OnePlus will be releasing a new phone in the second half of 2018, specifically, an upgrade to their T-series. Over the past two years, #T versions have come out about five months after their predecessors and have included small updates that fix any problems from the previous OnePlus device. While we do know a bit about OnePlus 6T, what it could be is much more exciting.

| Updated Aug. 22, 2019 with new phones. When will my phone get Android Pie? For the first time since Android's inception, this question shouldn't have an answer that lets you down. That's because Android Oreo introduced Project Treble, a new low-level arrangement that makes updating a lot easier. So with Pie, it's not if your phone will get it, but when.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

One feature in iOS you're likely underutilizing is 3D Touch, a highly useful, unique tool for iPhones ever since it first appeared on the iPhone 6S. Apple's pressure-sensitive interactivity gives iOS an extra layer of functionality, which can be clearly seen across the entirety of your device. From the lock screen to the home screen to the apps in between, there are plenty of ways to use 3D Touch.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn a Raspberry Pi into a router running through PIA VPN, which will ensure every connected device gets the VPN treatment.

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

Despite legends to the contrary, it appears that the saliva of a Komodo dragon is not teeming with pathogenic bacteria that kills their prey. Its reputation to survive while colonized with lots of horrible disease-causing bacteria, true or untrue, has made it the subject of research in pursuit of natural antimicrobial agents and led scientists to some remarkable findings.

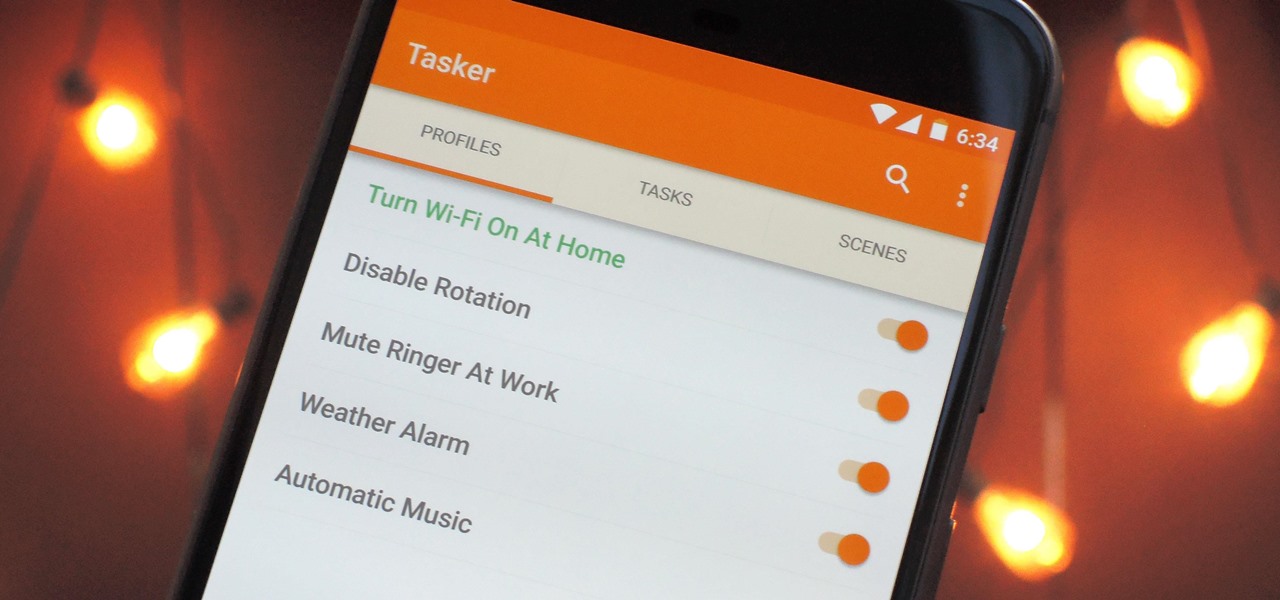
When it comes to automation apps on Android, Tasker is still the king of the hill. For a price of $2.99 on the Google Play Store, it's a great buy for any would-be tinkerer that would like to get into automating actions on their Android device. Then, when you consider that there's a free 7-day trial version available, there's almost no reason that you shouldn't at least test the waters with Tasker.

