A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

Nintendo may be developing cases that'll turn your iPhone into a gaming device like the Game Boy, but until something materializes there, you're stuck with cheap knockoffs on Amazon or a real Game Boy or Game Boy Color. But there's something else you can do to play eight-bit Nintendo games on your iPhone right now.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

While the Apple Watch does have up to 18 hours of battery life each day on a full charge, your results will vary depending on how often you use it and what you're actually doing with it.

Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.

The Reminders app is a simple yet powerful task manager, and it does a great job of reminding you to start an errand, alerting you to a project that's supposed to be done, or prompting you about a recurring chore. But with the latest Reminders update, the dates and times you set for tasks can act more like due dates thanks to the new early reminders feature.

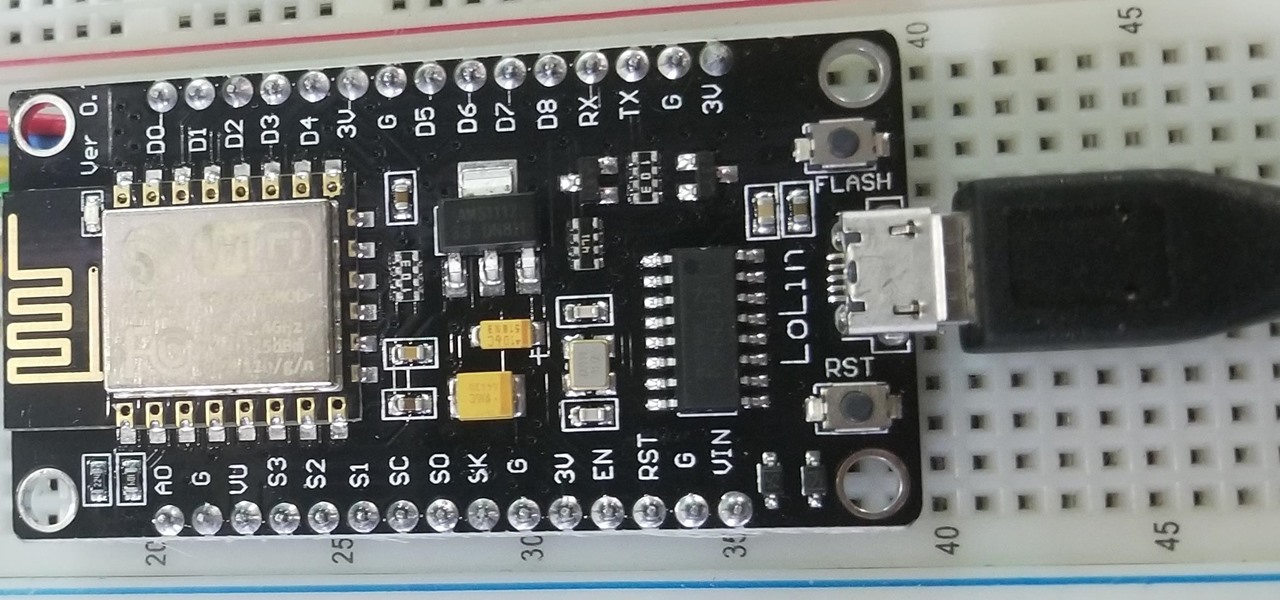
Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to sniff the air for packets from any device we want to track, turning on an LED when it's detected nearby.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

If you buy an Android phone from any of the big US carriers, it will come with several extra apps in addition to any apps the manufacturer preinstalled. It's all in the name of profit, of course. Some of these apps are from companies that paid the carriers to distribute their software, and some are from the carriers themselves, usually aimed at upselling you or perhaps collecting a little data.

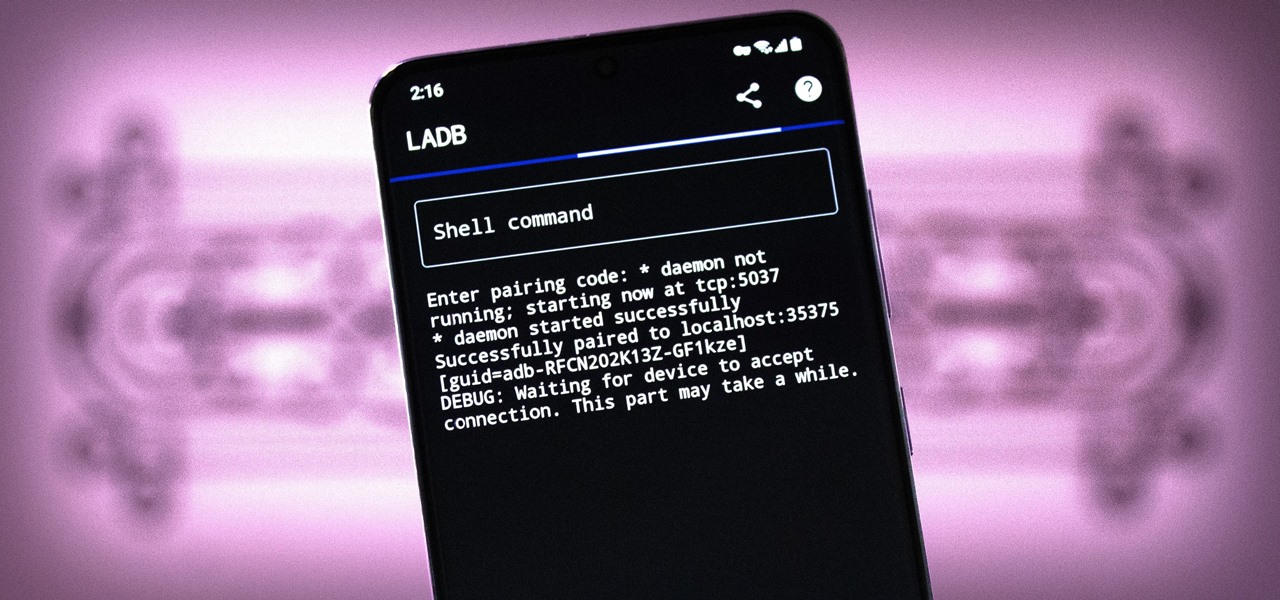
There are three tiers to Android customization: things you can do by default, things you can do with ADB, and things you can do with root. While root is still pretty tricky to get, ADB mods just got a lot easier.

