With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

Samsung and Apple are back in court, but this time it's not just money at stake. The Supreme Court's decision could have a far reaching effect on patent law and innovation in design.

The world of augmented reality has seen a myriad of different products, from sensor-laden smartphones to robust holographic headsets, but Google Glass's failures nearly killed the middle ground.

With certain apps and games, it's all about the settings. In order to get your money's worth with one of these, you simply have to take the time to tweak and adjust various options, which is something a lot of users don't necessarily want to do.

Welcome back, my tenderfoot hackers! Generally, you will want to perform a vulnerability scan before doing a penetration test. Vulnerability scanners contain a database of all known vulnerabilities and will scan your machine or network to see whether those vulnerabilities appear to exist. If they do, it is your job to test whether they are real and can be exploited.

Up until the last 15 years or so, watching the commercials during the Super Bowl was arguably more exciting than the game itself. Super Bowl XXIV featured the San Francisco 49ers blowing out the Broncos, 55-10, in the worst Super Bowl beatdown of all time. The game might not have been that exciting, but the commercials sure were.

What's up readers? Today I'll be introducing to you a new vulnerability called the Format String vulnerability (in case you missed the title). It won't be much, just a little motivation to keep you guys going. A little teaser, if you may.

Common knowledge is a funny thing: it represents a majority's opinion on a particular subject and somehow makes that opinion fact. If that 'fact' goes unopposed and unchallenged, then it is passed on and preserved from one generation to the next—regardless of whether it is true or not.

Hi nullbytes! I've been recently reading the whole Linux Basics for the Aspiring Hacker series and felt like it was missing some stuff I know, so I felt like sharing it with anyone who might find it useful too.

Welcome back, my greenhorn hackers! Digital forensics and hacking are complementary disciplines. The better you are at digital forensics, the better hacker you are, and the better hacker you are, the better you are digital forensics. Unfortunately, few people in either profession cross these discipline lines.

It seems like custom Google Now commands are a dime a dozen these days. With Commandr for Google Now giving non-rooted users their first taste of custom voice commands just a couple weeks ago, you may wonder why we're covering this subject again.

We all know that it's important to drink water regularly throughout the day. After all, it has so many benefits, including flushing toxins out of the body and maintaining kidney health and good bowel movements. Turns out that's only part of the story. While being properly hydrated is key to maintaining overall health, it's also a big component of maintaining and even increasing cognitive ability. Plus, drinking enough water regularly can help you lose weight, if you know when to drink it and ...

You probably already know by now that a custom Android ROM can change your user experience and give you what feels like a new OS on your device, and there's no shortage of them out there to try out.

Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look at abusing the trust that a user innately has for software updates to install our own listener/rootkit on their system.

Chakras represent a connection of spiritual energy between the human body and the mind. Discover information on chakra symbols and meanings with tips on alternative medicine from a spiritual healer in this free video series on alternative healing and chakras.

To play in the World Cup, soccer's ultimate tournament, you have to be among the best players on the planet. For the rest of us, Google has a hidden game to simulate the thrill of scoring goals for your favorite team.

While Apple introduced new AR features for iOS 15 and Object Capture for Reality Kit 2 during the WWDC 2021 keynote, updates for ARKit were curiously absent in the official presentation.

The augmented reality space is no longer about if but when every company and creator will use some kind of immersive device and software to produce and distribute 3D content.

Mobile augmented reality gaming pioneer Niantic is chomping at the bit to get games like Pokémon GO out of smartphones and onto smartglasses, and it appears to be taking matters into its own hands.

Based on recent reports, we've got a pretty clear picture of what to expect from Apple's rumored augmented reality headset expected to arrive next year, but the outlook is more opaque concerning its consumer-grade AR smartglasses.

If there is one constant in currently available AR headsets, it's that, for a quality experience, they'll carry a high price tag. Price is one of the reasons these devices are mostly marketed towards enterprise customers for now.

Google dropped several of the Pixel 4's more gimmicky features in favor of perfecting the basics on the Pixel 5. While you probably won't miss Motion Sense or the Assistant squeeze gesture, you'll definitely like the extra battery they packed into the space those features once occupied. Almost 50% more battery, actually.

The new Chromecast represents an evolution of Google's smart TV dongle as well as the Android TV platform. In addition to a remote control and the ability to install apps, Chromecast with Google TV hosts the debut of Google's innovative Google TV interface, which will eventually make its way to Android TV.

For the most part, new features for Google Maps, such as Live View augmented reality walking navigation, come to Android first.

The top five apps of the 2010s were all social media apps of some kind, and the fact that's not surprising to you says a lot. We may use them for other reasons here and there, but our phones are social media machines at their cores. The thing is, some make better machines than others.

While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

If you've ever needed to prove you have remote access to a device, or simply want a way to convince someone their computer is haunted, SSH can be used to make a device begin to show signs of being possessed.

