Whether you are a budding magician, or just a card game enthusiast looking to bone up on his skills, impress your friends and learn some of the many ways to perform card flourishes. Our expert magician will demonstrate each flourish, with step-by-step instructions and tips for properly performing them.

In these videos our expert will teach you how to do at-home waxing as well as what to expect if you go to a spa to get waxing done from a professional. You will learn what types of supplies you need to purchase in order to perform waxing at home. You will also learn about alternative hair-removal products, and the advantages and disadvantages of shaving vs. waxing. In these videos our expert will demonstrate how to do different types of waxing. You will see demonstrations of eyebrow waxing. Y...

For a car to operate normally, it must have some basic care and maintenance. In these free automotive repair videos, learn how to maintain your engine cooling system. The cooling system keeps your car from overheating on the road; a lot of heat is generated by an internal combustion engine, which must be properly dissipated. Our expert will show you how to check antifreeze levels and mix and refill your fluid if needed. He’ll also give you tips on how to find leaks, and how to flush your cool...

Tapas are a very easy dish to make no matter what type you are preparing. Shrimp, potato, and many other ingredients can make up specific tapas. In this free video series you will learn how to prepare shrimp tapas and potato tapas and chorizo as each step is laid out for you piece by piece from the utensils you will need to the way to properly serve them. So the next time your tummy is rumblin' and you've got a while until dinner keep these in mind not only for yourself but for guests you mig...

For a car to operate normally, it must have some basic care and maintenance. In these automotive repair videos, learn how to maintain your engine cooling system. The cooling system keeps your car from overheating on the road; a lot of heat is generated by an internal combustion engine, which must be properly dissipated. Our expert will show you how to not only spot and remove the heater core hose in a car but how to determine what is wrong with it, change it if needed and reassemble the vehic...

In this video series, our expert shows you how to operate the common stair step machine. Though the stair stepper has amazing potential to burn calories, it can be dangerous if not used properly. Sheila Lindsey illustrates the proper way to use the stair master machine. She also shows you how to monitor and stay within your heart rate. Shelia also gives you great advice on organizing a cardio workout routine. So, before stepping up to the challenge, learn how to get the most out of your stair...

In this online video series learn how to culture fruit flies from fruit fly culture expert Richard Reavis. Watch these videos to learn about the different types of fruit flies. And learn fruit fly culturing essentials such as what materials and supplies you need to culture; how to select fruit flies; how to clean the culture area; how to measure and properly mix the media, water, and yeast for the culture; how to add flies to the culture; how to prevent infestation and contamination of mites ...

Remember Brian sticking a 4-inch nail up his nose at Diggnation New York? Want to do it yourself? This time he shows you how it works!

Kathleen Wrightis going to show you tips and techniques for a successful Henna Tattoo at home. She shows you how to mix the henna properly and prep, as well as how to practice designs, and then how to care for your completed tatoo so it lasts.

It looks as though the novel coronavirus and social distancing guidelines are here to stay for a while. So companies of all sizes and industries are scrambling to adapt to a new reality in which everything from morning meetings to large-scale presentations are done entirely online. It looks like this is going to be the new normal for the foreseeable future.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to root another.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

Nowadays, our phones are capable of just more than 30 fps video. Phones like the Galaxy S10 can shoot 4K at 60 fps, even on the front camera. Slow motion functionality has recently started to appear on more and more devices — but as you may have noticed, the quality of the feature differs from phone to phone.

Using a green screen is an affordable and easy way to transport your video to anywhere imaginable, even to places that don't exist. You can use it to sit behind a desk in a busy newsroom or dance on the moon, but first, you have to know how to properly perform chroma key compositing two videos together. Fortunately, Enlight Videoleap on iOS makes it easy.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

Almost every phone comes with biometric security of some sort these days, but the same can't be said of Windows computers. While fingerprint scanners are becoming increasingly common with laptops and desktops, they're nowhere near ubiquitous. Thankfully, your phone's scanner can be used as a sort-of remote authentication point for your PC.

Waking up your Apple Watch to see "your heart has shown signs of an irregular rhythm suggestive of atrial fibrillation" might come as a shock. While your watch can send you warnings if it detects a fast or low heart rate, those messages are pretty vague, while the abnormal arrhythmia alert can downright scary. So what should you do if you receive one of these AFib notifications?

