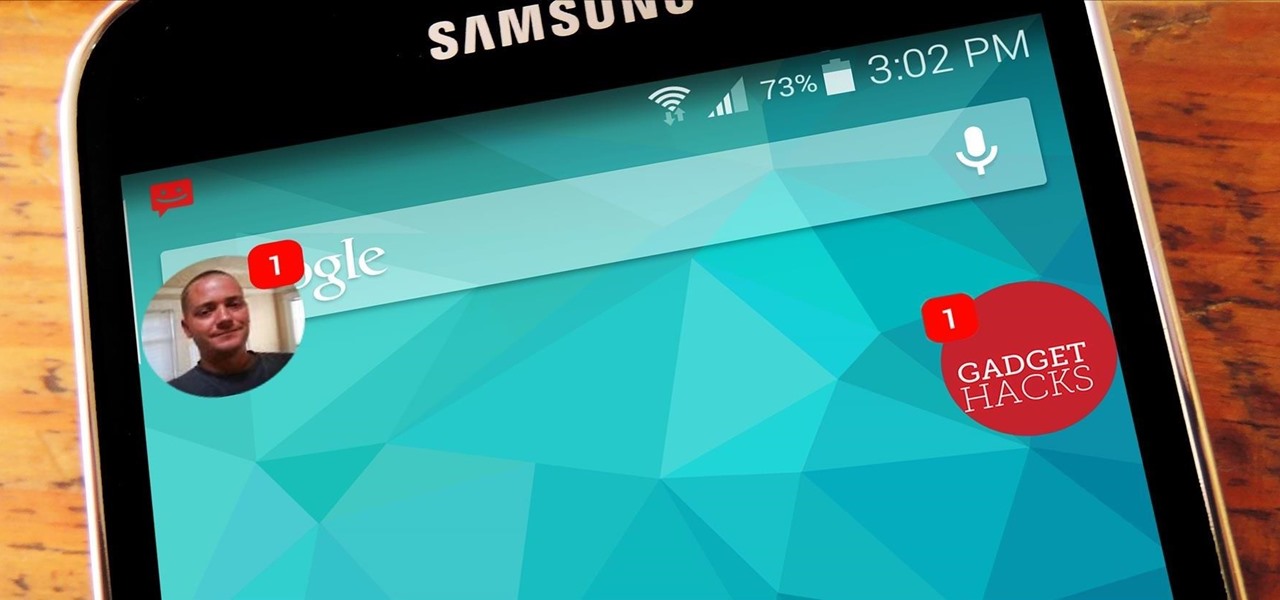
Beginning with KitKat, I've been used to customizing every aspect of my Android phone, but with the release of Lollipop, there is quite a bit of catching up that developers need to do. Most customization features, like quick settings rearrangement and theme support have already been ported over, but any type of lock screen customization has been noticeably absent.

One of the most mind-blowing meals I ever ate occurred when I was 12 years old. The main course and sides were good, if unmemorable, but my jaw dropped during dessert when my friend's mother whipped out a blowtorch—as in a bona fide welding torch from the hardware store—to finish off the crème brûlée.

With the Nexus 6, you get a very clean software experience with minimal bloat. While this is generally the main selling point for most Nexus fans, it can be a bit of a detraction for some.

With the sheer amount of photos, videos, and miscellaneous files we place on our computers, proper organization becomes necessary. Not only so that we can quickly get to a file when it's needed, but also to declutter folders and keep them from looking like random file dumps.

Like most people who cook in a small kitchen, I'm very wary of adding anything to my drawers and cabinets unless I'm sure it's going to be essential to my cooking arsenal or that it can be used in multiple ways.