There is much to be learned about Apple Music and the revamped Music application introduced in iOS 8.4. Throwing their hat into an already competitive field with other companies like Spotify, Tidal, or Rdio, this is a bold move on Apple's part. So, before you consider signing up for the new streaming service, let's take you through all the changes and features you should know about before doing so.
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started.

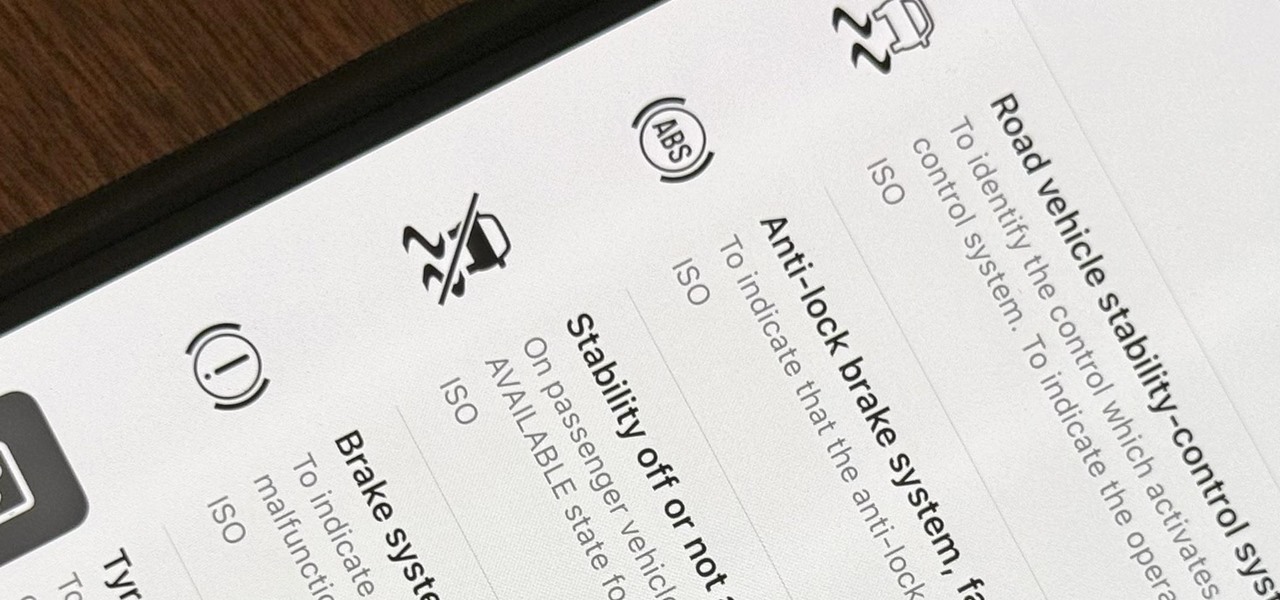
When you encounter a mysterious laundry care symbol or alarming vehicle indicator light, you might just ignore it rather than ask somebody, search online, or open a user manual for the answer. If you have an iPhone, there's an easier way to decipher the meanings behind perplexing symbols and signs—and it only takes a few seconds.

