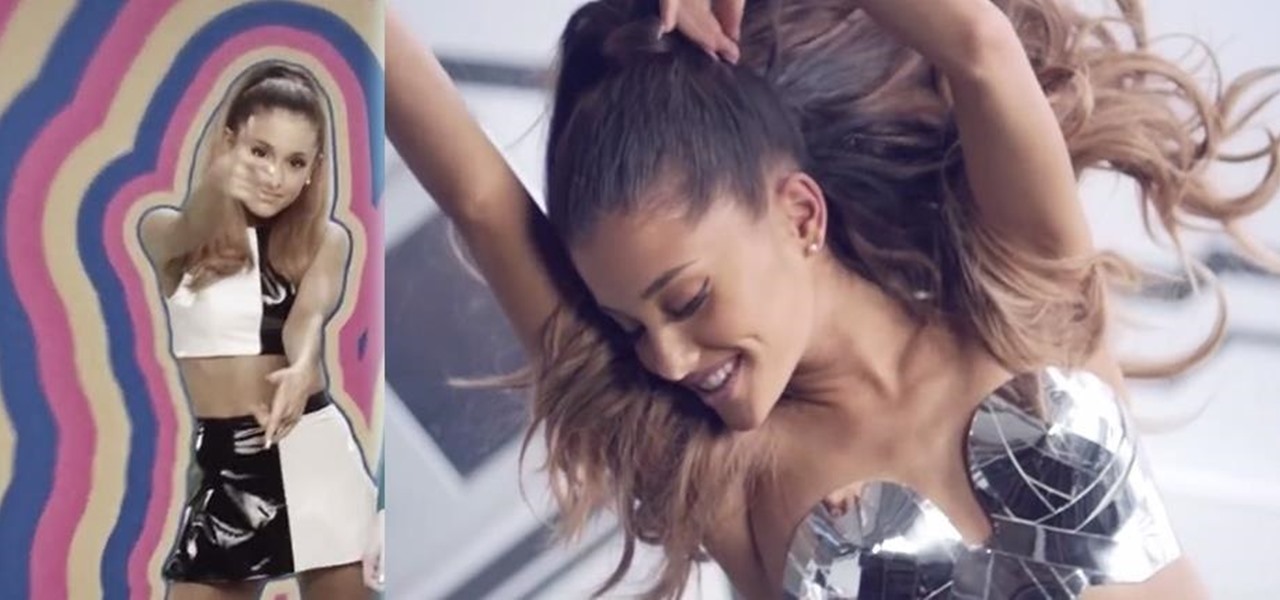Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the victim portion of the shell. Today, we'll be building the attacker portion. This script will initialize interaction with the victim portion of the shell, send commands, and receive the output.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

My least favorite aspect of the winter season is how my fingers always turn into stiff, numb digits, unfeeling and seemingly incapable of making even the slightest movement. Yes, that might sound overdramatic, but if you hate wearing gloves like I do, you probably know exactly what I mean.

When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a little social engineering, this can be a very effective technique.
Amazon is slowly trying to gain as much influence in the tech world as it has in the consumer market, and with the Amazon Fire HD 7, they have their eyes set on taking on the "budget tablet" space.

If you somehow forgot the pattern, PIN, or password that locks your Android device, you might think you're out of luck and are destined to be locked out forever. These security methods are hard to crack by design, but in many cases, it's not entirely impossible to break into a locked device.

On Thursday morning, May 28th, Google announced an upcoming version of Android—and within a few hours, a preview build of this so-called "Android M" release was made available to select Nexus devices.

Due to the way Android works, you normally need to be rooted to uninstall the pre-loaded system apps, aka bloatware, that came with your device. This is because the underlying files for these apps are stored on your system partition, which can only be modified with root-level access.

Brought to you by Brother International Corporation. Whether you are looking to complete a home improvement task, or you are hoping to start a new hobby, staying focused and energized during projects can be daunting. With emphasis on organization, planning, and creativity, we gathered together tips that will help you successfully tackle any project on your plate!

Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote code execution," so we are focusing our exploit development here on a buffer overflow.

Pop princess Ariana Grande has had quite the year. She released her second consecutive number-one album and is on the cusp of her first headlining tour in the U.S. early next year.

Apple just unveiled iOS 8 at the Worldwide Developer's Conference, and it has a lot of exciting features to play around with. Unfortunately, it won't be available to the public until this coming fall—but that doesn't mean you can't get it right now.

The old "my battery is dead" excuse for not calling your mother may soon be a thing of the past. A team from the Korea Advanced Institute of Science and Technology (KAIST), led by Professor Jo Byeong-jin, has developed a "wearable thermo-element" that can be built into clothing to power your electronic devices. The science behind the innovation converts body heat (thermal energy) into usable electric energy. Made with lightweight glass fiber, this small thermo-element strip can produce about ...

You've unlocked your bootloader and rooted your HTC One running KitKat, but there's still one lingering aspect of security you've yet to rid yourself of—S-On—the extra security measure HTC implemented into Sense.

