If you want to get to the rim more consistently in basketball, you couldn't ask for a better teacher than Manu Ginobli, an absolute king of getting to the rim off the pick & roll. Watch this video to learn how his eurostep move can get you past three defenders to the basket.

Washington State has a history of large earthquakes, as does California. More than 1,000 earthquakes are registered in Washington State each year. More than 10,000 are recorded in California each year. In an earthquake, non-structural elements, which is anything that does not actually hold the building up, may become unhooked, dislodged, thrown about, and tipped over. this can cause extensive damage, interruption of operation, injury and even death.

Rust protection doesn't have to cost a fortune. With a little zinc and some electricity, you can protect your precious metals from rust by galvanization. When you galvanize something, you're giving it a protective coating, and in this case, it's a zinc coating.

Suzy Cohen tells us in this video how to lower our blood pressure naturally. Believe it or not, the urinary tract is connected with our blood pressure. A dietary supplement called "Asparagus extract" is recommended. Asparagus in vegetable form is delicious when served with a little butter or feta cheese. When you take it as a supplement, you get a bigger dose. It is a wonderful diuretic, which means it makes you pee a lot. You should take it in the morning, so that you do not find yourself ru...

There's nothing more tedious, yet exciting, than watching surveillance cameras at work. They prey on the innocent and the unknowing. They protect businesses, workplaces, and homes. They catch criminals in the act, find hilarious anomalies, and are just darn cool when you're not the one that's supposed to be eavesdropping with them.

Michelle Phan presents this tutorial on how to take a tomato and turn it into an invigorating scrub.

Watch this science video tutorial from Nurd Rage on how to get lithium metal from an Energizer battery. They show you how to get Lithium Metal from an Energizer Ultimate Lithium battery.

Watch this video tutorial from the Polish Guy to see how to polish a stainless steel roller using Autosol. In this polishing tip we polish a stainless steel roller using Autosol Metal Polish. The tutorial includes detailed work instructions and best practices.

Watch this video tutorial from the Polish Guy to see how to polish a chrome car rim using Flitz Polish and a buff ball. In this polishing tip we polish a Jeep wheel using Flitz Metal Polish and a Flitz BuffBall. The tutorial includes detailed work instructions and best practices.

Watch this video tutorial from the Polish Guy to see how to polish an Andersen Door Handle using Simichrome. In this demonstration we use Simichrome to polish an Andersen Perma-Shield Frenchwood hinged patio door’s brass entrance handle. The tutorial includes a detailed work instructions and best practices.

There are two parts to the StormShield product: The server components (including the relational database and server) and the various agents that run on each endpoint. Among other things, the agent contains a host-based firewall and policy engine that can be customized to control applications and particular endpoint device features such as USB peripherals and registry entries. So watch this tutorial and learn how to protect your PC computer with SkyRecon's StormShield.

