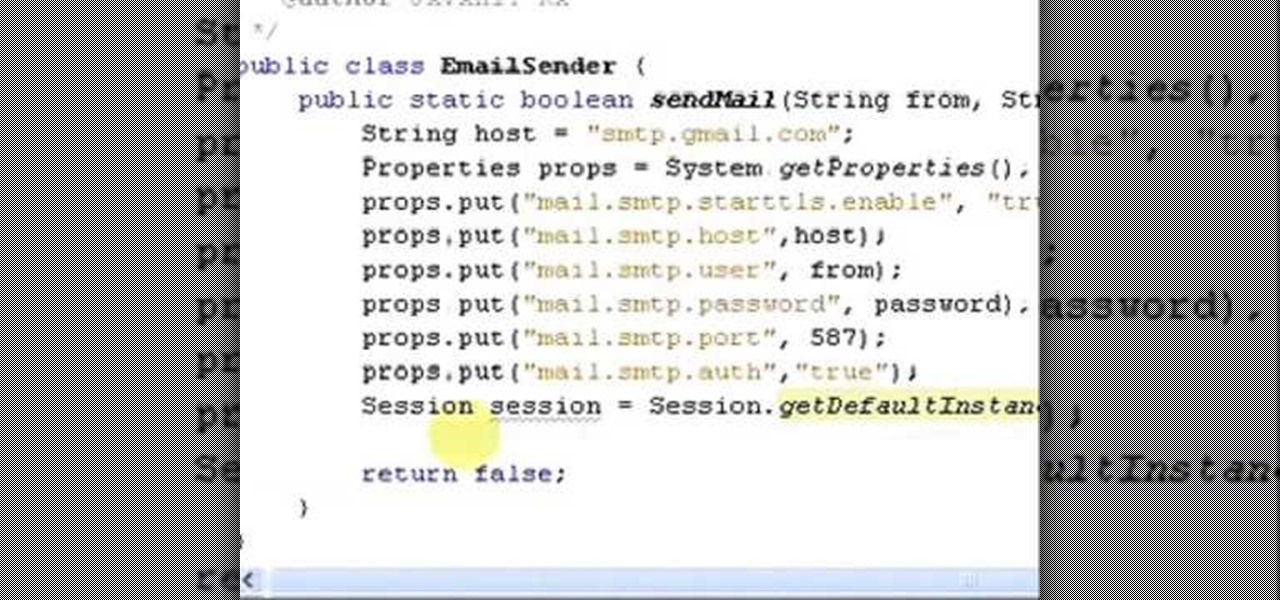
How To: Send eMail Using Java
It uses JavaMail API, NetBeans IDE 7.0.1 First download the JavaMail API as shown in beginning of the video then follow the video to send email dynamically from your Gmail account. No need to open your inbox.


It uses JavaMail API, NetBeans IDE 7.0.1 First download the JavaMail API as shown in beginning of the video then follow the video to send email dynamically from your Gmail account. No need to open your inbox.

In this web design tutorial we will show you how to protect yourself from losing your work just in case the program malfunctions, computer crashes or you accidentally forget to save document and so on. I highly recommend you utilize this Web Design Tutorial especially if you are working on large websites for clients.