Okay, so you're rooted and need to return your Nexus 5 to its stock firmware. Whether it's because you need to send your phone in to the manufacturer to fix a defect or you just want to use the device's over-the-air updating feature, unrooting and returning your Nexus 5 back to its fresh-out-of-the-box state is a fairly simple process with the right tools.

In direct competition with Pandora, iTunes Radio, and Spotify, Samsung has just launched Milk Music—a strangely named, yet completely free music streaming service for Android.

With the Samsung Galaxy Gear smartwatch only several weeks old, the extent as to what you can do with it is limited since there are only about 70 apps in the Gear Store right now, and a lot of those need the full app installed on your Samsung Galaxy Note 3 in order to function properly.

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?

Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux. There are some exceptions, though, including software like Cain and Abel, Havij, Zenmap, and Metasploit that are developed or ported for Windows.

Duct tape is the king of all household items. You can use duct tape for practically anything, like this sweet wallet. But duct tape isn't the only crafty tape out there; masking tape holds its own, too.

The reason Amazon's Kindle has become so popular over the past several years is due to the amount of digital books one can fit inside—over 1,000 for the smallest Kindle. Gone are the days of lugging around heavy books to school and the airport. Instead we can fit our e-readers snugly inside our bags and never worry about forgetting a book.

As if you needed another reason to lock down your Facebook profile, the company's sketchy new partnership with data mining firm Datalogix is geared towards giving advertisers more information on what you're doing—even when you're not online. It's just not enough that they can target ads based on your preferences, now they want to know how those ads are influencing your buying habits in the real world.

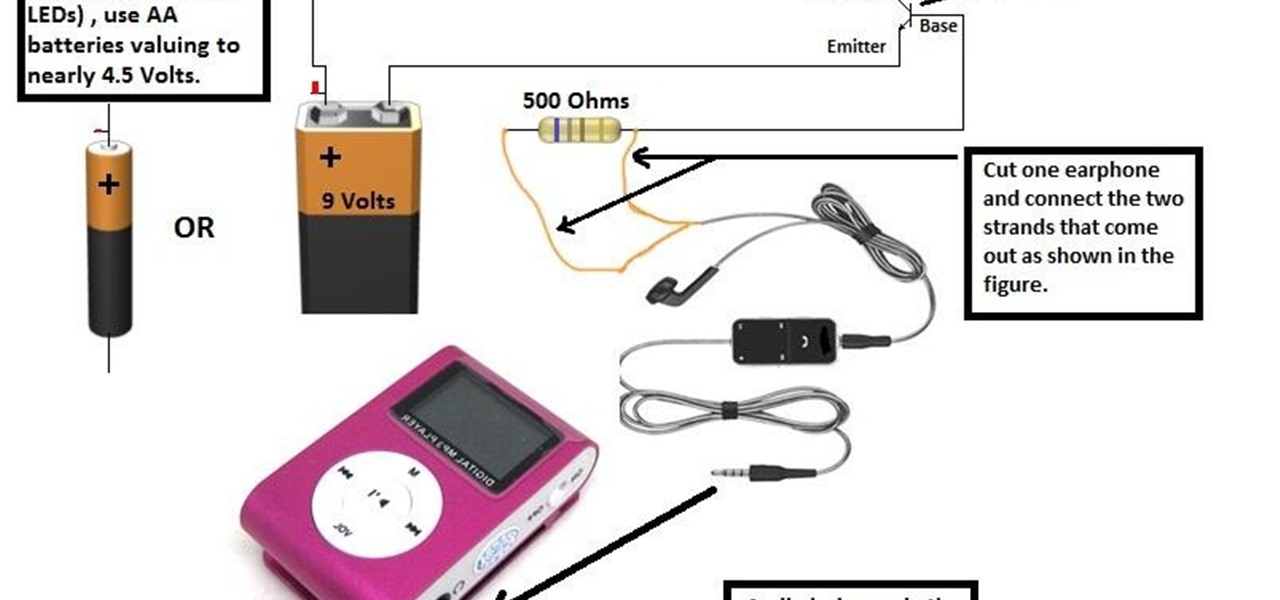
You must have seen some expensive mp3 players and CD players which have LEDs fixed on them and they dance to the tune looking really pretty.