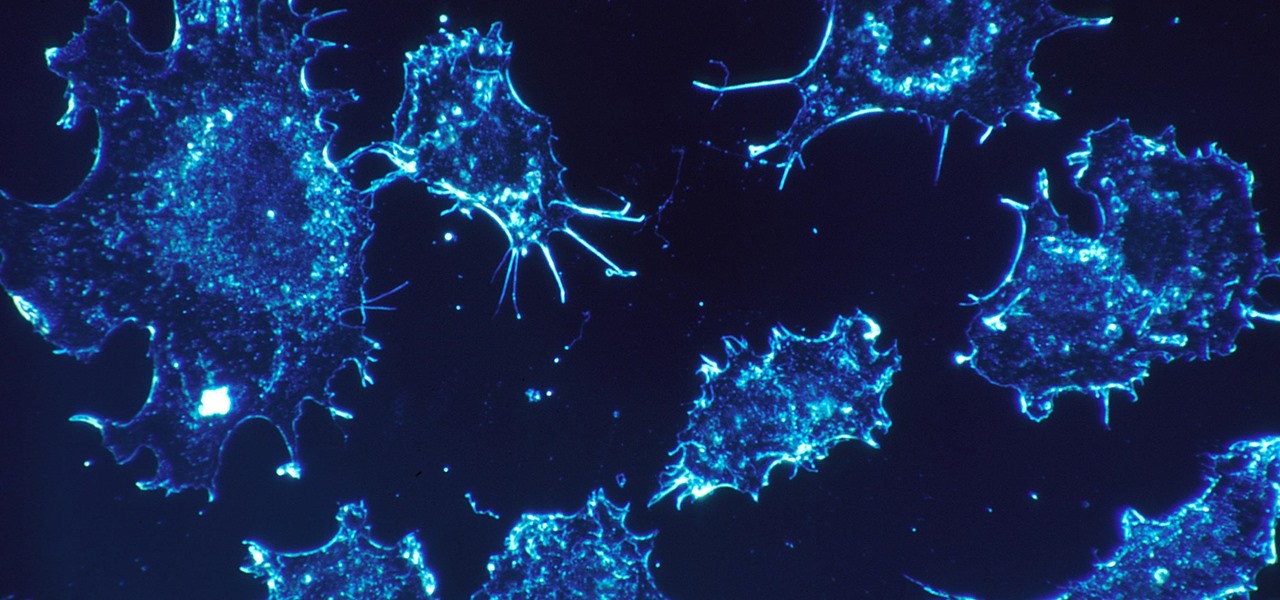
As our cells age, they eventually mature and die. As they die, they alert nearby cells to grow and multiply to replace them. Using a special imaging process that combines video and microscopy, scientists have observed the cellular communication between dying and neighboring cells for the first time, and think they may be able to use their new-found information against cancer cells, whose damaged genomes let them escape the normal dying process.

Hi Elite Hackers! Welcome! to my 4th post. This tutorial will explain, how to extend a (hacked) AP's range with a wireless adapter. I made this guide because after hacking an AP it was difficult to connect to it (poor connection) and further exploit it. You can also use this:

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.

In this tutorial, we learn how to password protect any folder on your desktop in Windows. First, right click on your desktop, then go to "new", then "compressed zipped folder" and name it whatever you want. Next, put what you want inside of the folder. After you've done this, open the folder then go to "file" and then "add a password". Pick a password that you will remember and type it into the text box, after you do this, click on "ok". Now your folder will be password protected and you will...

Use bird deterrents to protect your fruit trees.

Learn how to protect your documents and pictures by using a password. Free software needed: WinRAR

Food and drink spills have always been a nuisance by staining your car's interior, and causing your car's resale value to depreciate even more than necessary. Learn how to protect your car's carpeting and upholstery to keep the interior looking brand new and guarantee the highest possible resale value when it's time to sell.

Building a DIY Alarm System: The Concept So, you want to protect your property, or maybe a room, car, or even your backyard. The concept of an alarm system is to notify the "alarm administrator" that there is an intruder entering the previously designated boundaries. The triggers for this boundary could be as simple as a pressure sensor, or as complicated as a laser network. They all do the same thing, but some work better than others.

