As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

From Farmville to selling a company to Google, Amitt Mahajan has been through the startup ringer. Now, as managing partner with Presence Capital, he's funding the future of augmented and mixed reality.

Tea has been around for thousands of years, and as a result, tons of customs and ceremonies have sprung up around its consumption. Some cultures take their tea plain, while others put things in it. Sometimes there are special tea-holding vessels, other times not. Maybe there will even be special foods meant to be eaten with tea. However, in America, our appreciation of tea has waned. For many, iced tea is their biggest source of tea consumption, and it's imbibed with no ceremony whatsoever in...

This video shows you how to easily divide proper fractions. In the first step, you have to calculate how many times does the denominator fit into the numerator. You need to divide the numerator by the denominator. If the denominator does not fit into the numerator, you have to write 0, followed with a point, at the top of the calculation ("0."). Next, you add a 0 next to the numerator (multiply it by 10). Now, you have to calculate how many times does the denominator fit into the numerator ag...

Are your knives starting to look a little dull? This how to video demonstrates the proper way to use a sharpening steel to sharpen all your knives. If 15 or 20 passes over the steel doesn't work, it means you need to get your knife ground. Steels don't wear out! Unless perhaps you work in a commercial kitchen.

Al shows you the proper way to get the most out of the "wing" section of a buffalo wing. This video is a must-see if you enjoy chicken wings!

At first, it seemed like a clever art installation housed on the web, but now we're not so sure... the Newstweek hack may indeed be legit.
(Series designed to help explore whether your ideal employment ideas should be formalized into a business venture or as an employee or volunteer value added problem solver).

In this video series, learn how to play the piano from expert piano player and professional musician Tony Newton. Tony will teach you basic piano lessons such as proper posture and correct hand positions for the piano. Developing nimble fingers is paramount for great piano playing. Our expert piano player will show you how to practice correct finger techniques to enhance your manual dexterity and facilitate muscle memory. However, this series is not solely for beginners. You can learn more ad...

The gold standard in any business is reaching the front page of Google. You need to get your brand in front of audiences. While it can seem daunting, it's not impossible when you master SEO best practices.

Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the organization being tested can fix any potential issues. In a professional penetration test, there are six phases you should know.

Twitter is a science. The smarter you post and engage with others, the better chance you have at building a bigger audience. Scheduling your tweets is one way to get there. Most engagement occurs at specific hours, but you may not be around then to post your tweet manually. While the official Twitter app on iOS and Android doesn't allow you to schedule, there is another way.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

OnePlus releases some unique and exciting features before they start catching on with everyone else. Their OxygenOS is often considered the cleanest and most useful variant of Android. However, there are still a few key features OnePlus has yet to bring to their devices. This includes a proper lift to wake option.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

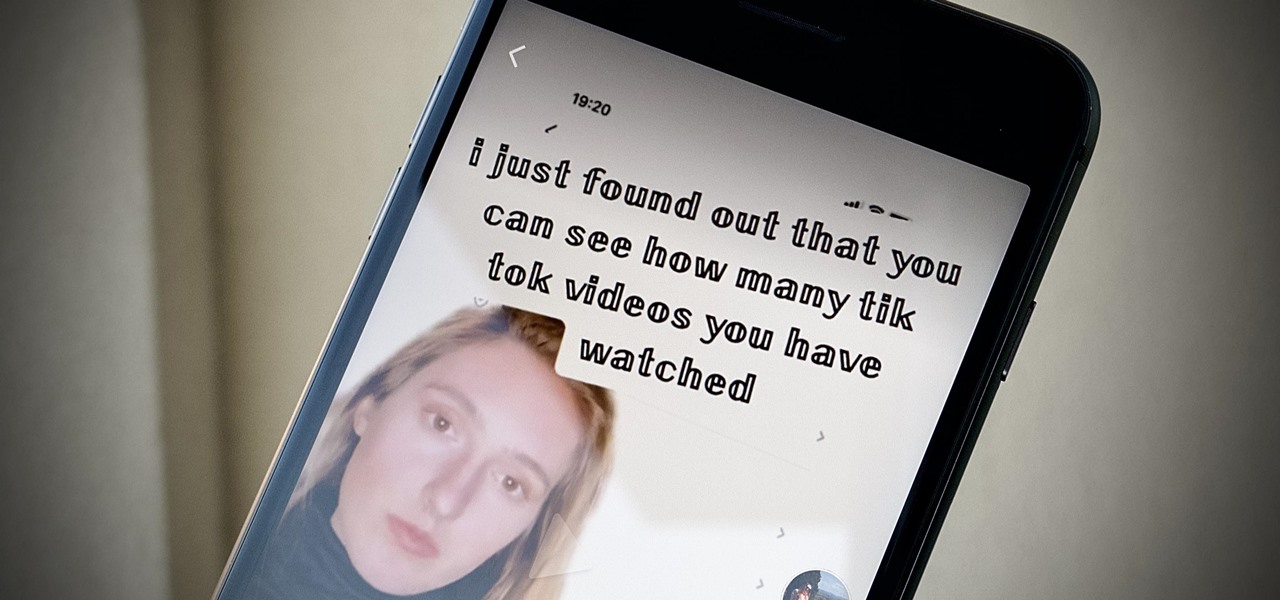
If you're as addicted to TikTok as much as I am, you probably heard about the app's alleged, hidden views counter, which can show you how many TikToks you've watched on your account. Most people who look at their counters are horrified to see that they've watched hundreds of millions of TikToks so far. Can that be right?