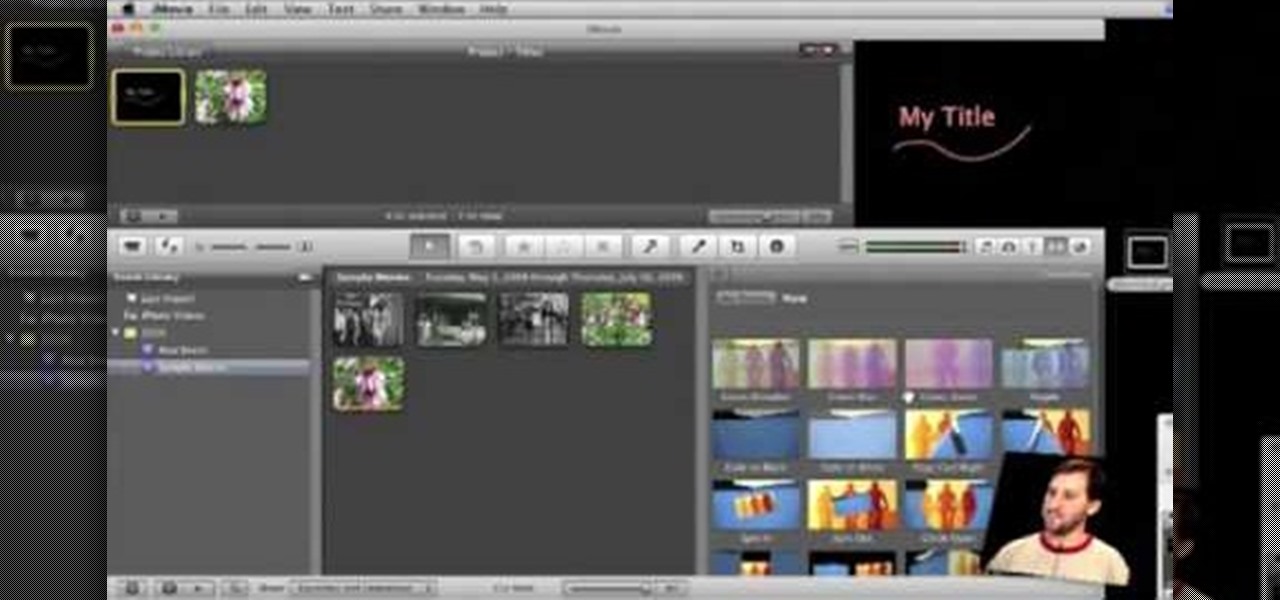
In order to make Custom titles in IMovie '09, you will need the following: Seashore or any other compatible program.

In this How To Video Kurtis Elwell will walk you through how to do a fakie on a BMX. The best place to start learning how to roll a fakie is on a steep hill or incline. As soon as you start to lose momentum on the hill you will stop for a moment then start rolling backwards. If your BMX is equipped with a cassette wheel it will start to force you to pedal backwards. Then, when you are rolling backwards and want to turn around, turn your front wheel to a 45 degree angle. Lean back a bit so all...

The Mac OS's Disc Utility allows for the encryption of files. To open Disc Utility click on the magnifying glass (spot light) up in the top right hand corner, and search for Disc Utility. Click on the first result in the list. Once Disc Utility is open, click on "create a new image" in the top tool bar. A new window will drop down, where you choose what you want to save the new image as. Give it a name, and choose the size you want it to be. Moving down, choose the encryption you want to use ...

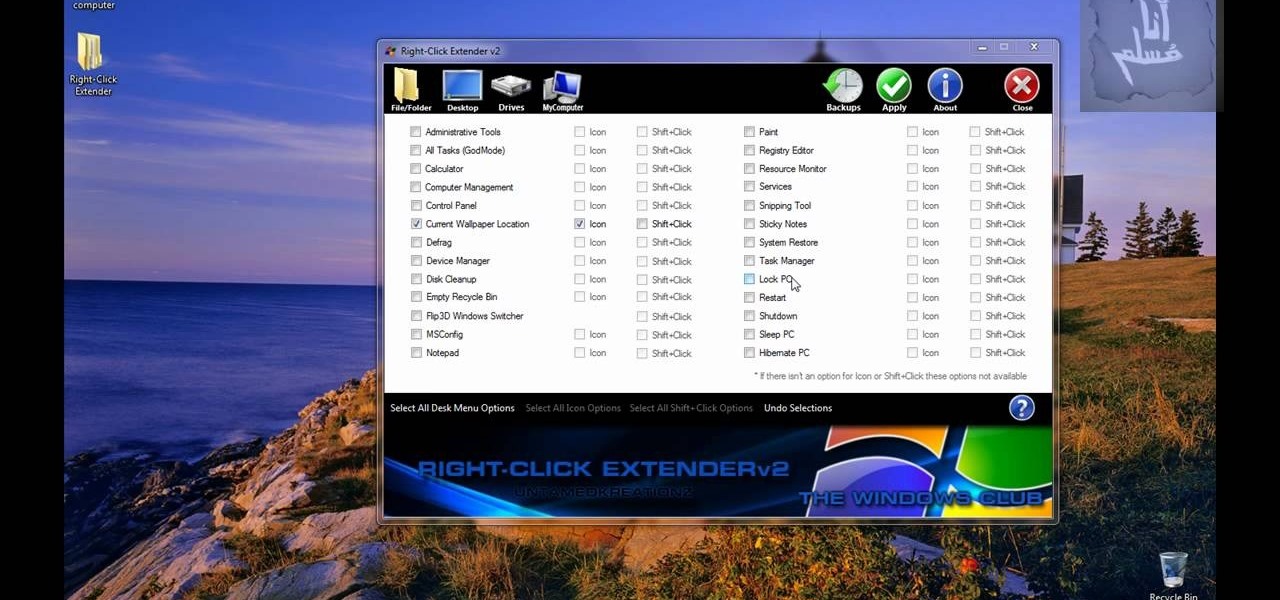
Tired of being limited with your right-click options in Microsoft Windows? There's a program that could help you out, and it's called Right-Click Extender. Insert many different additional items to the right-click context menu.