If it has an internet connection, it's got a huge attack surface for hackers. But what makes your phone even more dangerous is its portability and the collection of sensors it houses that can be just as good at tracking you as the camera and mic.

As the iOS 18 beta continues, Apple's still investing time into fixing up iOS 17. Compared to iOS 17.4 and iOS 17.5, which both had over 30 new features and changes, iOS 17.6 is a relatively small software update for iPhone. But there are still some important things to know about.

Apple last month released iOS 17.2, its biggest iPhone software update since iOS 17.0, with 60 new features. Now, as of Jan. 22, we have iOS 17.3. Overall, it's not the behemoth software update that iOS 17.2 was, but it has a few exciting new things you'll definitely want to know about.

Apple has a few exciting surprises for you in its latest iOS 16 and iPadOS 16 software updates. Released on Thursday, May 18, version 16.5 includes new features, bug fixes, and security patches, and there are even hints of some big things coming in future software updates for iPhone and iPad.

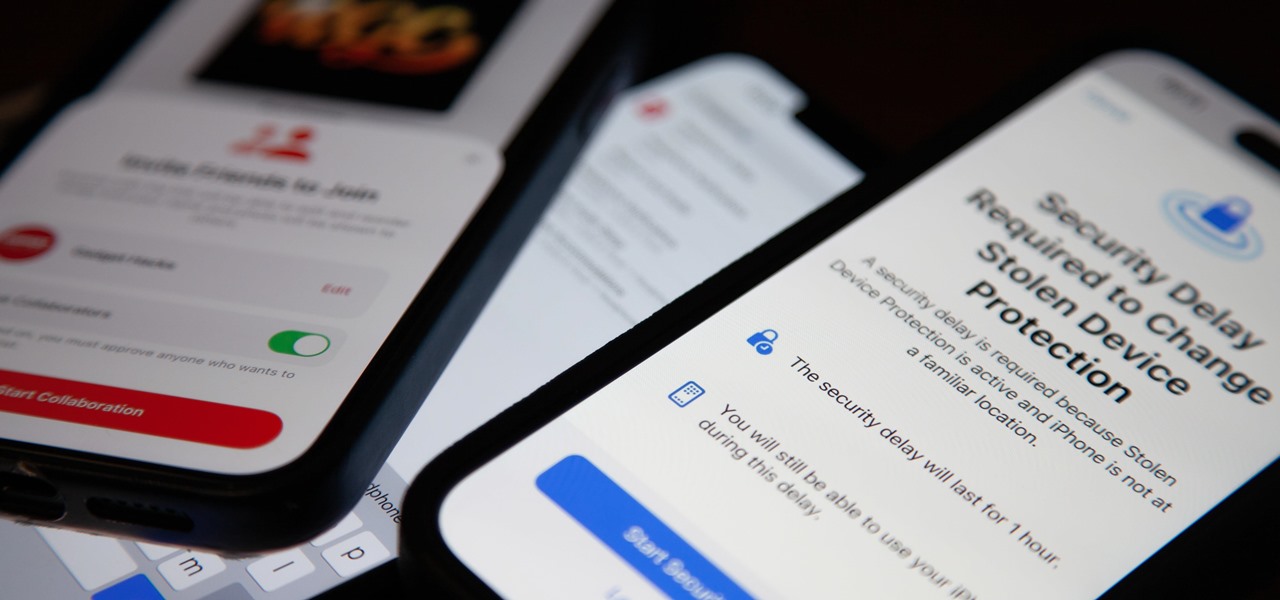
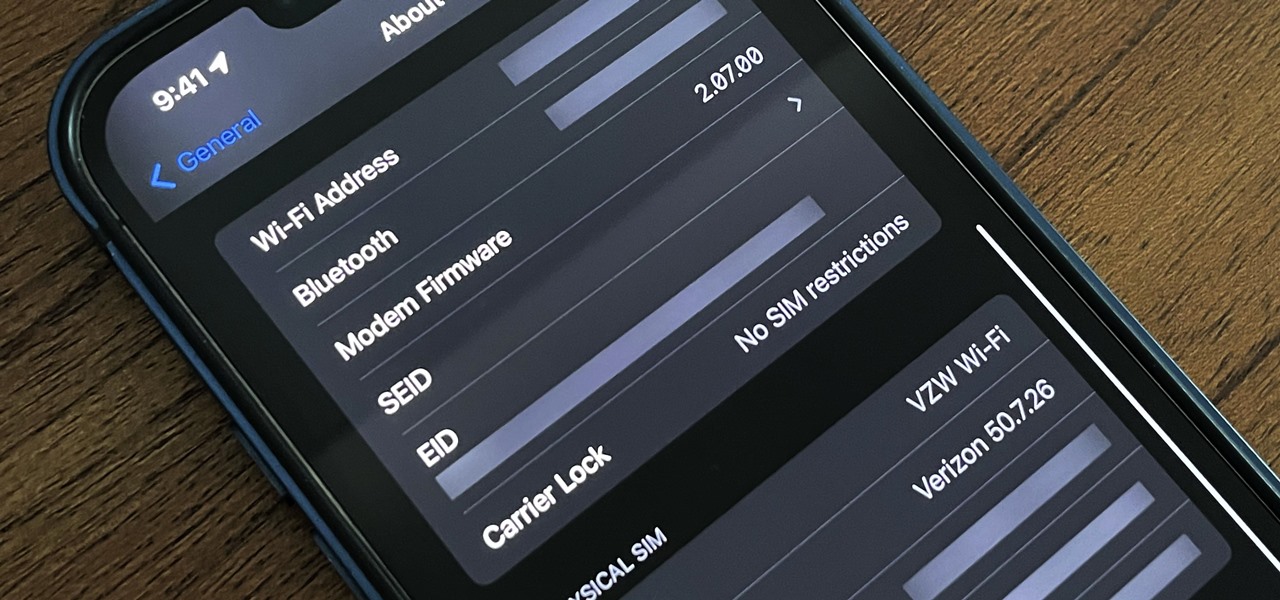
If your current cellular provider costs too much, has poor reception in your area, or doesn't support features you'd like to use, switching to another carrier is the obvious move. But can you bring your current iPhone or Android phone?

