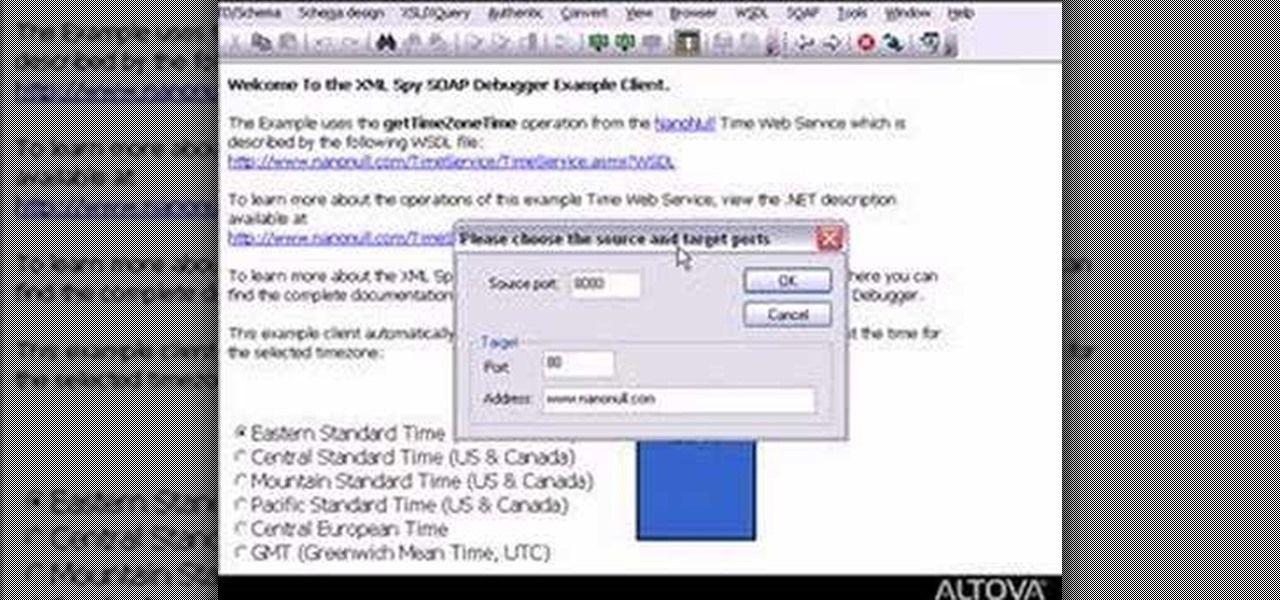
How To: Use the SOAP Client and Debugger in XMLSpy
Need to debug some exisiting net services? Well, check this video out for how to do some basic XML editing in XMLSpy.


Need to debug some exisiting net services? Well, check this video out for how to do some basic XML editing in XMLSpy.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

Drone mishaps, such as the collision that scratched a military helicopter in New York, are becoming something of an everyday hazard.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

Until very recently, Apple apps were among the only ones that would play nicely with Siri on iPhones. If you wanted to take advantage of the digital assistant to, say, compose an email, you would need to go with Apple Mail instead of the email client you actually use. As of iOS 12, this is no longer the case.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

Apple's Mail app for iOS isn't a bad email client by any means. However, it just doesn't cut it for iPhone users that want a more intelligent and advanced email solution. If you're in the market for an app like that, Spark is absolutely your best bet.

The iPhone X, iPhone 8, and iPhone 8 Plus may be some of the fastest phones of 2o17. However, the equally new iOS 11 isn't quite as impressive. That being said, Apple is continuing updates to the developer beta for iOS 11.1, as it releases the 5th version of the beta today.

Architects are natural candidates to be early adopters of mixed reality. Their trade consists of not only designing buildings and spaces, but also presenting those designs to clients, who then decide that their vision is worth spending thousands (if not millions or billions) of dollars to build in reality.

LOOOK, a Seattle-based mixed reality and development studio, can now peer into the future with their new geotechnical engineering visualization application for Microsoft HoloLens.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

Developing GUI apps in python is really cool. I ask those who understand the language to help convert some of the command-line or console programs or apps ( I mean programs that are useful to a hacker ) to GUI. I know GUI makes us lazy and not wanna learn but we should all know its fast. Today's tutorial is on p2p chat app I developed last week and decided to share it with the community since its kinda cool.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my nascent hackers! In previous tutorials for my Wi-Fi Hacking series, I have shown you how to crack WEP and WPA2 passwords, break a WPS PIN, and create Evil Twin and Rogue access points. In this continuation of the series, let's look at slightly different approach to attacking wireless.

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

Welcome back, my aspiring hackers! Domain Name System (DNS) is one of those things we seldom think about unless it doesn't work. Then, it can be very frustrating when we attempt to navigate to a website and we get that frustrating error message.

Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my beginner's guide to hacking Wi-Fi.

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.

Welcome back , my fledgling hackers! Lately, I've been focusing more on client-side hacks. While web servers, database servers, and file servers have garnered increased protection, the client-side remains extremely vulnerable, and there is much to teach. This time, we'll look at inserting a listener (rootkit) inside a PDF file, exploiting a vulnerability in Adobe's Reader.

I'm not admitting to anything, but let's be honest, most of us download content on the Web from time to time. With copyright holders laying down the law more and more often, it can't hurt to do so with caution. And even if you aren't downloading copyrighted material, you still don't want companies snooping in on your online activities. So just how do you protect yourself when torrenting? Avoid "Open Communities"
This video will show you how to record video on your Apple iPhone 3G for free! This is a complete guide to installing the iPhone Video Recorder on your iPhone 3G, which also works on the First Generation iPhone.
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

Have you tried working out with advance triceps dips? Advance triceps dips are an essential part of body sculpting and strength training. This fitness how-to video demonstrates how to work out the triceps muscle with advanced triceps dips. Learn about arm exercises in this training video.
If you want to tool around in the user interface of Star Trek Online and modify your client, this video shows you how. Do note that Cryptic doesn't support modding, and it could break your system. But if you want to alter the mouse pointer or your camera point of view, here's how!

Increase arm strength with side dumbbell lateral raises. Learn how to work out with dumbbell exercises in this training video. Take action: begin with moderate weight, keep shoulders back and chest high with abs tight, doing slow and controlled movements. Michelle, the instructor in this how-to video, is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifti...

Work out and getting in shape with dips. Learn how dip exercises can increase your strength and fitness in this training video. Take action: do not lock elbows, upper arms stay parallel to floor, and no partial reps, use full range of motion! Michelle, the instructor in this how-to video, is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifting and she en...

Strengthen the arms and the core with seated laterals. Learn how lateral exercises and weightlifting can keep you fit in this video. Take action: begin with a moderate weight, use slow and controlled movements, but do not keep hands above elbows. Michelle, the instructor in this how-to video, is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifting and sh...

Keep arms stiff for lateral pull downs. Learn exercises for the lats in this training video. Take action: this is a great exercise for swimmers or surfers, keep shoulders back and arms straight, but do not curl shoulders. Michelle, the instructor in this how-to video, is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifting and she enjoys training aspirin...

Increase strength in the triceps with triceps kick backs. Learn about muscle growth with arm exercises in this fitness video. Take action: keep head in line with spine, only movement should be with lower arm, and keep core tight. Michelle, the instructor in this how-to video, is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifting and she enjoys training...

Strengthen the triceps with triceps push ups. Learn how to increase arm strength with triceps exercises in this training video. Take action: position hands in diamond shape under chest,so that the elbows move straight back, and maintain plank position. Michelle, the instructor in this how-to video, is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifting ...

Add deep squats to your workout to really strengthen your legs. Learn how exercising with squats can strengthen the legs in this fitness video. Take action: feet wider than shoulder-width, toes pointed out, keeping abs tight and chest high, squeeze quads at top of movement. Michelle, the instructor in this how-to video, is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specia...

Work out the butt and thighs with press exercises. Learn about butt and thigh presses in this dumbbell fitness video. Take action: place feet higher or lower depending on target area, bring thighs to chest without rolling hips, but do not lock knees. Michelle, the instructor in this how-to video, is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifting an...

Work out your arms with dumbbell concentration curls. Learn how to exercises with curls in this fitness video. Take action: stay tight without rocking, get full range of motion, squeeze at the top of the movement, and plant your elbow. Michelle, the instructor in this how-to video, is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifting and she enjoys tr...

Strengthen the calves with calf raises. Learn about dumbbell exercises for stronger, more flexible calf muscles in this fitness video. Take action: use one foot or add dumbbell to increase difficulty, keep body straight and tall, and drop heel as low as possible. Michelle is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifting and she enjoys training asp...

Have you ever tried working out your arms with rope pulldowns. If so, you know that they are a great exercise for strength training and weightlifting. This fitness how to video demonstrates how to work out the triceps with triceps rope pull downs. Learn how to increase muscle strength in the arms with this workout video.

Have you tried working out with a barbell wrist curl? If so, you know that wrist curls are an essential part of lifting weights and strength training. This fitness how-to video demonstrates how to work out the muscles in your wrist with barbell wrist curls. Learn about barbell exercises, wrist curls, and strength training in this video.

Have you tried working out with dumbbell shrugs? A dumbbell shrug is an essential part of lifting weights and strength training. This fitness how-to video demonstrates how to increase muscle strength with dumbbell shrugs. Learn about dumbbell exercises in this workout video.