Many of us choose to use an iPhone — as well as other devices in the Apple ecosystem — because of the company's dedication to user privacy and security. If you need more proof of that commitment, look no further than iOS 14.5, released April 26, which adds new tools to protect our data while browsing the web and more control over the data installed apps collect on us.
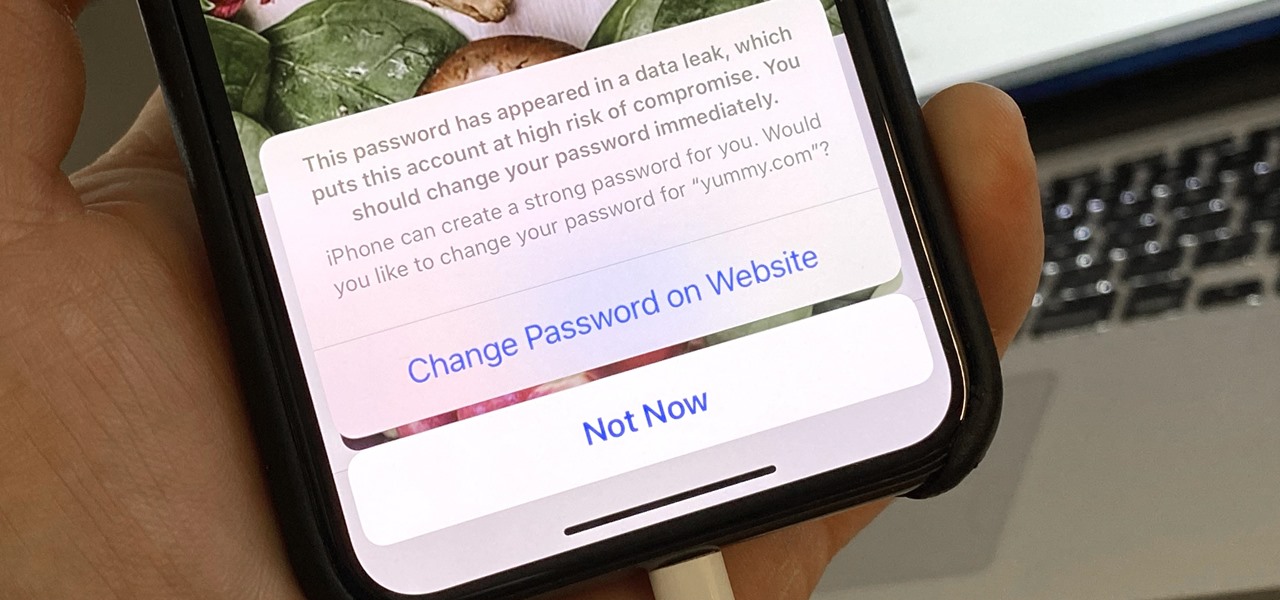
Everything lives online these days, so it's not uncommon to have hundreds of credentials for different accounts on apps and websites. That's why a password manager is a must, and your iPhone has one built right into iOS that you can start using today. In iOS 14, it's gotten even more useful since it can now monitor your passwords regularly to see if any match leaked password lists online.

With over two billion websites floating around cyberspace — only 400 million are estimated to be active — you need every tool you can get to stand out. Great design, fonts that capture attention, and SEO placement are all necessary ingredients to success.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

If there's one strength of Apple's that iOS and Android fans can agree on, it's the company's dedication to user privacy. With each new iteration of iOS, Apple builds upon these foundations, enhancing and increasing each iPhone's ability to protect its user's data. In iOS 12, Apple has added many new features to Safari, most of which have their own unique way of keeping you safe online.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

As you're surely aware, your phone can be used against you. Thanks to our cameras and microphones, a clever hacker can obtain access to your device and invade your privacy. But spying isn't limited to just these two sensors — gyroscopes, proximity sensors, QR codes, and even ads can be used to paint a very clear picture about who you are and what you're currently doing.

