There's a new macOS vulnerability that hackers within physical reach of your computer can use to gain root access to your system and accounts. Just by using "root" as the username and a blank password on a privilege escalation prompt, someone can install malware on your computer, access hidden files, reset your passwords, and more. Root access gives them the ability to do anything they want.

Essential just dropped the Oreo Beta Program for their flagship PH-1 phone. Users have been eagerly awaiting this update as the early Nougat builds of the PH-1 software have suffered from numerous performance issues and lag. The good news is that you can grab the Oreo update today with a few simple steps.

Update 10/14: Developer paphonb has added rootless Google Now integration to the leaked Pixel 2 launcher, so now, anyone running Android Nougat or Oreo can get the full Pixel 2 home screen experience. For those running Lollipop or Marshmallow, we've left the unaltered leaked version linked out below, but we've added a new link for the tweaked version with Google Now integration.
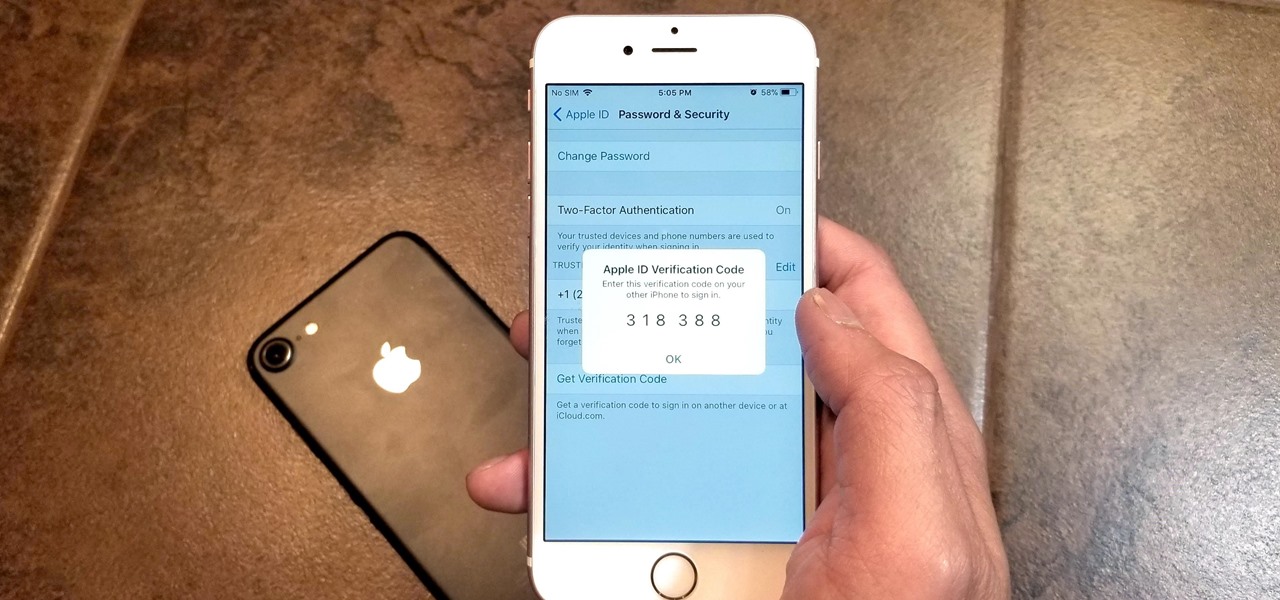
Two-factor authentication has been around since iOS 10. It's a handy option that adds an extra layer of security to your iPhone and makes its almost impenetrable security even stronger. This feature has remained intact in iOS 11 and iOS 12, and thanks to the straightforward nature of iOS, is relatively easy to enable.
When it comes to watching movies and TV shows in Amazon's Prime Video service on an iPhone, it's as simple as installing the Amazon Prime Video app, signing into it, then playing content. However, on an Android phone, it's a lot more complicated.

Google has an exclusive launcher for its Pixel devices, and it's pretty slick. But even though we've found ways to get this home screen app on other phones, certain features simply wouldn't work unless you were rooted. That's finally changed.

Deep down inside, Kindle Fires are actually Android tablets — the only trouble is, Amazon has layered so much of a skin on top of it all that you can't normally use Android's main app store, the Google Play Store. The Amazon Appstore, which comes bundled with Kindle Fire devices, only has about 600,000 apps, so it would be great if you could access Google Play's library, which boasts 2.8 million.

