If you’re camping outdoors, you’ll probably need to know how to make a campfire at some point. Fire is an important tool to have for cooking food and purifying water, for warmth and light, and for protection from wild animals at night. In this video series, learn the proper way to make a safe, long-burning campfire. Our expert, Brian Rajchel, will show you how to choose the right area in your campsite for the fire, how to build a fire pit, how to start a fire without matches, and how to prope...

Vampires and bad dreams aren't the only enemies of the unwary sleeper. Teeth grinding while asleep is an annoying and possibly painful problem afflicting may people. There are a variety of reasons you may grind your teeth but, luckily, there are also a number of solutions to this nocturnal problem.

In this video series, watch as football player and fitness instructor Sean Hobson teaches how to do football conditioning drills. Learn how to do a two step drop and pass, how to hand off the football, how to pitch the football, how to roll out as a quarterback, how to catch a football, how to block in football, how to throw a football, and how to play tight end.
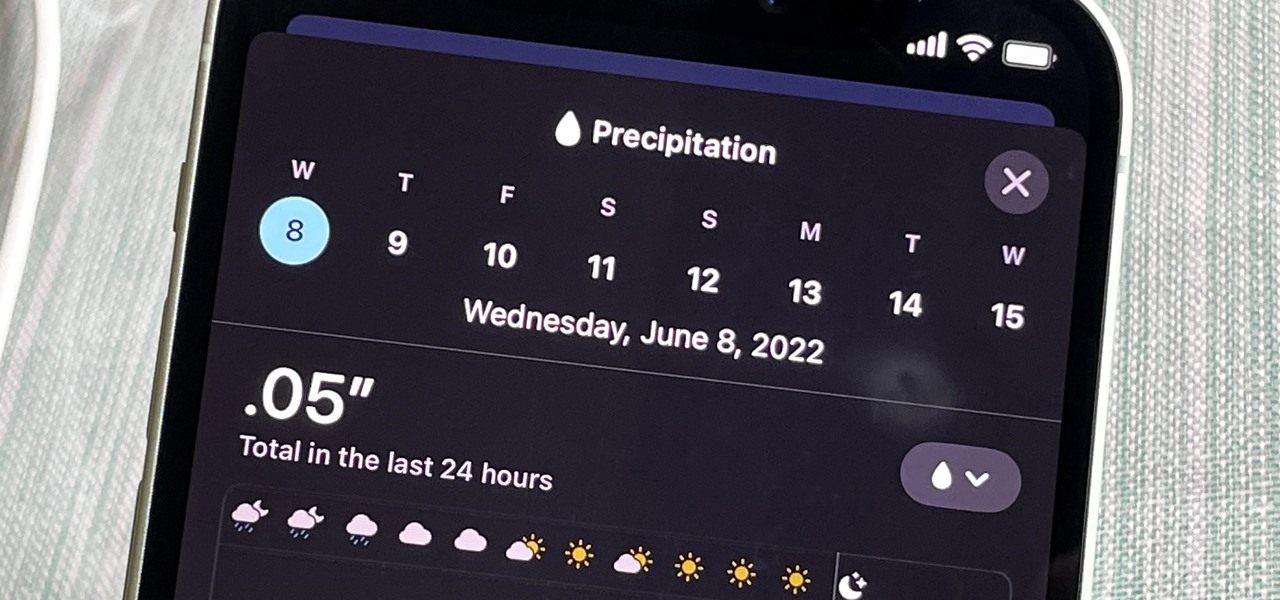
Your iPhone's Weather app received its biggest update yet. Apple finally incorporated its Dark Sky purchase into Apple Weather, so you'll see more information for each location's forecast. Plus, there are a few surprises to be excited about, such as the ability to add more trackable cities.

