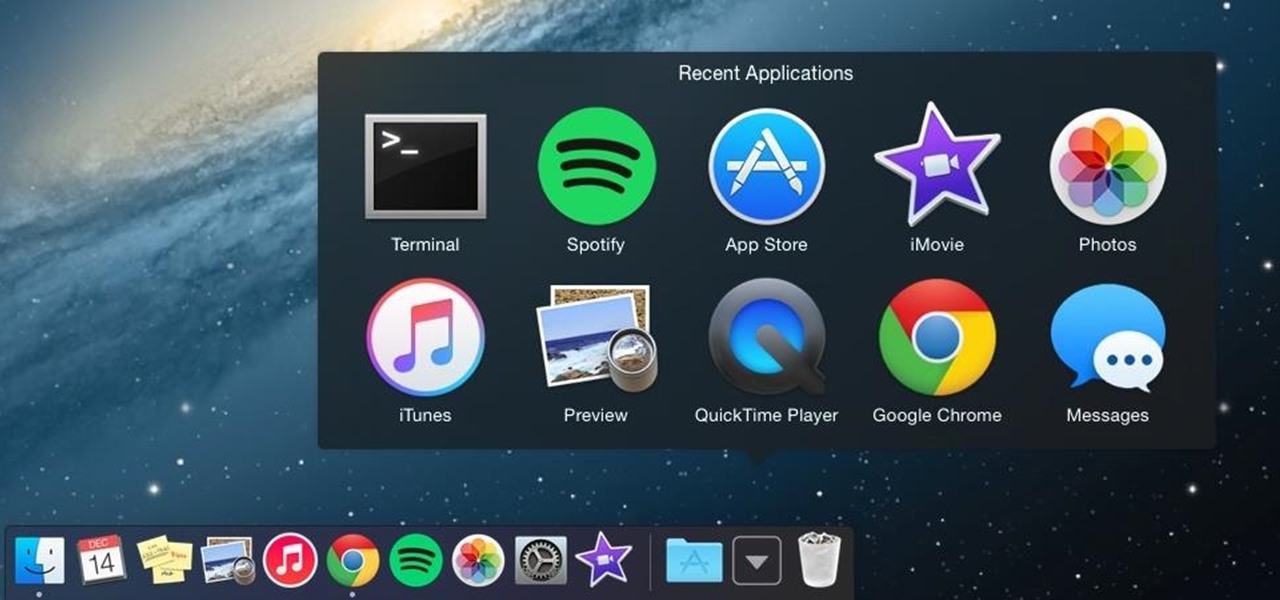
Apple makes it easy to access your favorite and most recently used applications and documents in Mac OS X. You can simply add your favorite apps and folders to the dock, and you can always visit the Apple menu from the menu bar to see a list of your most recently used apps and docs.

Welcome to the Part 2 of the series 'Cryptocurrency'. It has been late because of some errors, where all I typed was lost.

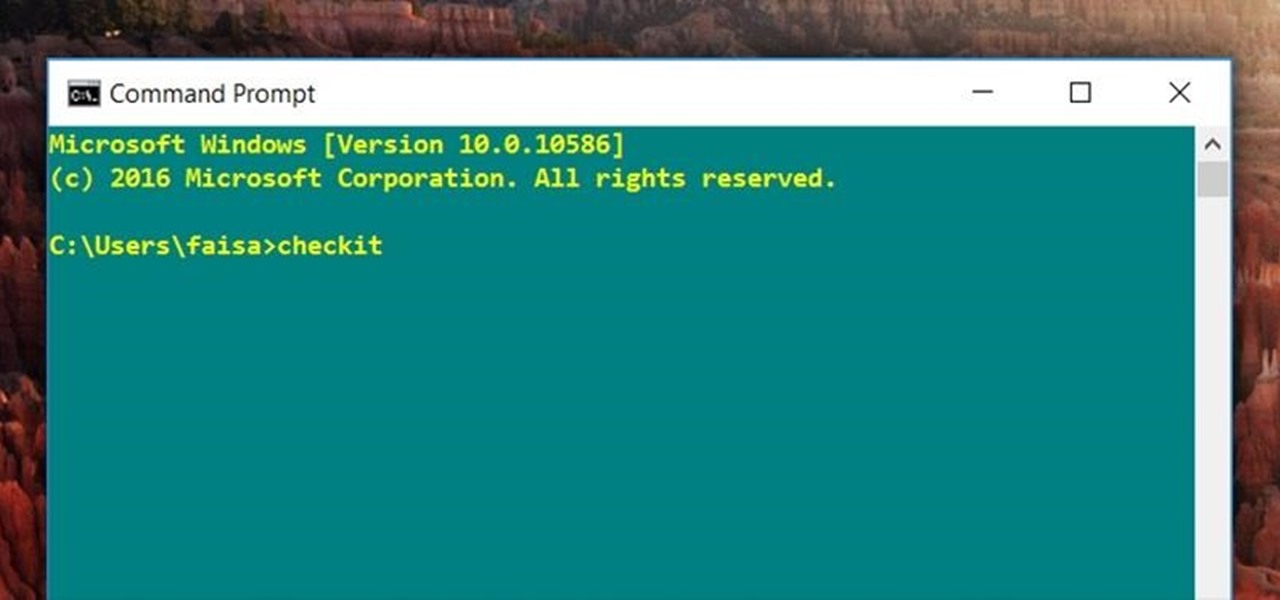
For those times when you can't get something done by clicking a few buttons with your mouse, the Windows command prompt has always been an indispensable tool. But as much as advanced users have relied on this useful utility, it hasn't seen a significant update since the Windows 95 days.

