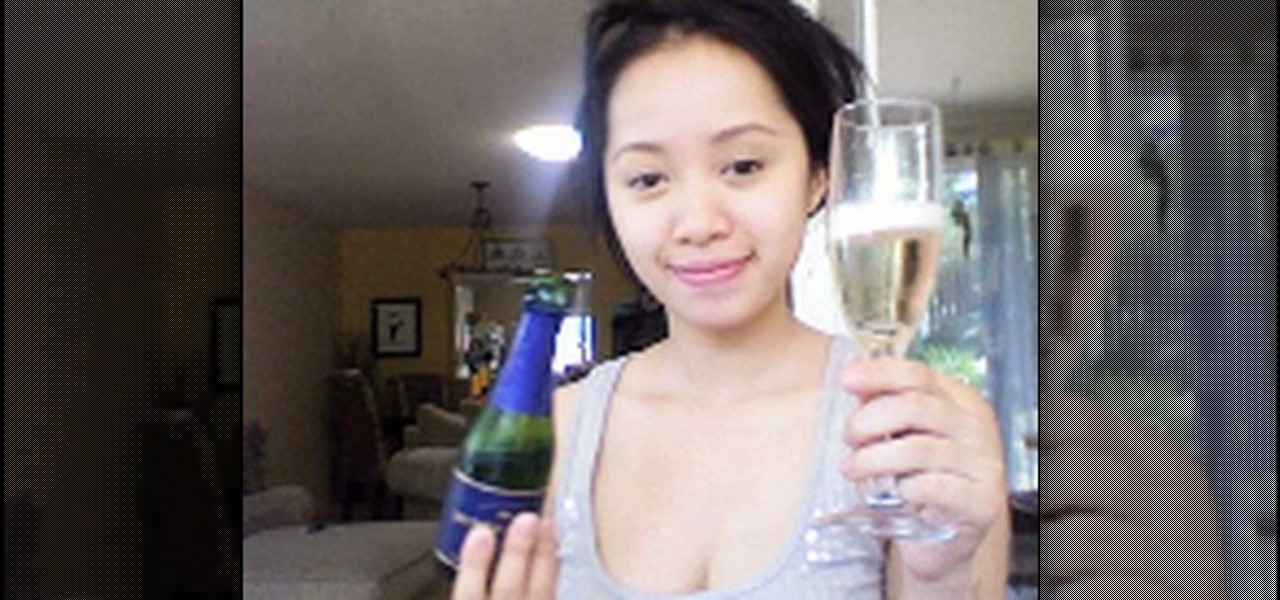One of the most annoying things about summer is mowing the lawn. Depending on how big your yard is, it can mean spending hours out in the hot sun while you could be doing something a lot more fun like watching the Olympics or making giant soap bubbles. Reclaim your summer with this remote control lawn mower that does all the hard work for you.
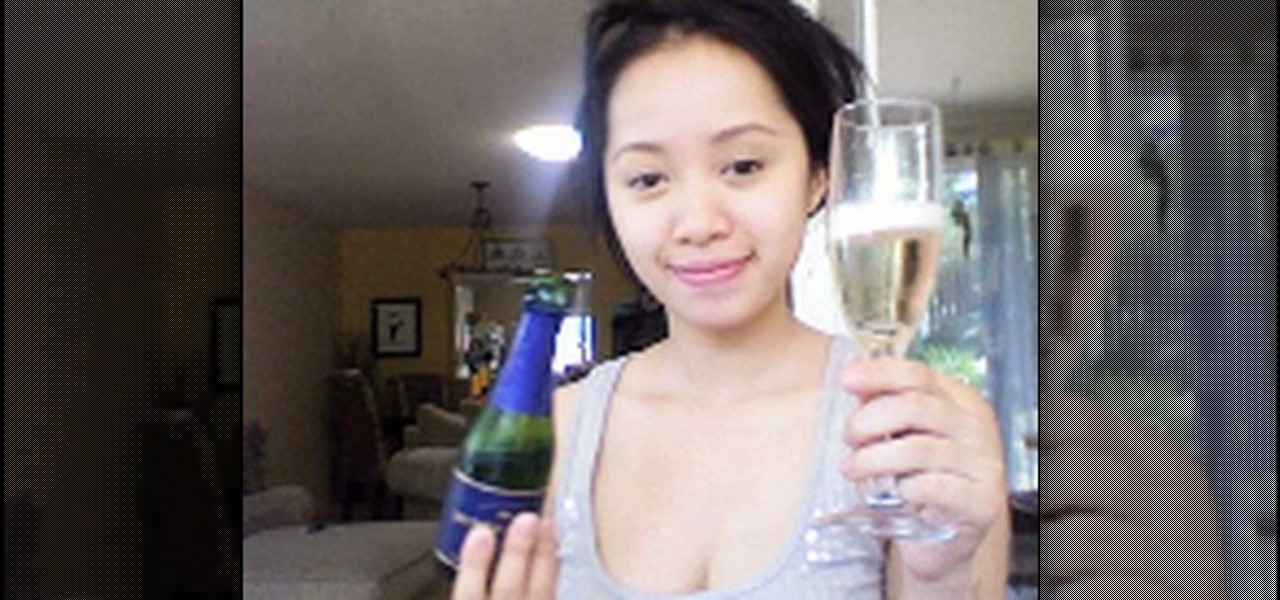
Michelle Phan presents this tutorial video on caring for your skin with champagne. You can use less than a sip of your champagne as a detoxifying cleanser/ toner.

