If print is a dying media, you might as well destroy books in the most beautiful way possible. Guy Laramée is a Montreal-based interdisciplinary artist who turns old books, such as the Encyclopedia Brittanica, into intricately-carved works of art using mostly a sand blaster and some paint.
No matter which smartphone you buy, it will come with an internet browser preinstalled. Depending on your OEM, the default browser might be called Samsung Internet, HTC Internet, Silk Browser by Amazon, ASUS Browser, or Google Chrome—there's just so many stock browsers available.

When the "Just another day in the office at Magic Leap" video was released last year, it was called a mind-blowing, stunning, and breathtaking take on mixed reality gaming. It was a great presentation of what the technology could be, but not for a second did I think it was anything other than a concept video, and I'm not the only one who thought that. This was a goal to reach for mixed reality, not the reality.

Oh no... your precious iPhone is in shambles. Maybe you shattered your screen after a crazy night of celebrating, or maybe your two-year-old jabbed a toy into your iPhone's charging port, completely destroying it in the process. Now what? Do you take it to a repair shop, or go to an Apple Store to have it fixed? This brief article will help you weigh your options.

Don't let the lack of owning a HoloLens stop you from joining in on the fun of creating software in this exciting new space. The HoloLens Emulator offers a solution for everyone that wants to explore Windows Holographic development.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

If you're an Android fan, you're probably familiar with Qualcomm's Quick Charge technology or, at the very least, what it can do. Quick Charge 3.0, the third generation of Qualcomm's fast-charging technology, is built into most Snapdragon SoCs and it's what lets you charge your phone's battery up to 70% power in just 30 minutes. What's not to like?

If you've ever wondered why the pictures and videos you share with Snapchat on your Android device seem to look grainy with low resolution, you're not alone. We all know it, and we've come to accept it as a plain fact: Snapchat image quality sucks on Android.

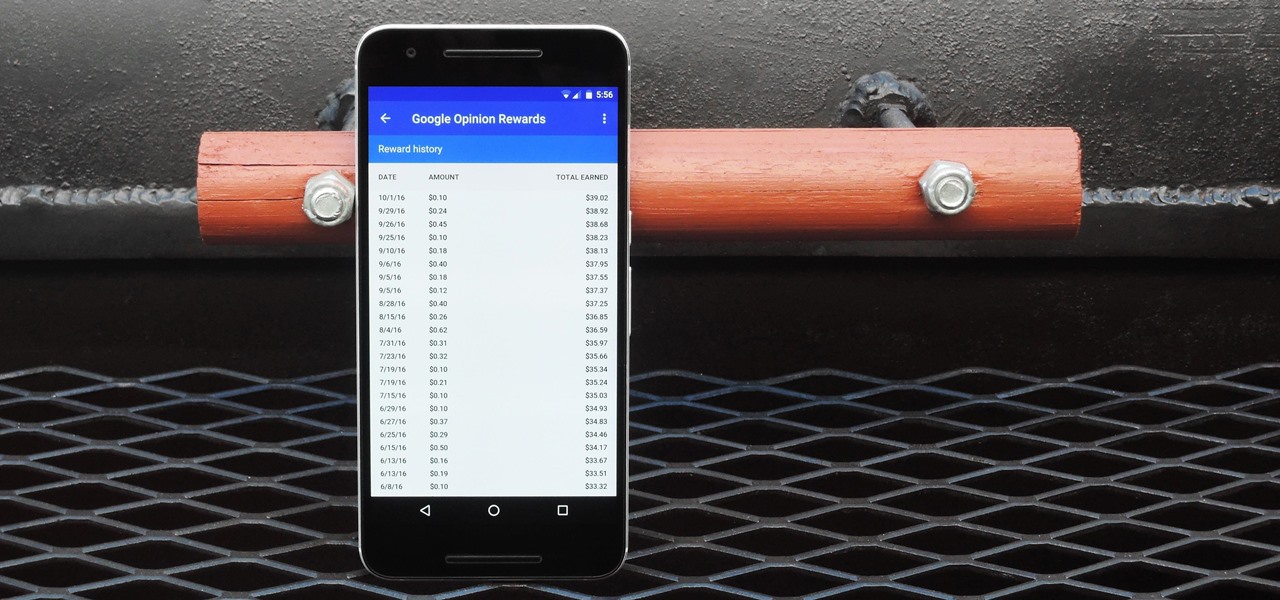
In case you didn't know, Google has an awesome app that gives you free money to spend on apps, games, movies, books, and virtually anything you can buy on the Google Play Store. The app is called Google Opinion Rewards, and all it asks in exchange for the Play Store credit is that you answer a few questions every now and then.