Samsung's new personal assistant, Bixby, is making its debut on the Galaxy S8 and S8+. In addition to taking voice commands and performing visual searches, a new Hello Bixby feature predicts what you might want to do next with an integrated home screen feed. All of these features look nice, but if you're not ready to shell out at least $750 for a new phone, you'll be glad to know that Hello Bixby just leaked.

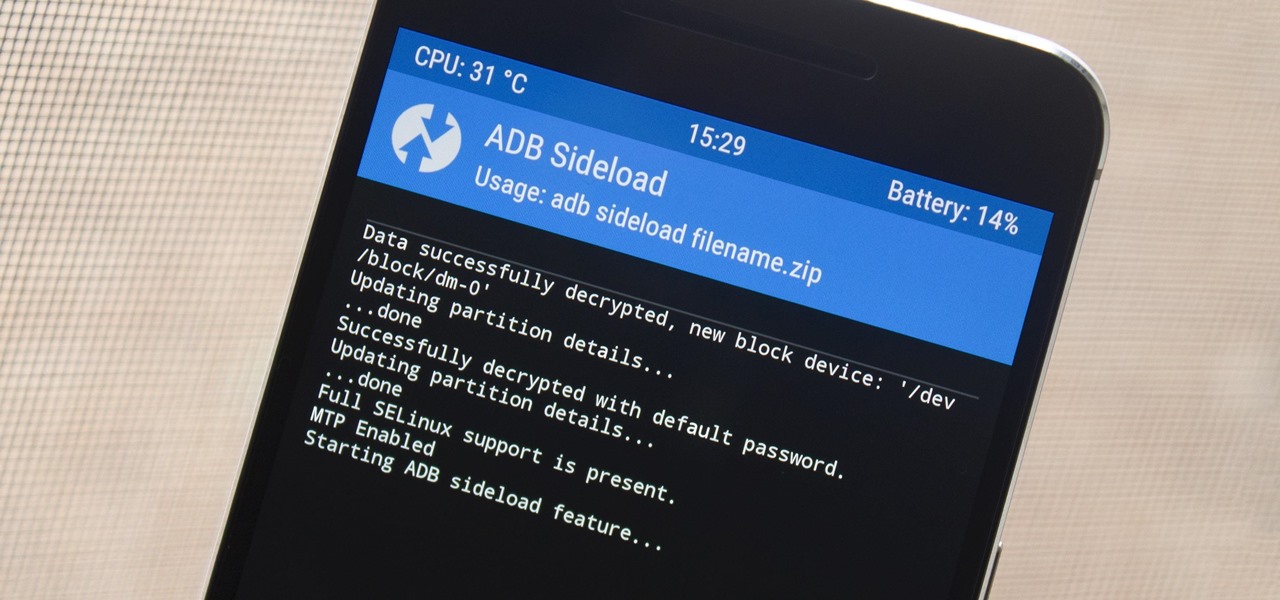
If you're one who likes to tinker with Android, TWRP is the first thing you should install. It replaces your phone's stock recovery mode interface and adds over a dozen advanced features to your device—most notably, the ability to flash ZIPs that can modify practically every aspect of your operating system. It's certainly one of the most powerful tools available for Android, and there's simply nothing capable of replacing it.

When you're sitting at your desk trying to get some work done, your Android device can be a big distraction. If a text comes in, you have to pick up your phone, unlock it, then respond with the clumsy touch screen keyboard—and by then, you've probably forgotten what you were doing on your computer.

The V20 is an amazing phone from LG powered by Android. Packing impressive features such as a removable battery, expandable storage, and the latest Android version straight out of the box, the V20 is a tough phone to beat.

Google's Pixel phones have a feature that lets you swipe down on the fingerprint scanner to open your notification shade and Quick Settings panel. It's one of those features that make you wonder why it wasn't there in the first place, since it gives you another way to interact with your device, and your fingerprint scanner isn't being used while you're screen is on anyway.

