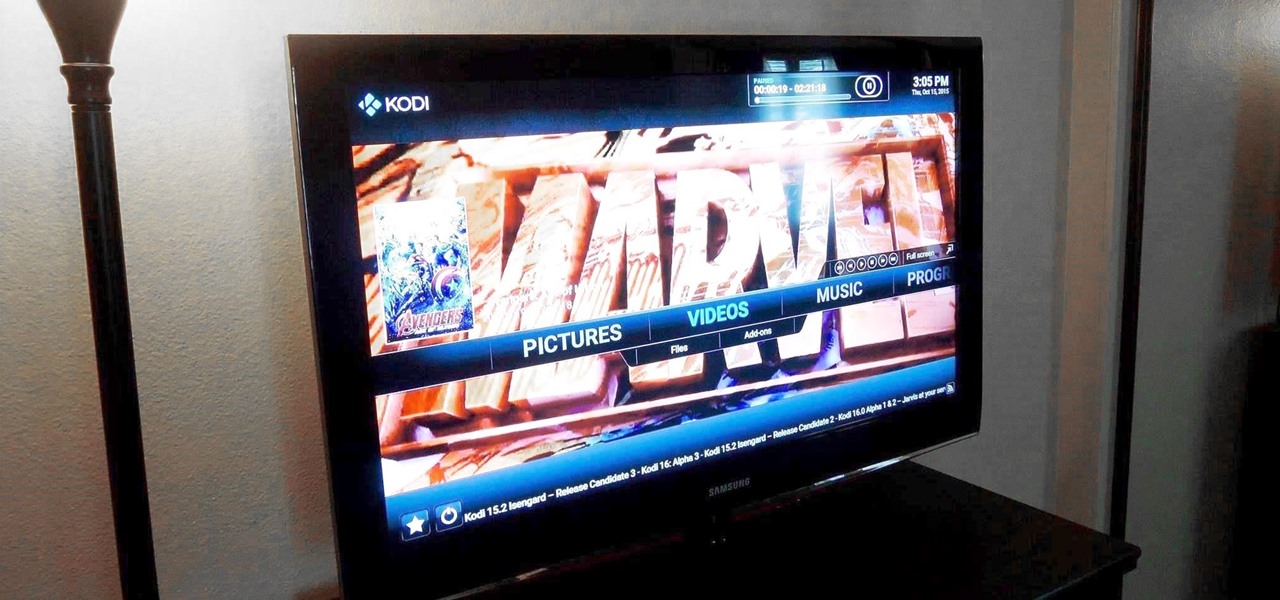
Amazon thinks that by simply removing an app from their Appstore, that they will stop users from accessing it. But with Android OS powering their Fire TV Stick and Fire TV, there really isn't anything they can do to prevent us from sideloading an APK onto the streaming media devices.

