
News: Safari Security Breach Fixed in iOS 10.3 Update
Don't ignore the update sitting in your Settings app; you'd be leaving your iPhone's security vulnerable.


Don't ignore the update sitting in your Settings app; you'd be leaving your iPhone's security vulnerable.

Princess Cruises' Coral Princess voyage disembarked in Fort Lauderdale on Saturday, March 18, after a 10-day cruise in which 182 people were sickened with symptoms of vomiting and diarrhea. According to federal health officials, a norovirus is suspected for the outbreak.

OnePlus just unveiled a new version of their popular OnePlus 3T—a limited edition all-black "colette" version for the boutique's 20th anniversary today. The slick device will feature the iconic colette logo on the back.

A bacterium which triggers respiratory disease has been detected in the water systems of two Pennsylvania nursing facilities.
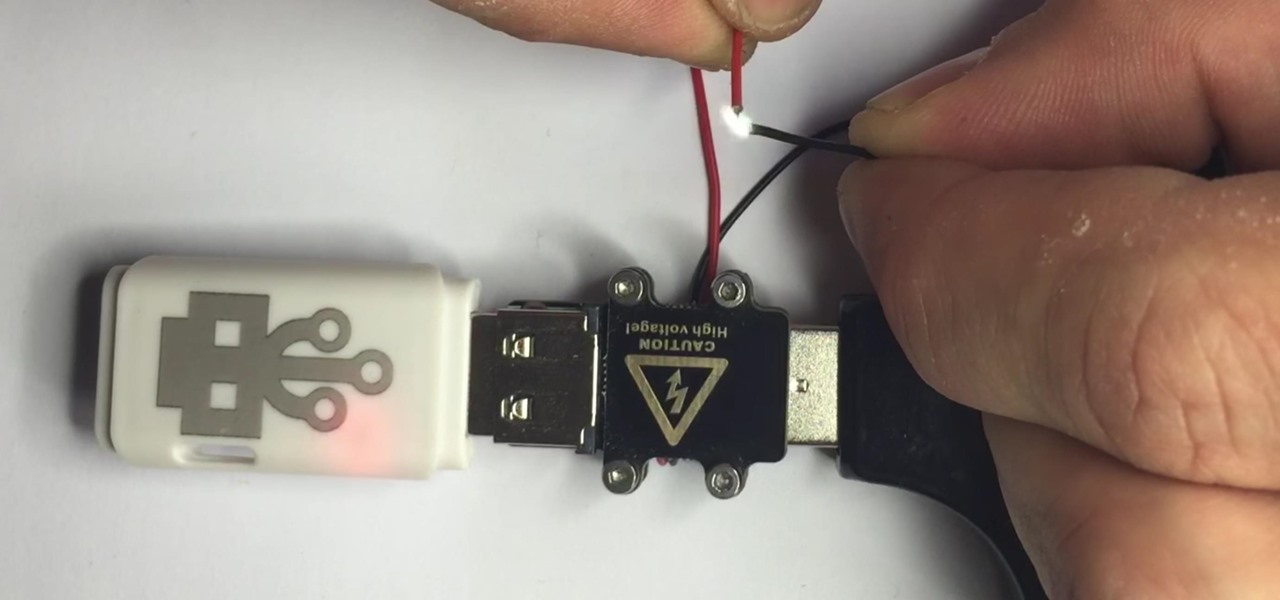
There are two types of bad USBs out there. One lets you trick the computer into thinking it's a keyboard or other USB device, and the other goes straight over malicious into computer killing territory.

