In this chapter, we want to start seeing some real progress in our dynamic user interface. To do that, we will have our newly crafted toolset from the previous chapter appear where we are looking when we are looking at an object. To accomplish this we will be using a very useful part of the C# language: delegates and events.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

One major component of Level 4 and Level 5 driverless cars is in very short supply. Venture capitalists and engineers from around the world are racing to fill the LiDAR production, price, and performance void.

Welcome to the final tutorial of the series on standard C. This article will cover the linked list abstract data type (ADT). There will be a lot of abstraction to try to deliver the understanding in the most basic way for easiest interpretation of what they are and how they work, then we will get into the guts of it and learn the technical code underneath. For those who have yet to grasp the concept of pointers, it's advisable that you do that first before approaching this. Having learned thi...

When you hand your unlocked iPhone to somebody so they can use the internet real quick, check out some cool photos, or do whatever, there's a possibility that they could snoop around where they don't belong. If you have some secret recipes, login credentials, intellectual property, or other sensitive information in your notes, you'll want to add some protection to them.

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

You either love kimchi or you hate it, but for those of us who love it, its salty, briny, spicy crunch is the stuff of life. Honestly, if you're not eating it regularly, you should start, since it's being studied for an amazing list of health benefits, including anti-cancer, anti-aging, and antioxidant properties; obesity and high cholesterol prevention; and promotion of immunity and skin health. The beauty of kimchi is manifold:

The world of spices can be bewildering. They promise to make your food more flavorful if you know how to make the most of them. Unless you know a couple of essential tricks, however, it just seems like you're adding bits of colored powder to your food.

In case you haven't heard, chia seeds are off of the novelty plant grower and in your supermarket. Why? Because they're a nutrient-dense food loaded with calcium and fiber (18% and 42% respectively of your RDA per one ounce of seeds). There are even some preliminary studies that show chia might be useful in combating diabetes.

If you've been to a farmer's market during tomato season, chances are you know that heirloom tomatoes are pricier (and funnier-looking) than their hybrid counterparts.

It has been a long while since I last came here to write an article. Graduate school keeps you busy. After I looked over what I had written previously, I decided that I should introduce another fun topic from cryptography. In this case, steganography.

Chances are that you've been using your microwave just to nuke leftovers, but they can do so much more than heat up last night's dinner—microwaves can help you peel garlic more quickly, get more juice out of lemons, disinfect your kitchen, dry out herbs, give beauty products new life, cause exciting explosions, and even arc weld.

About ten years ago, Western research figured out that green tea was a nutritional powerhouse. After all, in Asian countries where green tea is consumed throughout the day, cancer rates tend to be much lower, although there are probably other factors contributing to that fact, like less processed food and red meat in the standard Asian diet.

Even as someone with super pale skin that burns instead of tanning, I don't use sunscreen nearly as often as I should. Or, uh...ever. My skin cancer prevention routine mostly involves hiding from the sun as much as humanly possible. If you're like me and hate the greasy feeling of sunscreen, there are other ways you can protect your skin by increasing your sun tolerance. Your diet actually has a lot to do with how easily you burn, so by getting enough of a few key nutrients, you can decrease ...

Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely.

All kinds of people pretend to be someone they're not on the internet, including scammers, people attempting to wind others up, hackers and web predators. Almost all of these people will leave bases uncovered and they're all easy to expose when you understand how to. Here are my favorite ways of finding out when somebody is lying quickly. Image Search

The makers of arguably the two most important mobile AR apps, Niantic and Snap, both had good news this week, with the former preparing to replicate its success with Pokémon GO for another franchise and the latter notching another popular augmented reality Lens for Snapchat.

Since iOS 13, your iPhone's come equipped with a fonts manager that lets you install custom fonts for use in Apple apps and supported third-party apps. To add fonts, you need to use a font provider app that'll load them on your device and register them system-wide, and one of these apps shines above all else.

Sure, Microsoft has mostly marketed its HoloLens headsets towards enterprises and developers, but we learned this week that, like every other tech giant, the company is working on a consumer-grade AR wearable. Speaking of consumer smartglasses, Apple made another strategic investment this week that has implications for Apple's AR future.

Thanks to the grandest of puns, May the 4th is Star Wars Day. And what better way to pay tribute to the space opera than with the augmented reality superpowers of Snapchat.

There's already some fierce competition between Snap and Facebook in the AR space, but it's about to heat up even more, with Snap snatching up a 3D mapping startup that could add some new AR capabilities to its arsenal.