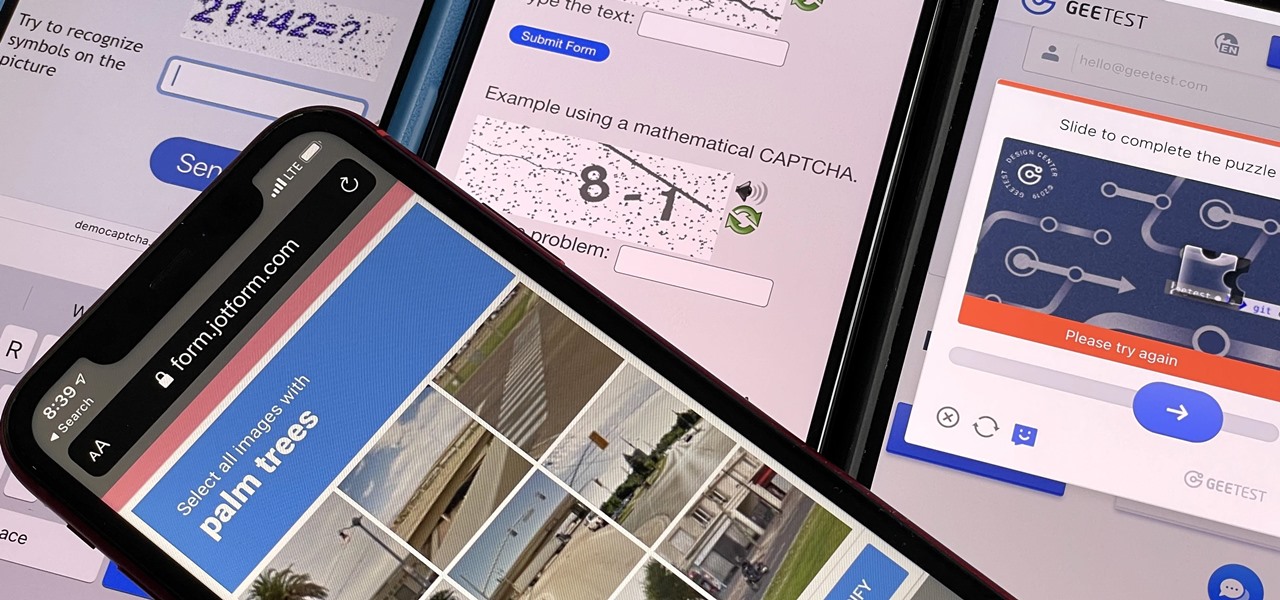
Some websites require you to perform a verification task so they know you're human and not a bot. It helps websites curb spam, abuse, unauthorized access, and cyberattacks but also adds an obstacle for anyone trying to visit their content. If you find it more of a nuisance than a necessary evil, there's an easy way to reduce the number of human verification prompts you receive on your iPhone, iPad, and/or Mac.

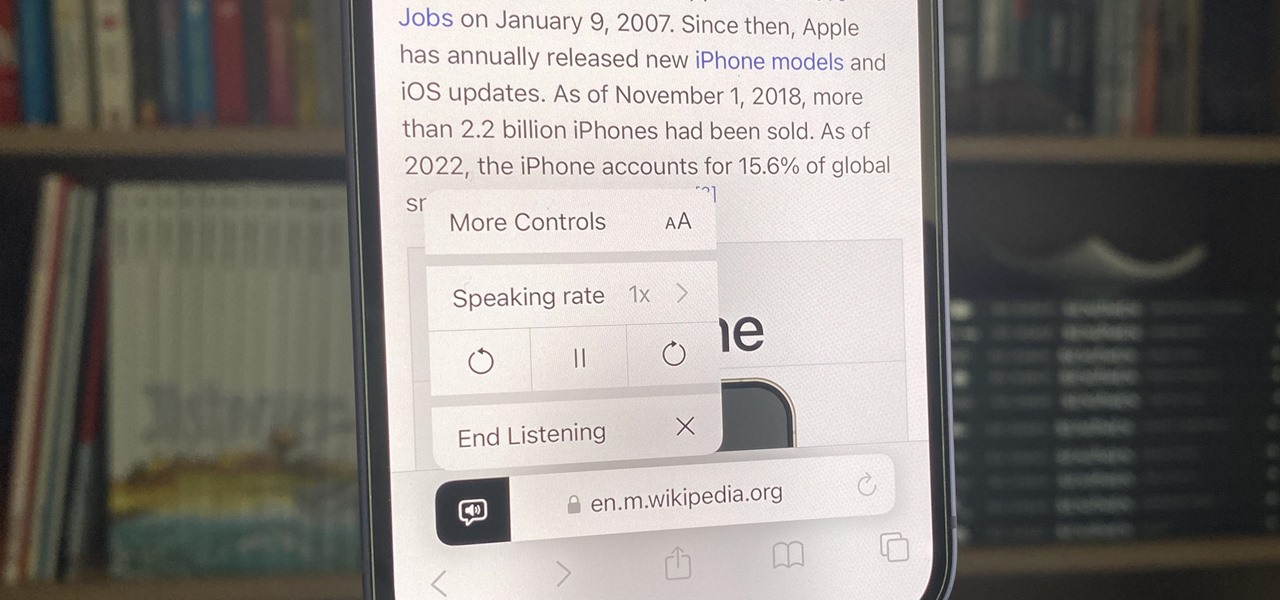
Speech-to-text technology can be seen on your iPhone in various places, from the Dictation tool to Apple's new behind-the-scenes, auto-created transcripts for podcast episodes. Your iPhone also has some pretty impressive text-to-speech capabilities. With them, your iPhone can read webpages, documents, or whatever text is on the screen out loud to you — only some of these tools aren't easy to find.

