Learning different coding languages can be difficult. You spend so much time mastering one and getting used to thinking along the channels you need for it that learning something new can sometimes be more difficult than starting from scratch. Starting from scratch, notably, is also difficult.

We've reached the point in the trajectory of augmented reality's growth where AR advertising experiences are becoming commonplace tactics rather than rare experiments.

When we're young, learning a new language is as easy as learning anything else. There have been ample studies that show adults struggling to learn a new language are not alone. Learning a new language is hard, particularly when done outside the guidance of a teacher or a school setting.

Now that more and more people are working on their personal computers and smartphones as opposed to their work computers as a result of the coronavirus outbreak, hackers are having a field day. Unencrypted home networks and public WiFi connections make it incredibly easy for cybercriminals and even government agencies to access everything from your browsing history to your banking information, and a Virtual Private Network (VPN) is the only way to stop them.

Many apps on your iPhone want to use your location, most of which are for valid reasons. But some apps can function perfectly fine without location permissions, while others have no business even requesting it. If you want to be more selective about which apps and services you give away your coordinates to, the best thing you could do is start from scratch.

While sheltering at home orders are lifting, companies are still conducting most business online. Case in point, hackers have been having a field day over the last few months. Securing your identity has always been important, but never as much as it is at this moment.

There are many considerations to make when choosing a web hosting plan. Storage space, performance, security, and reliability all matter. The cheapest option isn't always the best idea.

It's a myth that regular users only need the protection of a virtual private network when on a public Wi-Fi connection. First, almost all network connections can be accessed without the proper permissions. Second, ethical hackers also need to think about using a VPN as one step to encrypting and protecting their activity and identity during pentests, phishing, and other actions.

Now that the transfer tool for migrating your Google Play Music library to YouTube Music is rolling out, more fans of the former, which will meet its end in 2020, are giving its replacement a try.

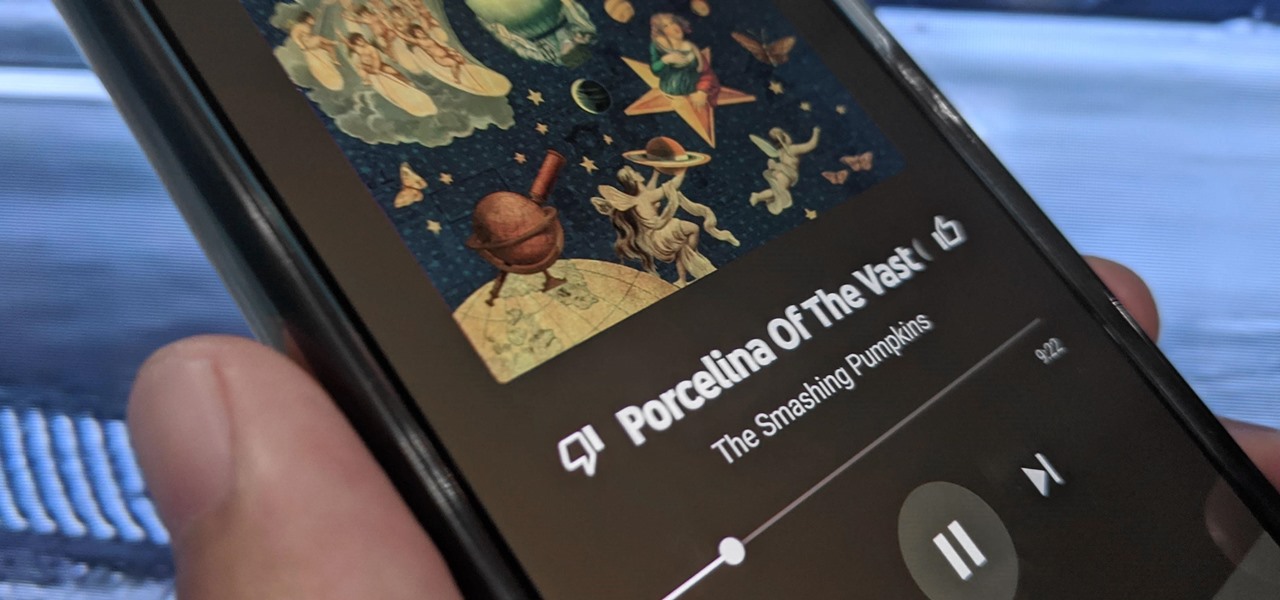
Over the last few years, Apple has significantly improved and scaled up your iPhone's ability to edit photos. Using the Markup feature, which was introduced back in iOS 10, you can add doodles, highlights, important text, your signature, and arrows and other objects onto pictures and screenshots. One of the lesser-known tools in Markup lets you zoom into essential details without cropping.