We've been predicting the rush of augmented reality wearable makers from China for a couple of years, and now it looks like it's in full swing, with one of the most promising entrants coming from startup Pacific Future.

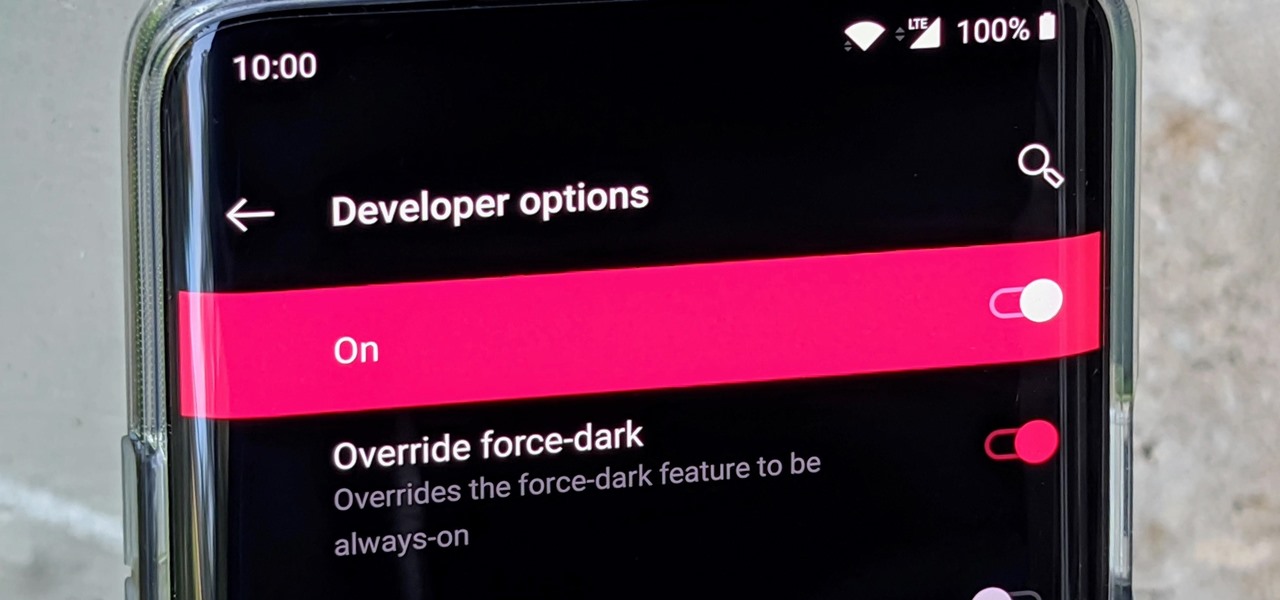
Google brought its official dark mode to Android 10 not long ago, but it might take a while for all apps to support the new feature. That doesn't mean you have to wait around for each app developer to add dark mode — just follow this guide to learn how you can force all apps in Android 10 to use dark mode.