Those moisture cracks in your concrete driveway could have been prevented. This how to video hows you how to keep your concrete driveway protected and looking good. Its a total DIY project.

In the Xbox 360 game Darksiders, you're nearing the end of the game when you get to the Black Throne, which consists of three guardians and Straga. Proceed across the bridge as it constructs itself then enter the main room of the Black Throne. Here you will find Azrael who will tell you about Straga and how he gains great power from the Well of Souls. You will need to defeat the three Guardians that protect the Well of Souls and use their power to destroy the three statues that imprison Azrae...

Ten verses are in this level of the Xbox 360 game Bayonetta. In Chapter 9 - Paradiso - A Remembrance of Time, get ready to fight Golem. From the floating clock face you can jump to the yellow floating disk. Follow the path of floating objects to the floating courtyard garden.
If you're tired of the boring old ringtones on your iPhone but don't want to shell out extra dough to buy a new one, here's an easy way to make your own.

There's nothing more maddening than opening the office fridge and discovering your lunch is gone. Put an end to the stealing with some of these strategies. This video will show you how to deter coworkers from stealing your lunch.

Video chatting over the Internet is an inexpensive way to keep in touch with your family and friends. This video will show you how to set up web video chat.

Download the P2 Step-by-Step Reference Guide. With Avid, editing footage captured with the Panasonic HVX200 camera is fast and easy. Avids system uses the same native file format as Panasonic P2 memory cards, so theres no need for any transcode, capture or file conversion process at all. You can edit directly and immediately from the P2 cards if you like or have Avid Media Composer create a rapid backup of your files. Nothing could be simpler or more immediate.

Varmints can sometimes show up during your FrontierVille game and threaten your crop production. You'll have to clobber them, which can get you food and money but costs energy. Here's a few tips to clobber varmints and protect your farm!

Shaun Alexander was an amazingly productive NFL running back. In this video, he takes some time to explain for young running backs how to hold the ball properly, protecting it from the defense and potential fumbles. Proper finger positioning and placing the body between opponents and the ball are both crucial elements.

Deer can wreck havoc on your plants and yard. No need to go to war with the deer, when with a few tricks of the trade, deer can be discouraged from feeding on your yard. The neighbor‘s yard, on the other hand, might seem that much more appealing.

In this video tutorial, you'll learn how to use the Second Copy backup application, for the Windows operating system, to protect your most important data. For step-by-step instructions on installing and using Second Copy, take a look at this backup how-to.

Keeping the hands protected from burns or rough equipment is the main requirement of welding gloves. There are a few things to look out for: quality material (all leather), reinforcements, good stitching, softness, toughness, comfort, and length. Watch this video welding tutorial and learn how to choose an appropriate pair of welding gloves.

This video tutorial demonstrates how to use Smooth-On's Encapso K rubber to create a realistic seascape display. Learn how to freeze and protect an underwater landscape sculpture.