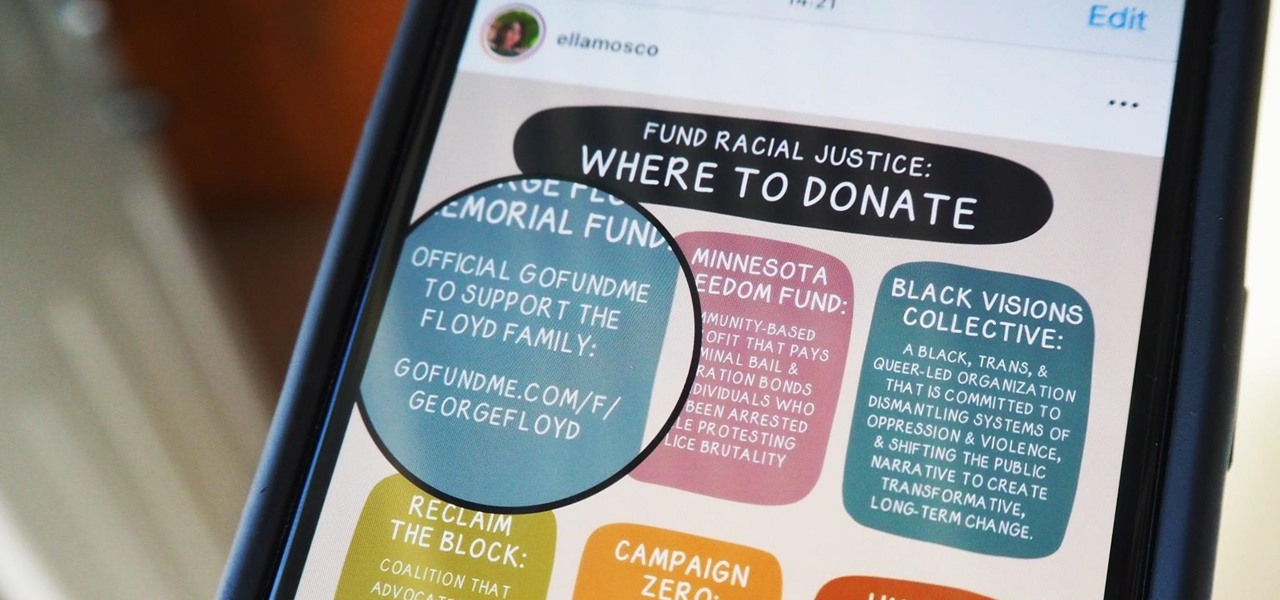
With thousands of people across the country protesting, you might be thinking about joining the march. But as is too often the case, law enforcement has been called to oversee the protests, and interactions aren't always peaceful or lawful.

For a hacker, there are a lot of advantages to creating a fake network. One advantage forces nearby devices to use their real MAC address if you happen upon a network that's stored in their preferred network list.

From booting into Fastboot mode with a single command to installing mods without root access, there's no shortage of reasons to use ADB. The catch, though, you had to be tied to a computer with a USB connection. However, a new feature in Android 11 finally allows you to run ADB commands over Wi-Fi instead of being tethered.

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.

In previous Android versions, you lost about an inch of screen real estate to the status bar and navigation bar. But if you enable Android 10's new navigation gestures on your Samsung Galaxy, you can regain the bottom part — and with the help of ADB, you can reclaim the top portion as well.

The response to the COVID-19 pandemic means that social distancing has become the new normal. It also means that more Americans are using video conferencing to connect with colleagues working from home or friends and family in quarantine because of the new coronavirus.

One vital part of Android 10's new navigation system is the "QuickStep" gesture. Swipe up from the bottom of your screen, then pause. You'll see your recent apps along with a dock containing a handful of icons for quick access. This dock is provided by the phone's launcher, which means your home screen is now integrated into the multitasking UI. So what happens if you change your home screen app?

Spotify launched an experimental feature in early-2018 called Spotify Voice, a voice assistant that lives right in the app. It lets you speak to quickly find and play your favorite songs, albums, artists, videos, and podcasts on the music streaming service. Although the feature was initially only available on iOS, it's been ported over to Android so that anyone can take advantage of it.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

Stadia is a lot like an Xbox or PS4, except there's no console — the games just stream from Google's servers to your phone, computer, or TV. But Stadia is limited to Pixel phones for right now, and when Google does expand support, it will still only be for select phones. Thankfully, there's a workaround for that if you're rooted.