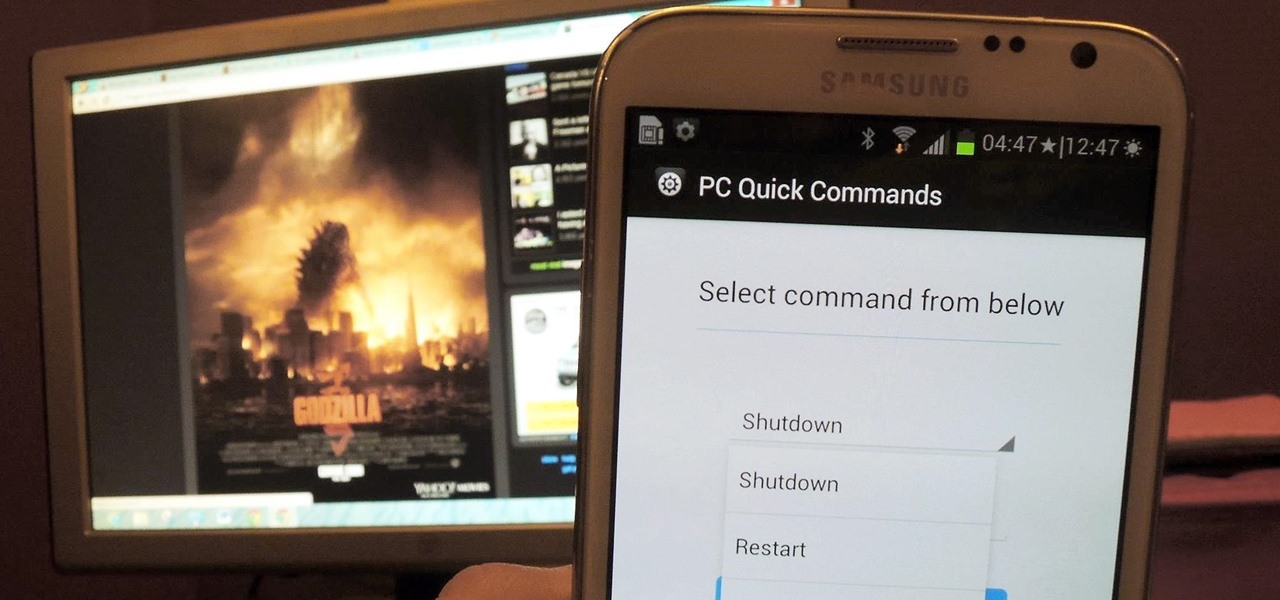
First, I want to give credit to the author where I first found how to do this: Astr0baby's Blog. This article was dated, so I took the script on his page and reworked it to make it work today. (I also included the way to make it hide the cmd line popup.) Requirements

Icebox cakes are some of the most satisfying, easy desserts to put together. This version made out of ice cream sandwiches takes the cake, literally, because the layers are almost pre-made for you. Simple and pretty when cut and served, it will be love at your first creamy bite. Depending on whether you want a layer of chocolate crunchies in your ice cream sandwich cake or not, this could be either a two-ingredient ice cream cake or a four-ingredient one. If you don't need the crunchy layer, ...

Blizzard Entertainment, the wildly successful video game developer that brought us World of Warcraft and StarCraft, has finally released their popular trading card game Hearthstone: Heroes of Warcraft to the Android platform.

One of the few areas where Android lags behind iOS is a comprehensive backup solution for apps. Root tools, such as the popular Titanium Backup, are capable of backing up all of your apps and their data, but not everyone wants to root their device and potentially run into issues with voided warranties.

Cold pizza is the holy grail of leftovers. That's a statement that elicits a slew of impassioned feelings. Either you love the idea of biting into soft crust and cold, fatty cheese, or scowl at the idea of pizza that isn't hot, crisp, and melty. Yet if we were to stand by the former sentiment, how would we argue on its behalf? Food Science Explains Why Cold Pizza Rules

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

Apple's iPhone 6 packs a powerful 4.7-inch Retina HD display with 1334-by-750 resolution, and it's so incredible in person that it almost looks fake. However, as awesome at this display is, it can always be better.

We've previously shown you how to get your Samsung Galaxy S4 looking more like its successor by installing the revamped S Voice app and the new Quick Settings. Now, we're taking it a step further by giving you the Galaxy S5's stock Settings app. After this mod, it'll be pretty hard for others to distinguish your GS4 from a GS5.

Whenever a new Android device is realized, the first thing I figure out how to do is to get it root access. Generally speaking, rooting has never been easier, with many one-touch methods like Stump and Towelroot available. But as manufacturers and carriers increase security with each new product, there is one tried-and-true root method that continues to work on most Samsung devices—Chainfire's CF Auto Root.

It's pretty logical for your MacBook to sleep when you close its lid, but under certain circumstances, you may not necessarily want this feature to kick in.

We're always looking for great food hacks to help us become better cooks who can create delicious food with less waste, fuss, and hassle. You never know where the next good tip will come from, so we've all learned to keep our eyes and ears wide open.

