Having an open-source platform like Android is great, allowing manufacturers and developers the ability to make their own skins and apps to truly customize the end-user experience. The only downside is that when an update comes to vanilla Android, many of us are left in the cold, unless you have a Google Play Edition HTC One.
Transparent status bars and new lock screens weren't the only new additions that came with the Galaxy S3 KitKat update. Along with better battery life and a smoother user experience, we got a new toggles design and recent apps menu. Of course, Samsung's infinite wisdom left these two aesthetic features hidden away. Luckily, with root, you can easily enable them with just a few quick edits.

The old "my battery is dead" excuse for not calling your mother may soon be a thing of the past. A team from the Korea Advanced Institute of Science and Technology (KAIST), led by Professor Jo Byeong-jin, has developed a "wearable thermo-element" that can be built into clothing to power your electronic devices. The science behind the innovation converts body heat (thermal energy) into usable electric energy. Made with lightweight glass fiber, this small thermo-element strip can produce about ...
Thousands of history files, cookies, other unwanted files stored in your system as logs and other formats. To manually check each one is difficult. New computers are too fast by processor behavior, after some times of working it comes to slow performance.
There are some really talented graffiti artists out there. Some of them are good enough that businesses hire them to paint advertisements, rather than hiring someone to scrub their work off the side of the building.

There are very, very few things better than a solid Hobbit songI mean, I was almost brought to tears when Pippin busted out this one in The Lord of the Rings: Return of the King.

Microsoft's updated web browser, Internet Explorer 10, has only been out for a few days on Windows 8, and there is already a storm of controversy surrounding its launch.

All kinds of people pretend to be someone they're not on the internet, including scammers, people attempting to wind others up, hackers and web predators. Almost all of these people will leave bases uncovered and they're all easy to expose when you understand how to. Here are my favorite ways of finding out when somebody is lying quickly. Image Search
I've noticed that a few people using the crypto-currency, Bitcoin are having issues importing private keys to their Bitcoin wallet. This is easy to do and doesn't require anything other than your Bitcoin client/daemon (as of ver0.6.0 ) and the command line.

In this video tutorial, viewers learn how to record songs on the Internet without a microphone. Begin by putting the sound control icon into the application bar. Then go to Volume Control and click on Properties. Click on Recording and then select all the recording options. Now close the window. Then select the mixage on the volume control, but do not close it. Then open the sound recorder in the Start menu and find the song that you want to record on the Internet. Play the song and click on ...

Escape into a crunchy concoction of chopped nuts, delicious dried fruits and creamy coconut milk. Be happy and healthy with a delicious raw version of those store brand granolas. This two part series takes you through all of the steps, from making your own coconut milk to making a quick bowl of fresh, raw granola.

4 things you MUST do for a successful deer management program. A successful program means healthy deer and great hunting!

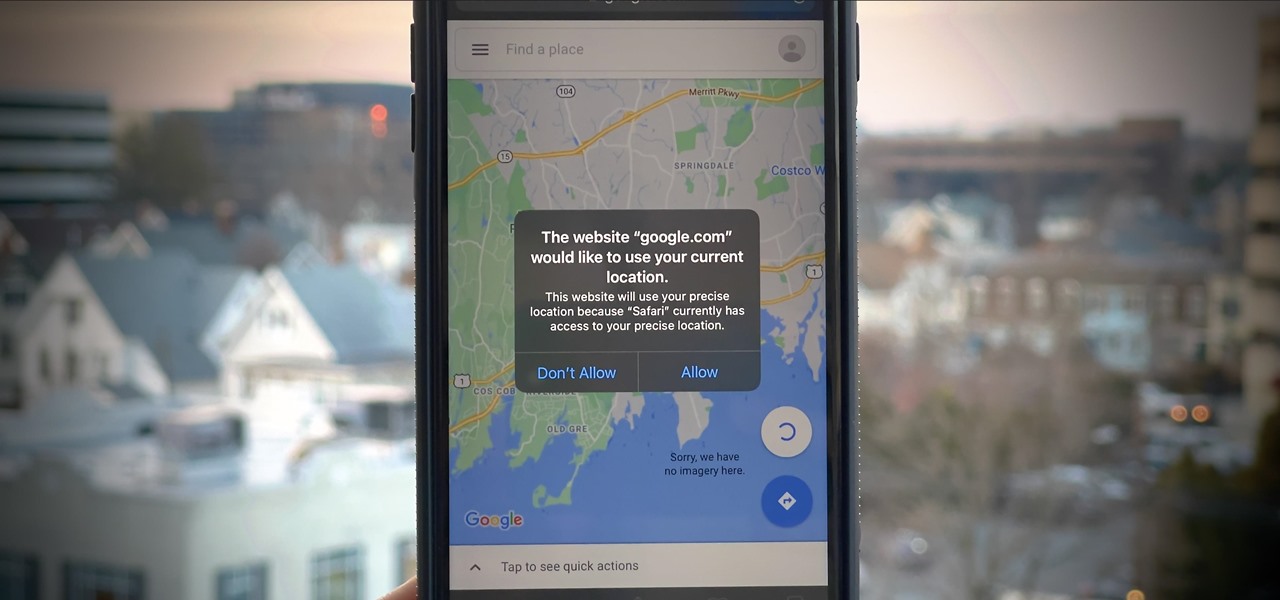
If you surf the web on your iPhone, you no doubt run into this problem all the time: a website wants your location. It can happen when performing a location-based task, such as using a store locator, or whenever a web app just wants to deliver better ads or local recommendations. If you're tired of allowing or denying permission each time, there's an easy way to stop the annoying security pop-ups.