Developers across the U.S. and Canada have started getting their augmented reality headset packages from Microsoft, and so far, everyone's raving about one gaming experience that shatters all doubts of just what the HoloLens can do... RoboRaid.
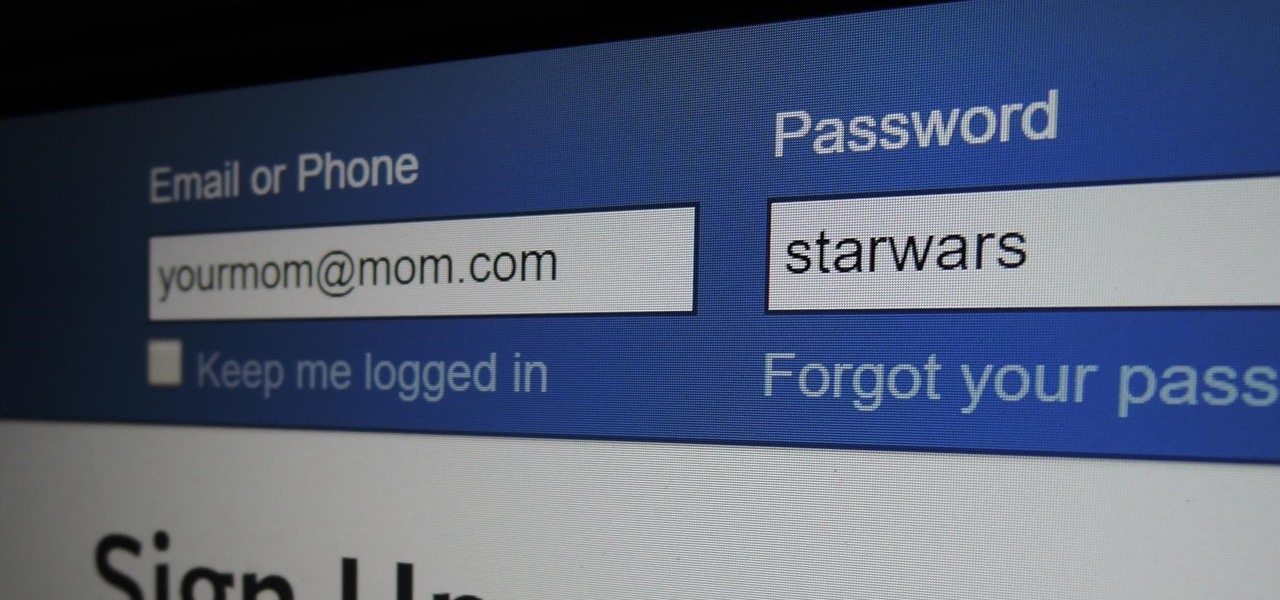
Some things never change. You'd think that with all the focus on web security, people might take the slightest precaution to keep their online activity private. Maybe there are more people suffering from Paula Poundstone's password troubles than we'd like to believe.

Welcome everyone to the second part of the How To Become Anonymous online series. Today I will (briefly) introduce you to what has been defined "The most secure OS" : Tails a Debian based OS. (Official website: https://tails.boum.org/)

You would think that with each major iOS update, there'd be fewer ways to bypass the lock screen. Unfortunately, Apple's developers have consistently failed every year since 2013 in this department, leaving open lock screen exploits for iOS 7, iOS 8, and now the latest iOS version, iOS 9, with each exploit being discovered within days of the OS release.

Whether it's the start, middle, or end of summer, it's prime-time grilling season. If you find yourself without a grill, however, it may seem as if half your summer plans of swimming by the pool while stuffing hot dogs in your face could be ruined.

For a number of years, I have had a vortex cannon on the top of my list of projects to attempt. Creating a sturdy cone for the barrel has always been a hurdle in the design, one I finally found a solution for in this video.

In addition to the fingerprint scanner, the Samsung Galaxy S6 has all of the basic lock screen options that other Android phones have: swipe, pattern, PIN, and password. There also just happens to be a secret sixth option called "Direction lock" that protects the device with a series of customizable directional swipes—only it's hidden in an unsuspecting settings menu.

Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it is essential to my country's (and my own) well-being that it not be traced back to me. Understanding digital forensics helps us to leave without a trace and never have a trail back to us or our employer.

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

A four-digit passcode is what protects your iPhone, and the sensitive material within it, from strangers or nosey friends. Four digits are the only thing preventing someone from snooping through your pictures and posting them online for the public to see, and that's if you even have passcode security enabled.