If you somehow forgot the pattern, PIN, or password that locks your Android device, you might think you're out of luck and are destined to be locked out forever. These security methods are hard to crack by design, but in many cases, it's not entirely impossible to break into a locked device.
Mostly all hackers like to have a laugh. We like to have fun! We like to troll. And maybe, even cause some havoc once in a while. But, while we do this, we must always stay in the line of the law.
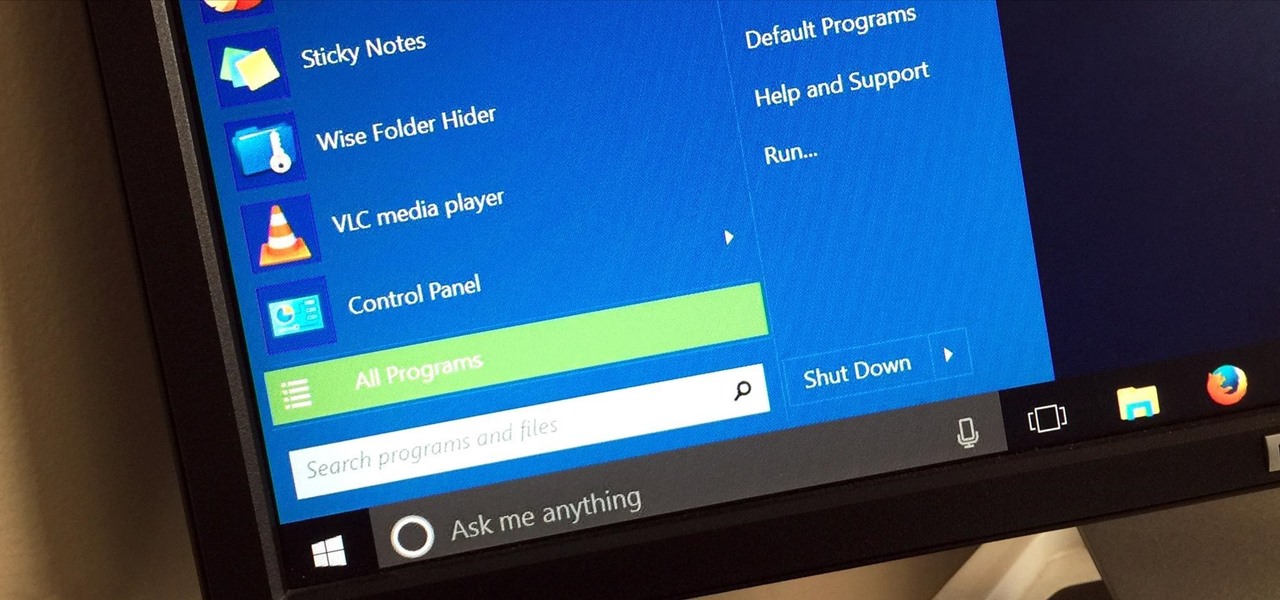
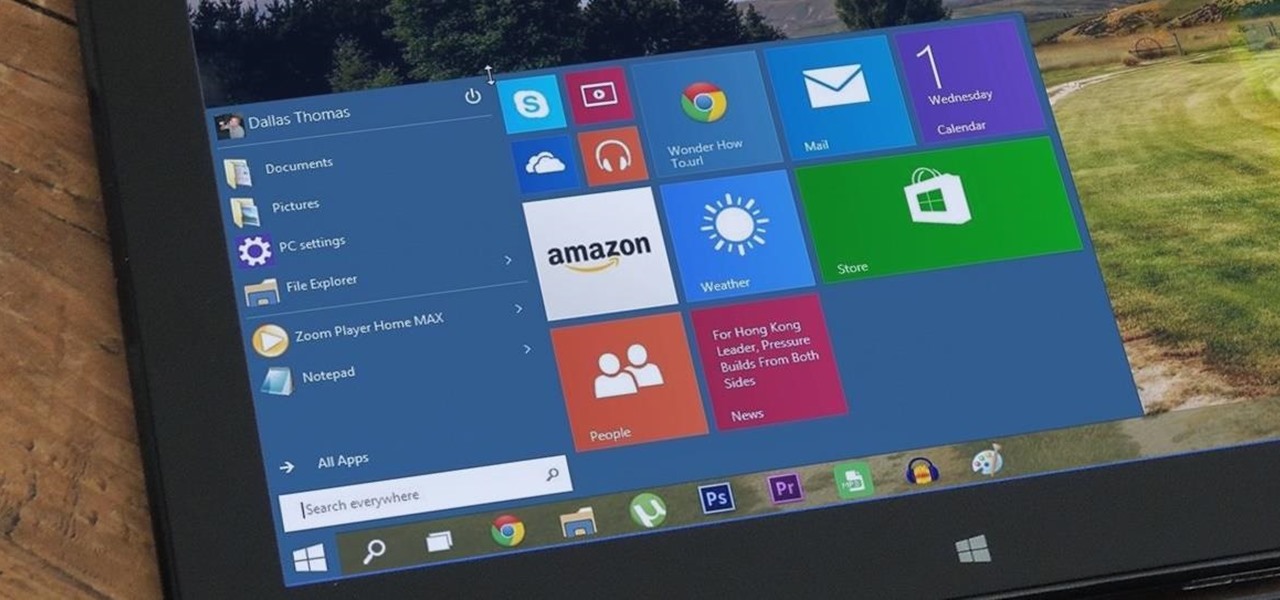
Windows 95, which introduced the Start menu to the world, recently celebrated its 20th birthday! The feature was an instant hit, becoming a core component of Windows operating systems. Well, it was removed in the mistake that was Windows 8, but you should know by now that the Start menu has been reincarnated for Windows 10.