Help me, George Clooney. You're my only hope. If that mash-up of cultural references doesn't make sense, it will momentarily.

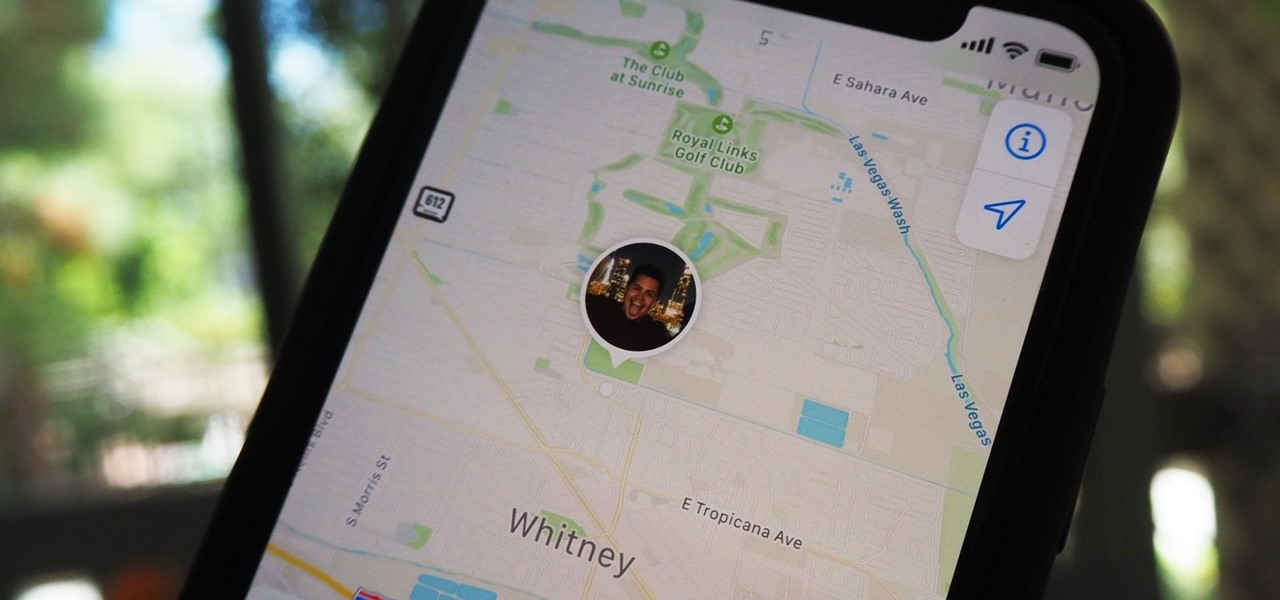
Sharing your iPhone's real-time location can be very useful when you want family and friends to know where you're at or your estimated time of arrival. By doing so, they can track you when you can't or don't want to update them manually. Depending on how you shared your location, however, they might still be able to track your exact coordinates after the initial share.

As protests surge in the wake of George Floyd's murder by a Minneapolis police officer, powerful photographs and videos from the demonstrations have gripped the world, putting our nation's very real and very justifiable widespread civil unrest out into the digital world. Unfortunately, these pictures could put you or others in danger if precautions aren't taken before uploading them online.

While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

The rise and fall of Meta, the Silicon Valley-based augmented reality startup that looked to challenge the likes of Microsoft's HoloLens, and others, took just six years.

Ever notice how some augmented reality apps can pin specific 3D objects on the ground? Many AR games and apps can accurately plant various 3D characters and objects on the ground in such a way that, when we look down upon them, the objects appear to be entirely pinned to the ground in the real world. If we move our smartphone around and come back to those spots, they're still there.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

1. The following Steps shows how to open a URL in a Web Browser, using a Button Click from a Flash Application. 2. Open a new Flash Application and place a Rectangle Shape from Tools and inside place a Text Box and Enter a Text named "URL". 3. Then convert it to Symbol by Right Click->Convert to Symbol and selecting type as Button. 4. Goto Button Properties and Name the button instance as "btnurl" 5. Then in the Action Screen Create a OnRelease() Event function for Button "btnurl" 6. use a me...