It is a truth universally acknowledged that food molded into fancy shapes somehow seems tastier. That's true even with chocolate, which is inherently delicious. Now, while you can buy chocolate that's been pre-molded into fancy shapes, you can have a lot of fun and save a few bucks by making your own specialty chocolate molds. All you need to get started are items you most likely already own.
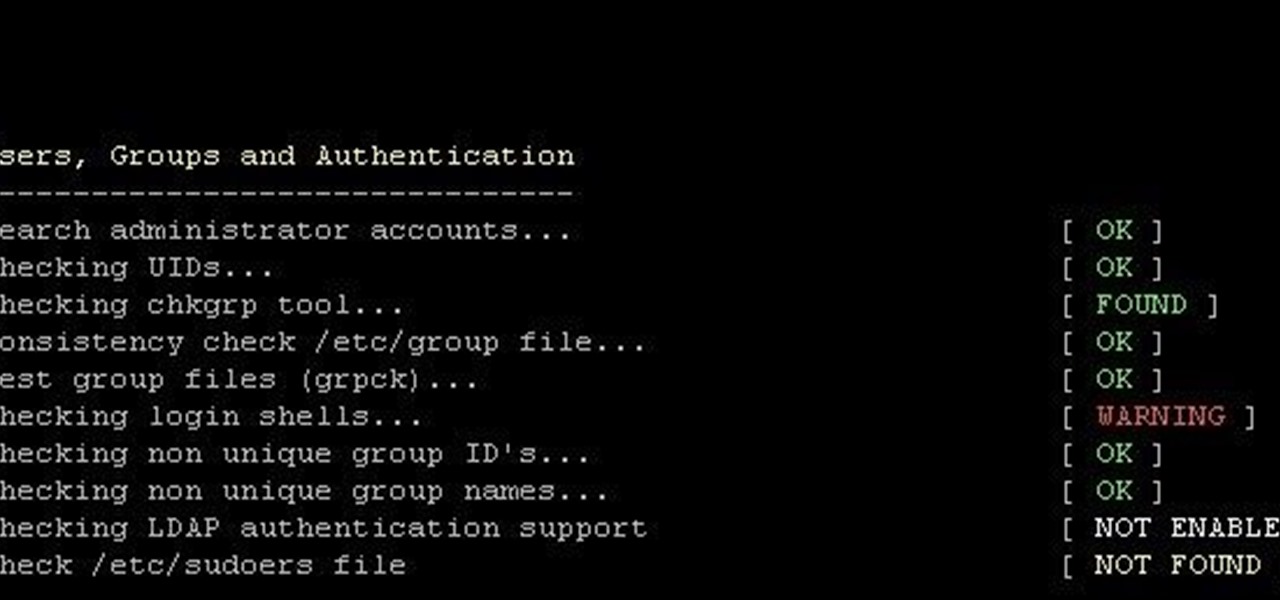
This is finding some of your vulnerability using Lynis. This tool Lynis is used on Unix and Linux type operating systems (sorry windows). So lets get started

French fries, like mashed or roast potatoes, are the type O blood of the food world—they're compatible with just about everybody. That's why it's so sad to bring home leftover frites (that's French for French fries) and have to toss them out the next day because they don't taste as good when they're reheated. Warning: Do Not Ever, Ever Use Your Microwave

The fingerprint sensor on the Samsung Galaxy S5 gets a little flack for its functionality, and that's mainly because the setup instructions ask you to swipe your index finger over the sensor to unlock your device or make mobile payments (and of course, because it was already hacked).

Holidays can be challenging, especially around Christmastime—but not if you invoke your inner MacGyver spirit. In my latest "life hacks" guide, I show you 10 amazing tips and tricks that'll hopefully make your holiday season a little more merry.

Sometimes the best place to hide something is where people least expect it, so in this project, we're making a super secret safe that only you'll know about.

When you're on the go, it's important to keep your belongings organized and at an arm's distance so you're not fumbling in public for your keys, cards, or phone.
When programming an Excel-file with links between sheets and assorted macros for whatever is needed you may want the file to behave as a program so that users can not access the ribbon even by double-clicking on the top bar. Protect the code from being accessed by pressing alt-F8 or alt-F11. Make sure you can run the macro show_sheets_and_ribbon () from the opening sheet before continuing to step 3

Who wouldn't want to know if someone was trying to log onto their personal computer without their permission? Be it your annoying co-worker or your girlfriend, there are many cases where people may try to gain access to your desktop or laptop.