While there are many advantages to working from home, properly managing your time can be a real issue. Working remotely requires a particular skill set, including an ability to focus, self-motivate, and communicate from a distance. Thankfully, all of these skills are teachable.
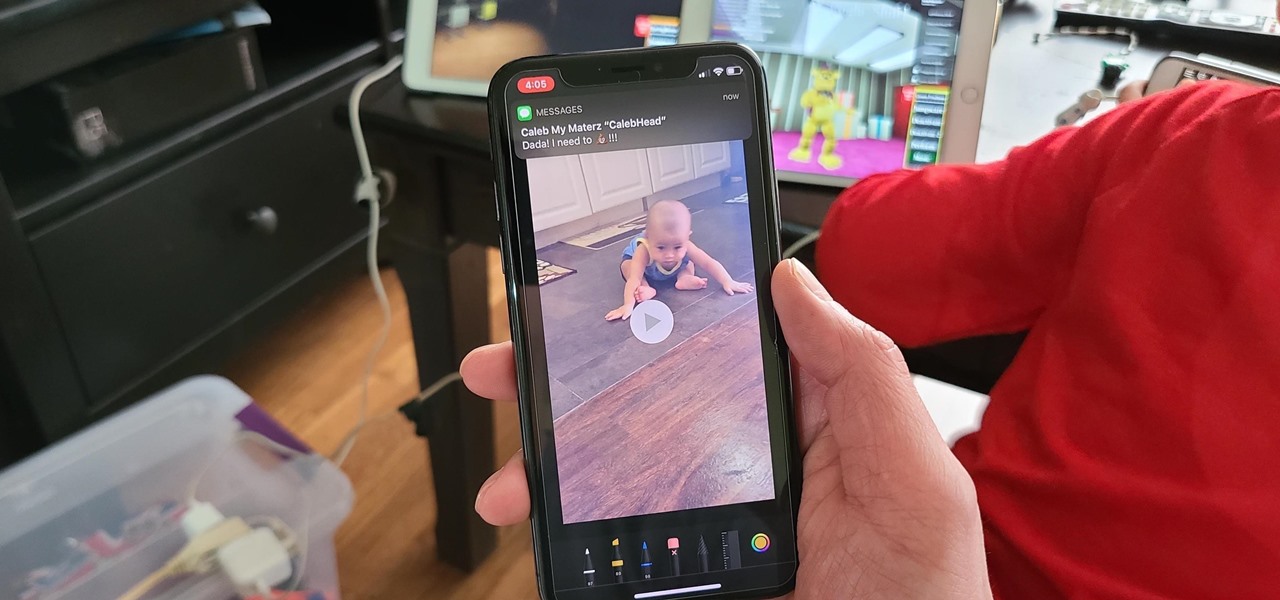
Since its introduction in iOS 11, the Screen Recording tool has been a great way to show less tech-savvy users how to use their iPhones better. It's never been easier to show your grandmother how to disable Live Photos or lower screen brightness. However, banner notifications can appear during a recording, forcing you to start over. They can even interrupt a screen share during a Zoom or Skype meeting.

Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a tool called Arjun can be used to discover hidden HTTP parameters in web apps.

Anyone who has used Linux long enough is familiar with sudo. Short for superuser do (or substitute user do, depending on who you ask), it allows users to run commands as either root or another user on the system. From a hacker's point of view, sudo is often all that stands between them and root access. We'll be exploring an older vulnerability in sudo that allows a user to run commands as root.