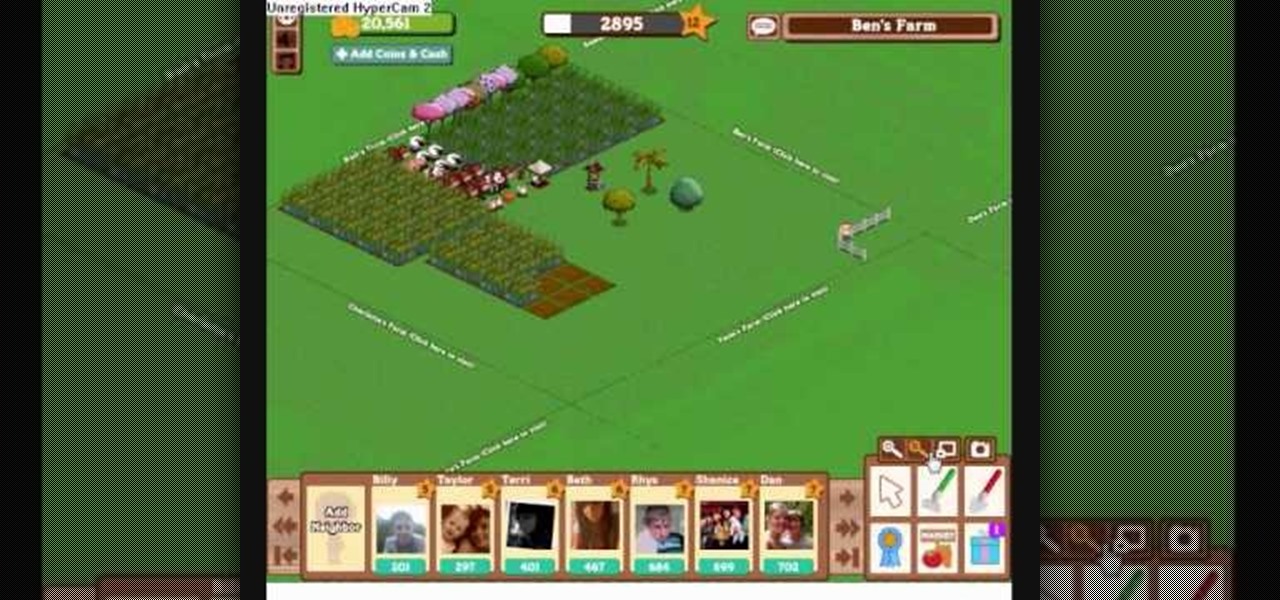
This is a great glitch to help improve your planting and harvesting in FarmVille. Believe it or not, the fastest way to do this is to simply trap yourself. That's it.

Spice up your farm in FarmVille! Make your farm appear to be 3D with this sweet trick. This video tutorial shows how to stack hay bales and hedges in FarmVille (01/07/10). If you're getting bored with the rather flat look of Farm Ville, this trick will show you how to make what appears to be hills. Using these, you can make your farm truly unique! Watch the video for details.

Every once in a while, you will have a lot of work to do in FarmVille, and a lot of space to cover. Use the fullscreen option to make life easier and see more at once.

Proud of the progress you've made in FarmVille? Take a photo within the game, and share it directly with all your friends!

Arranging fences can be a hassle if FarmVille. Once you understand the basics, however, you will be creating elaborate fence layouts in no time!

While sheltering at home orders are lifting, companies are still conducting most business online. Case in point, hackers have been having a field day over the last few months. Securing your identity has always been important, but never as much as it is at this moment.

Unlike some of the popular app lockers out there, a nifty app fittingly named App Hider completely erases apps, files, and their associated footprints from your smartphone. Think of App Hider as a micro-OS within your smartphone's system. This miniature ecosystem can operate copied apps independently, thus giving it an unprecedented layer of privacy and freedom within your handset.

