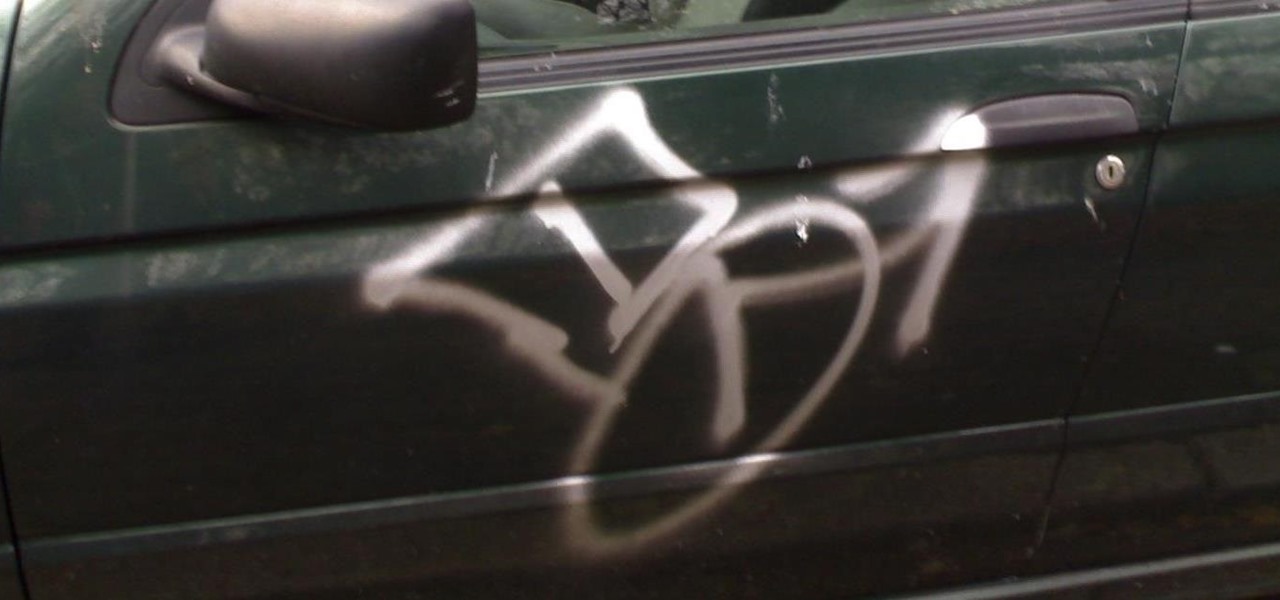It's nearly impossible to keep a stovetop clean when cooking, at least, in my experience. No matter what I do, liquid and solid food bits fall to the surface and around the burners every single time, creating a hard-to-clean mess.
For those times when you can't get something done by clicking a few buttons with your mouse, the Windows command prompt has always been an indispensable tool. But as much as advanced users have relied on this useful utility, it hasn't seen a significant update since the Windows 95 days.
As familiar as it may look at first glance, there are still tons of subtle changes in Windows 10. Many options that existed in past versions have been moved, and virtually every system menu received at least a small visual makeover.
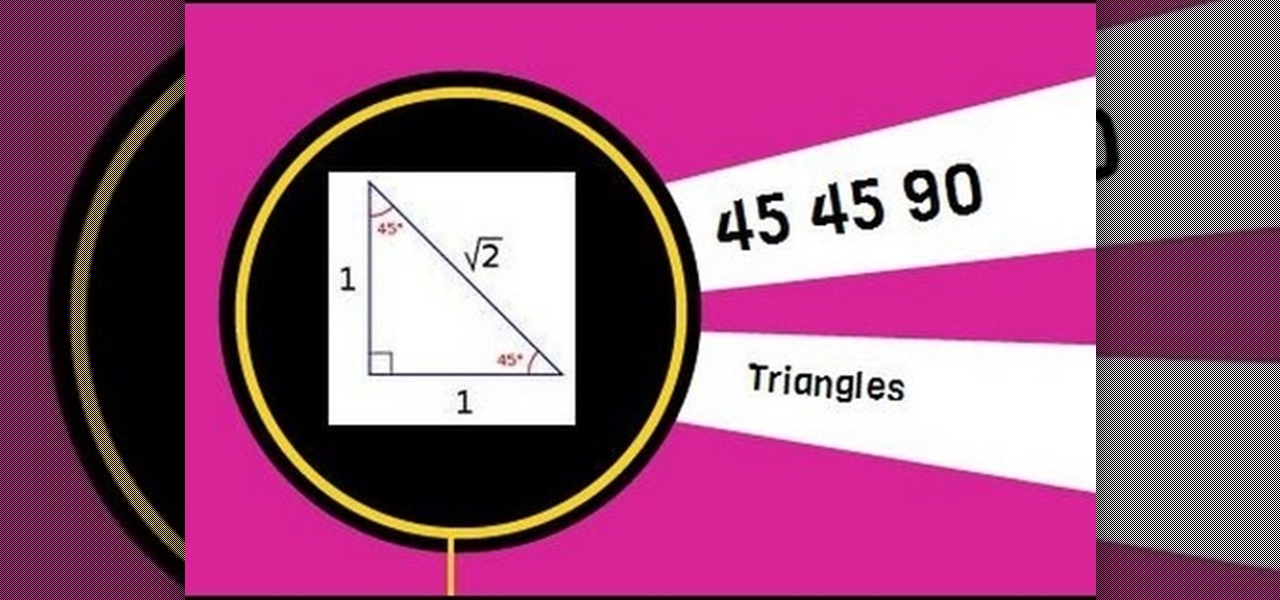
A 45 45 90 triangle is a special right triangle because you can use short cuts to find leg length and hypotenuse length. This video solves two problems involving leg length and hypotenuse length.