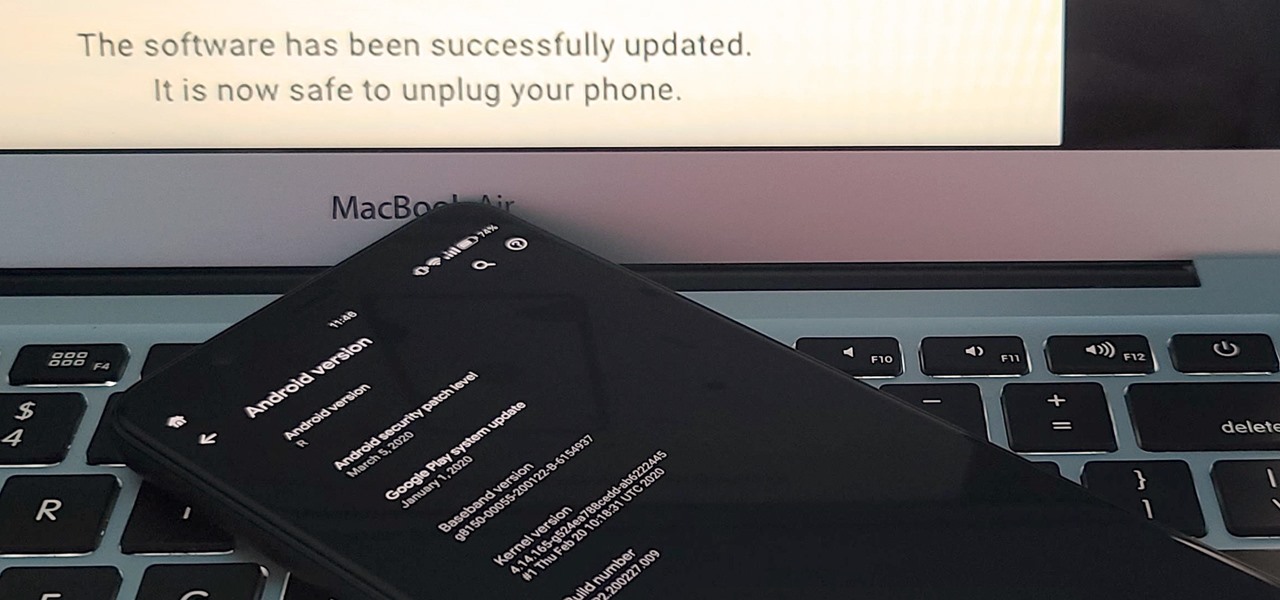
If you've ever tried to update your Android phone manually, you know the process can be unnecessarily hard. There are so many steps and parts, that if one thing goes wrong, the whole process doesn't work. Recognizing this, the Android team came up with an even easier way.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

The Pixel 4 is one of the most talked-about phones of 2019, and it has many things going for it, especially in the world of rooting and modding. Just as with previous Pixel generations, unlocking the bootloader is the gateway to realizing your device's true potential. It can make way for such things as TWRP, Magisk, custom ROMs, and many other device-specific mods just the same.

Apple unveiled the latest generation of its flagship earbuds, AirPods Pro, on Monday, Oct. 28. Aside from the increased price tag, new in-ear design, and wider charging case, the biggest change by far is in Active Noise Cancellation. Finally, we can listen to AirPods on a plane, walking by a busy road, anywhere with a lot of noise pollution. But how does it work?

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

I've been using the Galaxy Note 10+ as my daily driver for a while now. I love it, but as with any phone, it loses its pizzazz after a while. But since it's an Android phone, there's always a way to add fresh features and functionality to the UI.

Drone mishaps, such as the collision that scratched a military helicopter in New York, are becoming something of an everyday hazard.

One of the first steps in attacking a web application is enumerating hidden directories and files. Doing so can often yield valuable information that makes it easier to execute a precise attack, leaving less room for errors and wasted time. There are many tools available to do this, but not all of them are created equally. Gobuster, a directory scanner written in Go, is definitely worth exploring.

Samsung has stepped up its camera game with the Galaxy S10's dual- and triple-lens systems. But as impressive as the hardware is, the native Samsung Camera app still isn't as good with image processing and video stabilization as the Google Camera app for Pixel phones. Thankfully, you can get the best of both worlds.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