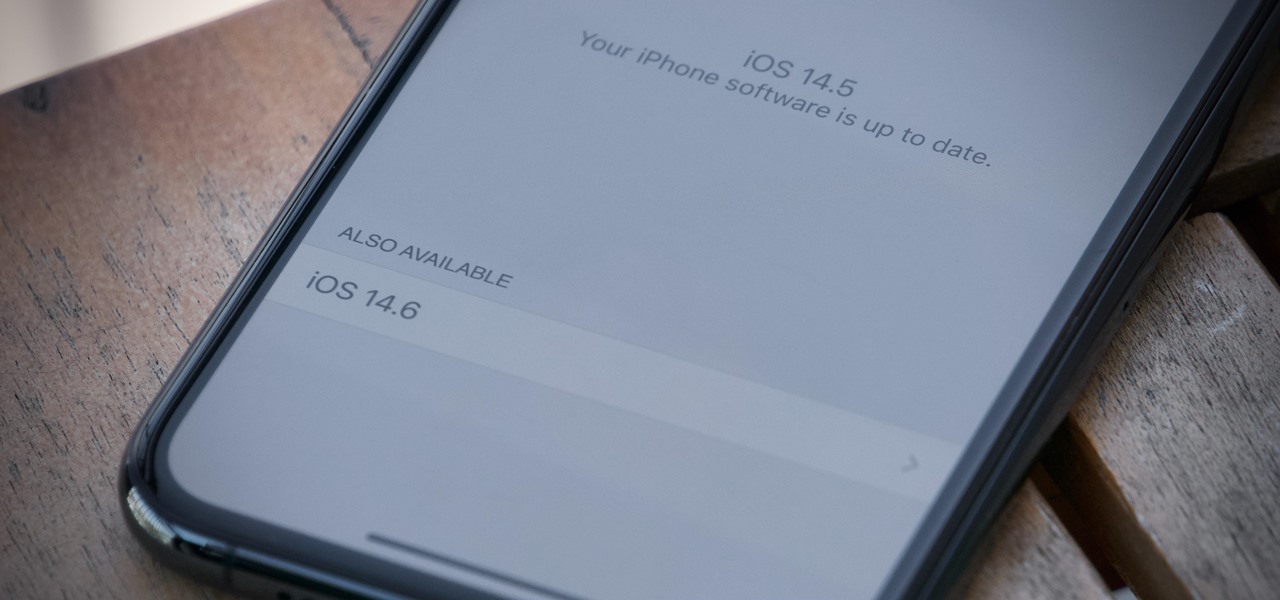
Apple released the first public beta for iOS 14.6 today, Friday, April 23, one day after the company seeded iOS developers 14.6 beta 1. The update introduces an easy way for testers to update from an iOS RC (release candidate) to the latest beta, via a simple option in Software Update.

Apple released the first beta for iOS 14.6 today, Thursday, April 22. The new beta (build number 18F5046e) comes just two days after Apple's spring event, as well as the iOS 14.5 RC, and features an easy way for beta testers to update to the latest beta software when running an RC.

The augmented reality industry has grown steadily over the past four years, but now it is on a collision course with uber-popular non-fungible tokens technology, with Looking Glass and music artist Reggie Watts among the latest to strike while the iron is hot.

We often discuss the augmented reality efforts coming from the biggest players in Silicon Valley like Google, Facebook, Apple, and others, but one name that keeps coming up when you really begin to dig into the AR space is Vuzix. Since the late '90s, the company has quietly but deliberately worked to build itself into a viable competitor in the enterprise space via its wearable display technology.

It's Black Friday time, and in 2020, that means a lot of online deals to make up for more stores closing on Thanksgiving, as well as everyone avoiding in-person shopping because of the coronavirus. But while you may wish to grab a better 65-inch 4K TV, the new PlayStation 5, or some hacker hardware on sale, Black Friday is also the best time to invest in your programming and cybersecurity education.

It's almost impossible to use Apple News at night without having to mess with the white point and zoom filters. That might sound a bit dramatic, but it's really not when you consider that iOS 13 has a perfectly good Dark Mode that should work for News. So why are we stuck reading most news stories in Light Mode? We're not, but you have to put a little work into it going dark in News.