There are a number of options and hidden menus within Android that provide users more control over their device. With this control, you can better manage how your phone operates. We came up with a list of tips and shortcuts that, when used, will slowly put you on a path to becoming an Android power user.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

Any internet user will need to download files eventually, and most simply have faith that what they are downloading is trustworthy. This doesn't give much clarity into the contents of the file, but if the file's author published the original checksum, comparing it to the SHA-256 hash of the downloaded file can ensure nothing was tampered with.

Throughout this NR50 series, we have talked about the incredible growth the augmented and mixed reality space has seen in the last year. More devices, software, developers, and use-cases seem to arrive daily. For this growth to have occurred, it took the work of many people, from many different backgrounds and skill sets — and Next Reality wants to recognize them for all that they have done and are doing.

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

The ability to make a meal for yourself used to be one of those life skills you had to learn or otherwise you would starve, but the rise of convenience foods, takeout, and other aspects of modern living have made it entirely possible to be a grown person and not know what to do in the kitchen.

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

Below are the official rules and guidelines for submitting content to WonderHowTo. Please look over them before publishing any articles. Ignoring the rules could result in deletion of your article or being flagged as a spammer. Most of these rules apply to comments as well.

In today's world of social media, there's really only two powerhouses—Facebook and Twitter. And those of you with Twitter accounts know the power of a Tweet. Getting more followers means reaching more people, but the vast majority of Tweeters are following only a handful of Twitterers themselves. Do you ever wonder why them? What's so special about these selected followed users? Is it worth it to follow them, too? That's up to you, but if you're searching for more people to follow, then it's ...

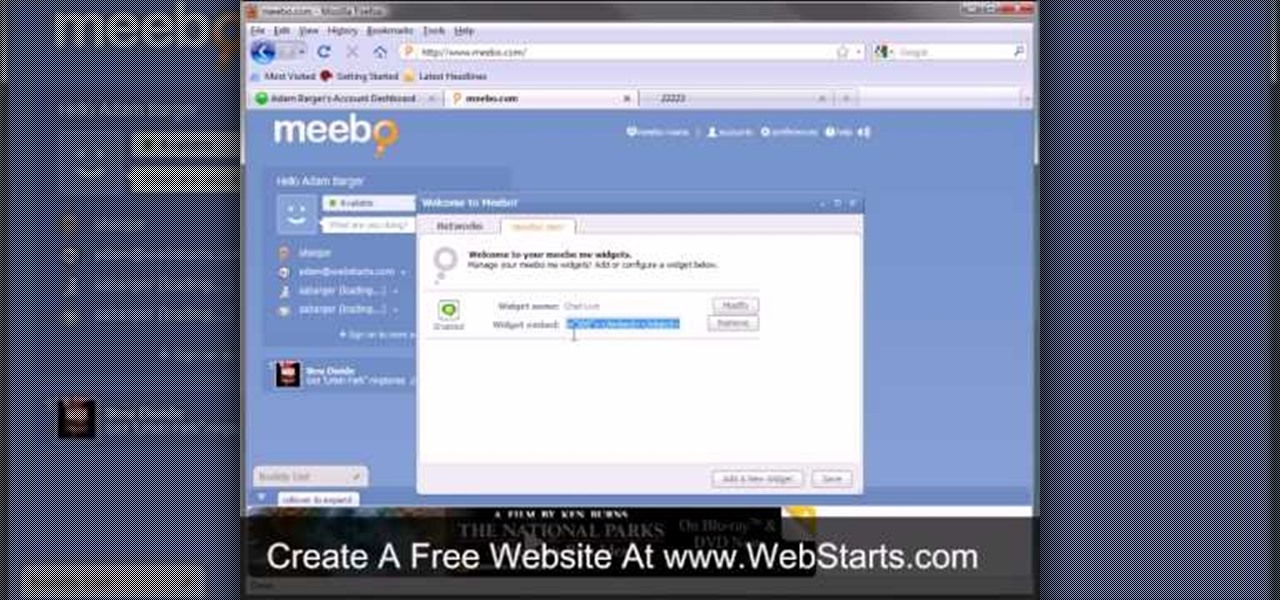
In this video, we learn how to add live chat to your website. First, go to the website Meebo and log into your account. Now, you will see the interface and the accounts you have associated with this client. There are several chat engines you can use through this interface. Once you have added all your chat clients, you can participate in the chats that occur on your website just from this one website. In order to add this widget to your website, go to preferences and choose the option for wid...