When it comes to your smartphone, you don't have to be a cheater to want a little privacy. I don't even like people playing Temple Run on my mobile because I don't want anyone beating the achievements I've been working on getting myself.

Lock screen exploits are becoming increasingly common in the mobile world. Four weeks ago there was the iPhone 5 passcode bug (which just got fixed yesterday...kinda). Then there were a couple lock screen bugs on the Samsung Galaxy S3 two weeks ago.
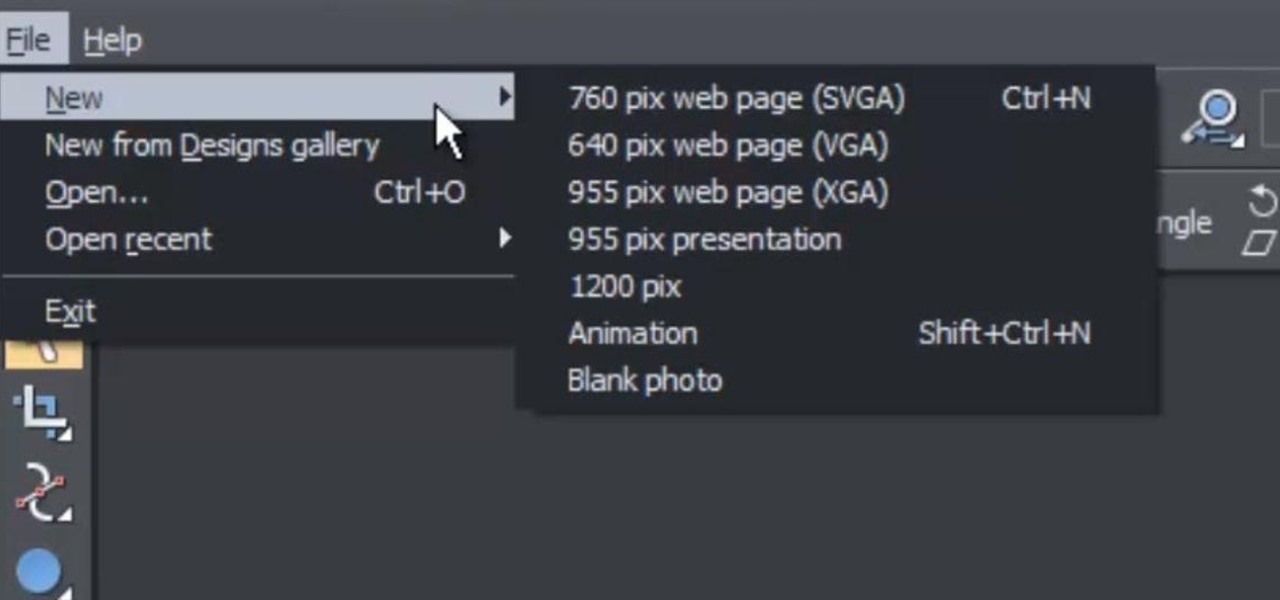
This web design tutorial is for newcomers to the Xara Web Designer software. In this web design tutorial, you will learn how to open a new document and save it using save as and save option.

There are many ways you can protect your computer from unwarranted access. For instance, you can use Lockscreen Pro to lock your Windows 8 computer and then have the program snap a photo of the culprit using your webcam.

We've all had that awful, sinking feeling when something you've been typing away at is suddenly gone. Maybe you accidentally hit the Back button, lost your internet connection, or your computer crashed, but whatever the reason, losing your work totally sucks. A lot of word processing programs have a built-in auto-save feature to prevent you from losing everything, but most websites and blogs haven't gotten there yet. An extension for Chrome and Firefox called Lazarus: Form Recovery can help y...