In iOS 13, Apple added an important new feature to its HomeKit smart home ecosystem called HomeKit Secure Video. With it, you have a secure, private way to store and access recordings from your smart home IoT cameras.

It's easy to take your iPhone's Notification Center for granted. As useful as it is for viewing important alerts, reminders, and more, the feature is pretty drab when compared to the customizable Control Center, Accessibility Shortcuts, and others.

I've been using the Galaxy Note 10+ as my daily driver for a while now. I love it, but as with any phone, it loses its pizzazz after a while. But since it's an Android phone, there's always a way to add fresh features and functionality to the UI.

The Files app received a big update in iOS 13. Before, it was limited to local and cloud-based files, but now you can access data from external storage devices, including SD cards and USB drives. But before you try to connect your favorite card or drive to your iPhone, there are a few things you need to know.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

You've probably heard of RCS messaging. The new standard has been promoted by Google as their answer to iMessage and is the backbone behind the new "Chat" features in Android Messages. With RCS, Android phones will now enjoy enhanced messaging like iPhone users have had for years — but is it really the same?

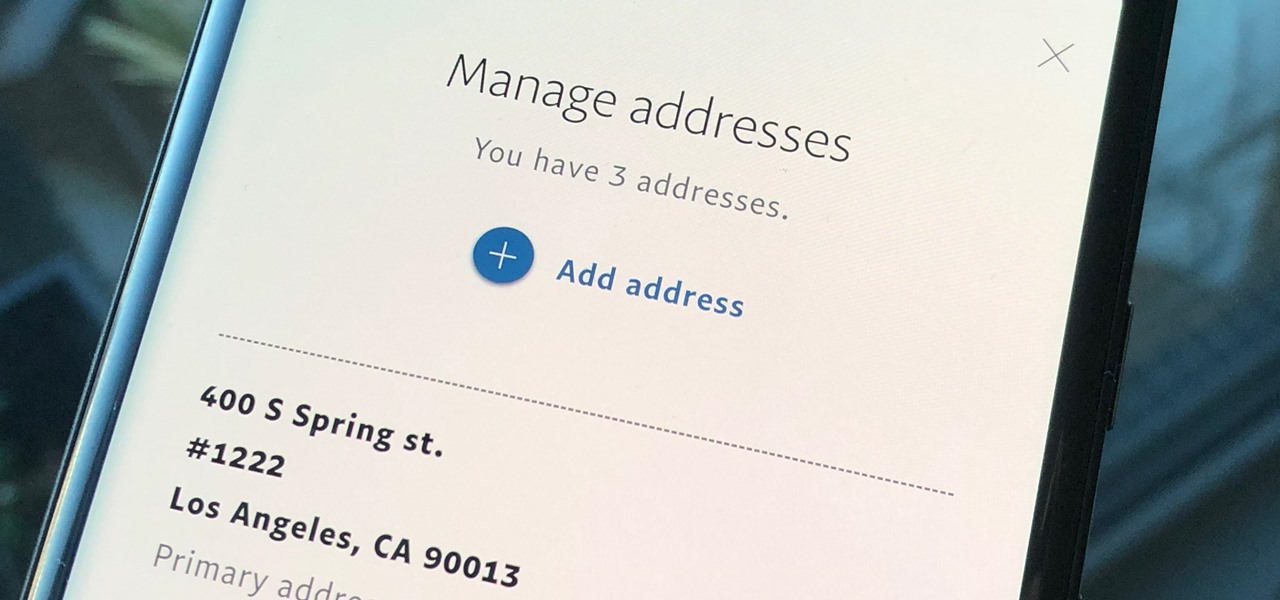
Whenever you move into a new home, whether that's a house or apartment, changing addresses on all your online accounts is one of the most monotonous tasks that needs to be done. It's even more tedious when you have to update both shipping and billing addresses. But it's necessary, and if you regularly use PayPal, it'll be one of the first places you'll want to update.

Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called "Cast All the Things," we can hijack a Chromecast to play nearly any kind of media with a single command in terminal.