Apple just released its iOS 16.6 update for iPhone on July 24. When you install the new software, it may look like there's not much to it since Apple doesn't include any features in the release notes beyond "important bug fixes and security updates," but a few new features are hiding within.

Spotify lets you customize some aspects of your experience, whether on the desktop, web, Android, or iOS app. And one of the simplest yet coolest customizations you can perform is changing your playlist cover images. However, it doesn't work on all playlists.

The screenshot tool on your iPhone can come in handy in various ways, but it may be even more helpful than you realize. So if you thought you knew everything there was to know about your iPhone's screenshot tool, it's time to put your knowledge to the test.

There's a little-known secret in the world of microwave ovens that even the manufacturers don't care to tell you in their manuals. And once you know it, you'll never go back to using your microwave as you used to.

Unless you have unlimited cellular data, you probably connect your iPhone to every Wi-Fi network you come across. It could be a local coffee shop, public library, or just a friend's place. Wherever it is, you'll need to ask for the access point's password if it's a secured network, and that can be a hassle if the place is busy or the owner forgets the credentials. Luckily, Apple has a solution for this problem.

Wordle has been popping up all over in the app stores, but none of them are the real Wordle. The popular word game app has amassed two million users since its launch in November 2021 but has no plans to hit the iOS App Store or Play Store any time soon — but you can still install the official Wordle app on the Home screen of your iPhone or Android phone.

I drop my smartphone a lot. Like an absurd amount of times. Practically multiple times a day. So it's surprising that my iPhone 12 Pro has lasted nine months without a cracked screen yet. Part of that has to do with the late-2020 model's durability, and the other part is thanks to my protective case.

Apple released the second beta for iOS 15 on Thursday, June 24. The update includes FaceTime's "SharePlay" feature for the first time, a new Maps icon, updates to Focus mode, in addition to many other changes and bug fixes.

Apple released the second Release Candidate for iPhone on Friday, May 21. The new update, build number 18F72, comes four days after the company seeded the first 14.6 RC to developers and public testers, and two days after the first beta for iOS 14.7.

Apple pushed out the Release Candidate for iOS 14.6 on Monday, May 17. The 18F71 build includes new features and bug fixes, including an option to unlock your iPhone with Voice Control. It comes just hours after Apple announced Spacial Audio and Lossless Audio playback for Apple Music, new features that will require iOS 14.6 to run.

Apple has a sterling reputation when it comes to managing its supply chain; it's where CEO Tim Cook proved his mettle to succeed Steve Jobs. Now, the company has made a strategic investment with a supplier that will be crucial to its future plans for AR wearables.

Apple just released the second public beta for iOS 14.5 today, Wednesday, Feb 17. The update comes just one day after the company seeded developers the second 14.5 beta. Because of that, we've had 24 hours to sink our teeth in beta 2's new features, like 217 new emoji, Apple Music lyric sharing, Apple Music UI updates, and new Shortcuts options.

Apple released the second developer beta for iOS 14.5 on Tuesday, Feb. 16. The update comes 15 days after Apple seeded developers the first 14.5 beta, which included a slew of new features such as default music app support, compatibility with PS5 and Xbox Series X controllers, and more.

Apple wants to support the advertising economy, but its primary focus of late has been user privacy and security. In Safari, cross-site tracking, which lets content providers track you across websites and apps to show you more targeted ads, is disabled by default. However, content providers can get around that using less privacy-invasive ad measurements, but you can stop that too in iOS 14.5.

The iOS 14.4 developer beta was pushed out a day ago, and now the iOS 14.4 public beta is out and ready for your iPhone. At first glance, there's not much to look at in the new beta release, and it's not yet known if it lays out the groundwork for missing features such as 5G data with dual SIMs, shared third-party app subscriptions, and Xbox Core Controller.

The next big phase of iOS 14 has started with the release of the iOS 14.4 beta. Right now, the developer-only beta features only one known item. Apple introduced the ability to scan App Clip Codes in iOS 14.3 with the Code Scanner control, and now in iOS 14.4, you can launch a local App Clip experience via Camera, NFC, Safari Smart App Banner, or iMessage.

We're still awaiting the arrival of consumer-grade AR smartglasses from the likes of Apple and Facebook. But that doesn't mean there aren't AR products out there to try this holiday season.