Megaupload was one of the very first file-sharing sites I ever used. But since 2005, the beloved (and pretty gangster) Kim Dotcom, has been in a legal battle with the U.S. Justice Department over copyright infringement.

Ever wonder what your brain looks like while you're singing? No? Neither had I, but as this music video for the song "Better Man Than He" by SiVU (aka James Page) will show you, the answer is "pretty cool."

UPS offers a four-step guide to prepare packages for shipping. These instructions include shipping advice on packaging materials and proper labeling that can help items arrive safely and on time. And when you are ready to ship, UPS Internet Shipping guides you through the required address fields. Packaging solutions made easy. That’s logistics.

If you take your camera equipment with you on a pretty frequent basis, having a camera bag can help protect it and makes it much easier to keep everything in one place. A good camera bag can be pretty expensive, but with this tutorial by photographer Allen Mowery, you can turn a cheap canvas messenger bag into a nice looking DIY waxed camera bag for half the price. For this project, you'll need a canvas messenger bag, a camera insert, and some paraffin wax, which can be found in the canning a...
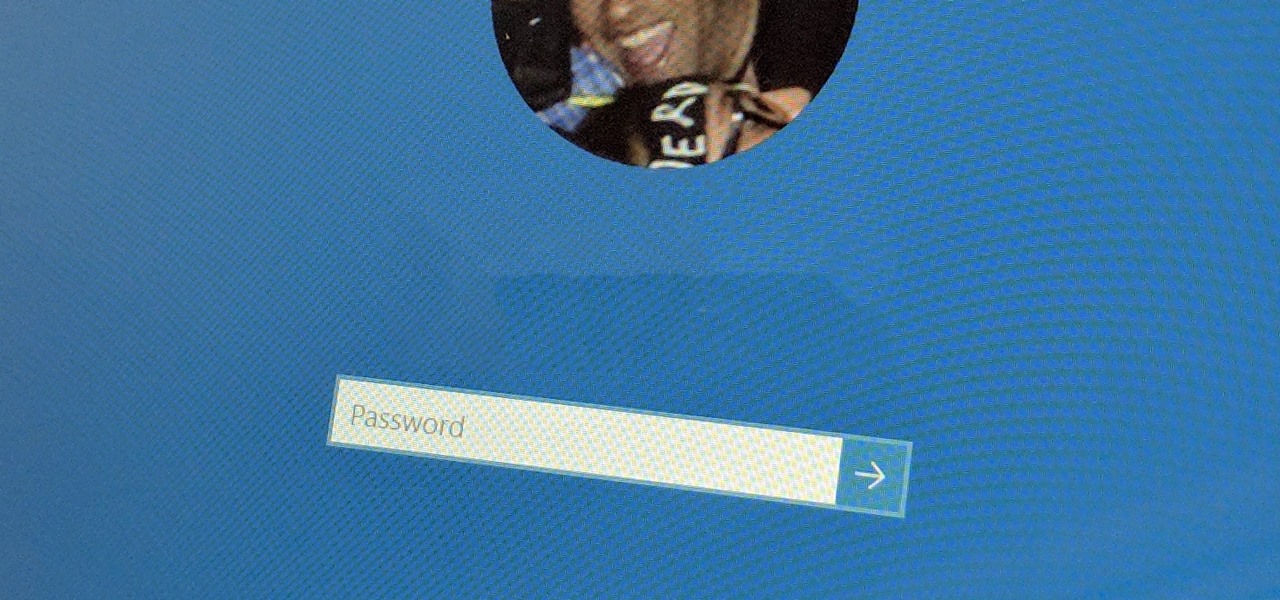
It's good to password-protect your PC to make sure that your personal files, folders, and important documents are safe and can't be modified without your permission. Though, entering the password all of the time before using your computer might frustrate you.
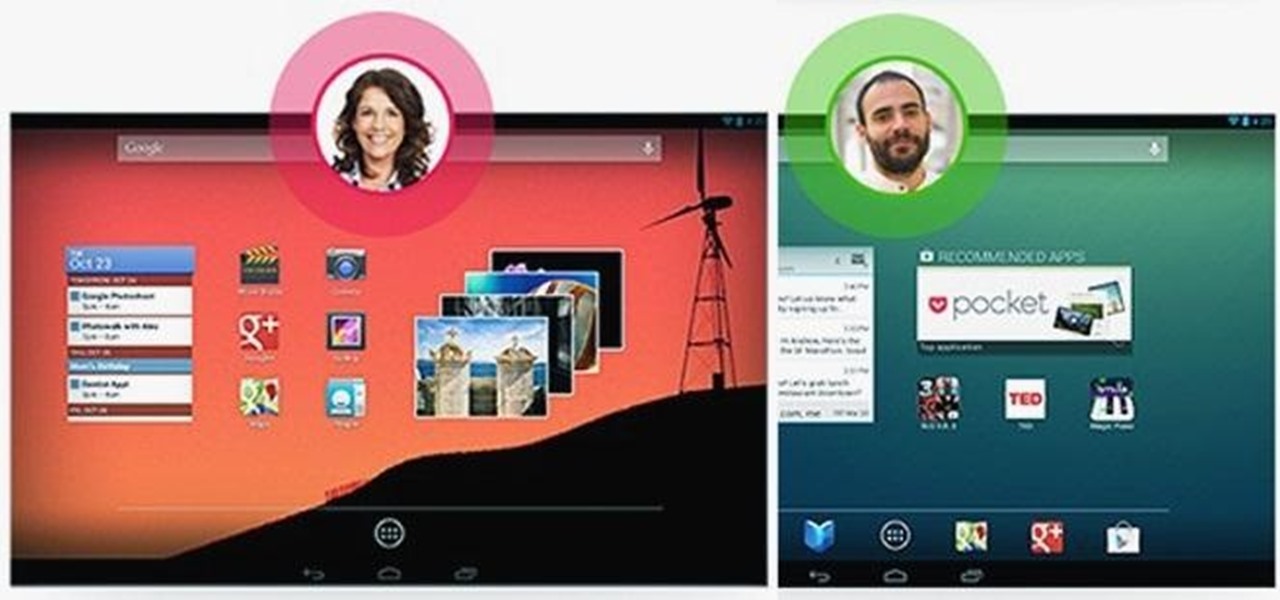
The most recent update for Android's Jelly Bean has some pretty cool new features, like better panoramic photos, gesture typing, and wireless sharing. From a security standpoint, though, the best new feature is the ability to add multiple users to one device. You can create up to 8 different accounts on Android tablets like the Nexus 7 or Nexus 10, so besides saving time hiding or protecting sensitive data, it could also save you some money. You can share a device with your family, kids, or s...

