
How To: Refill an ink cartridge
If you use your inkjet printer regularly, you’ve probably discovered that the cost of replacing the cartridges can quickly exceed that the printer itself. Refill the cartridges yourself to save some money.


If you use your inkjet printer regularly, you’ve probably discovered that the cost of replacing the cartridges can quickly exceed that the printer itself. Refill the cartridges yourself to save some money.
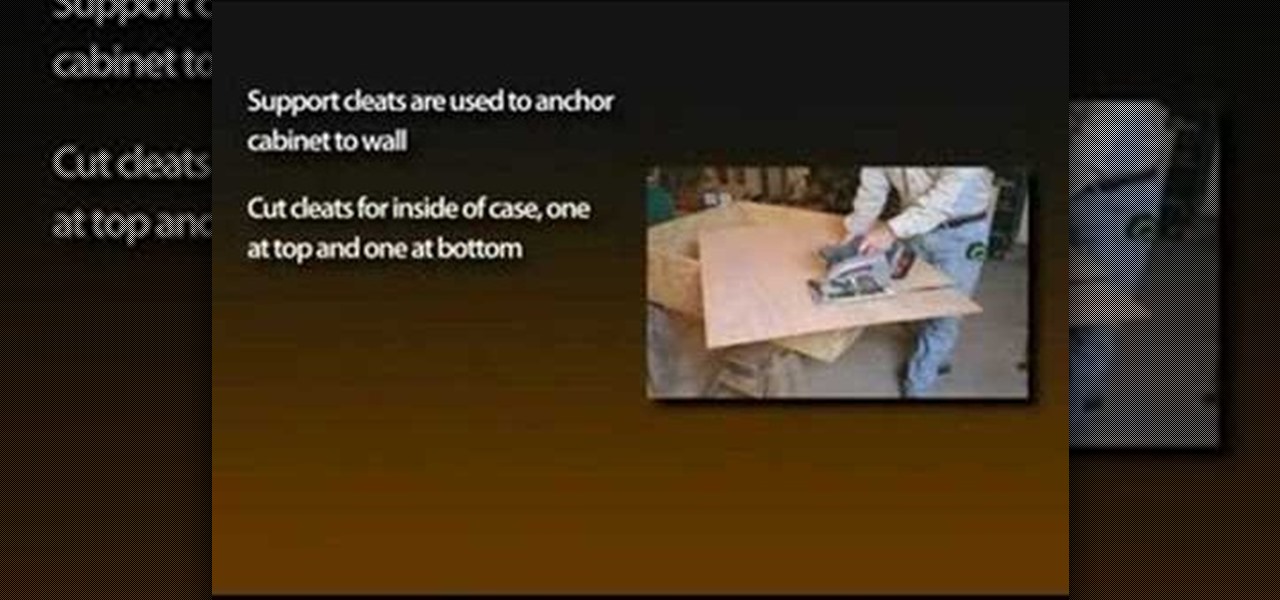
With the growing popularity of cordless power tools, it's extremely easy these days to accumulate a lot of portable tools, and when you add in quality corded tools, such as circular saws, routers, planers and air nailers, you can end up with a pretty hefty investment. These same tools are the first to “walk away” in a theft. Left lying around a shop or garage, they can also be somewhat dangerous for youngsters. A locking cabinet not only provides a secure place, but protects the tools as well...

Self defense for women is a great way for women to feel safe knowing they can protect themselves. Learn some self defense moves against frontal attacks with tips from a martial arts expert in this free women's self defense video series.

Don't let your scrapbooks get destroyed, learn how to properly store them, preserving them for life, in this free video series that will show you how to protect you scrapbook for years to come.

Whether you're hiking or hunting, spending time outdoors can also be an opportunity to spend time with man's best friend--your dog! Get tips from this how-to video on spending time with your dog AND keeping her safe.