In the wake of Apple Music making its debut on Android devices, Google has finally released its highly anticipated YouTube Music app. With these two tech heavyweights throwing their hats into the ring, the streaming music world is about to get rocked.

With every version bump, Android gets a new Easter egg that can be accessed by tapping the "Android version" entry in Settings. For the most part, these have generally been little animations or live wallpapers that depict the Android code name, but starting with version 5.0 Lollipop, things got a bit more interesting.
Greetings null-bytians. Say you have been able to penetrate your neighbour's AP, and of course you had spoofed your MAC address. Now you go on and test to see with excitement if the password really works and the MAC is still spoofed. You login successfully and you browse the web forgetting to check what your current MAC is. Well, if you may do an ifconfig command, you will see that your permanent MAC is being used. Oh!! and guess what, ... your real MAC has been logged. Even though there is t...

If you're a U.S. expat living, traveling, or studying abroad, or just someone who typically uses virtual private networks (VPNs) in order to access the North American video libraries of services like Hulu or Netflix, you were probably surprised to see that these video streaming services don't work on your Chromecast or Chromecast 2.

A growing trend for many artists (most recently Kanye West) is to offer exclusive or experimental tracks on music streaming sites like SoundCloud or YouTube before releasing them anywhere else. On rare occasions, some of these great songs never make their way onto an official album, which can be disappointing for die-hard fans who need to download every song available from their favorite artist or band.

!!!WARNING!!! !!!Because of misleading informations please wait for the new post about this same argument instead of reading this post!!!

Unless you have a newer iPhone 6S or 6S Plus, the front-facing "FaceTime" camera on your iPhone has a pretty weak, low-res sensor, which means unflattering selfies. You could use the rear "iSight" camera to take a high-res selfie, but framing your mug properly and hitting the shutter is difficult, takes many failed attempts, and usually results in a lackluster photo.

Your English teacher is a creep. The way he looks at your girlfriend, the way he always spends ages with the girls in the class going over their work but not the boys, just the way he is.

T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the potential for identity theft here is huge.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

If you've been using Windows 10 for a while, you already know that Microsoft incorporated lots of new features into it. So you're probably familiar with Cortana (the new voice assistant), the Edge browser (their replacement for Internet Explorer), the newly resurrected Start menu, and all of the other big changes.

Android has a brand new mobile payments system, and it's rolling out to most devices as we speak. Android Pay, as it's called, will replace the existing Google Wallet app as an update, and it brings some awesome new functionality such as tokenization and the ability to tap-and-pay by simply unlocking your phone.

Welcome back, rookie hackers! We recently began an exploration of ways to hack using the Bluetooth protocol. As you know, Bluetooth is a protocol that connects near field devices such as headsets, speakers, and keyboards. Its minimum range is a 10-meter radius (~33 feet) and maximum is at 100 meters (~328 feet).

Historically, battery life has not been a strong suit for machines running Windows. Poor decisions by hardware manufacturers combined with the resource-hogging behavior of Windows are to blame. However, Microsoft is trying to resolve this issue, once again, with the release of Windows 10.

People like to cite the iPhone as the device that started the smartphone craze, but the truth is, smartphones had existed for years by the time Apple got into the game. The real groundbreaking feature that this device brought to the table was a multi-touch screen to go along with its "smart" functionality, and this is still the main method we use to interact with our devices today.

Unless you've been living under a rock or ignoring recent news headlines, Ashley Madison, the dating site for married people (or individuals in a committed relationship) has recently been hacked. Millions of their users are shitting their pants, and for good reason, as all of those accounts have just been leaked.

Modern versions of Windows have revamped the lock screen to make it a lot more useful. If you're coming from Windows 7 and older versions of the OS, this lock screen is both new and useful (though you can turn it off if you just don't want it).

If you're just starting out with Android—or smartphones in general, for that matter—there are a lot of little things to learn. One of the first terms you'll likely encounter is "Wi-Fi," which is a wireless internet connection served up by a router in your home, office, or local coffee shop. This differs from your smartphone's regular "Mobile Data" connection, which is provided by your cellular carrier and included as part of your monthly bill.

Ruby is a dynamic, general-purpose programming language created by Yukihiro "Matz" Matsumoto in Japan around the mid-90's. It has many uses but with it's flexibility, it makes a great language to write exploits in. In fact, the entire Metasploit Framework is written in Ruby! The sole purpose of this series is to teach hackers the basics of Ruby, along with some more advanced concepts that are important in hacking.