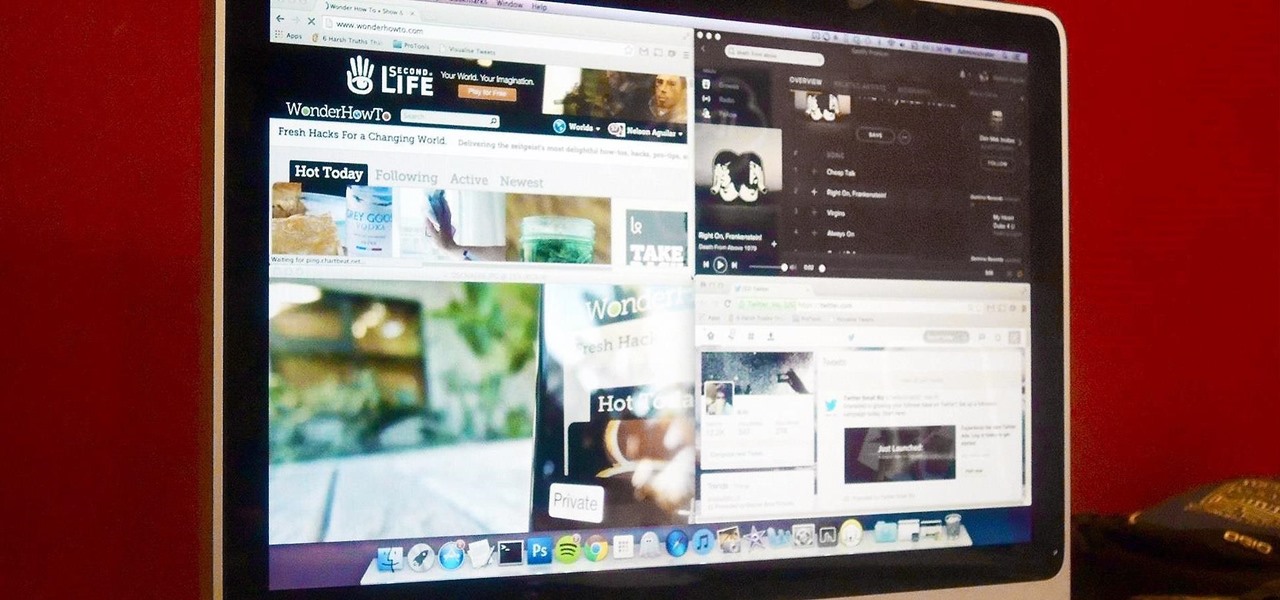
Mac OS X has finally added a way to use two apps side by side in full screen mode, à la Microsoft's Windows Snap. But since it's only available in 10.11 El Capitan right now, those of us with older systems will have to wait until the El Capitan Public Preview or final build is released later this year.

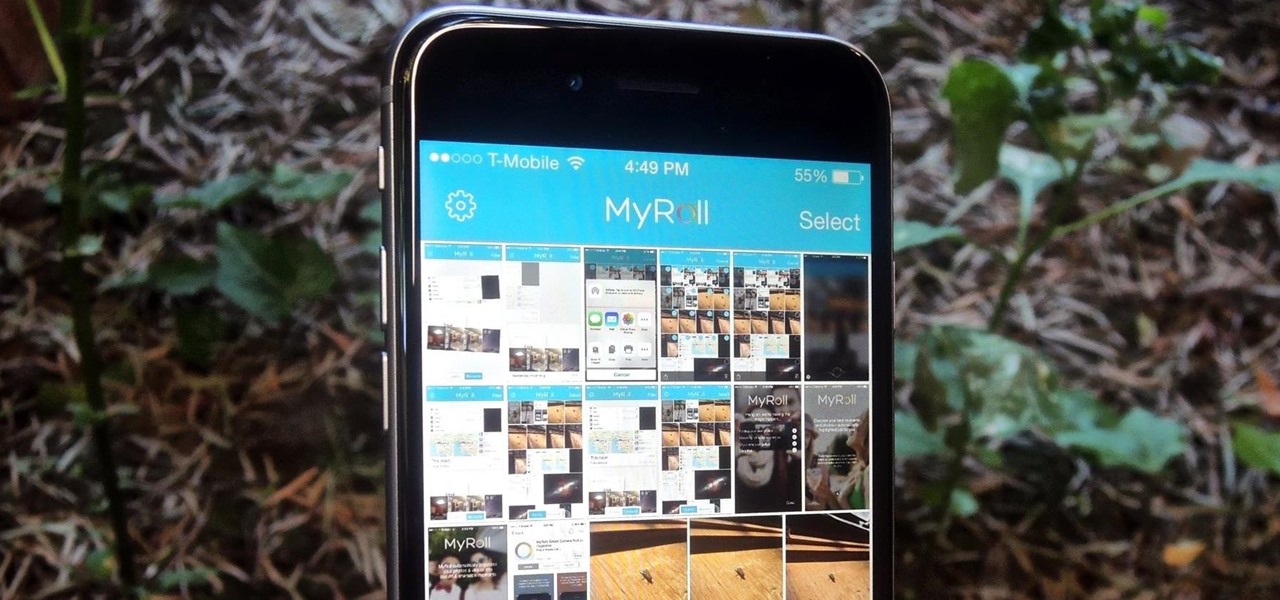
While there isn't a "Camera Roll" anymore in iOS 8 for your iPad, iPhone, or iPod touch, the photos that were once in it are not missing—they're just not as convenient as they once were. In the upcoming iOS 8.1 update, Camera Roll will be making a comeback, but we've found something better that you can use right now—even after Camera Roll returns!