When attempting to gain access to a server, there may come a point when you need to get around file upload restrictions to upload something. If we can find a way to get around the restrictions, then we can upload anything we want to the server, effectively compromising it. That is what we'll be doing here today, so let's get started!

Mobile payment systems have been around for almost 5 years now, starting with Google Wallet. But when Apple got into the game last year with their new Apple Pay service, things really started to take off. Around this time, Samsung responded by acquiring an up-and-coming mobile payments company that owned the rights to an incredibly innovative technology called Magnetic Secure Transmission (MST).

Windows 10 is officially here, and frankly, there's a ton of new features in Microsoft's latest operating system. From the return of the Start menu to the new Edge browser, Windows 10 can take some getting used to.

I'm often reluctant to use a home screen launcher other than the stock one on my Android. Once you're well acclimated with something, complacency sets in, welcoming change with much resistance. Well, my friends, I have seen the error of my ways...

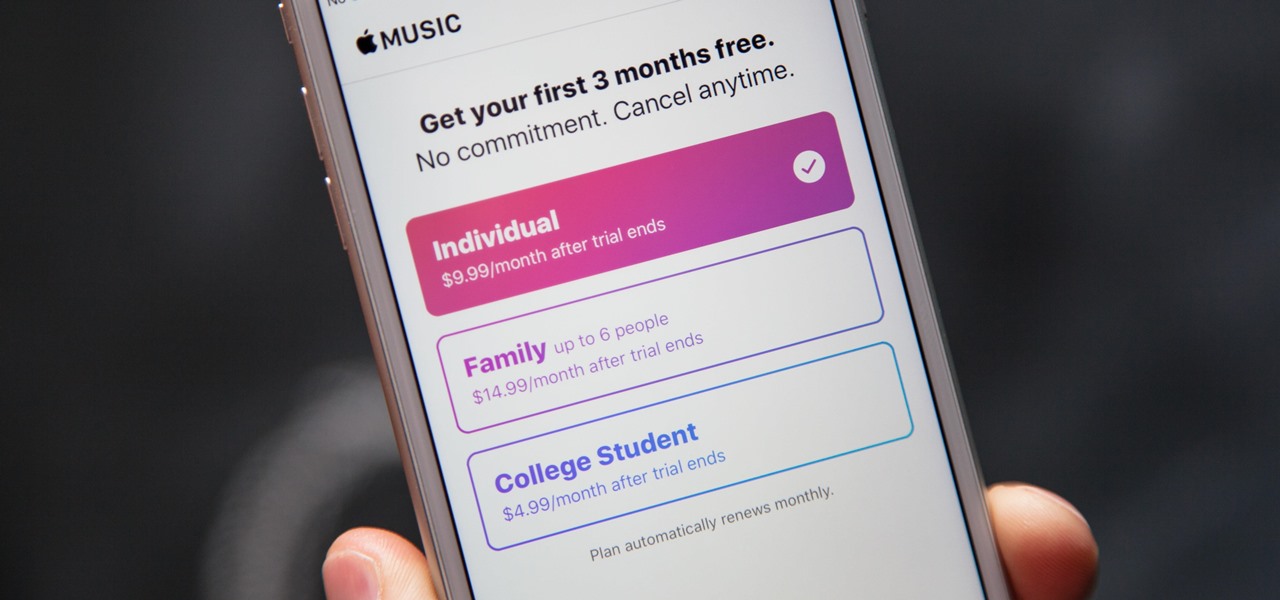
Apple's streaming music service, Apple Music, offers a three-month free trial that hopes to get you addicted enough to pay for a monthly subscription. You may even see a one-month trial if you're a former subscriber. While it's not very obvious, there is a way to cancel either free trial from auto-renewing. That way, you don't have to deal with Apple support to try and get your money back because you forgot.

Whether I'm in my car or making dinner, I always have music playing. And since I don't like to keep my headphones on me at all times, I end up using my Android's built-in speakers a good portion of the time.

When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

When it comes to smartphones, the biggest complaint voiced by most users is battery life. Sure, it's unrealistic to expect your Android device to run for weeks without a recharge, but many folks struggle to even make it through the day without having to top off their battery.

Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.

Edit: Some of the methods I show you may be difficult, or not work at famous or high quality hotels.

If you've ever attended school or held a job, you're probably well familiar with Microsoft Office, whether you used it or not. It's the most popular office suite available, and has been for some time. Apple does have its own suite of productivity apps (iWork), but Microsoft Office has always been the industry leader for word documents, spreadsheets, and presentations.

When it comes to getting your computer and smartphone to work well together, there's no service more robust and capable than AirDroid. For years, it's been the go-to tool for users looking to transfer files between their devices or access contact lists and call logs from their computer.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

At a closed-door presentation on September 30th, 2014, Microsoft unveiled the latest iteration of its industry-leading operating system. Dubbed Windows 10 (seems as if Redmond isn't too fond of the "9" moniker), this new version brings along with it many UI optimizations and under-the-hood tweaks. With a particular focus on optimizing the interface for traditional mouse and keyboard computers, one of the most noticeable changes is the return of the Start Menu. While touch-optimized devices wi...

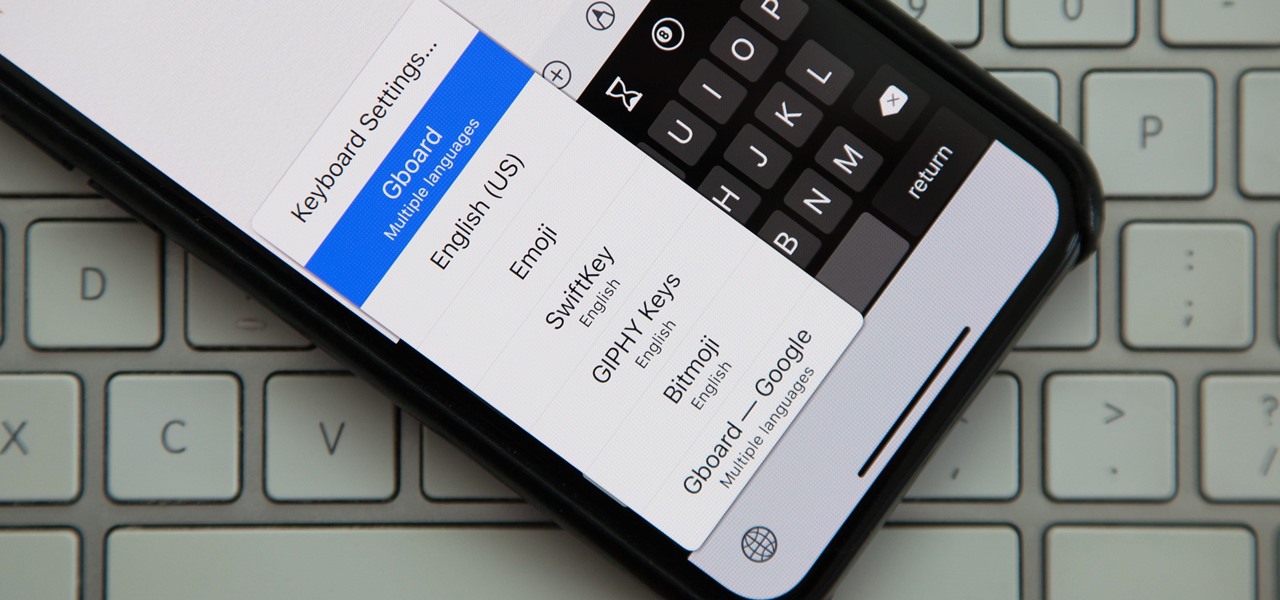
Back in iOS 8, Apple introduced the option to use third-party keyboards on iPhone, and since then, there have been a ton of third-party keyboards available such as Gboard, AudioShot, SwiftKey, Slated, and many more. However, adding and even using these keyboards can be kind of tricky.