With the Samsung Galaxy S III being a hot commodity, it's no surprise that your friends might try unlocking your fancy password-protected phone. While some friends have good intentions when using your phone, there are those certain friends who get into the phone to do this... The worst scenario might be that you leave the phone around a group of friends, come back and find that all of your social media accounts have been hacked. When you yell out to your friends asking who did it, no one make...
By default, your Samsung Galaxy S III comes equipped with a few app shortcuts that are available from the lock screen. But what if you don't use those apps very much? Wouldn't you rather customize the lock screen icons on your S3 to your favorite and most used apps?

Michael Faraday was awesome. He discovered electromagnetic induction, diamagnetism and electrolysis, and he invented the Bunsen burner (before it was the Bunsen burner). Because of his work, we can make suits that can withstand 1,000,000 volts of electricity and cases to protect our gadgets from nuclear attacks.

The worst part of moving into a new place is, well...moving. It's tedious, a lot of hard labor, and it can take forever, and don't even get me started on all those labels. It's also one of the only times in your life when everything you own can be stolen at once, since it's sitting in a movable container. Rather than risk losing everything, try this DIY Moving Truck Alarm System by Tim Flint that lets you know when the loading door is opened so you can catch would-be thieves red handed.

No one likes to think about the possibility of natural disasters, but we all know they could happen at any time. Some of us are a little more paranoid than others, but wouldn't it be nice to know that you'd be protected if anything really crazy ever happened? Like the zombie apocalypse?