This video demonstrates how to make a holiday punch needle ornament. First choose an ornament design and fit cross stitch fabric to a small embroidery hoop. There are designs on the CyberSeams website that can be traced onto the fabric. Put the fabric with the traced design into the embroidery hoop, thread the needle, dial it to "2", and begin punching the needle through the fabric to make the design. You can choose embellishments that can be sewed or glued on. When the design is finished, re...

Learn how to get a great rockabilly hairstyle. •First of all, curl up the hair using the le Angelique curls which are available in Pretty Choice and the link for which is available in the side bar. • And then use another curling iron which is also available in the same website and the information is also available in the side bar. •And then pin up the hair in such a way that it is closest to the forehead by finger styling just for the way it has to look. •And then she uses some bumble and bum...

Looking to fix your iPhone home button? Do you have a broken HOME button on your iPhone? In this video, learn how to get around it with an application called "mquickdo", formerly known as iHome for jailbroken iPhones. This also works for iPhone 1G or 2G and iPod 1G or 2G. Mquickdo allows you to use a series of finger swipes to function as the home button. This includes putting your iPod to sleep, going back to the home page, the double tap music menu, exiting an application, and more.
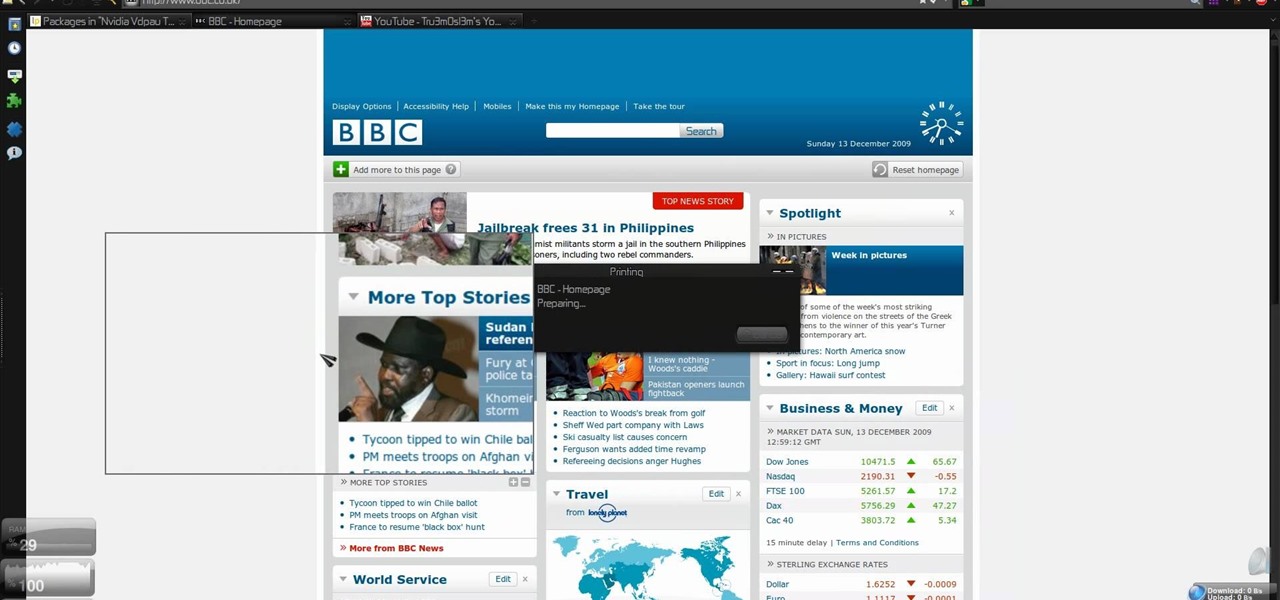
There's plenty of reasons why one would want to convert a webpage to a PDF document. And there's numerous ways on how one can convert that web page (HTML) into a PDF file. Check out this video tutorial on how to convert webpage HTML to PDF on Ubuntu Linux.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episodes from this Revision3 show.