While it doesn't come with any iPad models out of the box, the Apple Pencil is perhaps the best iPad accessory you can get. It's a powerful writing and drawing tool with an intuitive design and user-friendliness that makes it easy to take notes, draw sketches, mark up documents, and more. And there's a lot you can do with it — some of which you may not have noticed yet.

Apple's iOS 16.3 update for iPhone had impressive new features, but iOS 16.4 might impress you even more.

Here, you'll see how to properly teach children some vocabulary words by use of a scaffolding method. You'll learn about modeling, prompting, monitoring understanding, coaching and much more.

It seems like nowadays, whenever Facebook rolls out a new feature, it's immediately controversial. Social Ads put your name and face in the spotlight, Instant Personalization shared your information with partner sites, third-party apps were allowed to access your home address and phone number, and now Tag Suggestions implement facial recognition software to automatically identify your friends in uploaded photos. Most are calling it problematic or creepy, some insinuate CIA involvement, and it...

Tonight is the night. Christmas Eve. The night where Santa Claus and his trusty reindeer soar across the skies to deliver presents to all the good little boys and girls around the world. But tell me— do you know where Santa Claus is right now?

With FarmVille being one of the hottest Facebook games on the market, it's no wonder it's the primary target for scams and virus downloads. Anyone playing FarmVille is at risk, but the primary targets are those looking to improve their gameplay and build their farms and neighbors up. These "farmers" are the ones seeking quick hacks and cheats.

Last month, mobile application consultant Jonathan Stark unleashed his Starbucks Card to the public as an "experiment in social sharing of physical goods using digital currency on mobile phones." Basically, he purchased a Starbucks Card and registered it via the Starbucks Mobile App for iPhone (there's an Android one, too) which allows caffeine addicts to pay for coffee and baked goods with their mobile device. He then took a screenshot of the barcode and let anyone on the web download it for...

Filter effects aren't a new thing. But when Instagram hit the market, everybody began using them because it was simple. Take a picture, add an effect. It wasn't only easy, it was fun. It started a craze among smartphone users everywhere, prompting a slew of retro photo filter apps to pop up for Android and iPhone. One app that stands out from the crowd is FX Photo Studio.

After the media outcry of Google Buzz's privacy issues, Google has set its goals on making the privacy parameters of Google+ simple to learn and as explicitly manageable as possible. No small feat.

Spam is everywhere and Facebook is no exception. In fact, spammers are constantly stepping up their game by tricking unsuspecting Facebook users to participate in quizzes, games, apps, or "new features" that are actually dangerous computer viruses, spyware, or other trojan horses in disguise. Their attempts even trick people into unknowingly becoming spammers themselves.

There’s no point to playing all of the different tower defense games available today. Most adhere to the original formula, so playing 2 or 3 really good ones (like those mentioned in my previous post) would be more efficient.