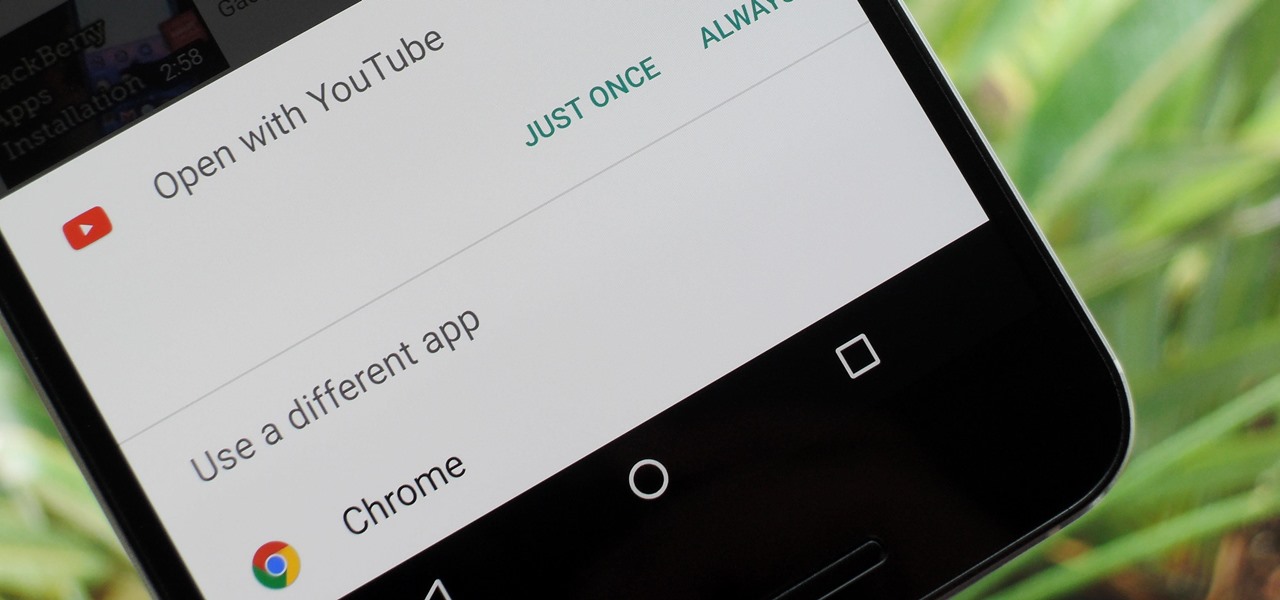
One of Android's biggest strengths relative to iOS is the fact that you can use any app to open compatible links, not just the stock ones that come preloaded on your device. When you tap a link that two or more of your apps are capable of opening, you'll see a message asking which app to launch it with—and from there, the choices are "Just Once" or "Always."

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.

There's a feature in Google's Photos app for Android, iOS, and the web that lets you create shared albums with your friends and family. It's really a useful feature that makes it fun and easy to collaborate on an album with a person or persons of your choosing.

Hello! This is my first post on this awesome website! I know that Windows exploits are less common than the more advanced hacks, but I found something I deem pretty cool and figured why not share it with you all. Alright, enough about me, lets begin.

As you might know, there are a multitude of tools used to discover internal IP addresses. Many of these tools use ARP, address resolution protocol, in order to find live internal hosts. If we could write a script using this protocol, we would be able to scan for hosts on a given network. This is where scapy and python come in, scapy has modules we can import into python, enabling us to construct some tools of our own, which is exactly what we'll be doing here.

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.

Hello my fellow hackers, Welcome to my republished revision of the ruby programming language, Part 1.