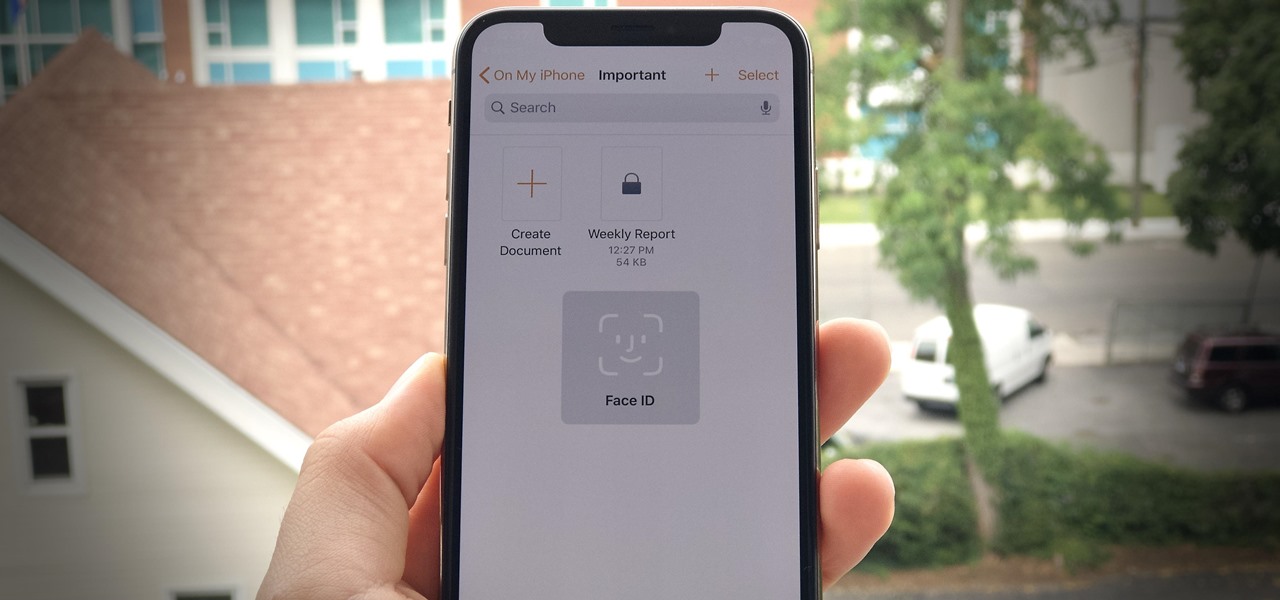
Your writing is just that — yours — so the work you do in Apple Pages should remain private until you choose to share it. Apple seems to share this sentiment. As another symbol of its dedication to user privacy and security, the company includes a feature in its word-processing app for iOS that allows you to lock documents behind a password, as well as with Face ID or Touch ID.

If you store important, sensitive information on your iPhone in Notes, you'll want to be more careful. When Notes syncs across your iPad and Mac via iCloud — devices that family members or coworkers may share — you run the risk of having your notes read, edited, and deleted by other people. Such a catastrophe is easily avoided.

When BlackBerry made the move to Android OS, they were aware of the limitations it presented. Unlike with BB10, they didn't create the operating system and would have to deal with the vulnerabilities already included. As a result, they added numerous security enhancements, and at the heart of this is DTEK.

Since the San Bernardino shooting in 2014, Apple's been engaged in a game of cat and mouse with law enforcement. Authorities want access to evidence on criminals' iPhones, but Apple wants to protect all of its customers' personal data equally. The latest installment in this saga has Apple outright disabling the Lightning port.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

When a photo or video is just too sensitive to leave laying around in your Photos app, you'll want to either delete it for good or hide it away in safe, secure location on your iPhone. As for the latter, Apple actually has a few tools available to make photos and videos hidden — even password-protected — on your iPhone.

After setting up your phone, there are a number of things you should do immediately before download your favorite apps. Specifically, now that your data is on the device, you need to take steps now to ensure it's both protected and retained. Fortunately, most of these steps are a one-time process.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

In case you didn't catch the big event in Cupertino, Apple just unveiled two of the most cutting-edge phones ever made — the iPhone 8 and the iPhone X. Out of the many glorious specs that were rattled off on stage, one stands out for being just a little confusing: Both models are rated IP67 under the IEC standard 60529.

While not cuddly to most, bats are shy, skilled flyers that fill an important role in their environments. A new study reveals a deadly disease decimating North American bat populations has stepped up its attack on vulnerable bat populations in the summer months.

Once we recover from the respiratory infection pneumonia, our lungs are better equipped to deal with the next infection — thanks to some special cells that take up residence there.

Facebook is testing a new feature in India. One that could help you protect your profile photos from being used on sites without your permission.