Get your numbering straight with Adobe's InDesign and this helpful tutorial, showing you what you need to know. It's essential when creating a project for yourself or a client, to get your numbering right the first time. There is no second chance. So, check out the steps and see how to turn this sometimes tricky task into a much easier one. InDesign offers a lot of options, and if you're going to master all it's tricks, watch this how-to to learn one of the most simple and essential tricks.
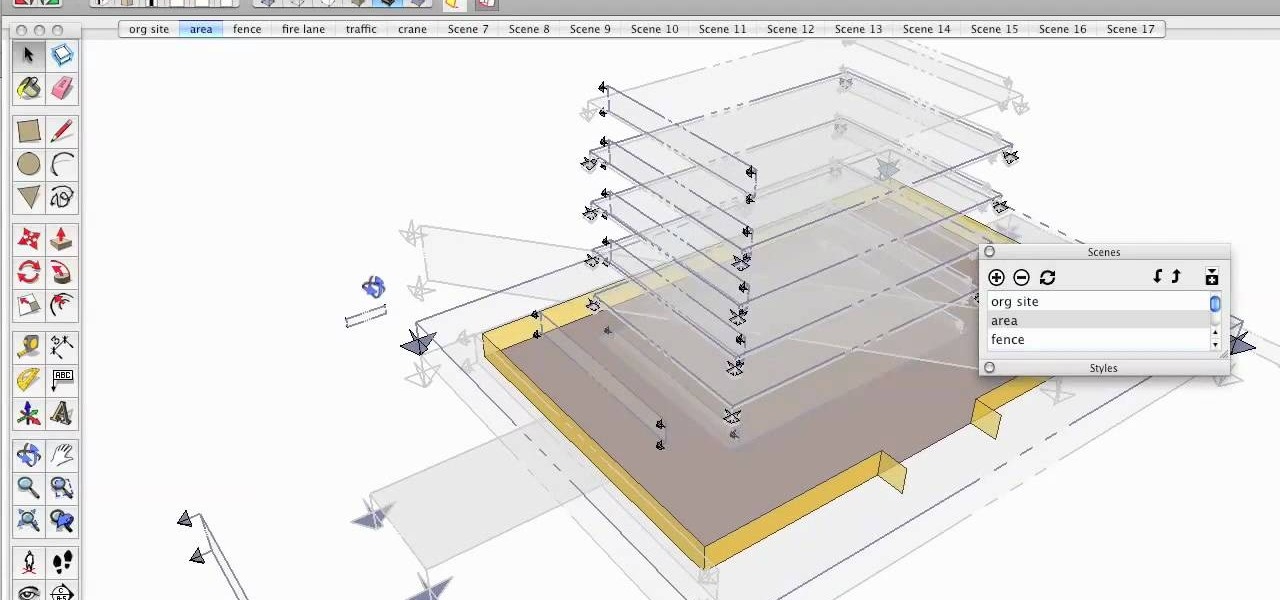
As you already know, Sketchup is a very cool program which allows you to design a myriad of things. But, did you know you can then animate those images? You can, and this tutorial will walk you through the steps to show you how. This is a very valuable thing to know if you're presenting something to a class, or client and want to show them the developmental stages of the project. So check out this video, get designing and put those pictures into motion!

If you think about it, your face is just another canvas, with makeup being the paint. You add highlights here to bring parts you want to emphasize forward, bronzer there to create fake shadows, and draw on patches of color (lips) or lines (eyes) to make things either pop or recess.
If you're a graphic designer, you've probably dealt with clients who sent you the wrong files, like JPG and BMP "source" files. You need to the EPS vector files, but they don't know what that is, and they don't care. They want that image or logo they sent you blown up to poster size for a billboard or something.
Today, BitTorrent Inc. released the SDK for uTorrent Apps, which will allow software developers from around the world to create Apps for uTorrent, the popular bittorrent client. This video will show you how to download the SDK, install it on your computer, make an app, view that app in a browser, and then package the app and view it within uTorrent without compromising uTorrent's famous lightness. This is a big day for bittorrent fans around the world; download the SDK and start making uTorre...