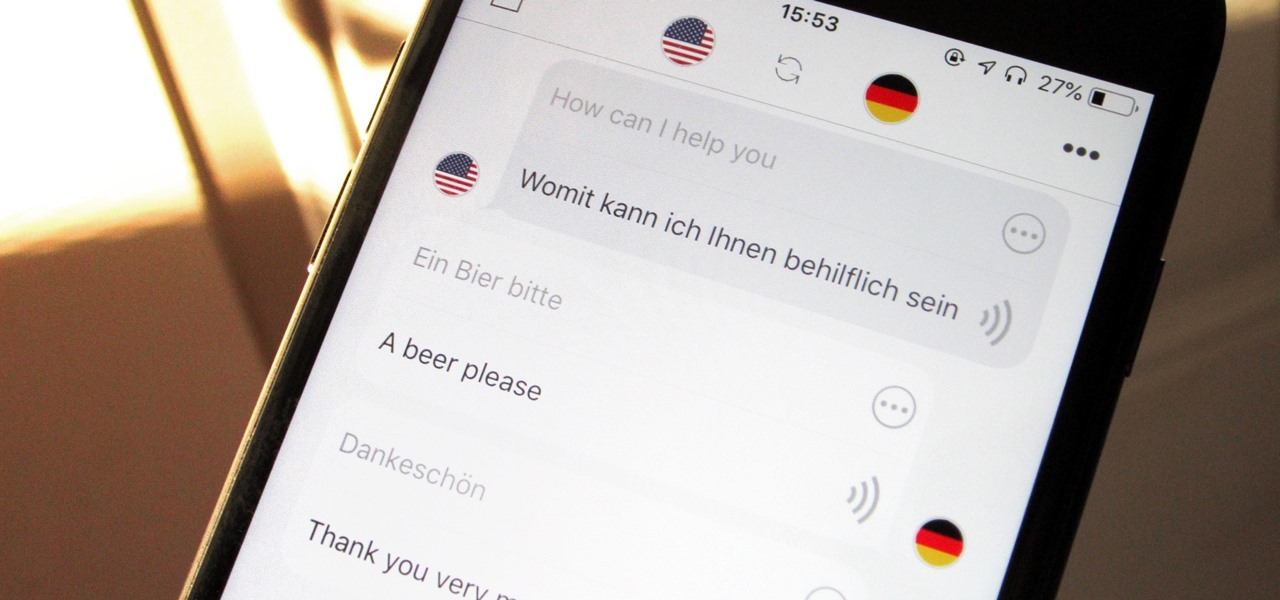
Nothing beats a human translator, but Google Translate and other software-based solutions have developed into decent alternatives for help with basic translations. Need an English word translated into German? No problem — but what if you need to have a conversation with someone who doesn't speak your language? Is Google Translate capable of doing that? The answer is not really.

It wouldn't be iPhone season without a new controversy. Chargegate, Apple's latest PR nightmare, is the name being used for charging issues on some iPhone XS and XS Max devices. If you plug in your iPhone at night — or whenever — then wake up or come back later and see that your iPhone has even less battery power, you're affected. But there is a fix you can implement right now.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

Android does a great job at multitasking. Split-screen mode and picture-in-picture are terrific at letting you manage more than one app at a time. But there are some limitations. For instance, when you're playing a video and you open a second video in split-screen, the first one pauses. Thankfully, Samsung has a fix for this.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