SQL injection is a type of code injection that takes advantage of security vulnerability at the database level. It's certainly not the easiest form of hacking, but if you're serious about turning a website upside down then this is the way to do it.

At first, it seemed like a clever art installation housed on the web, but now we're not so sure... the Newstweek hack may indeed be legit.

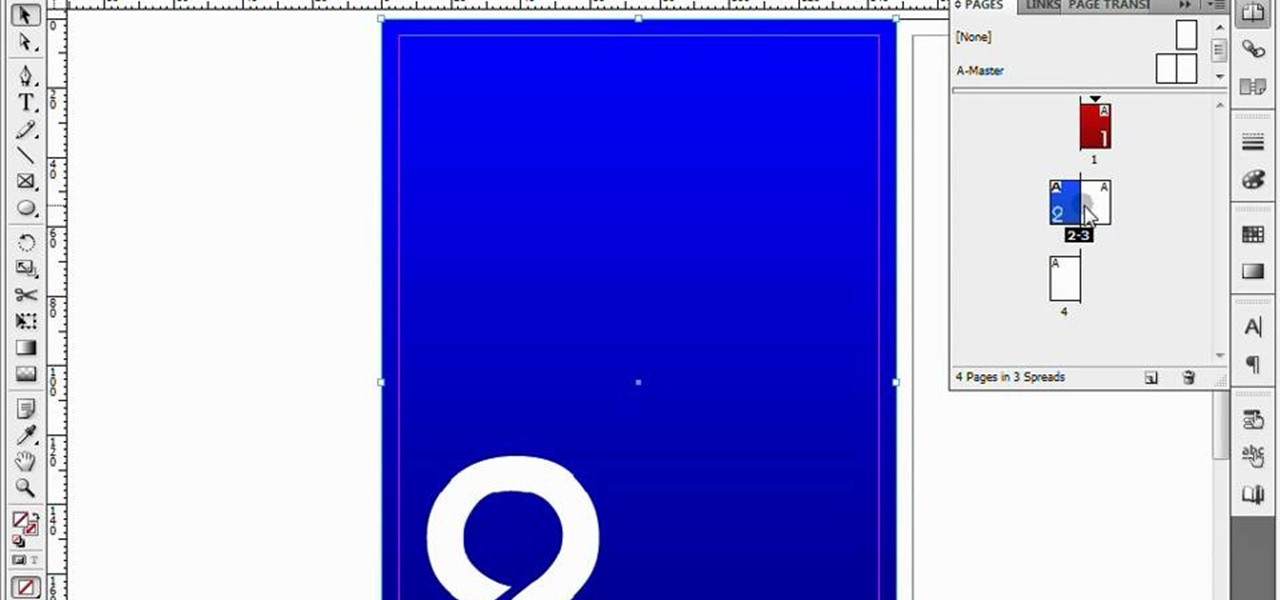
This tutorial will explain how to make buttons and links to flip between pages in InDesign files. Create sleek looking, easy to use documents that can be used as websites or PDFs. This video will show you how to use InDesign to its full potential.

In this tutorial, we learn how to bypass a blocked site on a school computer. You will need a proxy to do this safely. First, go to a proxy site like Proxify. Going through here will prevent the school blocking system from coming up and ruining your fun. If you are blocked, you can use a text file document and run CMD on your computer. This would be the more technological way to do it. Try doing the website first to see if it works, if not, then you can try to change the firewall on the compu...

In this video we learn how to alter your IP address. To do this, you will need to go to this website: http://shadysurfing.t35.com. After you go here, you will be directed to the site, click on the left hand side toolbar to display your IP address. Then, go to the web based proxy and search for the site you want to visit. From here, the site will pop up under a different IP address. You can use there at school or at work, whenever you don't want the information for where your IP address has be...

In this tutorial, we learn how to use Eraser to permanently erase data. First, open up Internet Explorer and search for "eraser". Once you do this, click on the first link that you see. Then, go to the download section of the website and download the first version that you see, it will be the newer version. Choose the bit processor that you have, then wait for it to download on your computer. Now install it and go to your Start menu to find the application. After this, open up the Eraser, the...