Learn how to use a heavy boxing bag to do speed alternate gut punches. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do single arm pec decks. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do seated arnold presses. Presented by Real Jock Gay Fitness Health & Life. Benefits

Pressure washers are a great way to clean a brick patio - if you do it right! The pressure washer can harm the surface you are cleaning or even yourself. The basic operation of the pressure washer is to take the low pressure from you garden hose and increase the pressure with a special pump. The pump uses either a gas powered engine or an electric motor to boost the pressure.

Samsung's not one to make drastic changes to what already works. They've continued on with the IP68 rating under IEC 60529 first given to the Galaxy S8 all the way to the the Galaxy Note 10. If you're a little confused as to what this rating means, don't worry, it's actually pretty simple once you get to the meat and bones of it.

In recent years, unwanted calls have become a top priority for the FCC. In 2016, analysts estimated that US customers received over 2.4 billion robocalls per month. As a result, the FCC has provided carriers new tools to combat this problem.

When it comes to resistance to the elements, Samsung seems to believe in the old saying "if it ain't broke, don't fix it." They've carried over the IP68 rating under IEC 60529 that was first found on the S8 all the way to their tenth-anniversary flagship, the Galaxy S10. While this certainly sounds great on paper, it's natural to want to dig a little deeper and find out what the rating means.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

It recently came to light that a number of Android phones are unable to stream HD video through services like Netflix, Google Play Movies, and Amazon Prime Video. If you're worried that your phone may be affected, there's a simple tool you can use to find out for sure if you can actually stream video in 720p or higher.

It looks like there is a fatal flaw in the current macOS High Sierra 10.13.1, even straight from the login menu when you first start up the computer. This severe vulnerability lets hackers — or anyone with malicious intentions — do anything they want as root users as long as they have physical access to the computer.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

Waymo claims in court documents filed yesterday in its lawsuit against Uber that ex-Uber CEO Travis Kalanick knew that former Google engineer Anthony Levandowski was in the possession of stolen documents while employed at the troubled ride-sharing firm.

Yogurt is more than an excellent source of protein, calcium, and gut-healthy probiotic bacteria. A protein isolated from probiotic lactobacillus bacteria in yogurt is capable of inhibiting drug-resistant bacteria.

The Centers for Disease Control and Prevention estimated that there were 212 million cases of malaria across the world in 2015, and 429,000 of those people died — mostly children living in Africa. Preventing and treating those infections has been a challenging world priority. That makes a new malaria drug discovery — published in Science Translational Medicine — incredibly important.

As the world goes into a frenzy over the latest strain of WannaCry ransomware, it might be a good time to remember to update all your devices. Yes, those little reminders your phone and computer throw at you every now and then to update your junk can be really annoying, but not without merit.

Chrysaor, a zero-day spyware believed to have been created by the Israeli "cyber war" group NSO, is an even greater threat to Android phones than it ever was to iOS.

Obstetric tetanus in an unvaccinated Amish woman after a home birth has emphasized the need for preventative healthcare.

Nineteen days ago, several hundred people could have been exposed by a traveler with measles in Nova Scotia, Canada. The next day, someone flying from Minnesota to Nebraska may have spread the measles to other passengers. A couple weeks ago, it's possible that a man and his six-month old child spread the measles in several Seattle-based locations. Authorities are trying to locate persons who may have been in contact with these people. None of the persons with measles were vaccinated. Why?

Norovirus outbreaks occur all year long, but peak in the winter months, which means we are in the middle of norovirus season. But there's still time to protect yourself from the highly infectious bug.

What's in a sneeze? Quite a lot—dirt, mucus, and infectious germs—it seems. And sneezing the right way can reduce the germs you share with neighbors.

Malware often disguises itself inside of seemingly non-malicious files, such as installer packages, where it can then gain root access to your computer to track activity or steal your information.