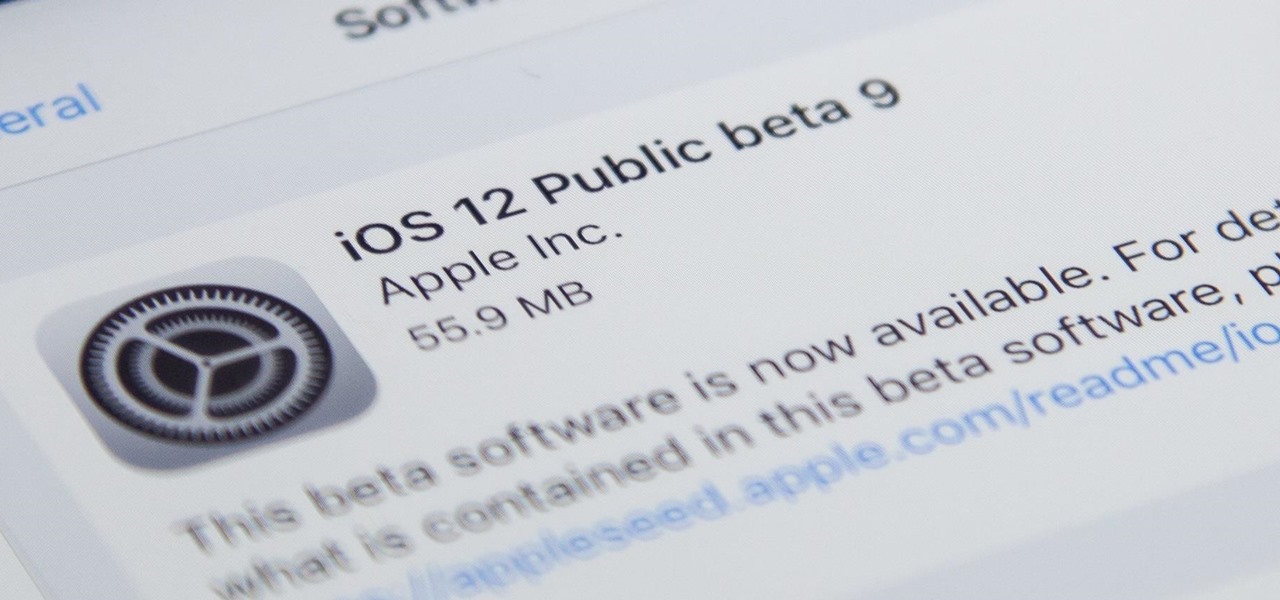
Apple released iOS 12 beta 9 to public beta testers on Monday, Aug. 27. The update comes at the same time as the release of dev beta 11. This is surprising, as Apple typically releases developer betas at least a few hours before the public version. Then again, everything Apple is doing with its iOS 12 beta as of late is surprising.

On August 1, Google Play started requiring new app submissions to target at least Android 8.0 Oreo's API. Then, as of November 1, all updates to existing apps were required target the same API. While at first glance, this change may mean little to you, it will have a profound impact on Android. Now, your favorite apps will be getting better.

When it comes to the sub-$250 price range, the new Nokia 5.1 might be the perfect phone. Of all the new models announced at Nokia's event in Moscow, the Nokia 5.1 offers the most with the least compromises. For a third of the cost of a flagship, you get a phone with a premium build, solid specs, and good battery life.

The "Up Next" feature in Apple Music helps you control which songs you want to listen in the order that you want. However, this list can become messy fast, quickly becoming a collection of songs you never wanted to listen to in the first place. Luckily, Apple has built a way for you to clear Up Next, it's just not very obvious.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

Using Hydra, Ncrack, and other brute-forcing tools to crack passwords for the first time can be frustrating and confusing. To ease into the process, let's discuss automating and optimizing brute-force attacks for potentially vulnerable services such as SMTP, SSH, IMAP, and FTP discovered by Nmap, a popular network scanning utility.

Kali Linux is known as being the de facto penetration-testing Linux distribution but can be a pain to use as an everyday OS — even more of a pain if that means carrying around a second laptop or the constant frustration of using the finicky Wi-Fi on virtual machines. But there's another option: installing a Kali subsystem on your Windows computer as a convenient compromise.