You can download the wallpapers, ringtones etc. for the Samsung Tocco Lite. First go the website Zedge. Then click on "no phone selected" to select your phone. Now you are ready to download anything you want for your mobile. For example, to download the wallpapers, select the wallpaper in search option which is located at the top left corner of the page and type anything you want in search box and click search. Now click any wallpaper you want to download and click pc download and then click ...

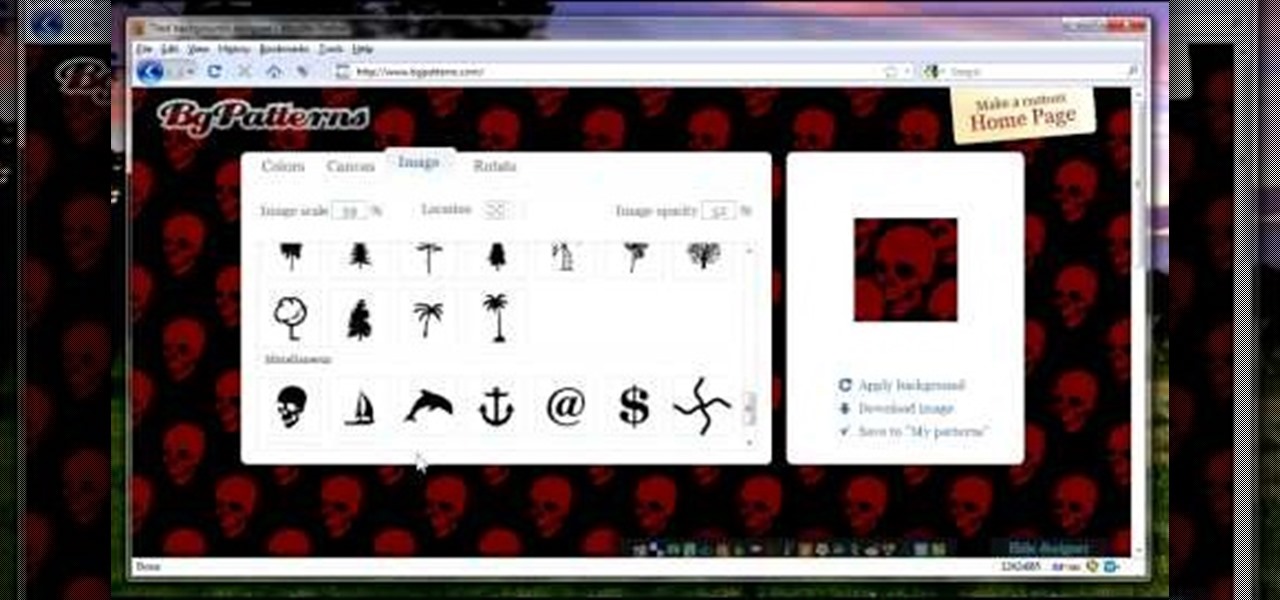
In this video, we learn how to create background patterns for web pages. First, go to the website BGPatterns. After this, the page will load and you will be able to create a custom home page. There will be a default pattern displayed on the page, but you can change this pattern and the colors as well. You can do a number of different things to make this page completely customized to how you want it to look. When you are finished, you can apply the background to your web page, save it, or down...