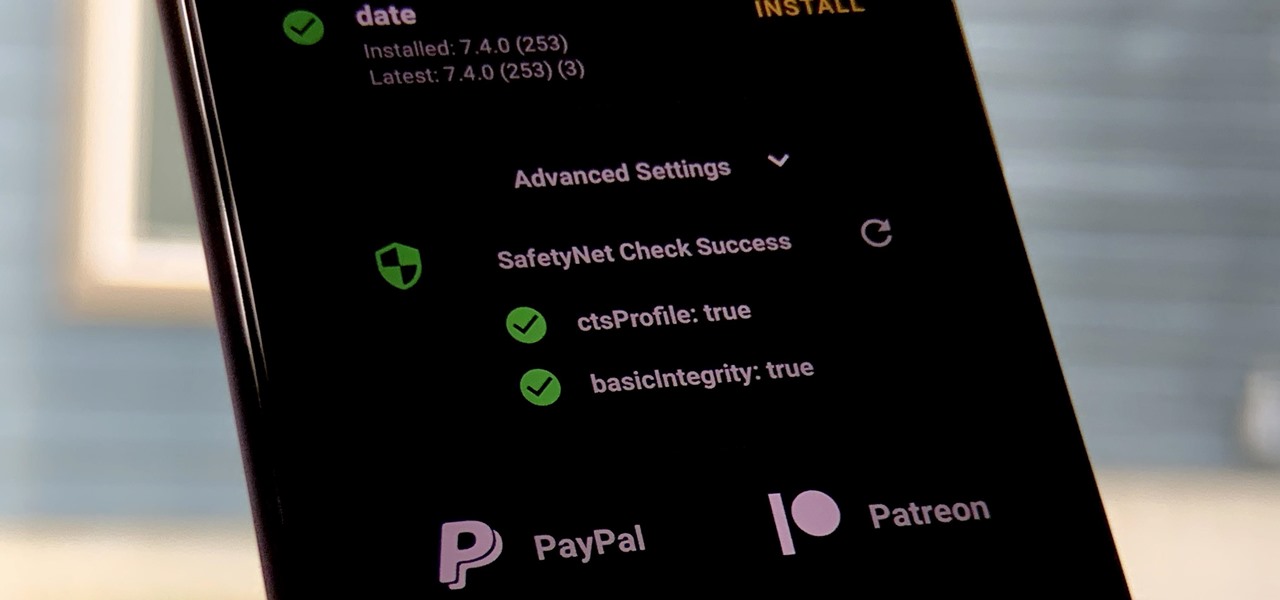
One of the longest-running cat and mouse games in Android has to be that of Google's SafetyNet feature and specific apps that can trip the flag. Many developers have resorted to using Magisk to create their modules since it can systemlessly pass SafetyNet in most cases. However, EdXposed is having some issues passing SafetyNet right now, which affects more than just your mods.

The latest official update for iPhone, iOS 13.2, introduced 22 new features and changes to the iOS 13 era, building off the improvements brought by iOS 13.1 and iOS 13 proper before it. It's time to take our first peek into what's next for iPhone and iOS, as Apple releases iOS 13.3 developer beta 1 today, Tuesday, Nov. 5.

GravityBox is a name that many know as the module to rule them all when it comes to customizing your Android device. Ask any of the longtime modding pros, and they'll tell you about the good old days during the Xposed era. The community was booming and full of great ideas, and there were never any shortages of fun modules to try. Thankfully, it still lives on even years later.

All those Apple commercials encouraging people to use their iPhones to make their smartphone movies look amazing, but how can you achieve some of the same looks? That's the question many often ask after plunking down over $1,000 for a brand new iPhone, shooting some video, and getting somewhat mediocre results.