Fast, cheap and easy! Make those rims/wheels shine and stay that way in a few minutes with this surprising method...WD 40. Don't spray directly on wheel/rim. Spray on cloth..

This flat hexagonal drink coaster is a cheap way to protect your tables from drink stains.

Marble countertops look beautiful in any style kitchen or bathroom. To help you make the most of your money, host Meghan Carter visits Vermont Marble Museum to discover how to select the right marble countertops for you and how to protect them for staining.

Learn how to mold, shape and work polymer clay for all your crafting needs. Be certain to protect your work place.

In this series of spooky videos about how to scare the heck out of your friends and neighbors, our haunted house expert tells you everything you need to know about setting up your own haunted house. Matt Cail, designer and director of the University of Washington's campus haunted house, shares the tips and advice he gained from putting the fright to university students. He begins by discussing goals for a haunted house then tells you how to achieve them with the seasoned advice of someone who...

A virtual private network is a necessary part of your arsenal if you're insistent on surfing the web privately and securely on your iPhone. The App Store is littered with hundreds of different VPN services that encrypt traffic and mask your IP address, but what they all have in common are connectivity issues.

As first reported by Next Reality last year, game developer Preloaded, in partnership with BBC Studios, has finally launched BBC Earth - Micro Kingdoms: Senses.

Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.

For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application that lets you encrypt text, photos, or archives with strong encryption using a password, keyfile, or both.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.

As you're surely aware, your phone can be used against you. Thanks to our cameras and microphones, a clever hacker can obtain access to your device and invade your privacy. But spying isn't limited to just these two sensors — gyroscopes, proximity sensors, QR codes, and even ads can be used to paint a very clear picture about who you are and what you're currently doing.

Between the Cambridge Analytica scandal and the revelation that Facebook logs your calls and text history on Android, many are considering joining the #DeleteFacebook movement. But it can be difficult to leave the site, because so much of its content is only available to active users. If you want to keep in the loop without sacrificing your privacy, you'll want to follow the steps below.

The Galaxy S9 is now in the hands of millons of excited users. Getting a new phone is always fun, but it's important to think about protecting your device. Perhaps the most popular cases for the Galaxy S9 are the official OEM options from Samsung. There are a plethora of cases, whatever your preference and needs may be. Let's take a look at each case individually, along with the pros and cons.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

Young girls, especially those who live in areas where HIV is epidemic, like sub-Saharan Africa, are particularly vulnerable to becoming infected with HIV. A vaginal ring containing the antiviral agent dapivirine has been shown to decrease the chance of developing HIV-1 in adult women over 21 and now in the first step for use in adolescents, the ring has been shown to be safe and well-tolerated in that younger age group.

A recently confirmed polio outbreak in Syria is connected to low levels of vaccination, worsened by conflict. It is the first confirmed incidence of polio in Syria since 2014. Before 2013, the last case of polio in Syria was in 1999.

Oh, Uber. It's not often to hear your name in the news and have it mean something good. You're being sued, you're crashing, your driverless program is falling behind. But I have to hand it to you; when the world is crumbling around you, you continue to fight against it. You've even made it to Canada.

Humanity is standing on an infection precipice. As antibacterial resistant grows, we're running out of options, and a recent scary case of total antibiotic resistance is a frighting view of our potential future. In the end, it was septic shock that took the life of a 70-year old woman with an incurable infection. One of few such cases in the US, her death could nonetheless be the shape of things to come.

Damn right, you don't just eat 'em. When you're done with your next Pringles can, you can turn it into a kaleidoscope, a pinhole camera, and even a solar hot dog cooker. But Instructables user TheSpodShed may have just created the most awesome way to upcycle empty Pringles cans—use them as a mini MIDI drum kit for your mobile device. This tiny drum kit will let you rock your face off without pissing off all your neighbors.

Our future technology has a lot of amazing possibilities, and few have more promise than augmented and mixed reality headsets. But these advancements come with several concerns over privacy, and if we don't understand them, we may lose control of our own data without even knowing.

So this is my methodology for this project of writing a rootkit. Please leave feedback on what is right/wrong. I tried to simplify concepts the best I could however...

Part 1: What is Popcorn Time? Part 2: What is a torrent?

In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' computer systems in order to gain a strategic advantage and to spy.