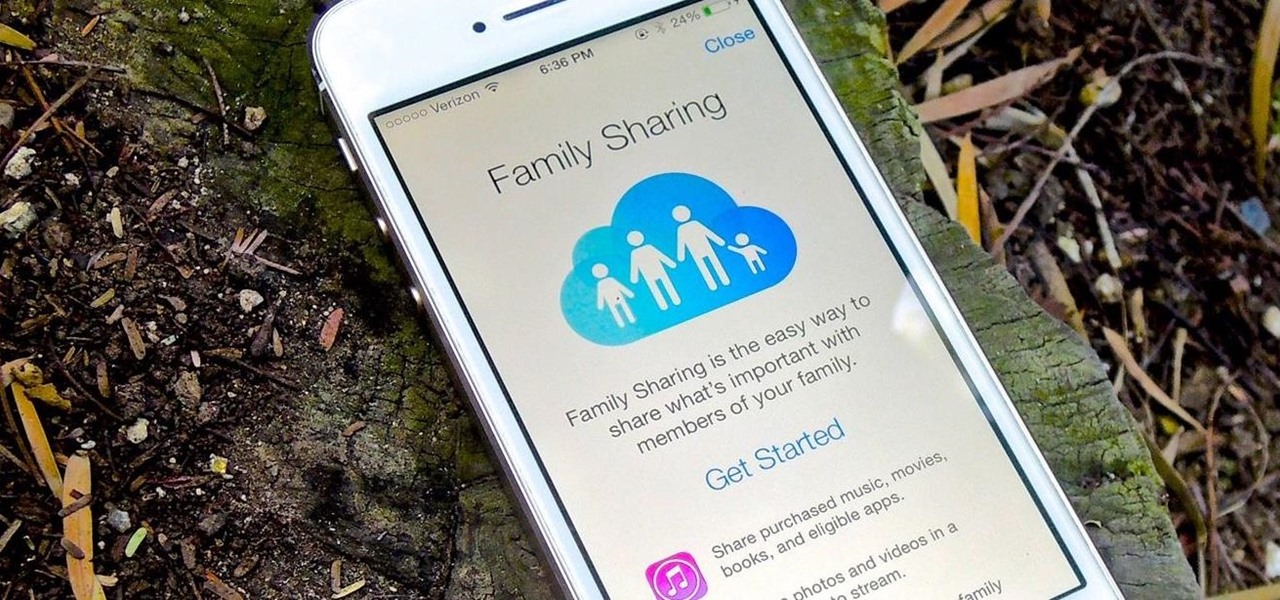
There are a ton of great new features in iOS 8, and one of the most interesting (and perplexing) ones is called "Family Sharing."

The new LG G3 is the latest Android flagship-level device to be released this year, and it's ready to give the Galaxy S5, HTC One M8, and the OnePlus One a run for their money. Sporting a gorgeous 5.5-inch QHD display, 3GB of RAM, and a huge 300mAH battery, the device looks great and has tons of power to boot.

Multitasking has always been one of Android's strengths relative to other mobile operating systems. As the first cell phone OS with "true" multitasking, Android's been ahead of the game in this department for quite some time.

Back in August, Google introduced Android Device Manager. This new service allowed you to locate, lock, or wipe a lost or stolen Android device from either a companion app or a web interface. Effectively, this is the "kill switch" that legislators are clamoring for.