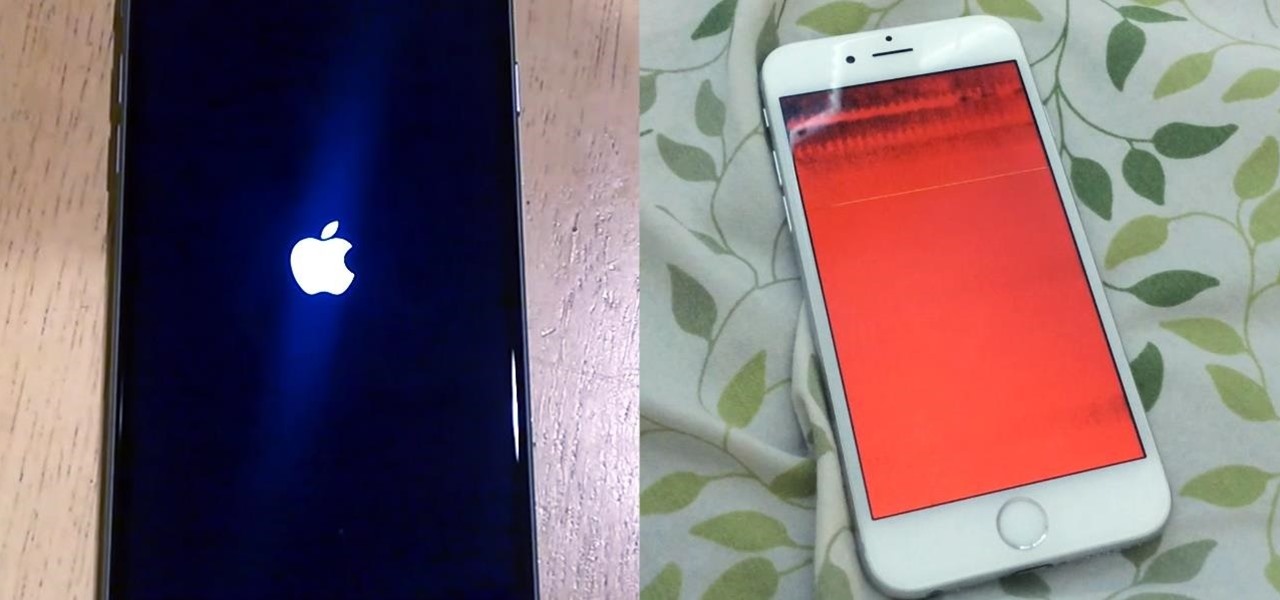
We recently ran into a serious iPhone 6 issue here in the Gadget Hacks office, where the device was stuck in an infinite bootloop with intermittent red and blue screens (of death?) and an unresponsive touchscreen and buttons. From what we can tell, we weren't alone, though some are experiencing only one or a few of the issues we've had.

If you've ever owned an HTC device or anything in the Nexus line, odds are, you have typed the word "fastboot" into your command line at one time or another. That said, odds are, you have only just barely scratched the surface of what this handy little Android tool can do. Let's take a deeper look.

Greetings. This how-to on hacking Windows 7/8/10 etc. admin account passwords using Windows Magnifier is focused on adding, changing, or deleting an admin level account on a Windows 7/8/10 etc.

Nearly two years ago, Peter Chou, CEO of HTC, confirmed that the company would no longer be locking bootloaders. Whether or not they've actually lived up to this claim is debatable. Any phone bought from a wireless carrier comes locked. Only the new HTC One Developer Edition ships with an unlocked bootloader, and it does not have any carrier add-on software installed.

You've gotten used to your brand spankin' new Nexus 7 and finally have a feel for Android, but now you want more features. Well, user Juan Mercator was in that predicament, and asked how to install the ever popular CyanogenMod ROM on his Nexus 7 over on our Nexus 7 SoftModder forum.

Forum member Luciano posted a terrific guide on adding hacks to our phone by editing build.prop. The article was great, but one of best things I saw in it was the "What You'll Need" section:

When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new user has been added and will begin to take preventative action.

Everyone floats in the Dead Sea because the amount of salt in water effects the density. Do a hands-on experiment and practice checking density. Here’s a good science experiment to do in class or at home, if you have access to an electronic balance.

If you have not used your eRecovery system in a long time and have forgotten the password, have no fear. This video is here to help you retrieve your details and use your program again. In this clip, learn how to recover any lost passwords with Acer's eRecovery Manager for Linux.

What is an oscilloscope? Well, it's an electronic instrument that produces traces of color on a cathode-ray tube that corresponds to oscillations of voltage and current. Check out this video to learn how to make the world's simplest scilloscope. The best part? You can do it in five minutes.

The two primary design paradigms in Samsung's One UI Android skin are vertical padding and rounded UI elements. The extra empty space at the top of most menus moves touchable elements closer to your thumb, and the rounded UI elements match the curved corners of modern smartphone screens. While you can't add the vertical padding on other Android phones, you can now get the rounded corners.

One of the biggest bummers about Netflix is the inability to create different lists for your favorite movies and TV shows. Instead, you're only able to lump titles into the single default "My List," and that can be impossible to browse. It doesn't separate titles into categories or genres, and titles are arranged for you automatically, so there's not much room for customization.

If you're using a VPN app to block ads or secure your Galaxy's internet connection, Samsung has decided you need yet another non-dismissible notification from One UI to tell you about it. Not just a status bar indicator like Bluetooth or Wi-Fi, but a full-size alert that can't be dismissed. The entire time your always-on VPN is running.