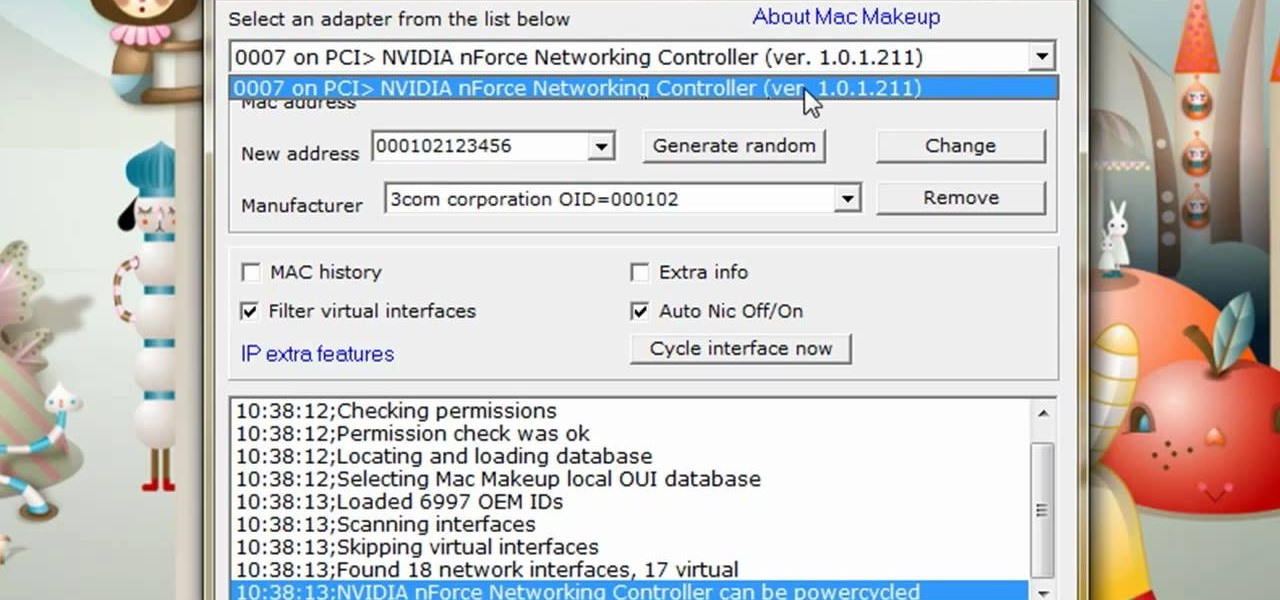
The video is about how to change the IP address. MAC address is the unique identifier a site of the most network adapters. MAC address is used to determine what IP address the computer will have and one way to change the IP address is by changing the MAC address. The method is only applicable for the windows systems and for the MAC systems you need to look at the link provided. In Windows in the start menu, type cmd in the run/search box, which will launch the command window. Type ipconfig/al...

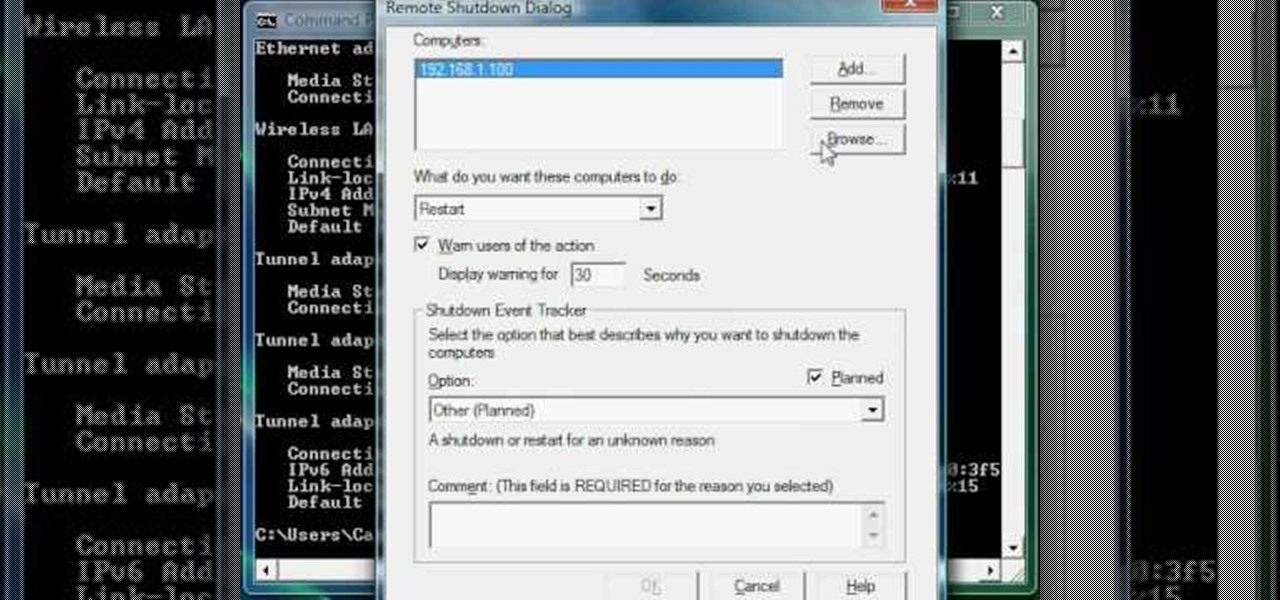
Now you can find your IP address if you need it and you don't know it, it very easy. Or if you have problem with a person on the internet, now you can discover who that person is. You can find her/his IP address and after that you can find her/his real name. But after you find the IP that you were looking for, you have to check if the person who own this computer is in your network, because if you want to find his/her name, the program works only if the owner is on your network. So if you are...