The smartphone has become one of the basic reasons for sore eyes. If you are addicted to your beloved smartphone, there is a fair possibility that your eyes will be paying off its expensive price. If you use your smartphone, tablet, laptop or any other similar gadget consistently, you may experience tired, dried, itchy eyes and also severe headache. Your vision can also become blurred by the time, which it means it is affecting your eyesight. However, you can lower down your eye strain by mak...

Coffee shops are a relaxing place to get work done on your laptop; there's free Wi-Fi, fresh coffee, and people generally leave you alone. Inevitably, those cups of coffee will go straight through you, resulting in a much-needed bathroom break. But while you're attending to your bodily functions, who's attending to your MacBook?
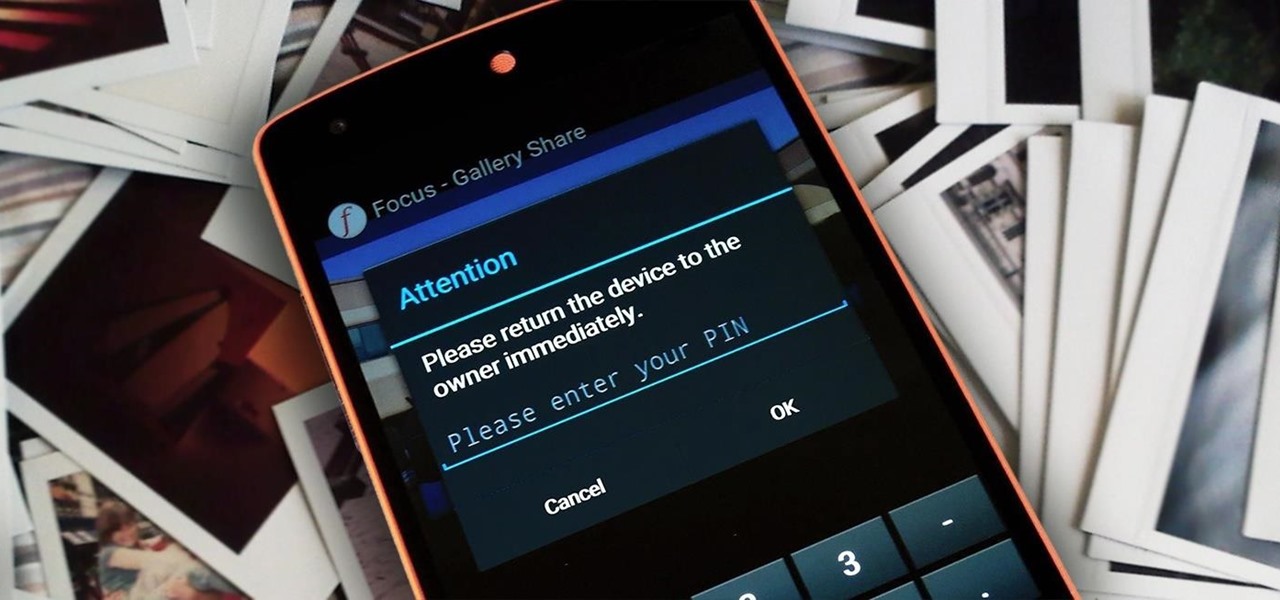
You have a cool picture that you want to show someone, but when you hand your phone over, they start swiping through all of your photos. Surely, you've encountered this scenario before. I definitely have.

Windows XP will always have a special place in my heart—it's the operating system I grew up on. It guided me through the glory days of AIM, Napster, and MySpace, but now it's dead. The OS that had been supported by Microsoft for twelve years officially lost its support on April 8th, 2014. Just like that, Microsoft has killed the beast, but for those of you who stubbornly refuse to cooperate, you can resurrect the dead. If you have Windows XP, this little known hack will get you further suppor...
Whether you're a celebrity or someone with something to hide, Facebook allows you to keep your "friends list" private so you can protect the identities of your Facebook friends. But it only kind of protects them.