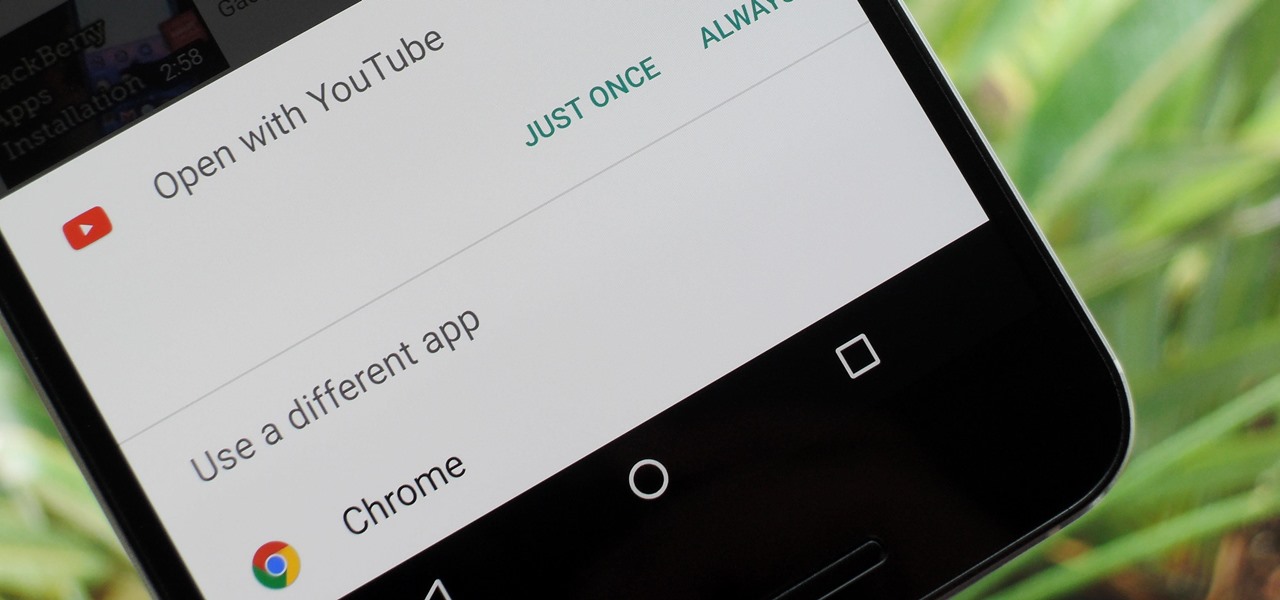
One of Android's biggest strengths relative to iOS is the fact that you can use any app to open compatible links, not just the stock ones that come preloaded on your device. When you tap a link that two or more of your apps are capable of opening, you'll see a message asking which app to launch it with—and from there, the choices are "Just Once" or "Always."

Traditional root ad-blockers like AdAway and AdBlock Plus have no effect on YouTube anymore. Until now, if you wanted to get rid of the commercials that play before your favorite videos, there have only been two ways—either by paying for a YouTube Red subscription, or by using an Xposed module to modify the YouTube app itself and force it into not showing ads.

Google just released Android 7.0 Nougat, and as usual, they're doing a staged rollout. This means that most users won't actually get the update on their Nexus devices for a few weeks—that is, unless they take matters into their own hands.

These days, the user experience on stock Android is a lot more refined and polished than manufacturer skins like Samsung's TouchWiz or HTC's Sense. This is mostly due to Material Design, the look and feel that Google implemented back in Android Lollipop, which has finally started to give Android a unified appearance with its sleek icons and abundant use of colors.

The new USB Type-C standard was supposed to revolutionize smartphone charging, but so far, it's done more harm than good. Many cable and charger manufacturers are struggling to keep their products in line with the proper USB-C specifications, so as a result, we now have to check to see if a cable is compliant before purchasing one.

We've heard of putting French fries on a slice of cheese pizza; after all, two fast-food favorites together are almost always better than one by itself. But French fries used as the crust of a pizza in lieu of traditional dough? That's an entirely different ball game. Don't Miss: 9 Pizza Hacks You Need to Try Before You Die

Sometimes the idea of cooking fish, especially for a group of guests, can be intimidating. There's the fear of the fish not cooking right, or sticking to the pan or grill. And even if you cook it right and the fish doesn't stick, you're left with the inevitable fishy-smelling cleanup. Not fun!

The newest version of Apple's mobile operating system, iOS 10, has been out for about a month now. But like every year beforehand, some of you who updated will not be happy with the latest and "greatest" iOS version.

Collecting Pokémon in Pokémon GO is only half the fun. Once you've reached Level 5, it's time to get your Pokémon ready to do battle with other Pokémon. This is where Gyms come in.

Pokémon GO, the biggest augmented reality sensation ever, broke app store records this opening weekend. But it also did something even more important: it gamified physical activity.