Want to forget about always pulling out your credit card to purchase something on your BlackBerry? There's a little application that can do it all for you? But how? Best Buy has answers. The Best Buy Mobile team explains how to use the BlackBerry Wallet application. This application can store personal information such as credit card information and shipping addresses on a secure website for easy access when shopping online.

Treasure may be buried as close as your own backyard. If you have some time to kill, try the art of treasure hunting. You’ll be sure to discover lots of interesting thing after learning how to use a metal detector to look for treasure.

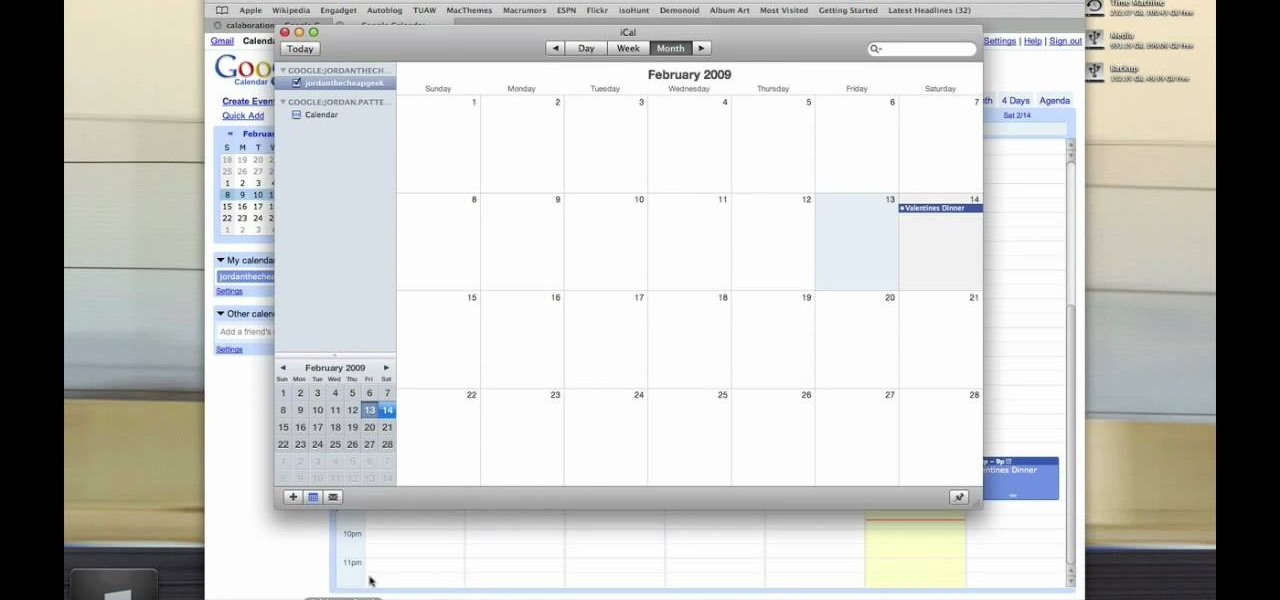
Jordan Patterson the Cheap Geek has made a video showing you the steps to sync your contacts and calendars on three mobile devices together, the iPhone, a laptop running Windows, and a Mac running OS X utilizing a few downloaded programs and Google Calendar. First he shows you how to sync calendars on the Apple computer, by downloading a program from Google code called collaboration code, and then running it. After putting in his g-mail account information, he tells the program which calendar...

Some computers might now have a working DVD drive and in such cases you can use a USB pen drive to install Windows 7 on it. To do this first connect the USB drive to your computer. Now go to the command prompt and run the 'diskpart' command to find the details of the hard drive. Use the 'List Disk' command to list all the drives on you computer. You can also find the USB drive in the list. Now use the Select disk command to select the disk. Perform a clean command of the disk. Next create a p...