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

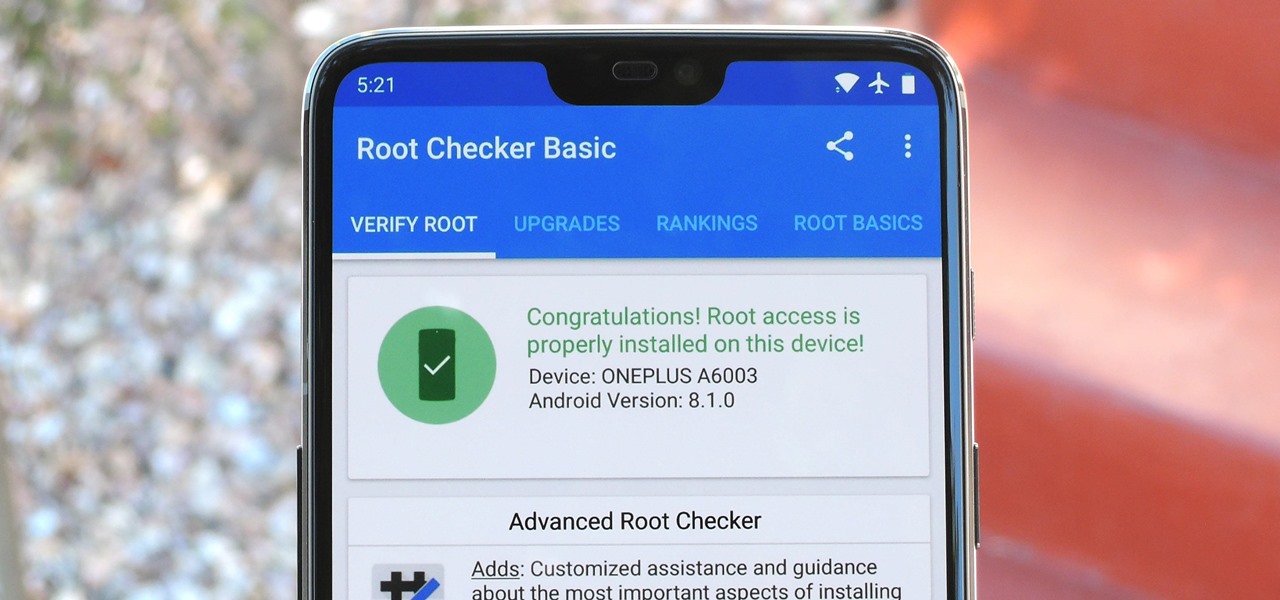
It's the icing on top of your cake (or whipped cream on top of your Android Pie) of despair. You may have not had the easiest time rooting your device, but you feel like you overcame all of the obstacles. Only now to discover that those very apps and mods you were rooting for still won't work — and the signs point to a lack of root access. Don't lose hope, because we have some tricks up our sleeve.

Before you can dive into customizing your OnePlus 6T, you must take the initial step of unlocking the bootloader to gain the ability to install TWRP, Magisk, custom ROMs, and other mods.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

For some Android users, this guide is sacrilege — but for others, iOS is just an attractive operating system that can be admired without feeling like you've betrayed your own phone. If you're one of those Galaxy Note 9 owners that have peeked across the aisle and desired an interface as clean as the one on the iPhone XS Max, you can configure your Note 9 to look like its rival with some tinkering.

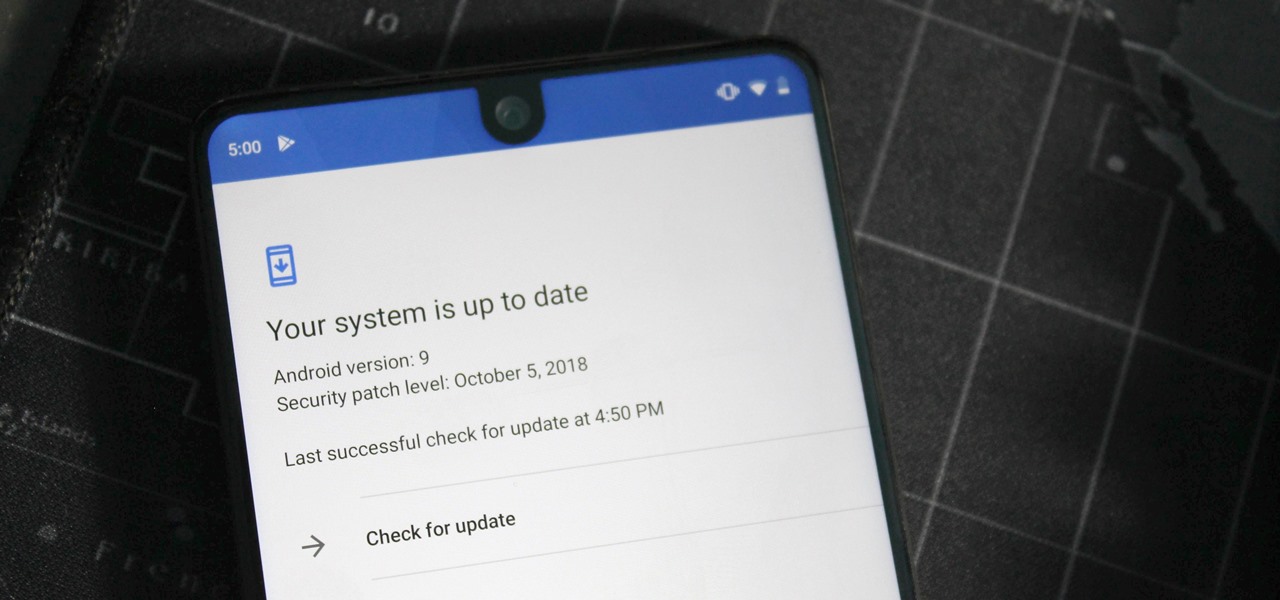
One of the issues with rooting your device is the inability to update your phone via OTA. Any security patches or software updates pushed out by the OEM are lost because your bootloader is unlocked. However, you still can update your device, it just a take a bit more effort.