There are a couple of limitations that Microsoft put in to Windows 7 upgrades that can prevent users from upgrading and ultimately force them to do a clean install. First limitation is that they won't let you to upgrade Windows 7 if you run Windows 7 release candidate that was released earlier this year, which they won't let you to upgrade to a download Windows edition. If you are running Windows vista ultimate you cannot upgrade windows 7 professional. We have to buy an ultimate edition then...
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.
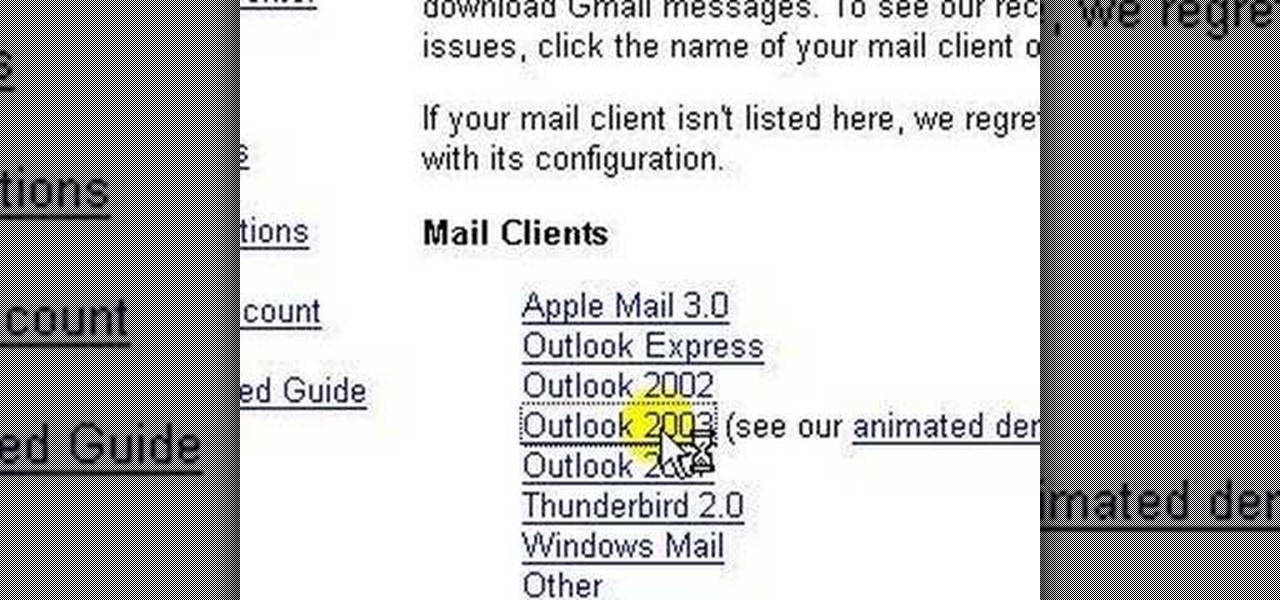
lakercoolman shows us how to set up our gmail account with this quick tutorial. Basically outlook express is a program that helps us to organize our email with added features such as contacts, to do lists and calender entries. Its an offline email client that allows us to work offline and also lets us set up exchange servers aswell. Ohter email servers such as hotmail and yahoo charge for thios service but the advantage of gmail is that IMAP or POP access is free. in ofer to set up, navigate ...
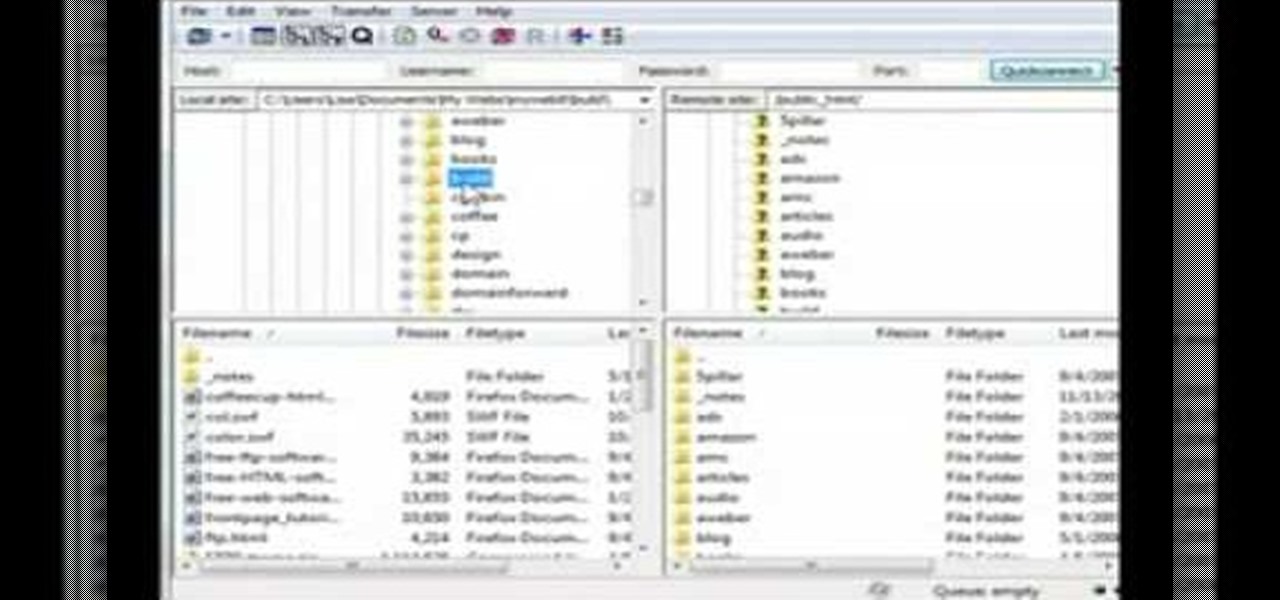
This video describes that how to use the file transfer protocol prgram. First we have to download filezilla to our computer. Go to google and download it first into the computer. There is a username and password to use the FTP. Open the filezilla and come to Host. There we have to type ourdomain.com or ftp.yourdomain.com. Next you have to enter the username and password. Next you have click quickconnect there. Then you will connect to your webserver. In filezilla there are four quadrants ther...