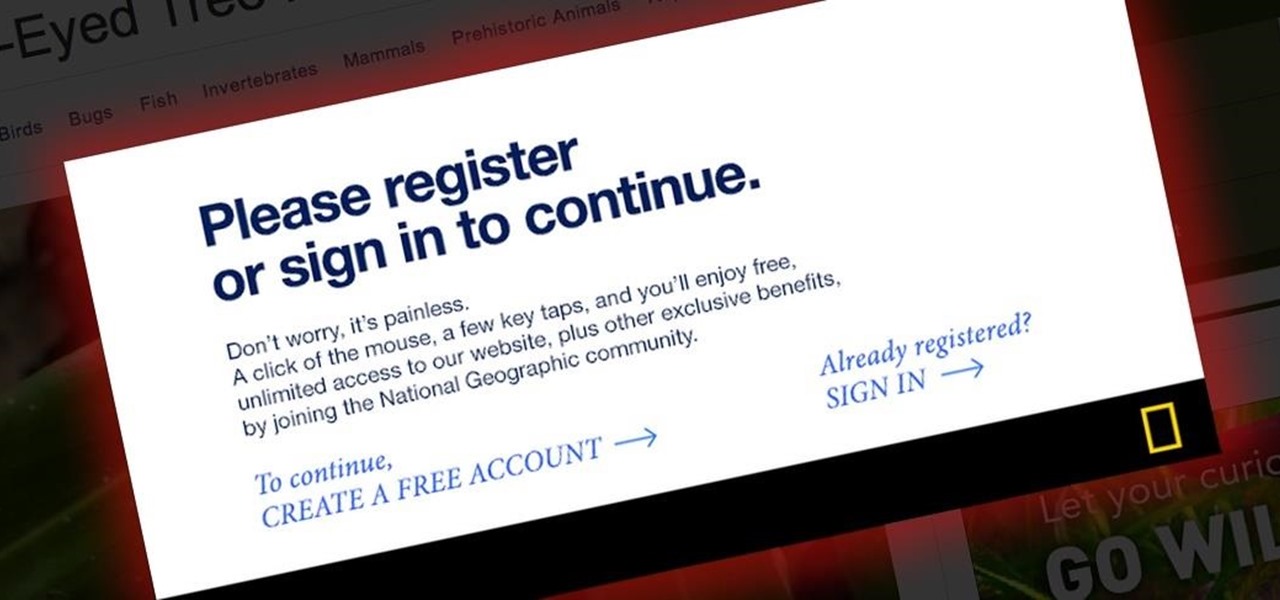
Last night, I was reading a riveting National Geographic article on the green-eyed tree frog, until I was quickly interrupted by an annoying popup asking me to "create a free account" or "sign in." Really, I'd like to do neither. I just want to read about tree frogs.

Greetings. This how-to on hacking Windows 7/8/10 etc. admin account passwords using Windows Magnifier is focused on adding, changing, or deleting an admin level account on a Windows 7/8/10 etc.

Keeping up with current events is a good step towards becoming a well-informed person, but sometimes it's a chore. In-between work, school, commuting, social lives, and hobbies, it can be extremely hard to find time to pick up a newspaper or browse CNN to find out what's going on in the world.

As with most OEMs, HTC would like you to think that you can do virtually anything with your new HTC One M8, but as a softModder, you know that isn't true. To actually unleash the full potential of that device, you need access to the whole system, not just the parts that HTC deems okay for you to mess with.

Nintendo fans rejoice! Not only can you play classic NES games on your iPad or iPhone without jailbreaking, you can play Game Boy Advance and Game Boy Color games. And that's not it. Now, thanks to @angelXwind, we can add Nintendo DS to our list of non-jailbreak emulators for iOS 7.

One thing almost every Android launcher has in common, from stocks to skins, is the way they handle organizing and launching apps and widgets. Tap an app icon to open the app. Drag apps together to create a folder. It's simple, it works, and it's what we know.

Welcome back, my tenderfoot hackers! So many readers in the Null Byte community have been asking me questions about evading detection and hacking undetected that I decided to start a new series on digital forensics.

The newest Android operating system, Android 4.4 KitKat, has been unleashed with the arrival of the Nexus 5, and soon to be rolled out to other Nexus devices and Google Play Edition smartphones any day now. Only problem is, the Samsung Galaxy S3 isn't getting 4.4 for a very long time. It doesn't even have 4.3 Jelly Bean yet.

Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.

Unless you like paying exorbitant prices for out-of-contract phones, most of us are stuck with the one we already have for two or more years. The tech industry moves fast, and as new phones are released seemingly every month, your Samsung Galaxy S4 might start looking older by the week.

Update: The installation process for Xposed Installer is now dead simple—check out our updated guide!

The shortest distance between two points is a straight line, but the shortest way to launch an app on an iPhone can be a much more complicated process.

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

To really customize your Samsung Galaxy S3, you'll need to be rooted, because most of the coolest mods and hacks require root access. If you haven't rooted yet, you're just barely touching the surface of what your GS3 can do for you.

In the UK, 20 percent of divorce filings include the word "Facebook." You may think you're being slick by using the site to chat with your ex, but the problem is that Facebook saves everything, and I mean everything. All someone needs is your login information and they have access to everything you've ever said on Facebook, public or private.

Welcome back, my neophyte hackers! Several of you have written me asking how to crack passwords. The answer, in part, depends upon whether you have physical access to the computer, what operating system you are running, and how strong the passwords are.

Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don't know anything about it, even how to access it.