Since the days of Android Jelly Bean, Samsung has implemented an energy preservation feature known as dynamic voltage and frequency scaling, or DVFS for short. What this essentially does is limit or adjust the frequency of the microprocessor to conserve power and prevent excessive heat from being generated.

I spend a lot of time helping friends and family with their tech problems, like clearing a browser's cache, scanning a Windows computer for malware, and speeding up a Mac. However, the issue I deal with most frequently revolves around forgotten network passwords.

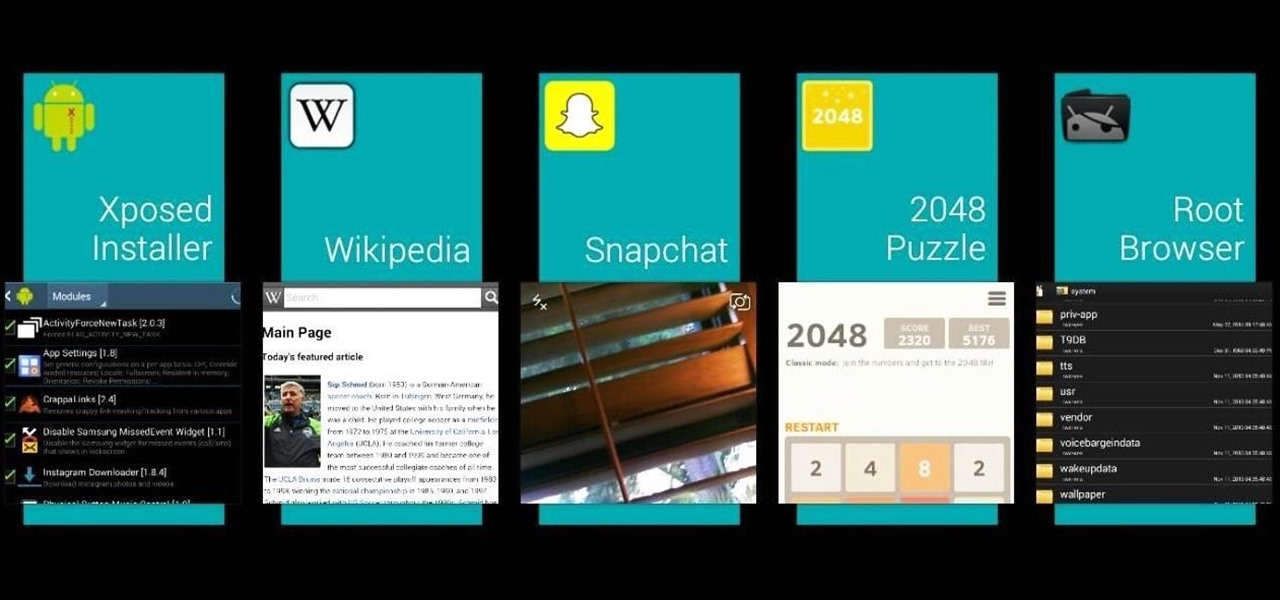
Having an open-source platform like Android is great, allowing manufacturers and developers the ability to make their own skins and apps to truly customize the end-user experience. The only downside is that when an update comes to vanilla Android, many of us are left in the cold, unless you have a Google Play Edition HTC One.