There are a lot of great new features in iOS 8, but not everyone is enjoying them. Some of you may just genuinely prefer iOS 7 over iOS 8, and some of you may be experiencing lag on older devices like the iPhone 4S, however minimal it may be. Whatever the reason, if you don't want iOS 8 on your iPad, iPhone, or iPod touch, there's still time to downgrade back to iOS 7.1.2.

iPad, iPhone, and iPod touch owners: it's that time again. iOS 8 has been released to the public, and those who have been eager to update since Apple's WWDC announcement won't have to wait any longer. Since iOS 8 promises to pack a bunch of new, really great features, it's time to present your options for getting on the latest and greatest for your Apple device.

When Android 4.4 was released, the massive changelog led to some awesome new features getting lost in the virtually endless list of new tweaks. One such change was the ability to set a default text messaging app, which streamlined the existing process of installing a third-party SMS client.

Last week's tech roundup featured iPhone 6 clones, an all-in-one sleep tracker, Xbox One updates, and other cool gadgets. This week, there's a lot more to show off, and a bunch of stuff that I need to get my hands on! Everything from app updates to putting stickers on your favorite items, I can't help but squeal at how much the "future" is right now.

Many game developers have finally realized that in order for their games to be successful, they have to support Android. To really win Android users over, they should also accommodate us hardcore gamers who have OTG cables with the ability to hook up controllers to our devices.

One of the most feature-packed camera suites out there resides on the Sony Xperia Z2. Along with the regular camera and video modes, it comes with Motiongraph, AR Effect, and Social Live.

Google Play Music is one of the best cloud music services out there. Without ever paying a dime, you can upload as many as 20,000 songs to Google's servers, then use the app on your smartphone to stream these songs without taking up any of your storage space. And if you're willing to shell out $9.99 a month, you can even play songs from the massive All Access library.

Apple took great strides to enhance Accessibility features on iOS 7 for low-vision users, adding button shapes, dark colors, bold keyboard text, and more. With iOS 8, Apple looks to continue their run at making life easier for the optically impaired.

The new OnePlus One packs a 3,100 mAh battery that promises to last all day and night. While that will work for most, some of us don't quite know how to put our phone down and save some juice.

Recipes are invaluable to cooks who are just starting out, but what if you want to get to the next level? Then it's time you learn how to apply simple math to food. In other words, learn how to cook using ratios, not recipes.

Admit it, you wish Siri was on your Mac, and so do I. She stole my heart on iOS, and now every time I open up my MacBook, I feel something missing. Wouldn't it be great if we could, I dunno, hack Siri onto our Macs? Yeah, it would!

The new iOS 8 was just unveiled, and it looks pretty awesome. Apple showed off some of the enhancements and new features we can expect to receive in the fall at WWDC, and while not the huge facelift we saw with iOS 7, it does showcase what Apple does best—refinement. Continuity

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

Sense 6 is great, don't get me wrong, but sometimes I start to miss the vanilla Android experience that comes with Nexus devices. You can always convert your M8 to the Google Play Edition, but then you'd have to ditch all the Sense exclusive features, and we wouldn't want that.

You don't always plan on getting drunk, it usually just sort of happens, right? You finish one beer, move on to the next, and all of a sudden you're a six-pack in and feelin' it. And when you're drinking in places you're not supposed to, it can get ugly.

Released last year for iOS devices, Frontback is a simple photo-taking and sharing app that not only snaps a picture of what's directly in front of the camera, but also behind it, which is to say, a selfie.

While rooting your Galaxy Note 2 certainly has its advantages—everything from increasing security to relieving the Power button of its duties—it's definitely not for everyone.

As fellow softModders, I'm sure you strive to find any and every way to make your phone unique. Wallpapers and icon packs are great to get started, but to really stand out from the rest, try changing your HTC One's boot animation.

I don't like a lot of app icons on my home screen. It makes everything on my Nexus 7 feel dense and congested. As a minimalist, I like a simple and well-organized home screen, which is why I regularly utilize my app drawer to launch apps.

Changing your wallpaper and downloading icon packs is nothing new to the HTC One, but some people will go overboard with remapped keys, icon layouts on custom grids, and extensive wallpaper cropping—processes that could take hours to get just right.

Americans consume over 1.2 billion pounds of potato chips each year, making it one of the most popular snack foods in the United States.

You probably use your smartphone to mostly surf the web, play games, and communicate with others, but there's so much more it can do. Thanks to integrated features and third-party apps, you can seamlessly control things around your home, including your TV, tablet, Bluetooth speakers, and even lighting fixtures.