As respectful as you may be, it's hard to resist looking through someone's iPhone when given the chance. You're not trying to snoop around, but it's just too easy to open up apps and read embarrassing emails or find scandalous Instagram follows. It's like looking through a digital diary riddled with deep, dark secrets.

There are many impressive features on a Samsung Galaxy Note 2, but just like any other smartphone on the market, the most used one is the camera. How many times did you take a picture today? Or admire all the selfies in your gallery? Or upload a video to Instagram, Vine, or Snapchat?
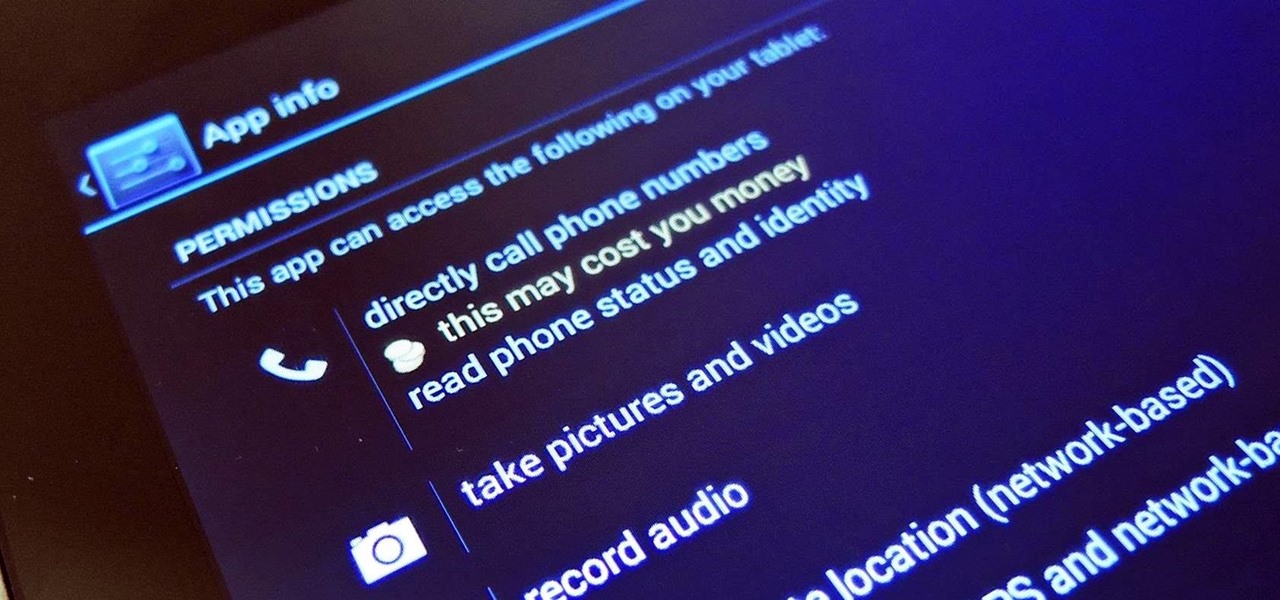
Privacy has been a heated topic in recent months, with everyone now up in arms over unauthorized leaks and exposures. And guess what—tablet and smartphone users are just as vulnerable.

Welcome back, my hacker novitiates!

Craigslist is probably the greatest site ever created, and I'm just talking about it's classified section, both awesome and amazingly creepy. Seriously, spend 20 minutes scrolling through the personals and you'll never want to take your eyes off the screen. But I digress—Craigslist is also one of the most convenient places to buy and sell pretty much anything you can think of. I've used it to buy my bed, my old bike (which was stolen!), and my couch. And while Craigslist is great in many ways...

Most of us have some sort of malware scanner or antivirus program on our computers, but what about our smartphones? A lot of people don't realize that computers aren't the only devices that are susceptible to malicious software and apps—they can follow you on your smartphone or tablet, too.