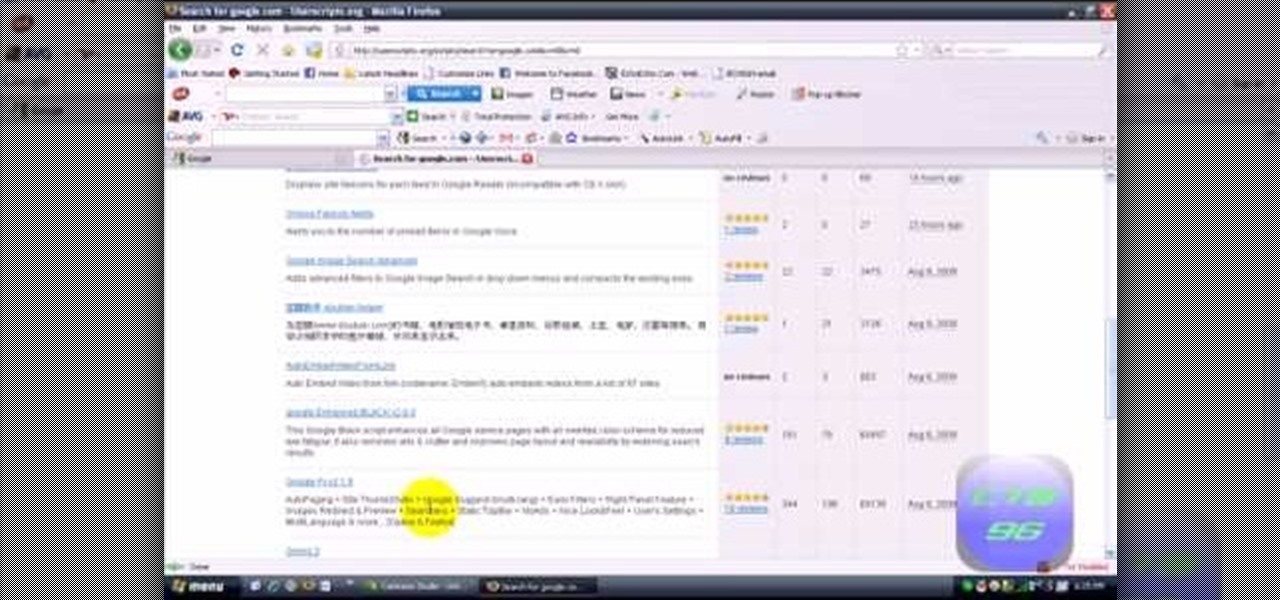
Greasemonkey is a Firefox add-on which works as a script manager for the collection of scripts available on the userscripts.org website. It can be used to manipulate the view and functionality of websites which has a user script. Greasemonkey only works in Firefox and not on any other web browser.

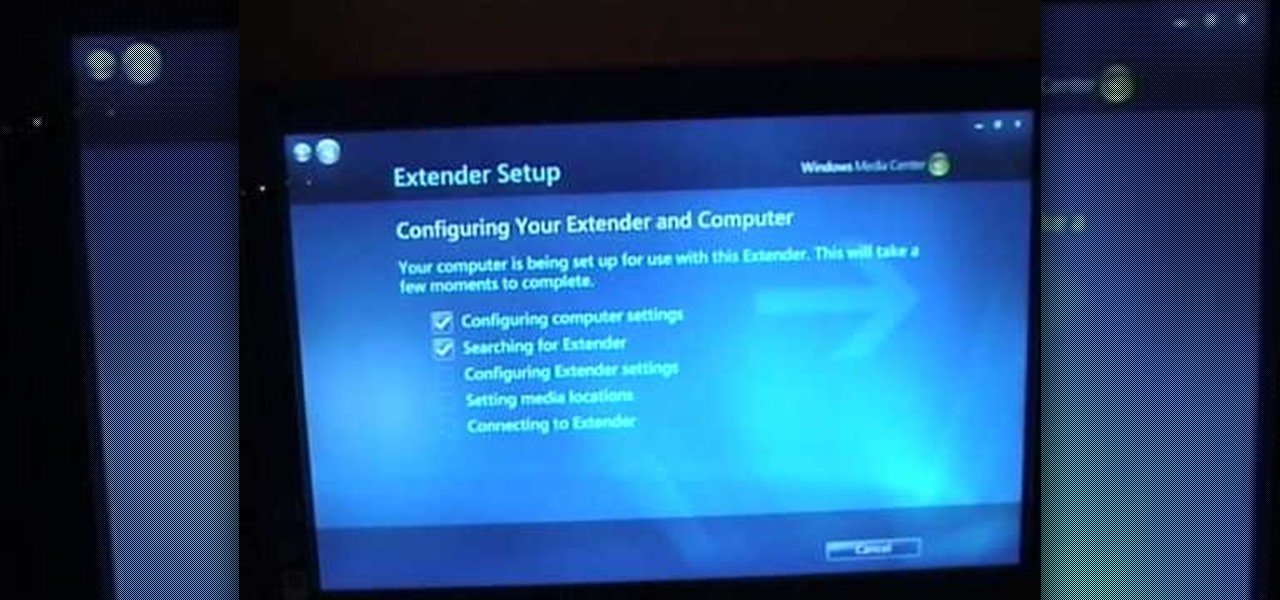
With Windows Media Center, you will have the ability to watch videos, live TV, and listen to music on the XBOX 360 without having to use your computer. You’ll need to have the following things: A PC equipped with Windows Media Center, your XBOX 360, and a fully functional high speed home network. On certain Windows 7 or Vista machines, Media Center is already included. (If not, it can be downloaded from Microsoft) A wired network is preferred for the best connection, although a wireless netwo...