Screen recording on your iPhone is one of the easiest ways to share what's happening on your screen with family and friends. The problem is, everyone knows it's a screen recording when you pull open Control Center to tap the record button. What if we told you there's a better way to end a recording, so what you're left with is a clean video?

If you're concerned about someone accessing your OneDrive files, you may want to upgrade your protection by enabling fingerprint or Face ID unlocking. Your sensitive information deserves to be protected, and now you can do so easily. Worry no longer — if you need to let someone else use your phone, with a password-protected OneDrive, sneaky file grabbers will be out of luck.

Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.

Rooting usually means sacrifice. With most root methods, you lose access to apps like Netflix and Android Pay when SafetyNet gets tripped. More importantly, you lose the ability to accept OTA updates, forcing you to manually flash new Android versions. But there's a way around all of this if you root the right way.

Next to things like natural disasters and disease, the specter of war is one of the only things that threatens to derail the 21st century's long stretch of technological innovation. Now a new app is using augmented reality to remind us of that by focusing on those most impacted by war — children.

With the addition of the OpenSSH client and server in the Windows 10 Fall Creators Update, you no longer have to rely on third-party programs to open an SSH server and connect to a Windows machine. While still a beta feature, this represents a long-overdue update fulfilling a promise made back in 2015.

After installing the new iOS 11 update on one of our iPads, we noticed something peculiar — AirDrop simply stopped working. The button was still there in the revamped Control Center, but it was almost imperceptibly grayed out. Tapping it did nothing, nor did long-pressing or 3D Touching. Even more perplexing, AirDrop was just working flawlessly before the update.

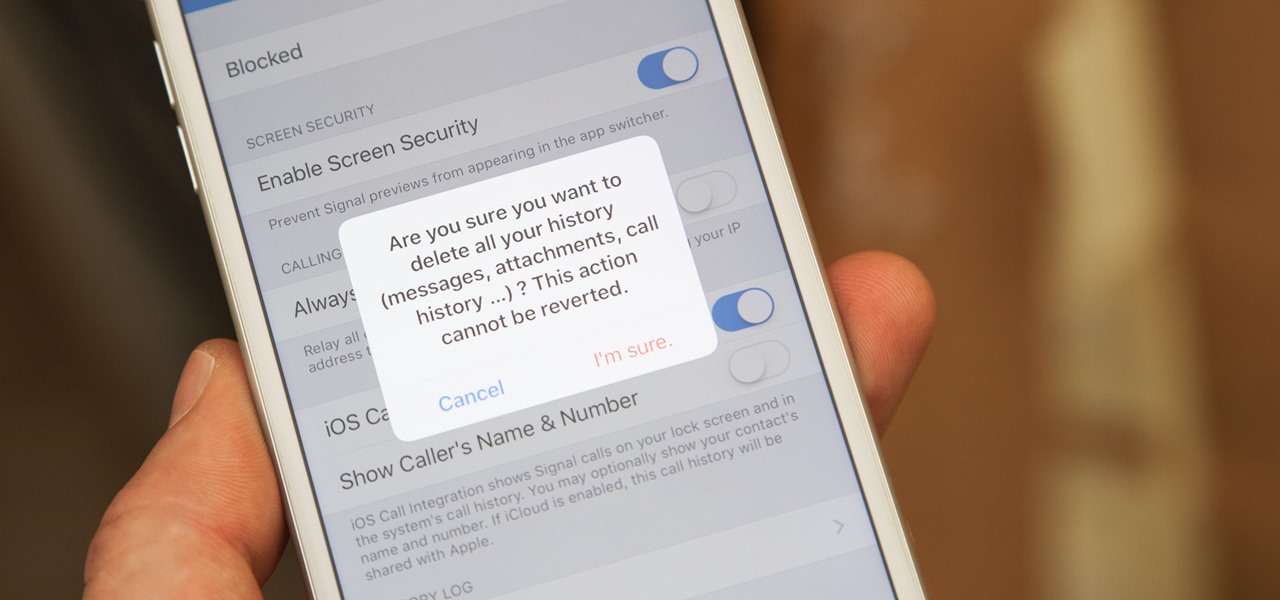
If thieves, hackers, law enforcement, or other would-be enemies should ever gain entry to your smartphone, they could also access conversations you've had in Signal Private Messenger. To better secure your encrypted communications, you can password-protect the whole app and its contents — but only on Android. Even then, it's necessary to perform data deletion on a periodic basis, if not immediately.