This video tutorial shows how to open a port for torrent downloading on your computer. Click Start menu, type cmd command in Search area. In cmd window type ipconfig and press Enter. Remember or write down your IP adress. Type exit and press Enter to close cmd window.
When stories are told about people in need, the ones with happy endings include the details of someone that produced an action that caused the people in need to be better off than before. Do we have to wait for the identification of a need? Could we on purpose just plan to present products and services that cause our customers and client to see an improvement in their circumstances just because of the business interchange with an owner manager of purpose? The fair exchange of products or serv...

Spotify integration in Bumble has been around for a few years now, allowing prospective matches to view the artists you listen to the most on the popular music streaming service. It definitely helps people connect, but sadly, it doesn't work as well as it should because it rarely updates to show what you're listening to now.
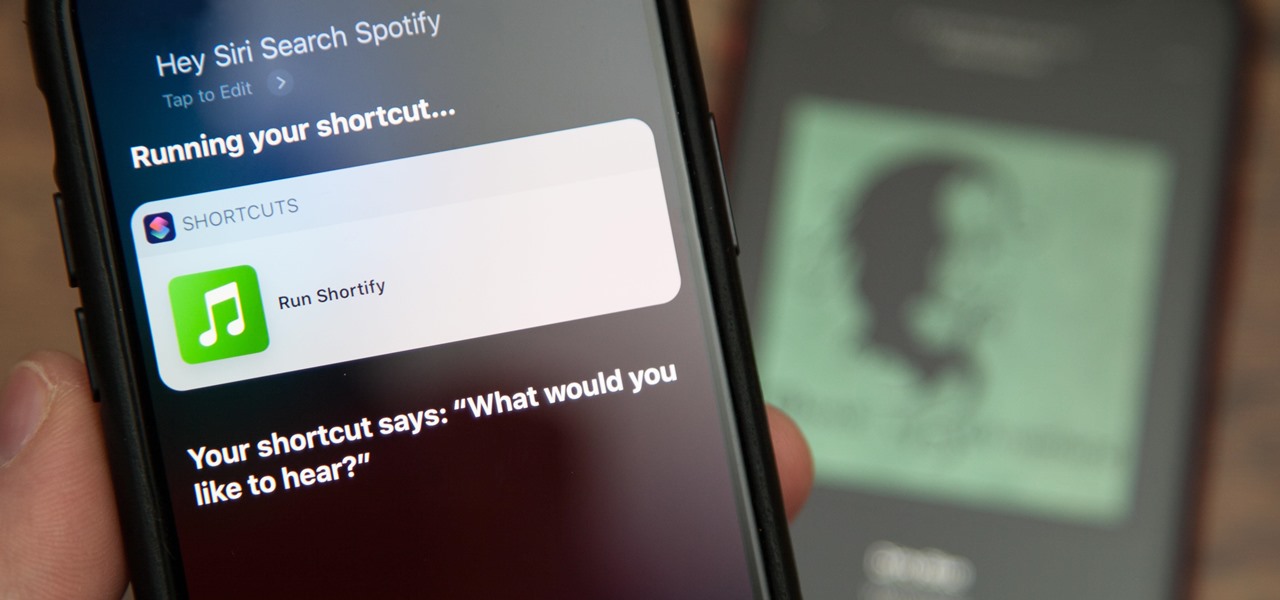
In iOS 13 and later, Spotify supports Siri commands, something we've wanted ever since Siri and Spotify were things. But if you're on iOS 12 still, you're missing out. All you can do is open the Spotify app, then pause and skip tracks with Siri after you start playing a song manually. There is a workaround, however.