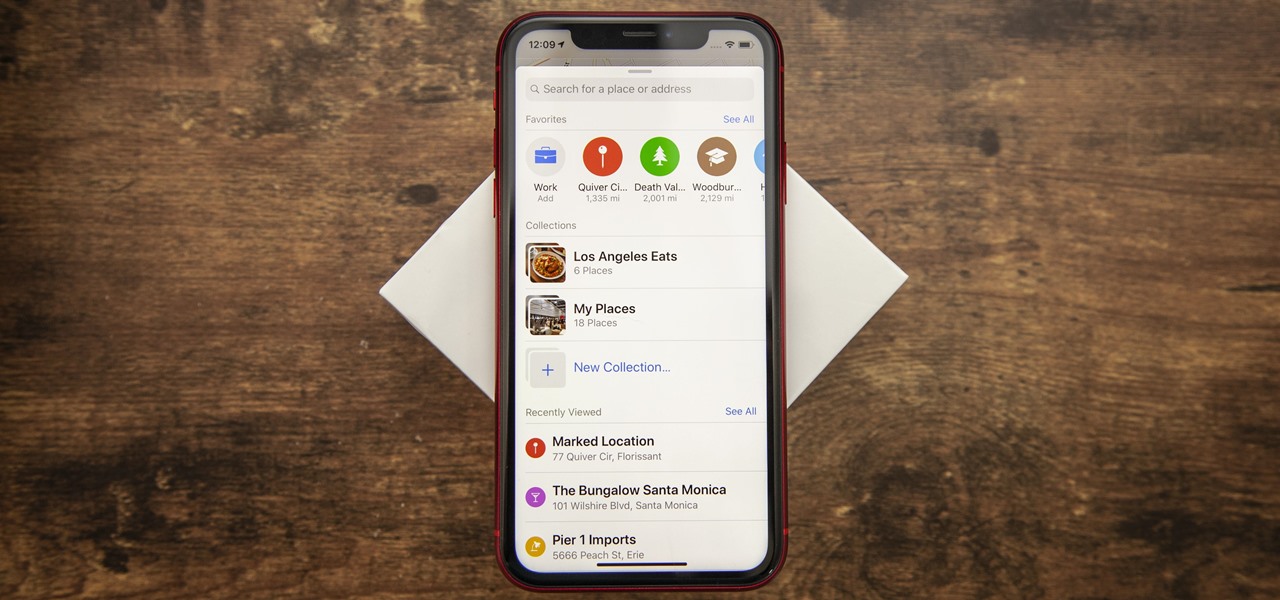
Apple Maps has had a rough lifecycle. After completely dropping the ball during its inception, Apple has been slowly improving its usability and feature set. After six and a half years, users still prefer third-party apps in iOS 12 over Apple Maps, with Google Maps stealing a large 67% market share. But iOS 13 for iPhone may finally close the gap.

While iOS 13 introduces over 200 new features for your iPhone, one of the biggest focuses this year is Photos and Camera. The update completely overhauls the Photos app, creating a more organized and natural way to interact with your pictures and videos. You'll also find a few new tricks in the Camera app. In all, Apple has added over 30 new features to your shooting, editing, and viewing experience.

Beta testing certainly has its perks. While you do need to deal with bugs, you're introduced to new features before the general community. And if we're talking iPhones, there are over 200 new features in iOS 13 beta. If you're already on board with iOS 13 public beta 6 for iPhone, you can get an upgrade on that firmware as Apple just released public beta 7 today.

In 2019, the Raspberry Pi 4 was released with specs including either 1 GB, 2 GB, or 4 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as well, if not better, than its predecessors. It also includes support for Wi-Fi hacking on its internal wireless card.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