Not all websites are created equal, and that's why Safari doesn't apply Dark Mode to each webpage you visit during your iPhone's system-wide dark appearance. But in Safari's latest update, Apple gives its web browser more power to automatically apply Dark Mode to specific website content without having to use extensions like Noir.

Did you know that you could learn all the fundamentals of web development for less than $35? Set yourself up for your new coding career in 2021 with The Ultimate 2021 Web Developer & Designer Super Bundle, which is on sale for just $34.99 right now — a huge 98% off the regular price of $1,886.

Dreaming up the next big business is easy. Running day-to-day administrative tasks is not. The tedious nature of entrepreneurship is the barrier that holds many people back from realizing their full potential.

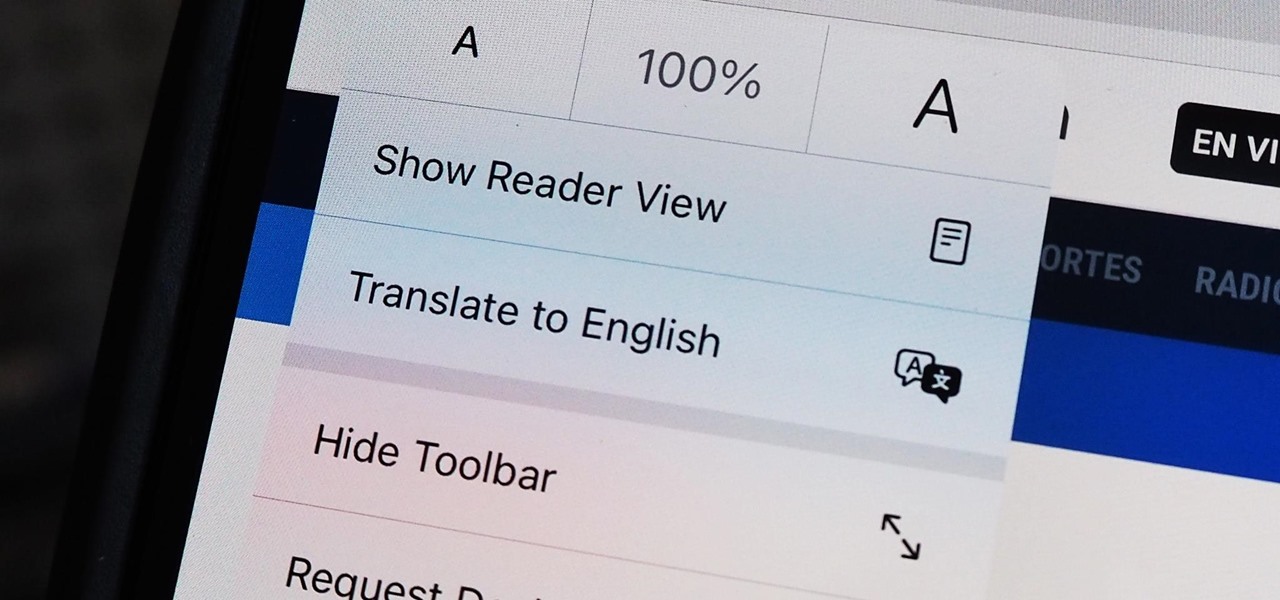
Since iOS 8, it's been possible to use third-party tools such as Bing Translator and Microsoft Translator to translate foreign language webpages in Safari into your primary language. Now, in iOS 14, there's a better way to do it.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

It's open season on Zoom, the video conferencing platform that has grown in popularity during the COVID-19 pandemic but has come under fire due to privacy issues.

Getting files from an Android device to a Mac or iOS device is not always easy or convenient, and the same goes for transferring content from a Mac or iOS device to an Android device. But we're here to tell you there is a better way than using USB cables, email, and cloud storage, and it gives you the look and feel of AirDrop.