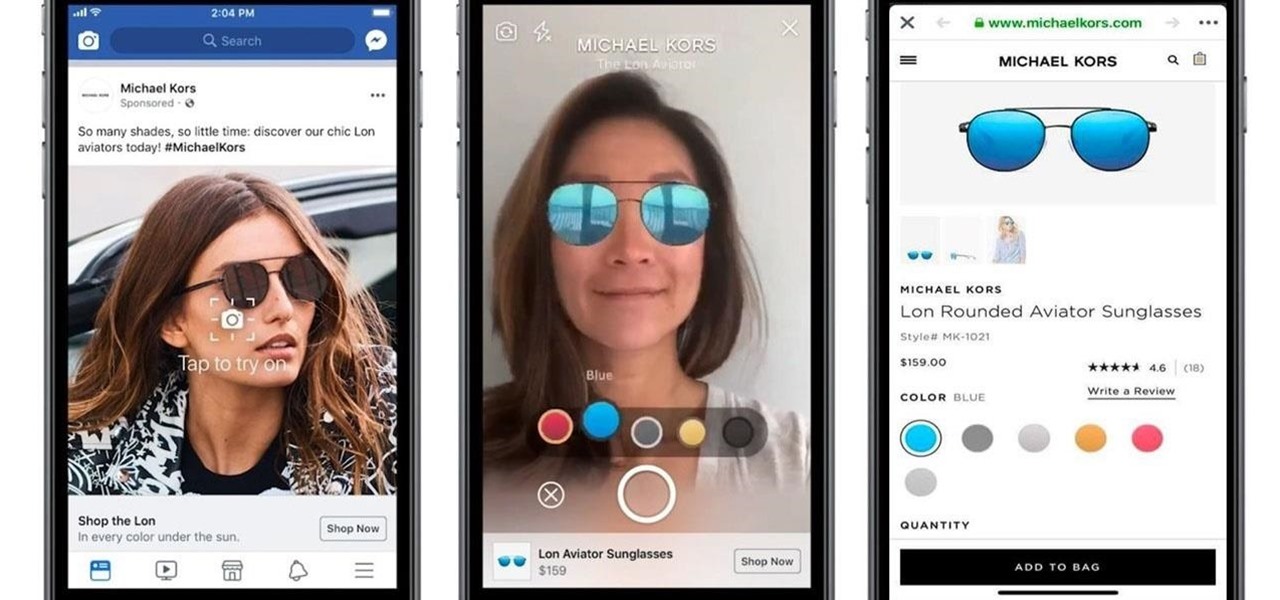
Facebook is preparing to make augmented reality experiences for brands more visible in its mobile app with Tuesday's introduction of augmented reality ads in its News Feed.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

If you've read our list of the best email clients for iOS, you'll know Apple's Mail app doesn't cut it when it comes to third-party integration. If you want to use some of your favorite apps directly in your mail client's calendar, go with Outlook.

With the addition of the OpenSSH client and server in the Windows 10 Fall Creators Update, you no longer have to rely on third-party programs to open an SSH server and connect to a Windows machine. While still a beta feature, this represents a long-overdue update fulfilling a promise made back in 2015.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

When it comes to differentiating from the competition, brands are continuing to leverage augmented reality to give consumers to the point that there are few "firsts" left to achieve in the marketplace. While L'Oreal jumps on the augmented reality bandwagon for cosmetics, Acura finds a new way to make augmented reality a spectacle in the automotive industry.