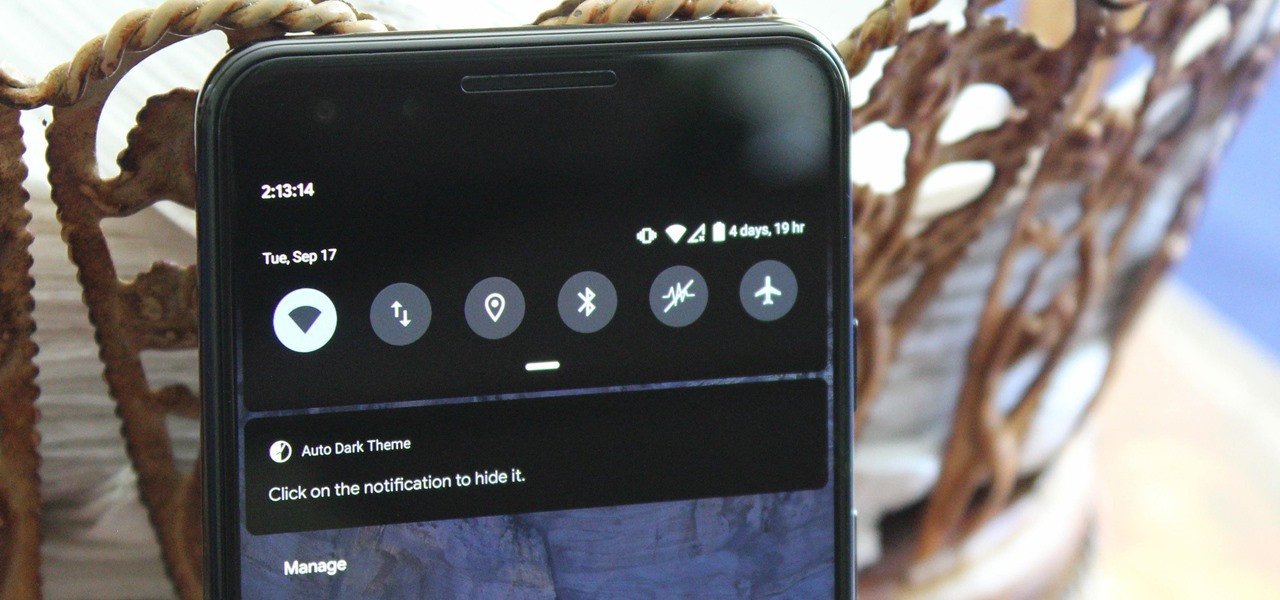
Android 10's new dark mode is a pleasure to behold for longtime users. Ever since OLED panels became widespread, we've been clamoring for the feature. But now that we have it, there's a new problem: it doesn't turn on automatically based on time of day. Thankfully, a simple app can turn dark mode into a true night mode.

Imagine a scenario where you're nowhere near your iPhone, but it's on loud, and you really need to silence it. An alarm may be blaring, notifications could be spitting out sounds left and right, and calls may be ringing. Things can get annoying real quick for whoever's around it. Plus, all that attention makes it easy for someone to find and possibly steal your iPhone. Luckily, you can quiet it down.

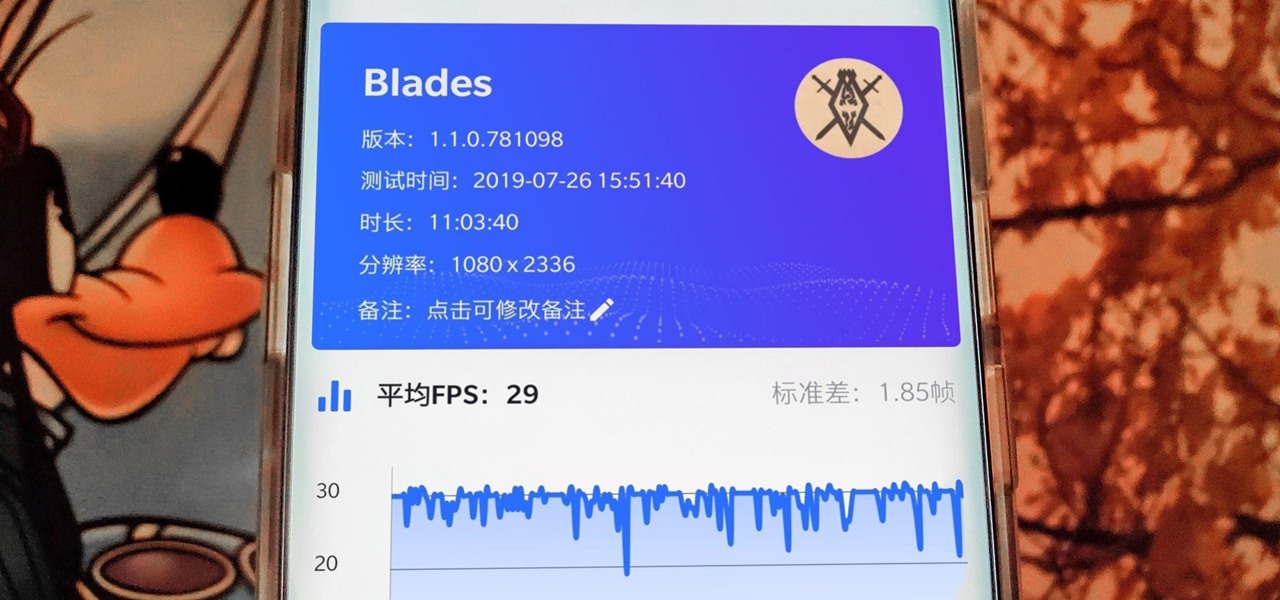
When you're gaming on your Android phone, does it sometimes feel "slow" and you can't figure out why? That means a drop in performance, which is when the frame rate dips, causing some noticeable stutters and lag. There's not really a way to know what's wrong unless you made the game yourself. But on the bright side, you can check any game's FPS with a simple tool.