Apple just released iOS 13.5 for public beta testers today, Monday, May 18. The GM (golden master) for iOS 13.5 arrives just three hours after Apple released it to iPhone developers, and 12 days after the release of iOS 13.5 dev beta 4.

Apple just released iOS 13.5 for iPhone developers today, Monday, May 18. This GM (golden master) update comes 12 days after the release of iOS 13.5 dev beta 4, which introduced updated COVID-19 exposure notification logging settings and the ability to share your Medical ID with first responders when placing an emergency call.

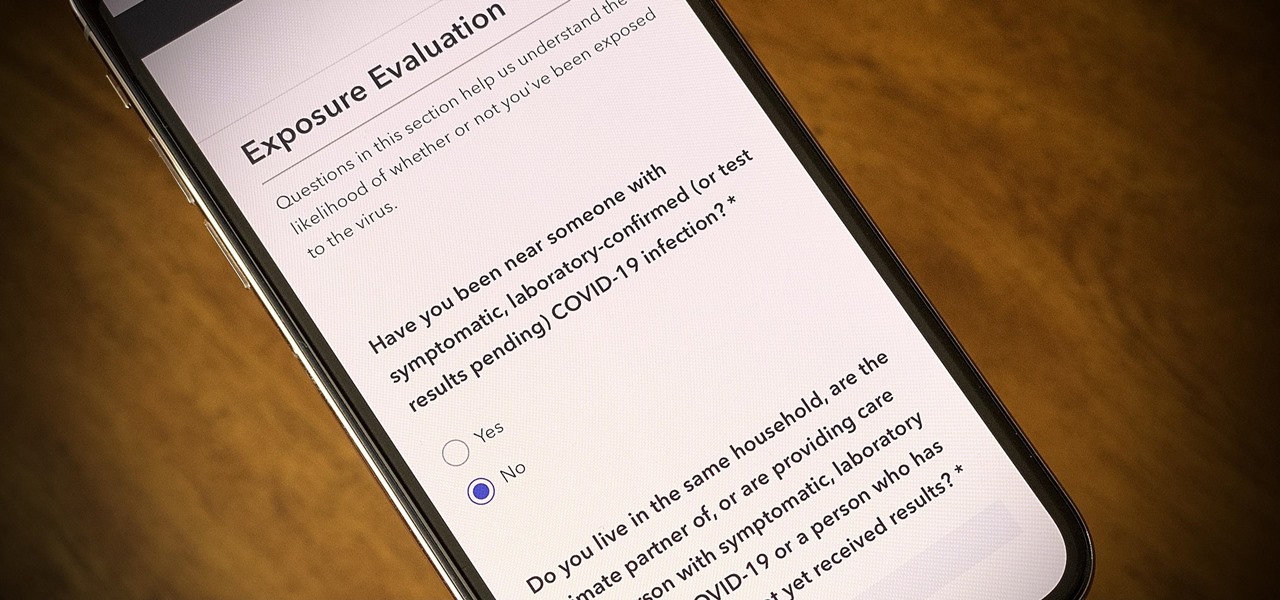
One of the scariest things about the COVID-19 virus is that you can show no symptoms but still be infected (and contagious). Naturally, we all want to know whether we're carrying the new coronavirus, but if you're showing signs of COVID-19, how can you be tested to know for sure? Websites are popping up to help with that, screening for symptoms, and directing you to a testing site if needed.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

The Unity 3D engine is not only responsible for facilitating the creation of 60% of AR and VR content but it also plays a significant role in producing the immersive stories that increasingly push the boundaries of cinema.

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

The 15-year-old star of the 1980s-inspired hit series Stranger Things, Millie Bobby Brown, may have (spoiler alert) lost all her powers as the character "Eleven," but in the real world, she still has augmented reality in her arsenal.

Apple revealed its newest line of iPhone models on Tuesday, Sept. 10, at its "by innovation only" event in Cupertino. While the release date for iOS 13 wasn't announced at the event, Apple issued a press release with the date. If you missed the event, you can still watch it from your computer, smartphone, Apple TV, and any other device that YouTube works on.