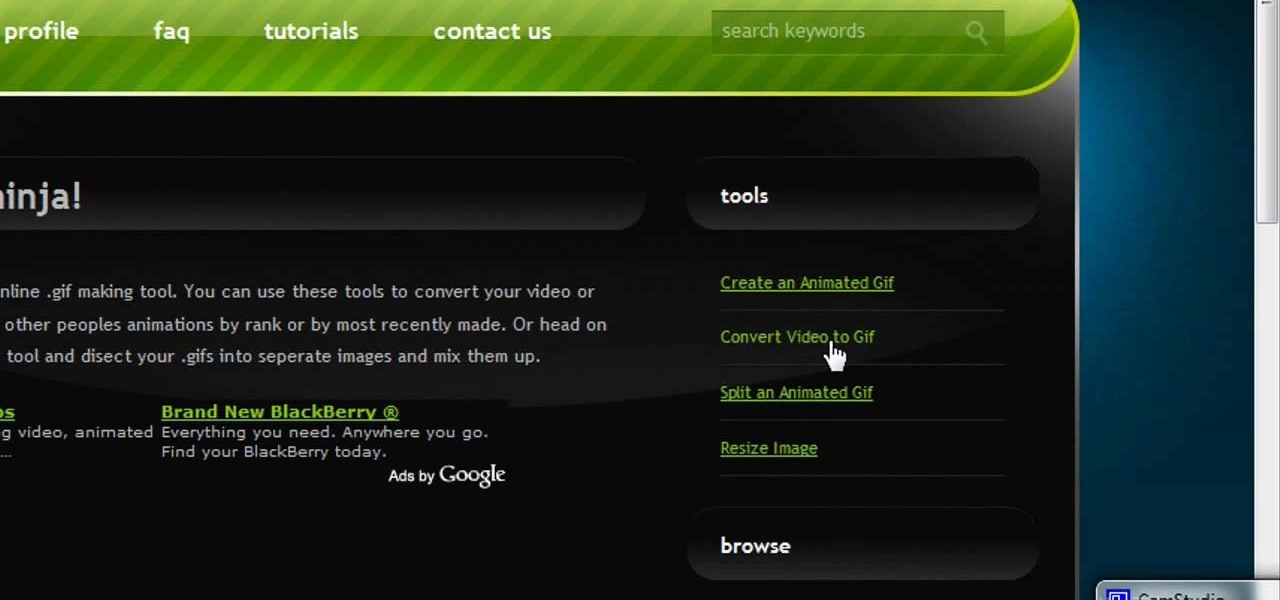
In this video, we learn how to make video clips into animated gifts. First, open Windows Movie maker and import a video file. Now, shorten the video to four seconds or less and save it. Now, go to the website gif ninja. Once on this site, you will see a section that says "tools", then click the button to convert your image to GIF. Once on this, you can browse and upload the file that you just created. Next, click "make my gif!" and a status bar will load on the bottom. When this is done loadi...

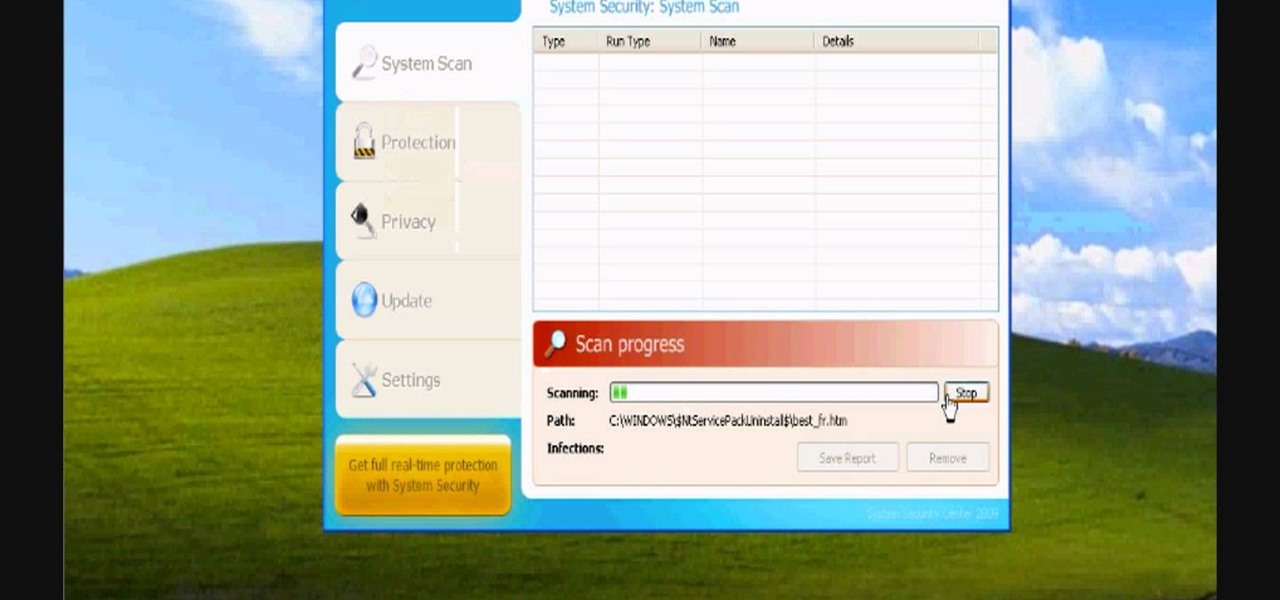
In this video, we learn how to avoid getting infected by "system security". Make sure you avoid the website that show the System Security Anti-Virus. Once you install this onto your computer it will pretend like it is doing a scan, but in reality is hurting your computer. It will pop up showing you that you have problems on your computer, but the alert will never go away. If you delete this, it will just re-install on your computer instead. To do this the correct way, you need to go to your m...