First you need a CRT TV, one Laptop, Headphone jack, Male and Female RCA jack, and output and input male female jack. And than one is audio cable and another one is video cable, and than connect it to your TV video out and audio out, and another one are connect to Laptops video out and audio out. And to get the video quality is good let set the Graphics property on your laptop and there are one option to TV set graphics and set them. And set the Screen Resolution and video stranded, and then ...

Expressions are new in SSIS (meaning that they were not in DTS) but they allow you to create extremely flexible packages. Expressions can be used to assign values to variables, help you determine whether to execute a task, and to assign properties. If you ever found yourself writing ActiveX code (VBScript) in DTS to determine which task to execute based on a variable's value, then you probably can forego the scripting all together in favor of expressions! They are very powerful in SSIS and yo...

This video shows you how to control your computer from your iPod touch. 1. Go to UVNC. Click on Installation. This will take you to download options. Download the latest stable version. 2. Install Hamachi, which helps you find your computer's IP address. Click on Download Here link, fill in the registration information, and click submit. 3. Install a VNC listener on your iPod so it can connect to your desktop. Jailbreak your iPod, and open the installer. Click All Programs; scroll down until ...

Wireless emergency alerts help warn mobile phone users of imminent threats to life or property, such as extreme weather and natural disasters. These alerts target affected geographic areas and come with a loud sound scary enough to make you want to turn off emergency alerts altogether on your iPhone, but there's a way to keep emergency alerts without the ear-splitting, intrusive sound.

Every single photo you take carries with it a considerable amount of seemingly "invisible" yet important information known as metadata. Although metadata is usually helpful to sort your photographs by location and date, that same information could potentially be used against you, especially if the pictures are taken during a precarious situation.

If you were upset about "Friends" leaving Netflix, fret no more. The entire series, all eight Harry Potter movies, as well as HBO's massive catalog, are now available as part of HBO Max. If you're already an HBO Now subscriber, however, it can be a bit confusing to know how to switch over to this brand new service. Here's how.

The "what (blank) are you" augmented reality filters on Instagram have become so popular that more and more Hollywood giants are following the augmented reality-powered social media meme train, with the latest example coming via Snapchat.

As fun as Twitter is, it can also quickly turn scary. Anonymous, aggressive, and troll accounts can attack you for your tweets and stalk your every move. While you could make your profile private and block users, there are lesser-known privacy and security features that you can switch to improve your safety online.

One Instagram creator's augmented reality homage to Disney's deep bench of animated characters has earned him fifteen minutes of fame.

The longer it takes Apple, Snapchat, Facebook, and other tech giants to build their own version of augmented reality headsets and smartglasses, the longer runway of practical experience Microsoft gains with the HoloLens and its sequel. The latest example: AR cloning.

With Microsoft taking direct aim at enterprises for its HoloLens 2 with a $3,500 price tag, one startup is betting that business will be willing to pony up for glasses-free 3D displays as well.

With Pokémon GO as its cash cow and the forthcoming Harry Potter: Wizards Unite and Niantic Real World Platform promising future revenue streams, Niantic has convinced investors to bet on its flavor of augmented reality

Every photo you take is brimming with metadata such as iPhone model, date and time, shooting modes, focal length, shutter speed, flash use, and geolocation information. Share these pictures with friends, family, or acquaintances via texts, emails, or another direct share method, and you unwittingly share your location data. Even sharing via apps and social media sites can compromise your privacy.

Magic Leap continues to launch new AR apps on its fledging app store before the door closes on 2018, and this time the app is a sequel from a veteran VR developer and early Magic Leap development partner.

Augmented reality gaming company Niantic Labs is now instigating conflicts between Pokémon GO players, but it's not as bad as it sounds.

Fresh off shipping an augmented reality game for Magic Leap, Resolution Games has farmed another $7.5 million in funding through a Series B round.

On Wednesday, the tech world woke up to fairly shocking news with the announcement that AT&T would be the exclusive wireless carrier for the forthcoming Magic Leap One, as well as an investor in Magic Leap.

Last month was a whirlwind for the augmented reality industry, with the Augmented World Expo, Apple's Worldwide Developers Conference, and an exciting Magic Leap Twitch livestream all wrapping up before the ides of June. Now that we've had a chance to fully digest it all, we have a real sense of where the augmented reality industry is heading.

A new study published by American University demonstrates how Pokémon GO and other augmented reality games can help city governments bring communities closer together.