One of the first steps in attacking a web application is enumerating hidden directories and files. Doing so can often yield valuable information that makes it easier to execute a precise attack, leaving less room for errors and wasted time. There are many tools available to do this, but not all of them are created equally. Gobuster, a directory scanner written in Go, is definitely worth exploring.

As promised with its teaser from Build 2019, Microsoft has unveiled the details for its augmented reality version of Minecraft for smartphones.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

Some websites block image downloads on their webpages so you can't save them for reuse. That means long-pressing or force-pressing on protected images in Safari on your iPhone will not do anything or will omit the "Save Image" option. Taking a screenshot is the obvious solution to bypass restrictions, but you won't get the best quality. Thankfully, there's another way.

Browsing the web can be dangerous. With all of the various threats out there, it isn't enough to just avoid bad links and visit only HTTPS websites. You need to take advantage of the tools available to you so you don't end up the victim of some scam. Fortunately, Opera is making this a bit easier.

The last time we heard from Meta, the makers of the Meta 2 augmented reality headset, things looked pretty bleak. Now, as several new facts have come to light, we have confirmation regarding the beleaguered company's fate: Meta is done.

One the leading game developers for the PlayStation 4 and Oculus Rift platforms, Insomniac Games, is finally releasing its first major augmented reality title: Seedling for the Magic Leap One.

When OnePlus announced their partnership with T-Mobile and the deal the magenta carrier is set to offer, mouths dropped. But as usual, this deal comes with some caveats. The bulk of these will hurt the folks who love to root, something a large portion of the OnePlus community enjoys doing.

A major obstacle to the mainstream acceptance of smartglasses is the current inability able to smoosh processors, sensors, and batteries into a pair of frames that look cool. Wearables maker Thalmic is hinting that it may have figured it all out.

Two companies armed with web-based augmented reality tools, Vertebrae and Shopify, are ready to help online retailers boost their sales.

If you didn't get the memo, passwords aren't enough protection for your online accounts. Even a long and complex password offers only one line of defense which can falter. Two-factor authentication adds an additional layer, bolsters your defense, and decreases the risk of your account becoming compromised.

Apple's dedication to iPhone security is one of the company's biggest selling points. It's no surprise then that iOS 12 offers users a simple yet powerful way to make, save, and auto-fill strong passwords to your iCloud Keychain when creating accounts in both Safari and in apps. The best part? You hardly need to do a thing.

Yesterday, I talked about what I think is the most immediately mainstream-friendly app on the Magic Leap One is (Screens), and now we'll touch upon the runner-up: Helio.

With summer in full swing, these Snapchat lenses are as hot as ever. With people celebrating the 2018 World Cup in Russia, Snapchat contests that earn could earn you a free ride to Comic Con, and the everyday innovation that comes out of Lens Studio, there's something for everyone here this week.

Just a year after facing trade secret theft allegations from his former employer, ex-Meta Company employee Kevin Zhong and his new company are ready to ship the product that triggered the lawsuit.

With the exception of "Reflection" on the iPhone X, Apple hasn't updated their catalog of ringtones and alarms since iOS 7 dropped back in 2013. Since then, the company has come a long way with the quality of the iPhone's speakers, but their tones haven't adapted to meet those changes. That's left an opening for others to create their own ringtones mastered for the iPhone.

The pending union between Prince Harry and American actress Meghan Markle is almost guaranteed to set the internet ablaze as millions tune in to experience the spectacle and pageantry of such a momentous event. If you've cut the cord and are wondering where you can stream the royal wedding for free, we've got you covered.

Even if your default mobile browser is Google Chrome, you may not want Google to also be your search engine. Maybe you're not impressed with Google's search results all the time, maybe you want a more private search experience, or maybe you just don't want Google's hands over everything in your life. Whatever the case, it's easy to switch from Google to another default search engine.