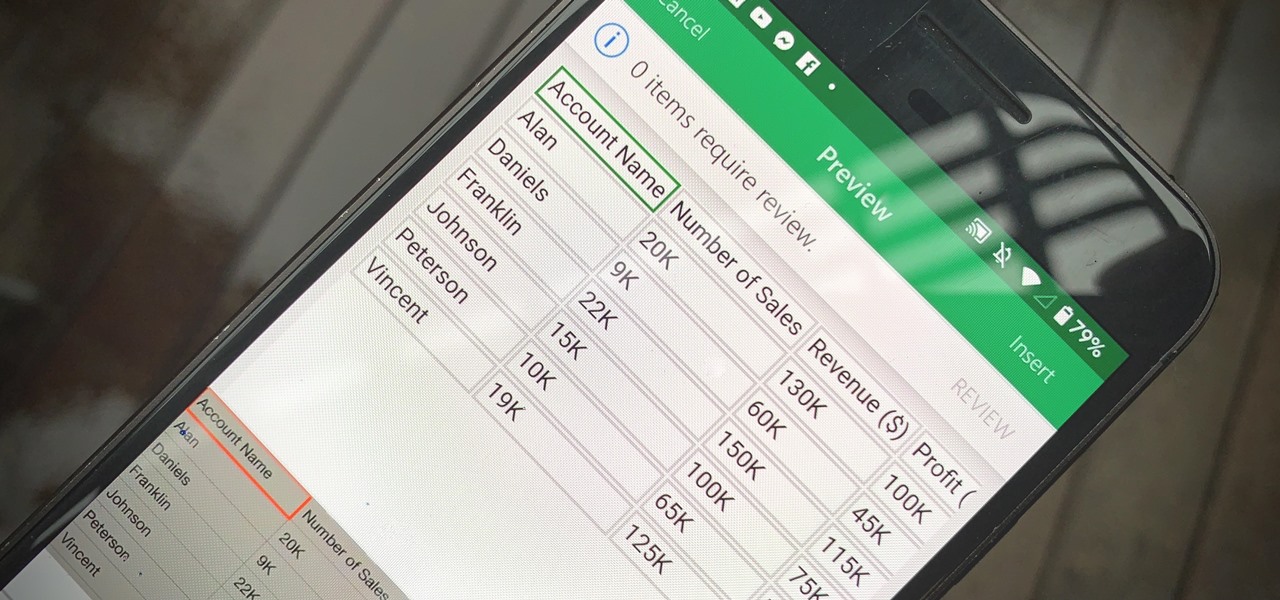
Creating a digital spreadsheet by hand can certainly be tedious, especially if you're copying a printed paper table word for word, number for number. Instead of typing information that's already there, however, use Microsoft Excel on Android or iOS to snap a photo of that printed chart and import it directly into your digital one.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

With the change to a glass back, many of us are concerned about the durability of OnePlus 6. While glass does offer some benefits such as lighter weight, without proper reinforcement, it can easily shatter in one drop. Now we have our our first look at its durability thanks to JerryRigEverything.