Unruly customers. Crazy exes. Horrible bosses. When you need proof of insanity or just want it for your records, recording a phone call is a must. Problem is, it's not the easiest thing to do on an iPhone — but it's completely possible.

Hello you sexy, savage, surreptitiously tech-savvy penetrators (Pun intended)!

In an attempt to increase advertising revenues, Snapchat introduced Discover back in January of this year, a feature that brought a handful of prominent media partners, such as CNN, ESPN, and Vice to your feed, along with their tailored news stories and videos.

With iOS 8.4 and iTunes 12.2, we got our first look at Apple Music, Apple's new streaming subscription service. While it's a little late to the party, there is definitely an incentive for iOS and Mac OS X users to switch over from competitors due to its heavy integration with the Apple ecosystem.

A while back, I wrote review of my favorite hacking movies of all time. Two of my key criteria were; (1) how realistic was the hacking, and (2) are the hackers portrayed as the "good guys." This past winter, a new hacker movie was released, appropriately named Blackhat starring Chris Hemsworth (from Thor fame) as a blackhat hacker who is released from prison to stop a notorious and destructive hacker that only he can stop. Although the movie did very poorly at the box office, I thought it was...

T-Mobile's "Uncarrier" initiative has done wonders for my wallet and my data usage. Before I had to deal with being throttled down to 2G speeds after passing my data limit, but thanks to their unlimited data plans, I'm free to use as much LTE data as I possibly can. The only downside is, when sharing data through a mobile hotspot (tethering), T-Mobile imposes a 5 GB limit (which was recently upped to 7 GB for some).

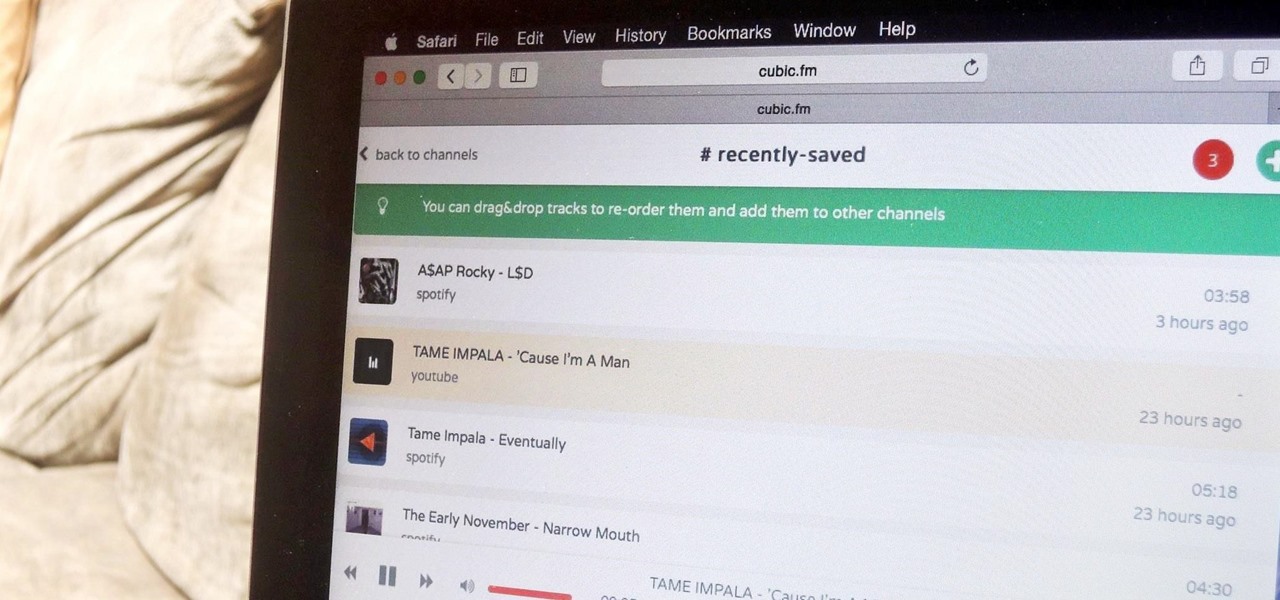
The options for finding random or specific music to listen to are vast. Spotify is excellent for streaming popular music and new releases, while SoundCloud provides a healthy dose of user-generated remixes and originals. And then there's YouTube for everything else.

On an Android device, you can download almost any file type into a neat and tidy "Downloads" folder, and those files can then be accessed with an appropriate app, shared via email, or transferred over to your computer. On an iPhone, there is no such folder, and saving files from Safari is almost impossible unless you're jailbroken.

Google recently announced the beta release of a developer tool called ARC Welder for Chrome, which allows developers to run and test their Android apps on any computer with the Chrome browser installed.

Ad blocking on Android usually requires root access, but a pair of new browsers based on the open source Chromium and Firefox builds are looking to change this.