Transparent status bars and new lock screens weren't the only new additions that came with the Galaxy S3 KitKat update. Along with better battery life and a smoother user experience, we got a new toggles design and recent apps menu. Of course, Samsung's infinite wisdom left these two aesthetic features hidden away. Luckily, with root, you can easily enable them with just a few quick edits.

The old "my battery is dead" excuse for not calling your mother may soon be a thing of the past. A team from the Korea Advanced Institute of Science and Technology (KAIST), led by Professor Jo Byeong-jin, has developed a "wearable thermo-element" that can be built into clothing to power your electronic devices. The science behind the innovation converts body heat (thermal energy) into usable electric energy. Made with lightweight glass fiber, this small thermo-element strip can produce about ...

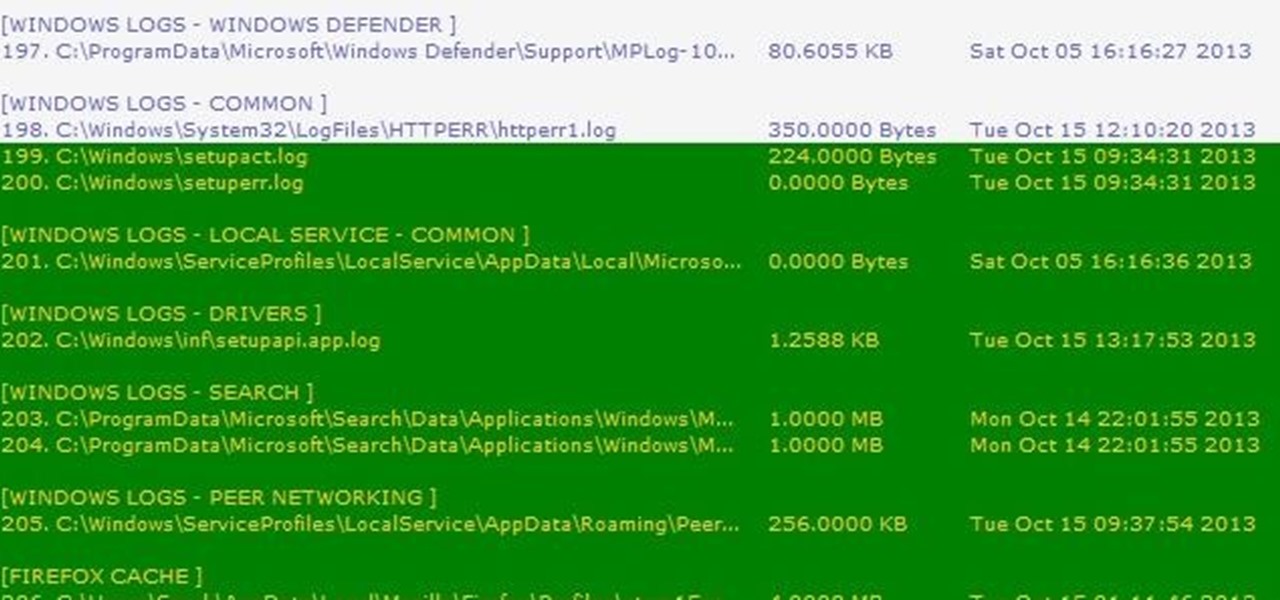
Thousands of history files, cookies, other unwanted files stored in your system as logs and other formats. To manually check each one is difficult. New computers are too fast by processor behavior, after some times of working it comes to slow performance.

There are some really talented graffiti artists out there. Some of them are good enough that businesses hire them to paint advertisements, rather than hiring someone to scrub their work off the side of the building.

There are very, very few things better than a solid Hobbit songI mean, I was almost brought to tears when Pippin busted out this one in The Lord of the Rings: Return of the King.

Microsoft's updated web browser, Internet Explorer 10, has only been out for a few days on Windows 8, and there is already a storm of controversy surrounding its launch.
I've noticed that a few people using the crypto-currency, Bitcoin are having issues importing private keys to their Bitcoin wallet. This is easy to do and doesn't require anything other than your Bitcoin client/daemon (as of ver0.6.0 ) and the command line.

