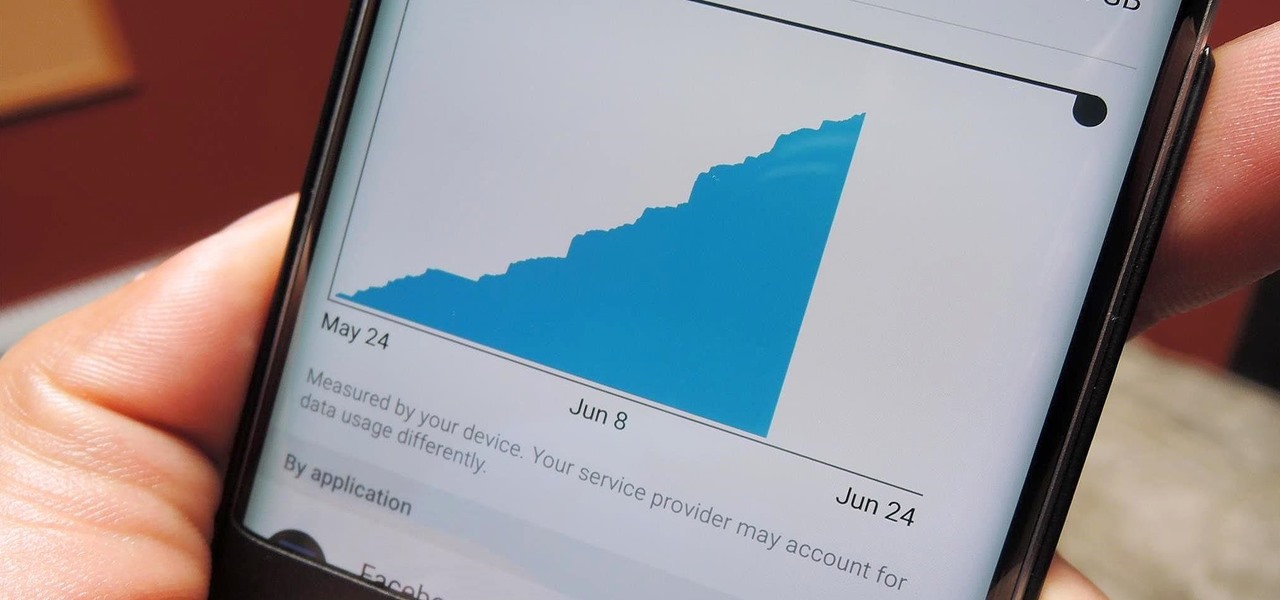
Cellular carriers like to nickel-and-dime us out of every bit of money they can feasibly justify, so as consumers, we owe it to ourselves to make sure that we're getting our money's worth.

Hello again, folks! I'm back with another (final) guide on runtime crypters which is an extension on my previous runtime crypter guide. If you have not read it yet, I highly recommend that you do since the fundamental theory of the PE format. Again, this will be a Windows-specific guide, so I'll repeat this: If you're a hater and cringe at the slightest sound of Microsoft's grotesque baby, feel free to close this tab, delete your history, exit your browser, pour some oil onto your machine and...

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

So you dropped your smartphone and the screen cracked. Again. Just the thought of sending it out for repair or buying a new phone is driving you mad.

Welcome back to another episode of Java Tutorials, In today's tutorial, we'll be learning about what methods are, proper syntax when writing Methods, and why they are beneficial in a program's code.

This article is to all the newbies on here wanting to become a hacker. Since I have seen many newbie questions on here, I need to address this.

Spaghetti squash is a versatile vegetable, but it has a reputation for being intimidating to prepare... not to mention time-consuming. Heating it up in the oven can take at least 30-40 minutes, which is a definite time-suck for those who want to get dinner on the table, stat.

When it comes to cooking grains, there is an unspoken rule to never stray from the exact measurements. Consulting charts for the proper ratio of liquid to grain is considered the difference between crunchy, undercooked pebbles and a mushy mess... that is, until now.

Personally, I think everyone should have the freedom to sit down and enjoy a delicious breakfast each morning... but that isn't always attainable, especially because of the prep work and cook time that tasty meals often require.

Hello, in this episode of In the Kitchen with Matt, we will continue with the Star Wars theme, last episode we made Star Wars Death Star Peanut Butter Cups, this episode we are making Star Wars Death Star Popsicles. So we are really getting great value out of our Death Star molds, because of the versatility they provide. These popsicles are super easy to make, if I can make them, you can make them! If you have any comments put them down below, and I will get back to you.

Whether your holidays are cause for celebration or exhaustion from over-celebrating, alcohol is more often than not involved in the merrymaking. We at Food Hacks are very fond of enjoying this particular indulgence in lots of different ways.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

Winter is already here, and when Jack Frost is nipping at your nose, he tends to nip on your wallet, too.

There are going to be tons of great Black Friday deals on electronics in stores like Best Buy, Target, Walmart, etc. But if you can't endure another holiday of standing in lines and running over people to get what you want, shopping on Amazon from the comfort of your own home is the way to go.

BlackBerry has yet to find a home amongst the iPhone and popular Android phones, with sales plummeting over the last couple years, but this might be a thing of the past thanks to their latest device, the BlackBerry Priv. It has decent numbers so far and was even sold out on Amazon shortly after its initial release.

It might be difficult to admit, but a lot of us are probably guilty of lurking on Instagram profiles, whether it be an ex you've been keeping tabs on or someone cute you literally just met.

A classic French omelet is supposed to be completely cooked through with no brown edges. This is a delicate balance to strike, though. I always find that the moment I flip an omelet, it completely falls apart—unless it's so well-done it's rubbery, of course.