WhatsApp is the go-to messaging app for millions worldwide and its easy to see why. The app can be considered the Swiss Army Knife of texting thanks to numerous features like Group Chats and Status Stories, in addition to striking a great balance between ease of access and overall security.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

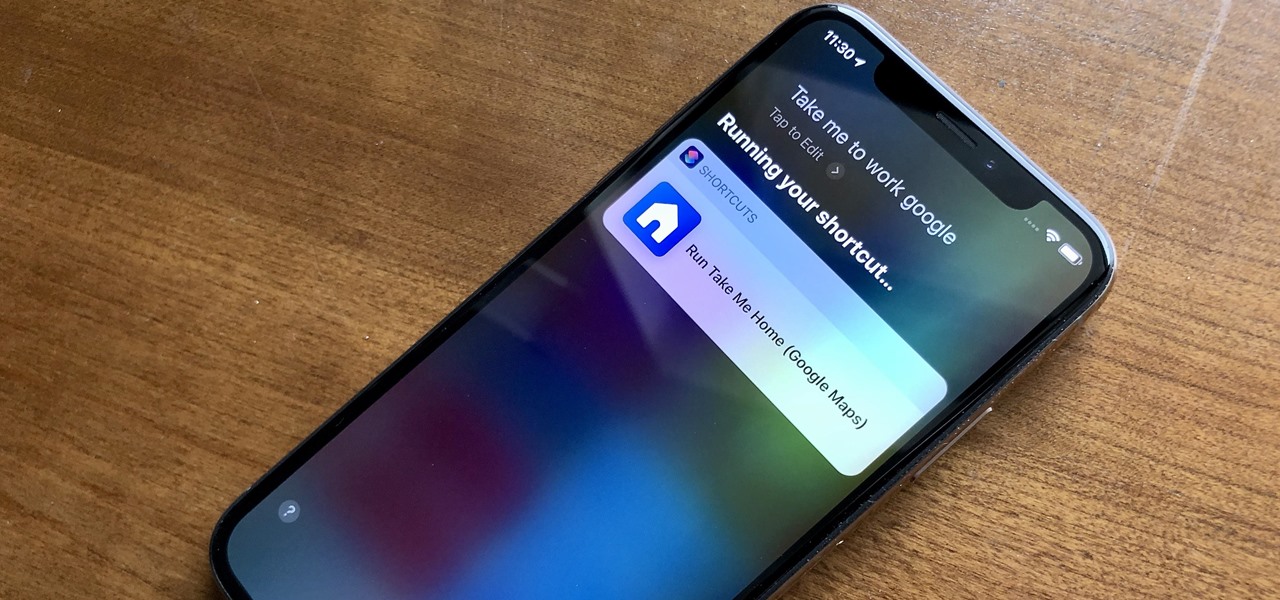
When driving, you can get directions hands-free by asking Siri. You can also make general map searches, show a location's details, call a query's phone number, and view traffic details. However, Siri defaults to Apple Maps for all those. If you prefer Google Maps, Waze, or another third-party navigation app, the map-based Siri commands won't work. But that doesn't mean you can't still use Siri.

In late-2017, Instagram rolled out a feature that automatically saves your ephemeral Stories to a private archive. Before that, Stories disappeared into the ether after 24 hours, but not everyone was comfortable losing these precious photos and videos. If you post to Instagram Stories quite often, you can now easily access your history from your account — and you might not even know it.

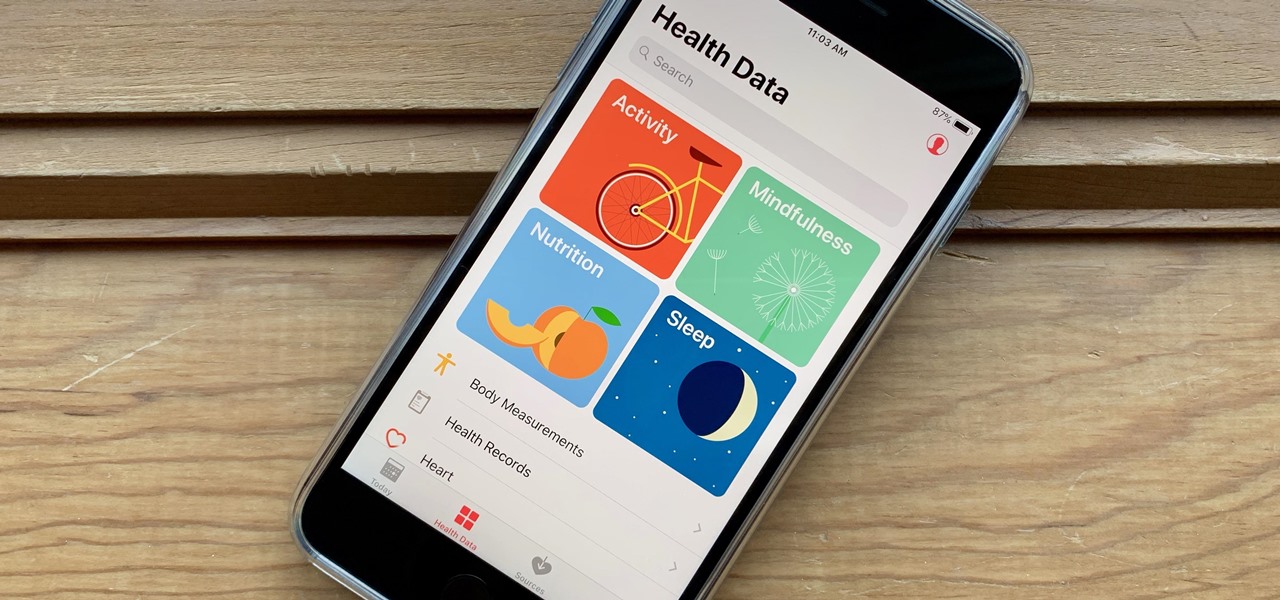
It's not easy staying fit and healthy these days with addicting phones, oversized portions, and long workdays, to name just a few things. To succeed, it takes work, commitment, and an understanding of your mind and body — and your iPhone can help you with some of that. While Apple pushed its Screen Time tool to help curb unhealthy smartphone habits, its "Health" app can help with everything else.