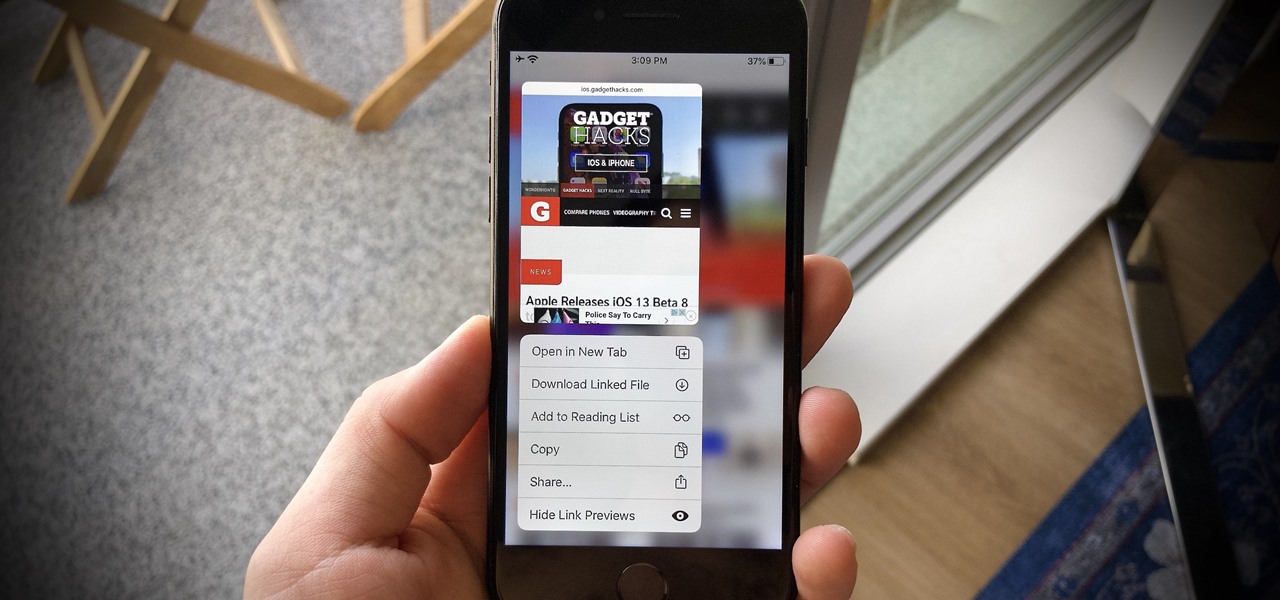
Twitter's official iOS app is adequate if you're not much of a tweeter, but if you are, there's a lot of useful features that are missing. Luckily, there are plenty of free Twitter clients available that you can use on your iPhone. These third-party apps have features such as customizable interfaces, post scheduling, and different browser options for opening links, to name just a few.

While many are familiar with Samsung, I'm pretty sure most Americans couldn't name the second-largest smartphone OEM. It's actually Huawei, and they recently released a spec-sheet dream of a phone in the Mate 20 Pro. So naturally, we wanted to see how it compared to the largest OEM's best offering.

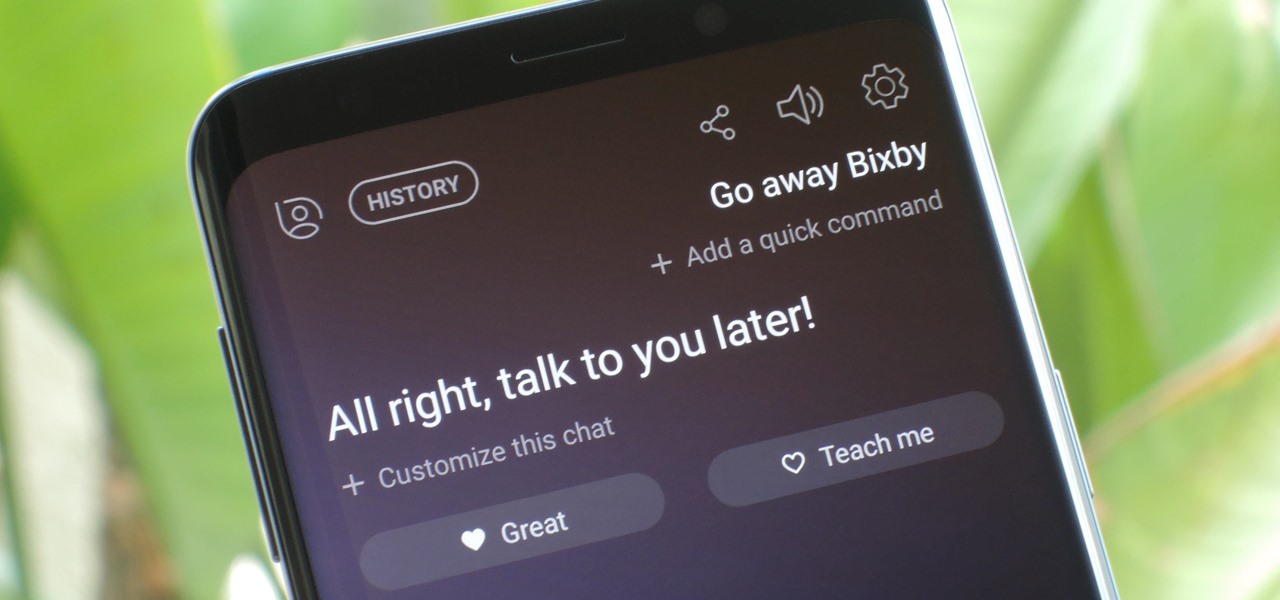
Sorry Samsung. I know you really wanted Bixby to be the next Siri, Google Assistant, or Alexa — but it just isn't. Burying the option to disable the app won't change that. Sure, Bixby has some redeeming qualities, but there are many of us who don't want it shoved down our throats. We'll show you how to disable the app to prevent it from launching every time you try to access just about anything.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.