At first glance, caviar doesn't seem overly appealing to the masses; not very many people would be willing to spend upwards of $1,000 on a tiny spoonful of salty sturgeon eggs from the Caspian Sea. Caviar truly is the ultimate symbol of luxury and fine dining.

Black lights come in all shapes and sizes, and they're useful in a variety of ways. They can help you spot fake currency, urine stains, interesting rocks, and deadly scorpions, and they can even help you view cool fluorescent artwork.

OneDrive, formerly known as SkyDrive, is a free online storage solution developed by Microsoft. If you're a fan of using cloud-based storage systems, then OneDrive offers you plenty of benefits. It's also heavily integrated into Windows 10, including the new File Explorer, in an effort to make utilizing OneDrive easier for you.

In an age where restaurants can charge $20 for eggs Benedict at brunchtime (if you're lucky enough to even get a reservation on a Sunday), many people long for a way to create this classic dish at home. But once you've taken pains to perfectly poach an egg and gently crisp your sourdough, the problem of the hollandaise still lies before you. The key to any good hollandaise sauce is to apply enough heat to cook the egg yolks, but not enough to scramble them. The minute the eggs begin to solidi...

If you ever need to spice up a party, drinking games can really get things started quickly. The objectives are generally to complete tasks or challenges, but it's really all a thinly-veiled excuse for increasing everyone's alcohol intake in a hurry while testing levels of inebriation.

Windows 10 marks a new era for Microsoft with the return of the Start menu, the demise of Internet Explorer, and the introduction of the remodeled Windows Store.

If you've ever turned on an episode of Iron Chef or Top Chef, chances are you've seen a contestant in gloves and goggles, yielding a canister that looks far more fit for a chemistry lab than for a kitchen. Wonder what's in the canister? Liquid nitrogen, the go-to tool/ingredient of molecular gastronomy, and one of the trendiest items in many gourmet chefs' kitchens.

Welcome back, my novice hackers! As most of you know by now, a notorious commercial, legal hacking group named "Hacking Team" was recently hacked. As part of the hack, thousands of emails and other material on their servers was divulged. Among the material released were three zero-day exploits. In this tutorial, we will walk through the steps to load one of them, which has become known as the CVE-2015-5119 exploit.

Flowers may be beautiful, but they're not usually appetizing. Sure, nasturtiums are hip in fancy restaurants, but they're primarily used as a garnish. Granted, fried squash blossoms are incredible, but the point remains: flowers are usually reserved for looking at, not masticating.

In the past, updating a rooted Samsung Galaxy device has always involved the complicated process of downloading the proper firmware for your variant, installing device drivers, then sideloading the update with Odin.

A good chef's knife is a thing of beauty and, with proper care, a joy forever. It can totally change the way you cook and turn even the dullest prep work into a glee-filled task.

There are certain ingredients that chefs regularly use to elevate their food beyond the status of what us mere mortals can create. Shallots are one. Good, real Parmesan cheese is another. And the rind of that real Parmesan cheese just so happens to be one of the culinary world's biggest kept secrets.

Oatmeal isn't the most glamorous breakfast, but it's definitely one of the best. It's healthy, filling, delicious, and easy to personalize. And, if you have instant packets, oatmeal is also a very quick and easy breakfast.

With all the stress that goes into booking flights and lodging, packing (and not forgetting) everything you'll need, finding pet sitters, and everything else that goes with a trip overseas, there's the added stress of staying connected while abroad.

At its core, grilling is the simplest form of cooking. You create extreme heat, you put a piece of food on top of the heat, and then you sit back and watch the magic happen. Yet despite the inherent simplicity in grilling, there are a million ways to make it more complex, more unique, and, yes, even more flavorful.

Samsung has a long-standing reputation for packing their devices with lots of added functionality, and the Galaxy S6 Edge is no exception. It comes with a nifty feature called "Information stream," which allows you to get quick, at-a-glance information by swiping the edge of your screen back and forth while the display is off.

Contrary to popular belief, sushi is not the raw fish that one gets at Japanese restaurants, but the rice that comes with it. It's hard to tell whether this popular misconception led to or came about because of the primary flavors that we think of in sushi are the fish. We often say a sushi restaurant has great fish, but almost never that it has great rice.

One lump or two? That was the age-old question with sugar cubes, which used to be a staple of any tea salon or dignified household this side of Downton Abbey. These days sugar isn't really used in cubes much except in bars and restaurants, and that's a shame. Cubes are a lot less messy than granulated sugar, and you can measure the exact amount you put in your drink no matter what.

CyanogenMod continues to be the most popular custom ROM for a good reason. Their team of developers always stay on top of the latest trends, and ensure that their software is packed with nice tweaks and awesome features. One such feature is an audio equalizer that allows you to fine-tune your device's various sound outputs. It's got a great interface, and works with any app that calls on Android's default audio mixer.

Greasy fast food. Snacks. Candy. Empty stomachs. What do these all have in common? They're all things that people commonly have for lunch during the week, because it beats the hassle of having to plan, make, and pack lunches before their workday.

The only mail I like getting comes in the form of an Amazon package, but when I go to my mailbox, it always ends up being a pile of credit card offers and catalogs I could never see myself ordering from. Those pieces of junk mail usually end up in the trash, which is horrible when you think about all the trees that had to get cut down in order to produce them.

Sony has a gorgeous line of smartphones using the moniker "Xperia," and the latest and greatest model is the Z3. The firmware for the Xperia Z3 was just updated to Android Lollipop, and many system apps of course got tweaked and refreshed with this latest version.

When it comes to added features, no manufacturer out there can hold a candle to Samsung. Whether it's a remote control for all of your electronics, a heart rate and stress level monitor, or a seemingly-magical stylus, Galaxy devices always have as much functionality as possible packed in.