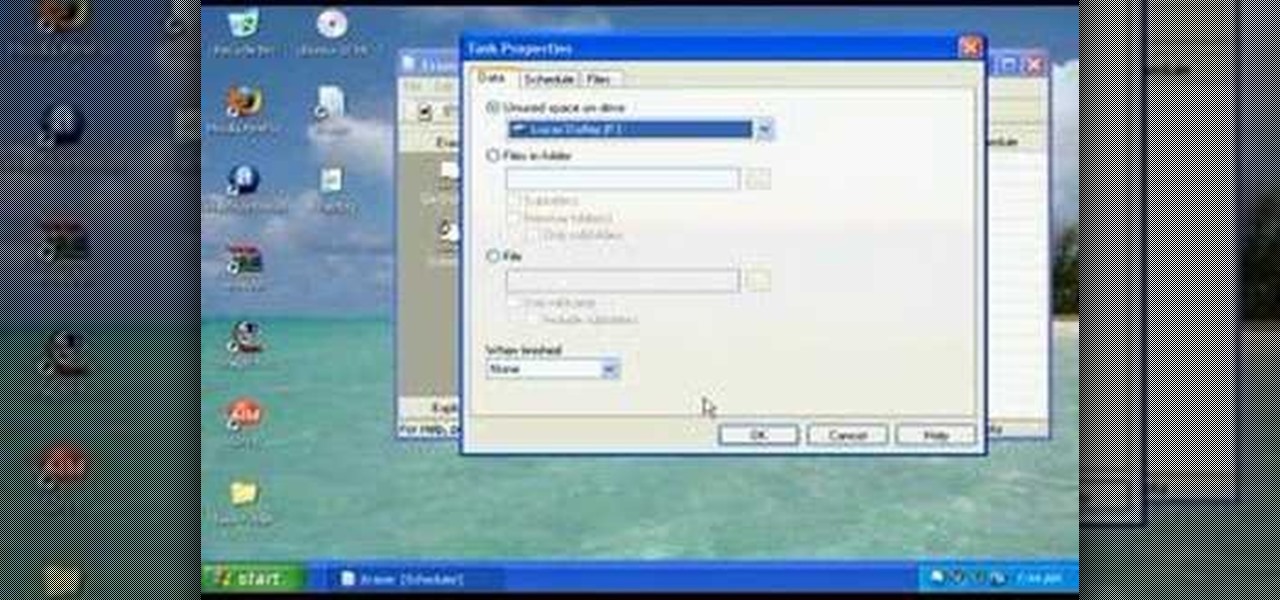
Just because you update to the Windows 7 operating system doesn't mean you have to lose all of your older programs and applications. Windows 7 has a virtual PC option that you can download, which allows you to use older programs and apps via Windows XP Mode.

In this video tutorial, viewers learn how to get high definition wallpapers using Google. Begin by opening your web browser and go to the Google website. Then click on Images from the top menu and type in "HD wallpapers" in the search bar. Now click on Google Search. In order to get the best picture quality, be sure to select Large images from the Showing drop-down menu. Once you found an image of your liking, click on the image to have it full sized. Now right-click on the images and select ...