Not content with bringing the first untethered mixed reality headset to market, Microsoft wants to expand their Windows Holographic operating system beyond HoloLens into vastly more robust technologies.

Cool, refreshing fruit, ice-cold margaritas (or beergaritas), and popsicles... this combination of food and drink just screams summer. Turn up the chill jams on the stereo, fire up the grill, and throw on your shades—you're just one pool away from the best summer party ever.

Today's pollution, hectic lifestyle, inadequate sleep and no time for pampering can leave your skin lackluster resulting in drying skin and making dry skin drier ultimately causing the early appearance of wrinkles and aging. A good fruit facial helps relax your skin from deep inside and the proper messaging gives it a rosy glow by increasing blood circulation imparting your face with a luminous glow. These are even better because they are natural and chemical free unlike the artificial facial...

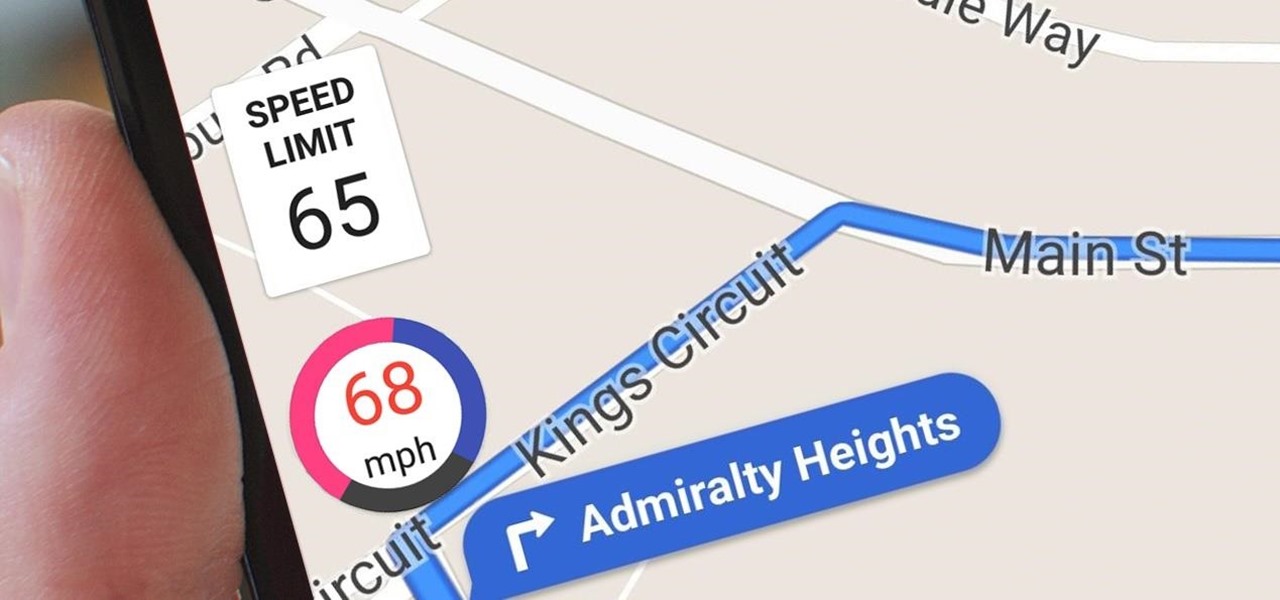
Google Maps does a lot of things well, but one feature it's always been lacking is an on-screen speedometer. Well, now you can add one with Velociraptor, and you can even set it to alert you when you're traveling above the speed limit.

A VPN service is almost an essential these days. Good ones can block ads, prevent tracking cookies, encrypt your internet traffic for better security, and even spoof your device's location to bypass geo-restrictions — all things you should be concerned about in the age of NSA snooping and Facebook data mining.

Many "quick and easy" donut recipes involve a donut pan and an oven, but those are basically just mini cakes shaped like donuts. Chances are, if you're in the mood for a donut, you aren't looking for a cake "donut" recipe—you want the real thing—a donut shop donut, fresh out of the fryer and topped with sugar or glazed to perfection.

Soon all Android users will be able to use Samsung's cool Soundcamp app to write and record music. The announcement was made at the Samsung Developer Conference 2016, stating that the app, which was released last year for Samsung devices only, will become available to all phones and tablets running Android 5.0 or higher very soon.

The thought of peeling tomatoes for pasta sauces and soups has long been an overwhelming idea for us, one we often steer clear from when reading recipes or searching out new dishes to create. Even the methods that are supposed to speed up the peeling process (like roasting, poaching, and freezing) are more work than not.