Whether due to spotty cellular reception or just data that you want to save, popular navigation apps like Google Maps and Waze offer an offline feature that lets you navigate from one location to another in the absence of internet service. Apple Maps also lets you use its service offline on your iPhone, though the feature is not as straightforward as it is on its competitors.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

Noted poet T.S. Elliot once wrote that "April is the cruelest month." But Magic Leap might argue that March is the most miserable, as the Ides of March brought more legal woes to augmented reality startup. Elsewhere, its closely-held branding secrets have been spilled by way of the US Patent and Trademark Office (USPTO).

In January, ZTE announced they would be conducting an Oreo beta program for Axon 7 users to test Android 8.0 before the masses. Since then, no additional information was released — until today, when ZTE finally opened up the Oreo beta to US customers.

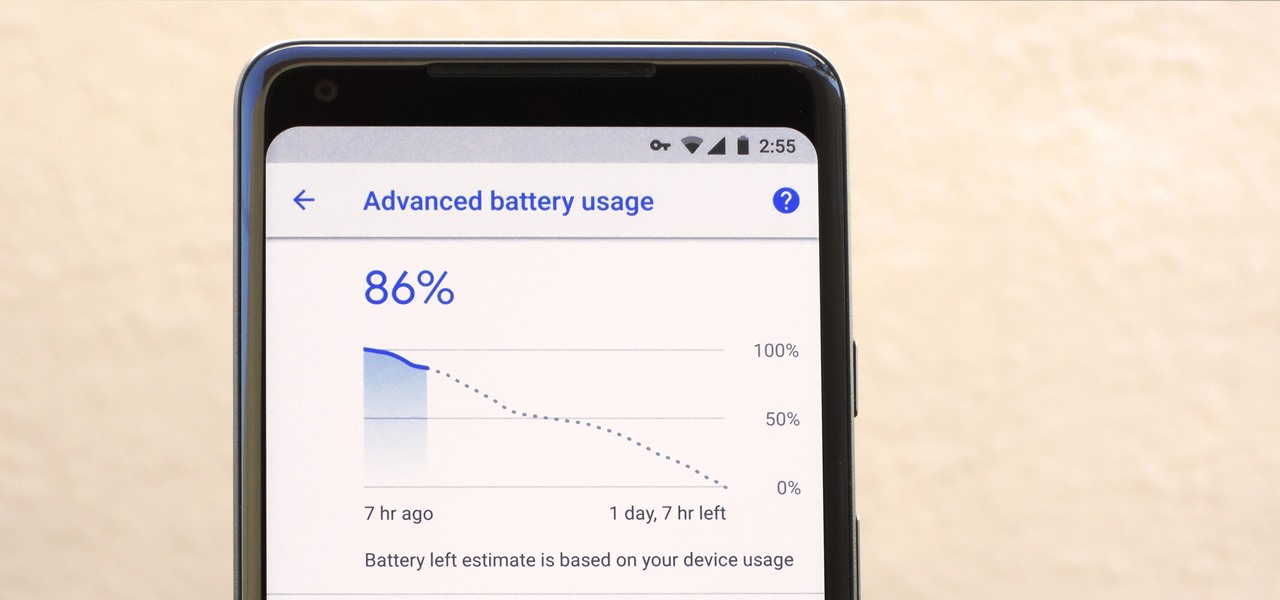
After Apple's recent fiasco, it's now common knowledge that smartphone batteries degrade over time. But aside from causing terrible battery life, a degraded battery can also trick your phone's software into thinking the device has more juice left than it actually does.

The app that started as simply a photo-sharing social media platform has expanded to encompass so much more than that. Between live videos, stories, chat, and animated stickers, Instagram is more than the sum of its pictures. Now, there's a new feature to add to that list for Android and iOS — video and audio calls.

Despite their sometimes fluffy reputations and occasionally ethically compromised viewpoints, tech evangelists are important, don't let anyone tell you otherwise. The right passionate voice behind the right technology platform or piece of hardware can sometimes spell the difference between fostering a community of potential users and watching a product die on the vine.

You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay secure, there are a few steps you can take.

It took a few months, but several major phones are finally receiving updates to Android Oreo. At this point, we've spent significant time talking about Oreo on the Galaxy S8, Galaxy Note 8, and Essential Phone. While an update to the latest OS is always great, there is one big Android 8.0 feature that isn't coming to every phone.