In this tutorial, we learn how to remove the ads from Spotify. First, you will need a proxy, which you can get from the website: Proxylist. Just simply click on a free proxy once you get to the site, then write down the proxy and port. Next, go to edit, then preferences. After this, change the auto-detect to https, then put the proxy next to the box that says "host". Next, type in the port next to where it says "port", then click on the "apply" button listed at the bottom of this window. Now ...

In this tutorial, we learn how to download and play free PSP games. First, go to the website ManyISO. After you go onto the site, you can search for the games that you want to play. Download the game, then have it download through the software that you choose. Once it's finished downloading, install it to your computer. After this, you will be able to open it up on your computer and burn it onto a disc that you can use on your game console. Download as many games as you'd like, then enjoy pla...

In this tutorial, we learn how to install fonts onto GIMP. First, go to the website DaFont, then click a font you like. Download the font and then right click on the zipped folder and extract all that is indie of it. Now go to control panel then fonts, then view installed font. Copy and paste the font you have extracted into it. After this, go into GIMP and try out your new font in the software. If you like it, you can use it whenever you would like to! If you don't, you can simply uninstall ...

In this video, we learn how to upload Wordpress files using Filezilla. Before you get started, you will need to know the host, username, and password for your domain name. After this, click the quick connect button to connect to your server. The left hand side will show the local files on your server. Look in the root directory of your server and right click, then choose "create directory". Now, click on the plus sign to see a blog sub directory. Next, find where you downloaded Wordpress onto...

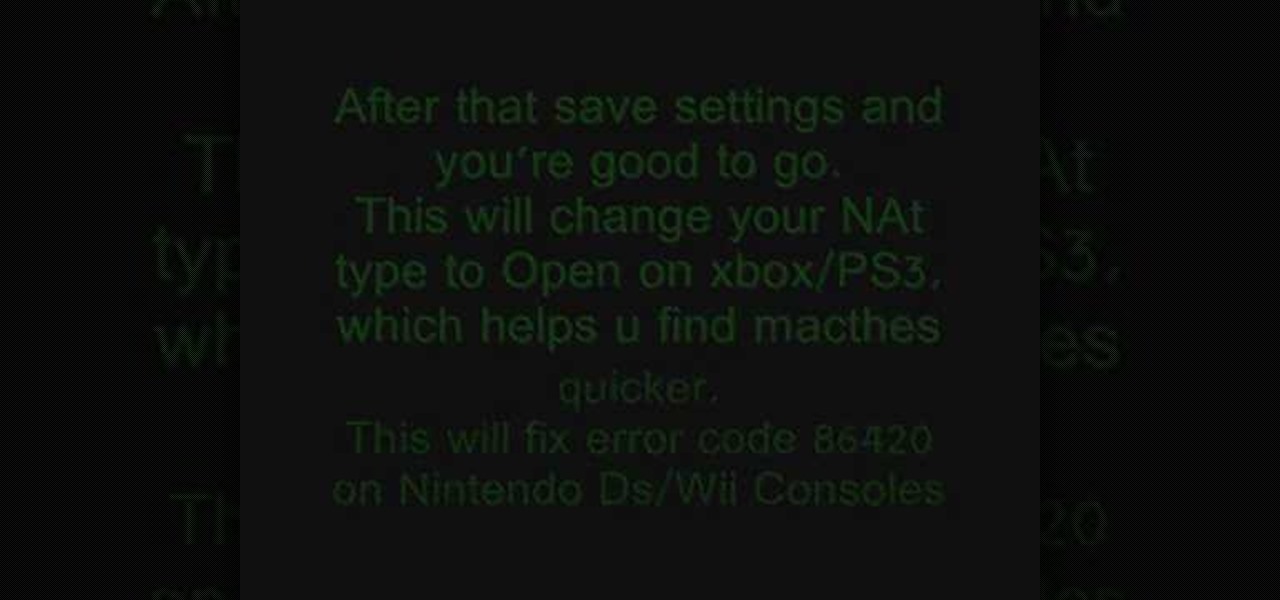
In this tutorial, we learn how to fix error code 86420 and change your NAT type to open. First, go to the website to change the settings for your Linksys router. Next, go to the applications tab that says "applications and gaming". After this, go to port range forwarding, then write in a name next to where it says "application name". Under "start" write the number 1 and under "end" write 6553, then keep "both" marked under protocol. Next, enter in the last 3 digits of your console's IP addres...