When it comes to proper tomato storage, conventional kitchen wisdom (and Alton Brown) state that tomatoes are best stored at room temperature—not in the refrigerator. Supposedly, refrigerated tomatoes develop a mealy texture and lose their flavor if they are exposed to cooler temperatures over time.

Welcome back, my tenderfoot hackers! As you should know from before, Snort is the most widely deployed intrusion detection system (IDS) in the world, and every hacker and IT security professional should be familiar with it. Hackers need to understand it for evasion, and IT security professionals to prevent intrusions. So a basic understanding of this ubiquitous IDS is crucial.

If you're gluten-free, on a diet, or just cutting the carbs like me, eating a sandwich can be a dangerous game. There are traditional alternatives such as lettuce or egg wraps, but they have their drawbacks: they can't hold as many ingredients, they can be lack flavor when raw and un-rendered, and it's hard to layer the toppings and condiments to create your perfect bite.

It's about that time again. Spring weather is here, a new season of Game of Thrones is upon us, and we're getting ready for the next version of Android.

Frozen meat is a saving grace for weeknight meals. Whenever I crave a certain protein, all I need to do is defrost it. Sometimes, I don't even need to defrost it in order to use it.

If you have a local Trader Joe's, you know first-hand how enchanting the frozen aisles are—almost every item offers the promise of a delicious meal or dessert. (We're always tempted to open the package and eat the cookie butter cheesecake, stat.)

Note: a bug was found in the Insertion Sort implementations. The bug was corrected in each language. Please refer to the pastebin links for the most up-to-date versions of the sample code. Any screenshots may be behind. More about the bug can be found here.

Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.

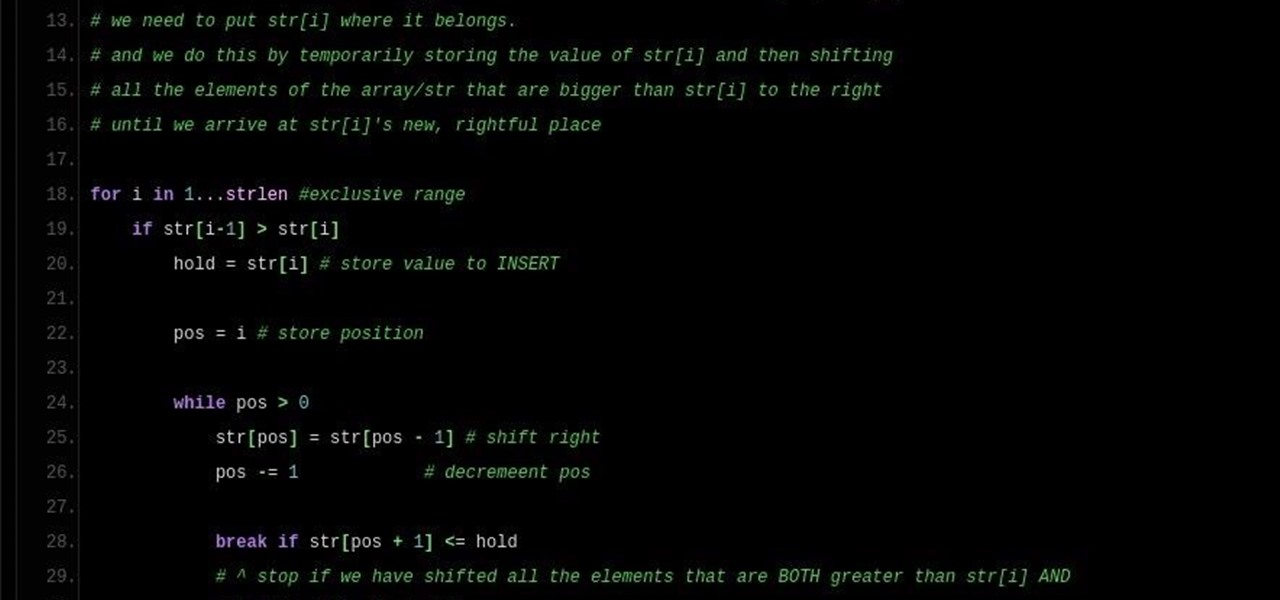
Welcome back, NB community, to my series on sorting. I introduced in my last article the concept of complexity. When I say complexity, I'm talking about time complexity.

Cable TV providers were dealt a pretty significant blow on Thursday, February 18th, 2016, when the Federal Communications Commission decided that customers should have a choice in what type of device they use to watch cable, instead of being forced to rent a set-top box.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

Many users across the web have reported issues with receiving notifications from the Gmail and Hangouts apps on Android. The problem is most prevalent with users running Marshmallow, and the gist is that notifications from these apps are extremely delayed or don't come through at all.

Earlier this week we showed you how to use multiple accounts on Instagram, and now Facebook is rolling out a similar feature for its Messenger app, as well as a few other features.