IngletonPottery demonstrates how to create a giant clay pottery novelty goblet in less than eight minutes in this video. The goblet can be used as a decorative piece or it can be used to drink from. The choices are endless for this giant piece of art. The giant goblet begins as a big blob of clay. A portion of the clay is wet and the spinning table begins. While the clay is wet it is placed on the spinning table and then the molding process begins. To mold the clay requires concentration and ...

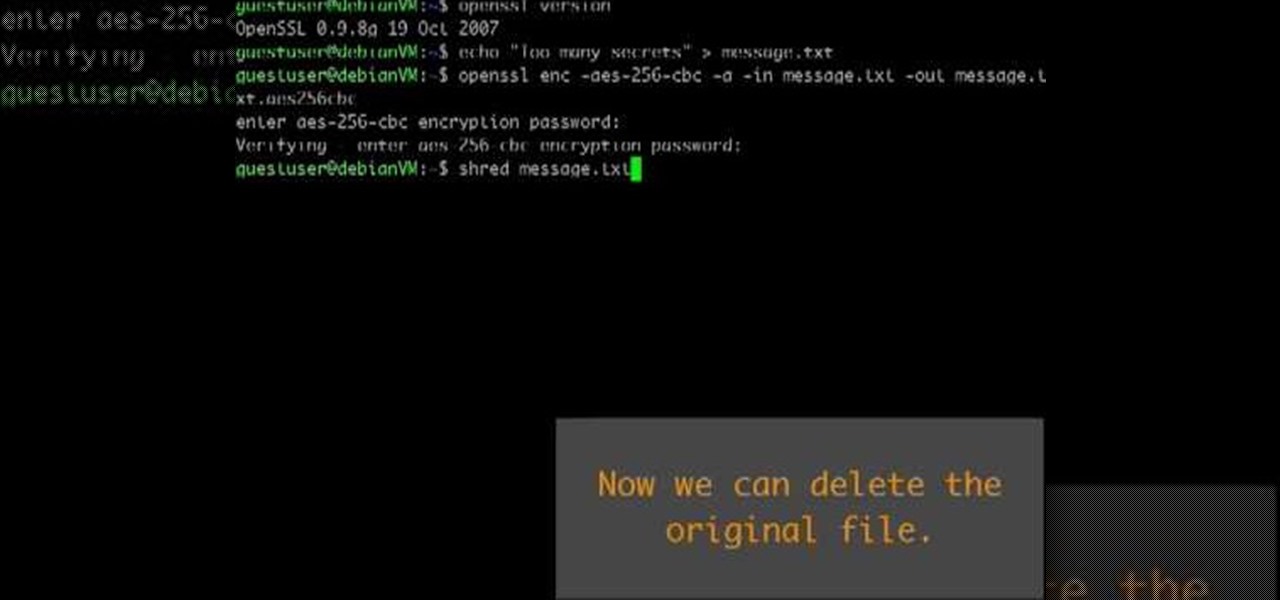
This video shows how to encrypt files with OpenSSL in Debian Linux. First we check if open SSL is installed on the system. If not, install it using packet manager. Next create the file going to be encrypted. Now encrypt the file. In this case AES algorithm in ypher block chaining mode is used. AES is US-government standard and can be considered secure. Now we are prompted for a password. In order for the encryption to be secure, we need to choose a strong password. Now we can delete the origi...