In this video tutorial, viewers learn how to clear their cookies in Mozilla Firefox. Begin by opening the web browser. Then click on Tools from the top menu and select Options. In the Options window, click on the Content tab and deselect "Block pop-up windows". Click OK. Now click on Tools and go to Options once again. Click on the Privacy tab and click on Clear Now under Private Data. Make sure that Cookies and Cache are checked and click OK when finished. This video will benefit those viewe...

There's always a faster and more efficient way of doing things when it comes to Facebook. And if you have a Facebook Fan Page (Like Page) for your website, it's easily done right from your mobile device. Learn this super quick tip to post updates, videos, and pictures right to your Fan Page via your mobile device. Super easy you can do it in seconds.

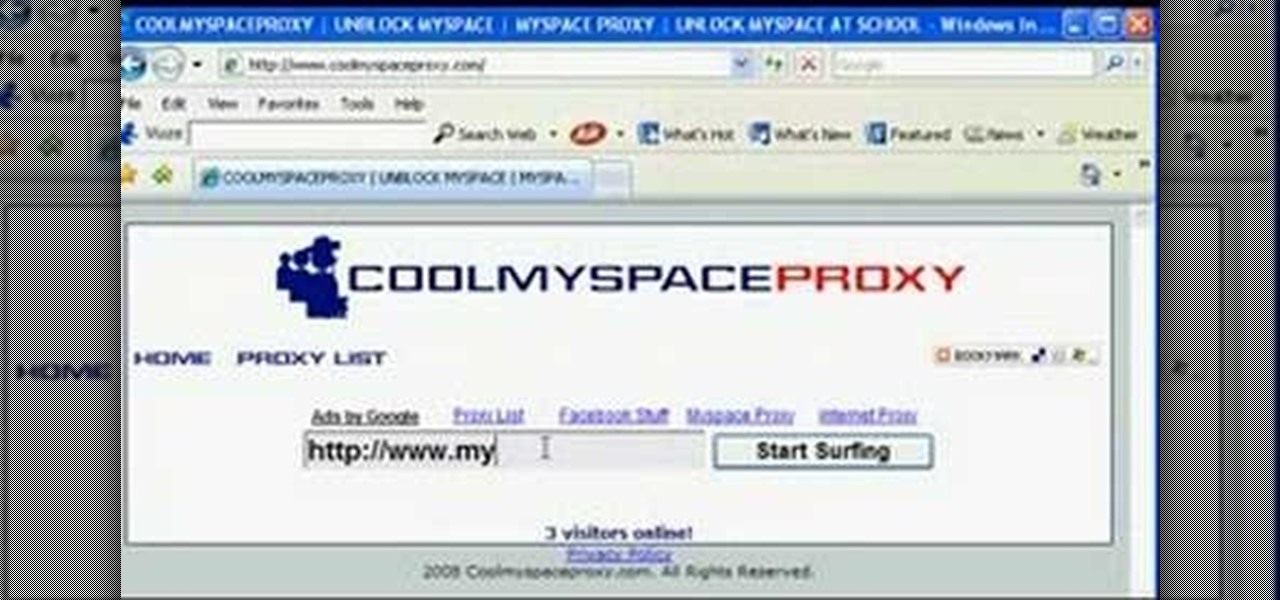
In this Computers & Programming video tutorial you will learn how to unblock MySpace (or any other site) at school or work or anywhere else. This is really very easy and simple to do and takes practically no time. It is like going directly to the original site. For this, you first go to the site Cool MySpace. Once on this site, simply type in the address of the website you want to go to in the surf box. For example, http://www.myspace.com and then click on 'start surfing'. That's it! You are ...

Facebook is an internet phenomenon which is quickly gaining popularity. For those who do not yet have a Facebook, this video will show you the basics of how to meet people and to connect with people online as well as how to set up your profile on the site. After creating an account using your email address and setting up your password, log on to the website. Set up your profile by clicking on the tab labeled "info" and entering information which you would like to share about yourself. You can...