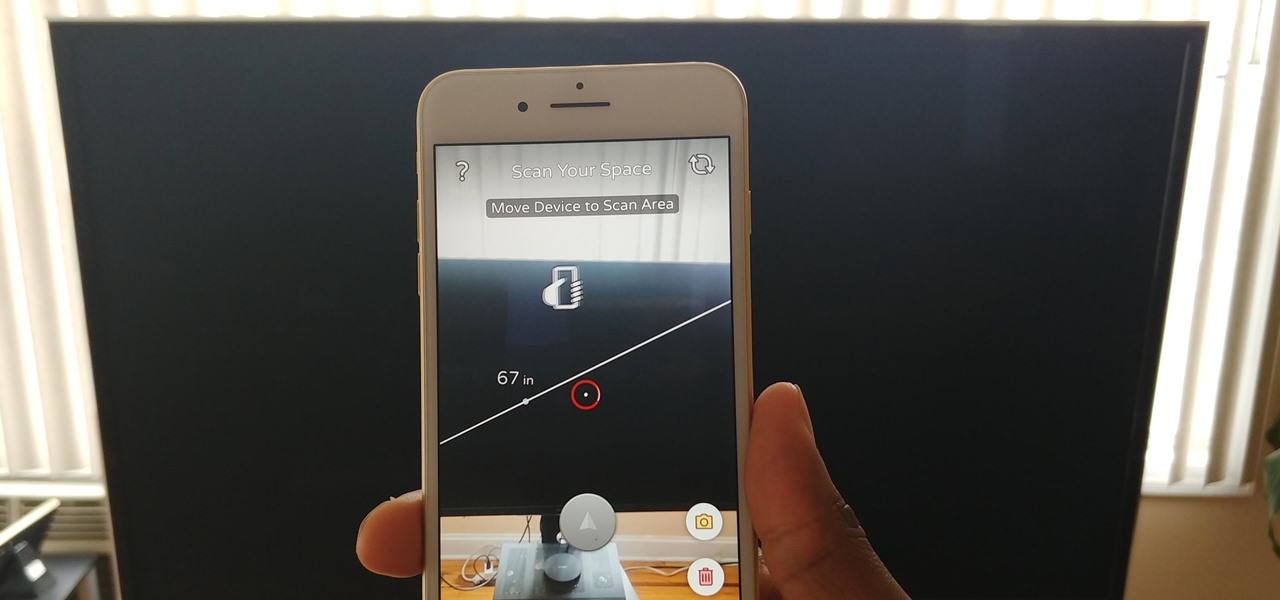
Our phones have evolved past a simple pocket computer. They have become more like Swiss Army Knives, opening up possibilities that were previously considered Sci-Fi material. Thanks to the recent push into augmented reality, a new world of tools is becoming available to mobile users.

The default Camera app got a few more tricks up its sleeves when iOS 11 was released, and the best addition by far was the inclusion of a built-in QR code reader since that meant no more third-party apps just for QR code scanning. However, Apple's built-in QR code scanner did have a vulnerability at one point that would let hackers direct you to a compromised website without you even noticing it.

Magic Leap's recent flurry of patent applications prompted us to look around for any trademark movements from the company, and it turns out that the Florida-based company has been quite busy.

OnePlus has now officially upgraded both the 5 and 5T to Android 8.1 Oreo. As implied by the version number, this isn't a huge update from Android 8.0 Oreo. However, OnePlus has included a few of their own features as well.

With the S9 and S9+ upon us, you maybe wondering if it's time to retire your aging Galaxy and either sell it or do a trade-in to get Samsung's latest flagship. Before you do, however, it's important to make sure that all its components — most notably the sensors — are working fully in order to avoid potential headaches.

For some of us, mornings are difficult. But if you can manage to start your morning right, you can trigger a chain reaction that leads to a more productive day. Fortunately, our phones have the tools to help us get off to a good start.

One thing that makes Apple great is the connectivity between its products. Many tasks you do on an iPhone can be switched over to a Mac or iPad quickly and easily. The Notes app is no exception to this advantage, but you need to make sure you're set up so that your notes sync properly on each device you have.

Apple has tools built into iOS to help parents monitor the iPhone habits of their children. However, those same tools can be used by everyday iPhone owners to both hide apps they don't care about, as well as restrict features they don't need or that infringe on privacy. Whether you fit into one category or the other, all iPhone users can benefit from the "Restrictions" feature.

Most of us have never put much thought into this, but the question needs to be asked — what exactly happens to all of our online accounts when we die? No, the internet won't just know and delete accounts for you, so you need to plan for life's one guarantee. Because without a plan, things become a lot harder to sort out.