1. The following Steps shows how to open a URL in a Web Browser, using a Button Click from a Flash Application. 2. Open a new Flash Application and place a Rectangle Shape from Tools and inside place a Text Box and Enter a Text named "URL". 3. Then convert it to Symbol by Right Click->Convert to Symbol and selecting type as Button. 4. Goto Button Properties and Name the button instance as "btnurl" 5. Then in the Action Screen Create a OnRelease() Event function for Button "btnurl" 6. use a me...

First you need a CRT TV, one Laptop, Headphone jack, Male and Female RCA jack, and output and input male female jack. And than one is audio cable and another one is video cable, and than connect it to your TV video out and audio out, and another one are connect to Laptops video out and audio out. And to get the video quality is good let set the Graphics property on your laptop and there are one option to TV set graphics and set them. And set the Screen Resolution and video stranded, and then ...

4 things you MUST do for a successful deer management program. A successful program means healthy deer and great hunting!

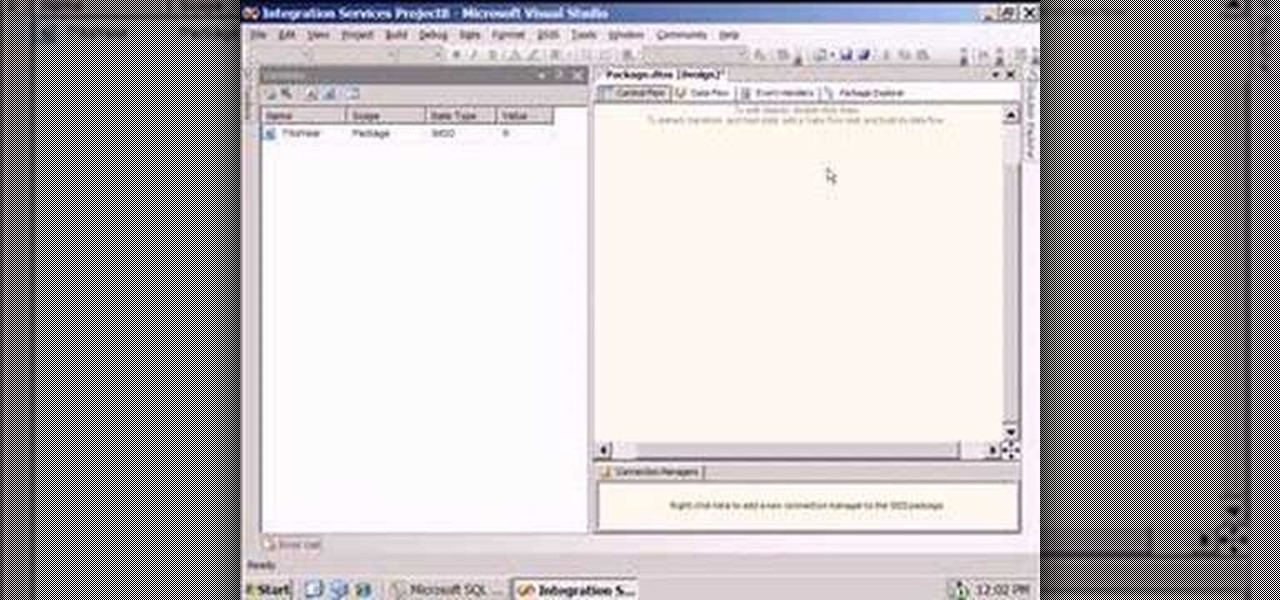
Expressions are new in SSIS (meaning that they were not in DTS) but they allow you to create extremely flexible packages. Expressions can be used to assign values to variables, help you determine whether to execute a task, and to assign properties. If you ever found yourself writing ActiveX code (VBScript) in DTS to determine which task to execute based on a variable's value, then you probably can forego the scripting all together in favor of expressions! They are very powerful in SSIS and yo...

In this online video series learn from power tool expert and Industrial Technology teacher Jon Olson as he teaches and demonstrates how to use and maintain the power screwdriver. Learn important power tool tips and techniques such as construction work area safety, electrical safety, how to use the chuck on a power screwdriver; how to use a power screwdriver; tool maintenance; battery tool use and care; how to use the torque adjustment collar; how to drive a screw at an angle; how to use the v...

Help me, George Clooney. You're my only hope. If that mash-up of cultural references doesn't make sense, it will momentarily.