Nissan began to offer Level 2 driving capacities in a mainstream model when it debuted its ProPilot self-drive option for its Serena minivan in Japan last year.

Ride-hailing services are everywhere nowadays and with new companies developing all the time, it is one of the most convenient ways for people to get around. Companies like Uber make it easy for passengers to call a car to pick them up and drive them to their desired location. These services have been especially helpful for commuters as well as those who might need a ride home after a night at the bar. However, ride-hailing services require driving with a total stranger, which means the safet...

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

Hello, fellow hackers. I'm sure we've all seen it somewhere: the undying question of "How do I hack the game so-and-so?" And the answer usually is, "Come back when you actually know how to hack!" But how does one even go about "hacking" a game? What could that even mean?

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

When Google Play Music launched a few years ago, I ditched iTunes and began using the service as my one and only source for listening to my personal music library. While All Access is great, I still prefer the radio feature on Spotify, so I still use that to discover new music.
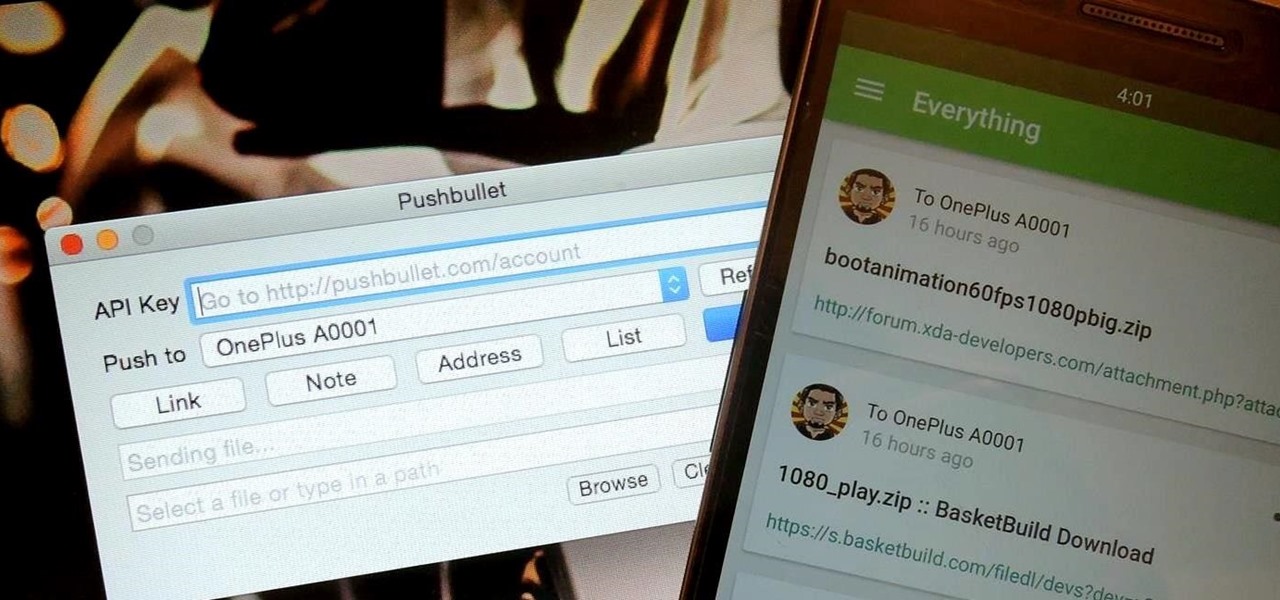
Before Continuity and Handoff were even announced, Pushbullet was already allowing users to quickly send notes, links, and photos between their devices with a few clicks.

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.
In any project management career, there is no such thing as a person who knows everything for each project. Many times, those who got too much confident with their jobs fail because they were not able to make things clear before and during the project implementation.