Many apps on your iPhone want to use your location, most of which are for valid reasons. But some apps can function perfectly fine without location permissions, while others have no business even requesting it. If you want to be more selective about which apps and services you give away your coordinates to, the best thing you could do is start from scratch.

A modern iPhone is capable of running sophisticated, exquisitely-rendered games that rival titles on current-generation consoles. However, there is some value in classic video game titles, whether you grew up playing games on the Atari 2600, Nintendo Entertainment System, and Sega Genesis or not.

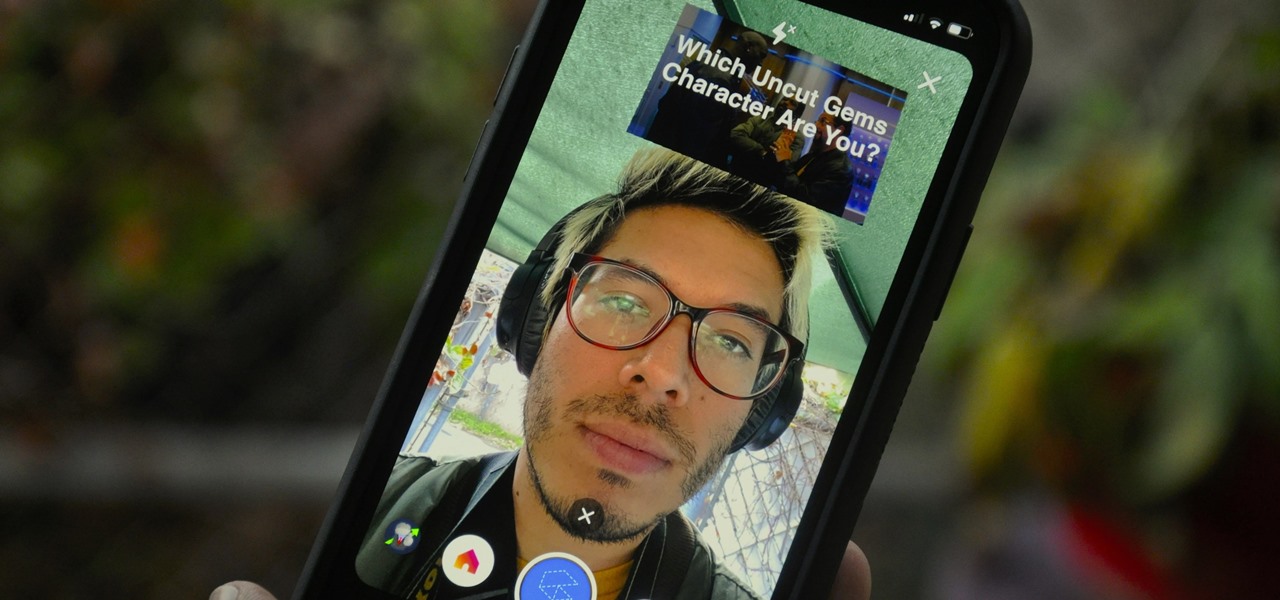
There's a new trend on Instagram Stories: People are making viral AR filters where images of popular characters from TV shows, movies, and other mediums shuffle above your head until one sticks. The filters range from Disney and Pokémon characters to Harry Potter and Friends, but you're not limited to just that because you can create your own "which are you?" filter.

Over the past decade, Marvel Studios has been a dominant force at the box office, raking in more than $21 billion dollars. Averaged out over that span of time, the yearly earnings of those movies outweigh the gross domestic product of some countries.

OnePlus will be releasing a new phone in the second half of 2018, specifically, an upgrade to their T-series. Over the past two years, #T versions have come out about five months after their predecessors and have included small updates that fix any problems from the previous OnePlus device. While we do know a bit about OnePlus 6T, what it could be is much more exciting.

The gig economy is thriving, and if you aren't already making money with your phone, you could be missing out on easy residual income. Some people just want extra cash, and some even manage to completely ditch the 9–5, enabling them to work at their own pace and set their own hours.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

When you can't reach your iPhone or don't have it on you, how do you get help from emergency services? Unless you have one of those life-alert mobile triggers, someone nearby, or some amazing telepathy skills, hope might be the only answer — unless you wear an Apple Watch, that is.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn a Raspberry Pi into a router running through PIA VPN, which will ensure every connected device gets the VPN treatment.

From Farmville to selling a company to Google, Amitt Mahajan has been through the startup ringer. Now, as managing partner with Presence Capital, he's funding the future of augmented and mixed reality.