While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

The rise and fall of Meta, the Silicon Valley-based augmented reality startup that looked to challenge the likes of Microsoft's HoloLens, and others, took just six years.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

In this video series on how to play French horn, learn basic tips and techniques for playing this brass instrument, including how to hold the horn, form proper embouchure, and changing pitch using your lips, the rotary valves, or by putting your hand in the bell. Also learn some intermediate French horn skills involving orchestral music, like how to play slurs, legato, glissando, staccato, and accent notes. Finally, get some practical care and maintenance tips for your horn, as well as some b...

In this do-it-yourself motorcycle maintenance course on video, learn how to fix and repair your hog, so that you can ride cross country without having to stop in at a mechanic. The ultimate riding experience is characterized by freedom and independence: to be in charge of your ride and in control of your bike. So get tips on tire and brake care, how to change motorcycle spark plugs, replace the air filter and change the oil, adjust the primary chain, and other common bike repairs you’ll need ...

In this video series you'll learn how to use a brad nailer from expert Jon Olson. He demonstrates how to lubricate, prepare and load the nail gun, how to deal with a jam, how to set the nail depth and pressure, and basic tool safety. He also shows you how to identify the different parts of the finishing nailer, and how to perform daily maintenance and more.

A chop (or miter) saw is a power tool used to make accurate cross cuts in wood, plastic, and light metals. It has a fixed blade, attached to a moving arm, that spins over a small worktable. The operator lines up the piece to be cut and drops the saw blade, allowing for quick, easy work. Watch this instructional video series, and decide if the chop saw is a tool you'd like to introduce into your workshop. Lessons include general safety tips, uses for the chop saw, replacing the cutting saw bla...

For a car to operate normally, it must have some basic care and maintenance. In these automotive repair videos, learn how to maintain your engine cooling system. The cooling system keeps your car from overheating on the road; a lot of heat is generated by an internal combustion engine, which must be properly dissipated. Our expert will show you how to not only spot and remove the heater core hose in a car but how to determine what is wrong with it, change it if needed and reassemble the vehic...

In this series of instructional videos, expert Jon Olson demonstrates how to use a random orbit sander, including tips on how to create bevels, replace discs and brushes, empty the dust bag and general cleaning, care and basic maintenance of the tool. He also covers tool safety, including electrical safety, personal safety, such as wearing protective eye gear, tips for sanding paint and the importance of keeping your woodworking work space clean. Watch this free online tutorial and you'll att...

This video shows you how to control your computer from your iPod touch. 1. Go to UVNC. Click on Installation. This will take you to download options. Download the latest stable version. 2. Install Hamachi, which helps you find your computer's IP address. Click on Download Here link, fill in the registration information, and click submit. 3. Install a VNC listener on your iPod so it can connect to your desktop. Jailbreak your iPod, and open the installer. Click All Programs; scroll down until ...

Wireless emergency alerts help warn mobile phone users of imminent threats to life or property, such as extreme weather and natural disasters. These alerts target affected geographic areas and come with a loud sound scary enough to make you want to turn off emergency alerts altogether on your iPhone, but there's a way to keep emergency alerts without the ear-splitting, intrusive sound.

As NASA nears the launch of another mission to the Moon in 2024, and a subsequent mission to Mars in the 2030s, augmented reality is increasingly being woven into the normal space operations to test various capabilities.

You only 'thought' the HoloLens 2 was the most expensive augmented reality device on the market. As with many things tech, Japan is here to up the ante with what may indeed be the most expensive AR-dedicated wearable we've seen—the Canon MREAL S1.

While most established media brands are satisfied with copying Pokémon GO to jump into augmented reality gaming, at least one property is taking a slightly different approach.

Good communication is essential when managing teams and overseeing complex projects. Whether you're developing the latest and greatest app or trying to get ahead of a large data science project, effective communicators are always in high demand.

In the coming years, artificial intelligence (AI) will revolutionize every facet of technology and business. AI researchers are in high demand. Salaries in this field are regularly in the hundreds of thousands of dollars.

If you were upset about "Friends" leaving Netflix, fret no more. The entire series, all eight Harry Potter movies, as well as HBO's massive catalog, are now available as part of HBO Max. If you're already an HBO Now subscriber, however, it can be a bit confusing to know how to switch over to this brand new service. Here's how.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

The "what (blank) are you" augmented reality filters on Instagram have become so popular that more and more Hollywood giants are following the augmented reality-powered social media meme train, with the latest example coming via Snapchat.

One Instagram creator's augmented reality homage to Disney's deep bench of animated characters has earned him fifteen minutes of fame.