iOS 12 has a feature that lets you instantly share saved Wi-Fi passwords with other iPhone users, but it can be finicky when you're sharing with multiple people. Then there's an even more pressing question: How do you share your password with Android users? Thankfully, there's a Shortcut that can solve these problems.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

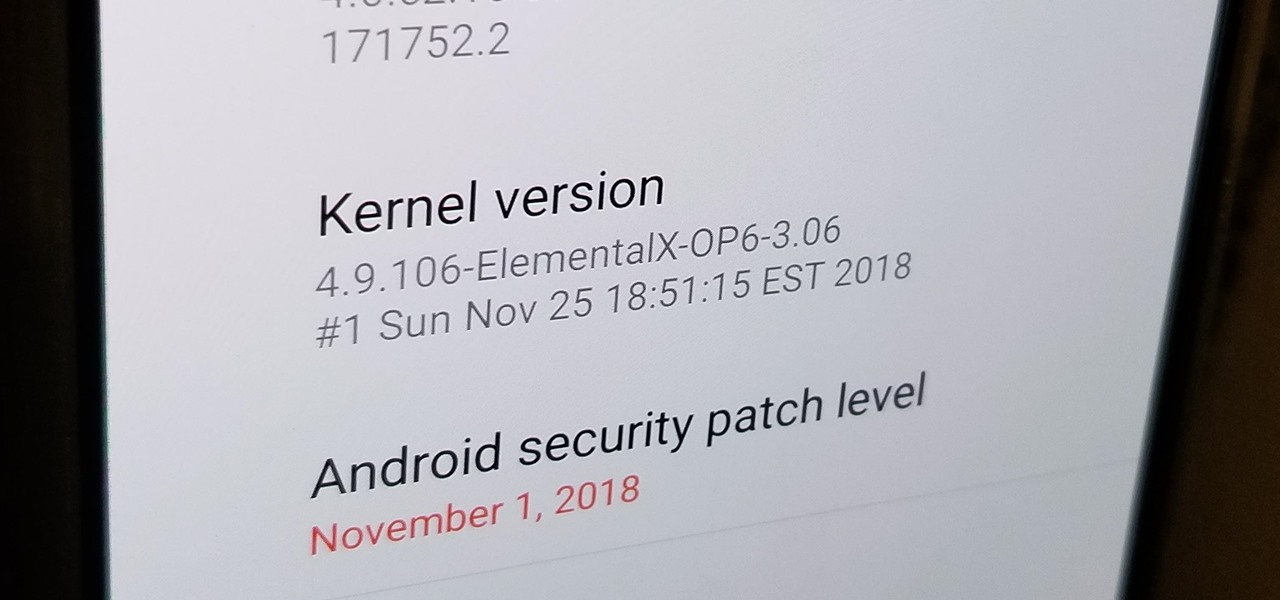
After you unlock the bootloader, install TWRP custom recovery, and flash Magisk to gain root access, what might be the next step of your modding adventure? A custom kernel, of course! Flashing a custom kernel onto your device gives you a whole new level of tweaks and customizations, and it allows you to have full control over how your system performs.

Before you can dive into customizing your OnePlus 6T, you must take the initial step of unlocking the bootloader to gain the ability to install TWRP, Magisk, custom ROMs, and other mods.

You can easily deck out your favorite phone with great wallpapers, ringtones, and icons, but what about fonts? Not all Android skins let you change the system font, and even when they do, the options are often limited to a few choices. Certain root apps can open up the system font to customization, but some of these can cause problems now that Google introduced a security measure called SafetyNet.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.