In my first few articles, we focused on operating system hacks. These hacks have been primarily on older operating systems such as Windows XP, Windows Vista, and Windows Server 2003.
I've noticed that a few people using the crypto-currency, Bitcoin are having issues importing private keys to their Bitcoin wallet. This is easy to do and doesn't require anything other than your Bitcoin client/daemon (as of ver0.6.0 ) and the command line.

Tattoo lady and reality TV star Kat Von D is obviously extremely talented with the tattoo needle. Creating interesting designs for clients that include celebrities, Kat Von D exudes a distinctive style that includes looking like a tougher version of a classic pin up.

In this video, we learn how to give a professional hand massage. First, spread oil onto the hand with your hands, which will prevent you from sticking together. After this, open the hand up and interlock your fingers with theirs and start to massage the inside of the hand. Open the hand up and work your fingers into the sensitive muscle areas. Go slowly, but apply enough pressure around the hands to make a difference. After this, work the tendons on the front and work your hands around each o...
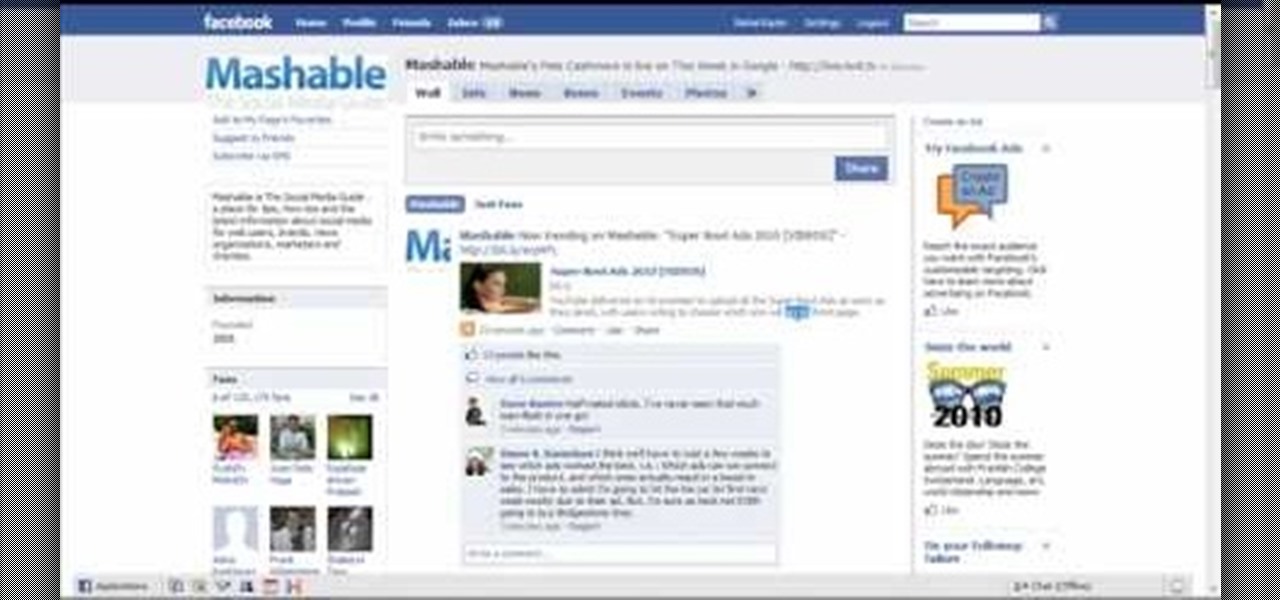
This instructional video Nehal Kazim from Site shows you how to make a complete Facebook fan page. Before creating a fan page evaluate the reasons of making a fan page. A fan page lets you connect with your future clients and fans and keeps them updated and gives them a platform to talk about your organization. To create a fan page go to the bottom of any page and click 'Advertising', select pages and click create a page. Select a suitable category and a suitable name make sure to select it c...

For a mom, there is always so much to do that your own personal care routine may take a back seat. But in this video, top hair stylist Gary France offers tips on how to style very short hair for the busy mom. France shows us his process on a busy working mom. The client receives a lighter color to brighten up her look, a trim to texturize her hair and styles the hair without using a blow dryer, which is great for saving time. France shows us that just because you have kids to take care of doe...