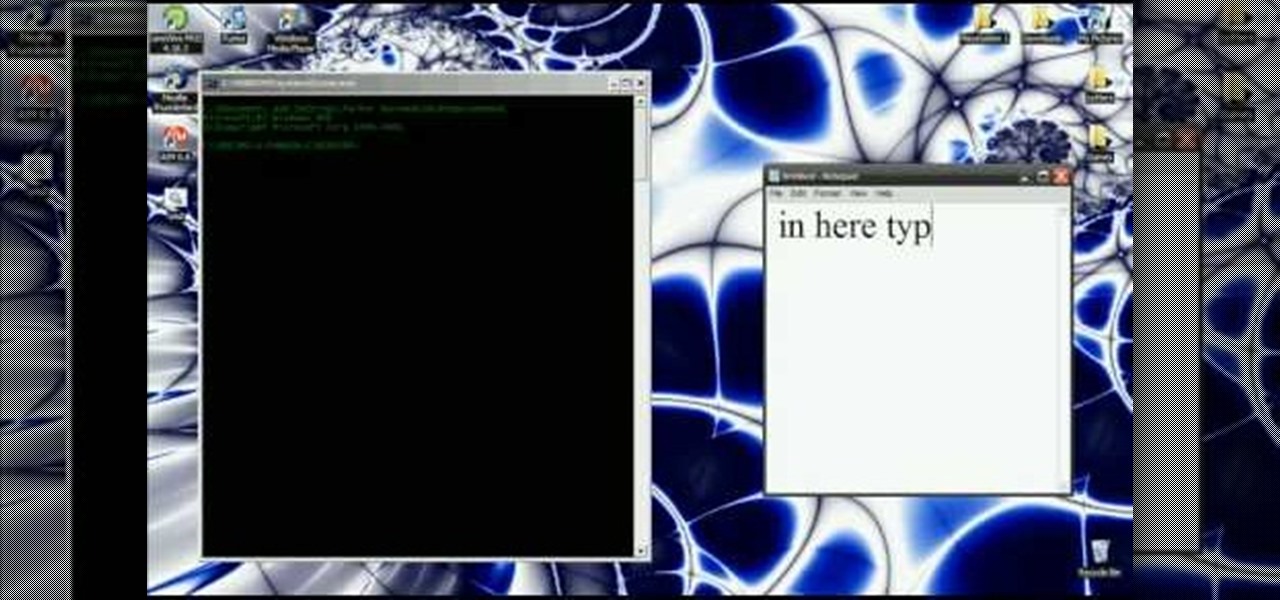
In this video you will learn how to get past website blocks on your school network. Some school computers have command prompts blocked. If this is the case then you will want to open a notepad. In the notepad type command, then save as something school related, making sure the file name ends with .bat. Do not save it on the desktop, but rather in a folder deeper on the unit. Once you've saved it, make sure no one is looking, then open the file. It will bring up a blank black window. In the bl...

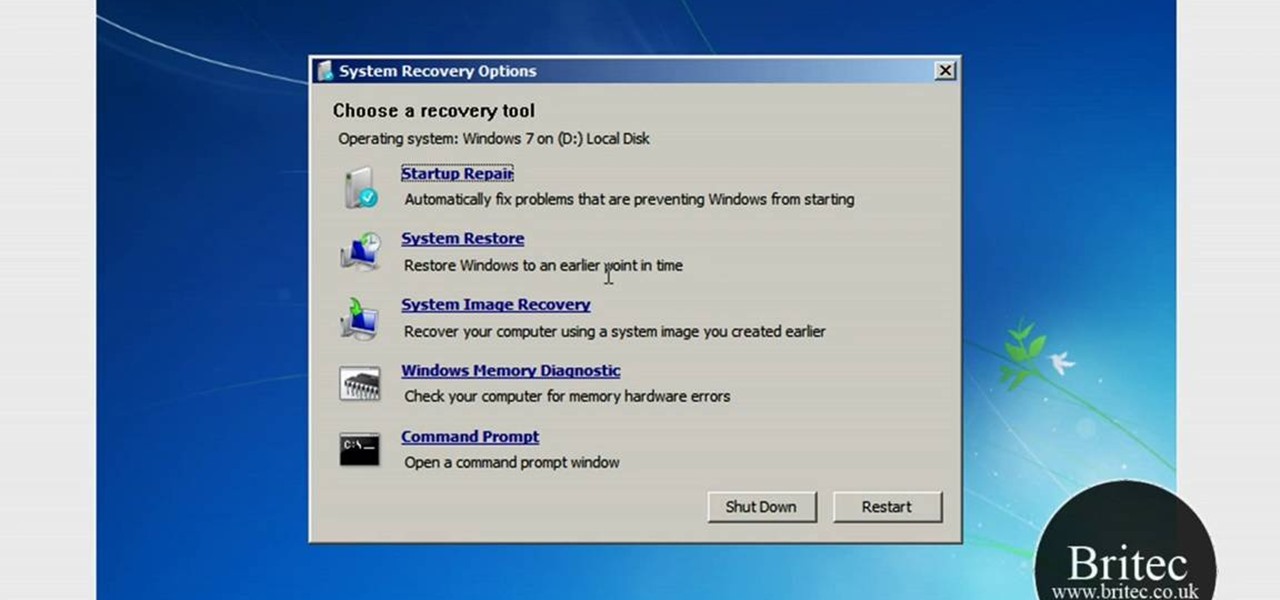
This video tutorial from Britec09 presents how to backup and restore Window 7 registry.First, press Start button and enter regedit command into Start Search area.Registry editor window will open, click File-Export.This option works on all Windows operating systems.Type file name - registrybackup and click Save. You can save it wherever you want, but in this video it was saved to Desktop.Next step is to reboot to Windows DVD. Insert you Windows DVD and reboot computer.Press any key to boot fro...