Although the Galaxy Note 9 is an amazing phone, many members of the Android community won't even look at it. This isn't just because of the Samsung Experience skin, but the large amount of bloatware that comes with this device. However, with a little work, you can remove all of it.

Although the Essential PH-1 got off to a rocky start, thanks to steady updates, it has slowly become one of the best Android phones to come out in recent years. For $499, the Essential Phone is a cheaper Pixel, receiving updates almost as soon as the Pixel lineup does. What's more, you get a phone with an easily unlockable bootloader, which is the first step to rooting.

If you haven't heard, another big OEM has decided to drop the headphone jack. OnePlus, the hero of the people, has just announced that the OnePlus 6T will not have the popular port. With this decision, audiophiles and others are limited to just three big-name options.

If you've been getting that "Please update from the iOS 12 beta" alert continuously in iOS 12 public beta 9, Apple just issued a fix for it Friday, Aug. 31, with iOS 12 public beta 10 — just in time for Labor Day weekend. This marks the second update this week as dev beta 11 and public beta 9 were released on Monday. It's also just one day after Apple announced its Sept. 12 event.

You can feel it in your bones. You may die if you don't get this phone. There's just one problem — the price. Suddenly, you come across what seems like manna from heaven. That very device, at a deeply discounted rate, can be yours.

As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing man-in-the-middle attacks.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

Year in and year out, OnePlus flagships top our list of the best phones for rooting. Why? Primarily because rooting does not void your warranty, and OnePlus goes out of their way to make the whole process as easy as possible.

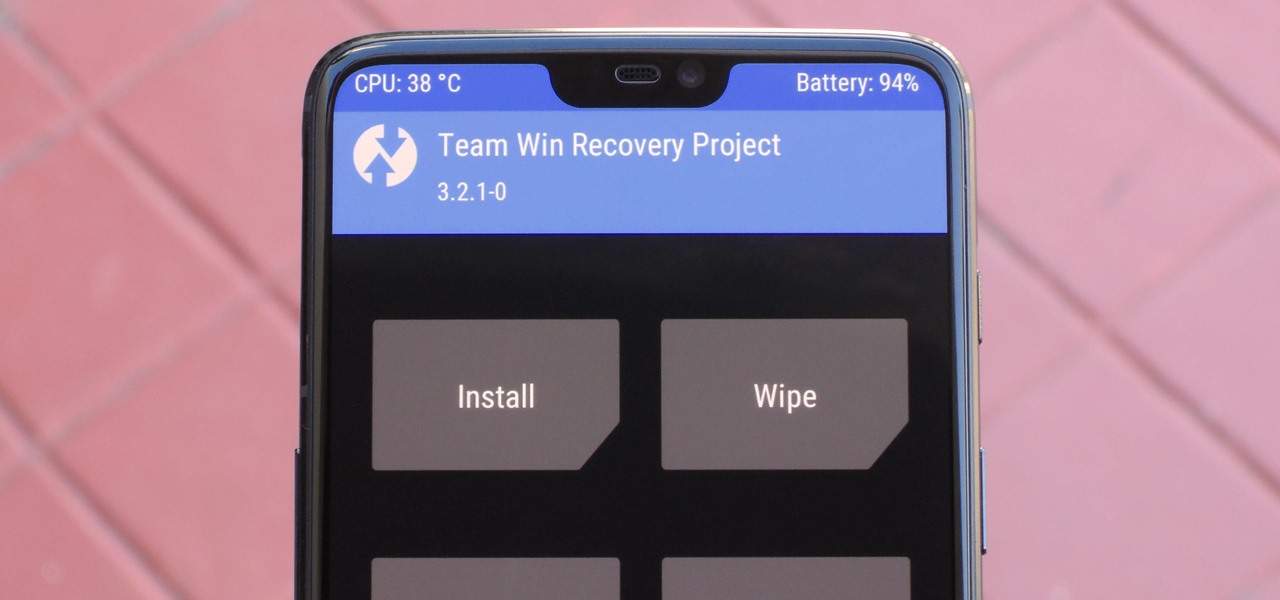
When it comes to modding Android, there's no better tool than Team Win's TWRP custom recovery. You can use it to root your phone, flash mods like Magisk or Xposed, and even replace the entire operating system with a custom ROM like LineageOS — honestly, there's not much this utility can't do.

If you're using a mobile device, it's a pretty safe bet that your apps are sending lots of information back and forth from their servers. To make sure there is no inappropriate data collection going on, it's worth setting up a web proxy to spy on this traffic, so you know exactly which apps are "phoning home" and when.