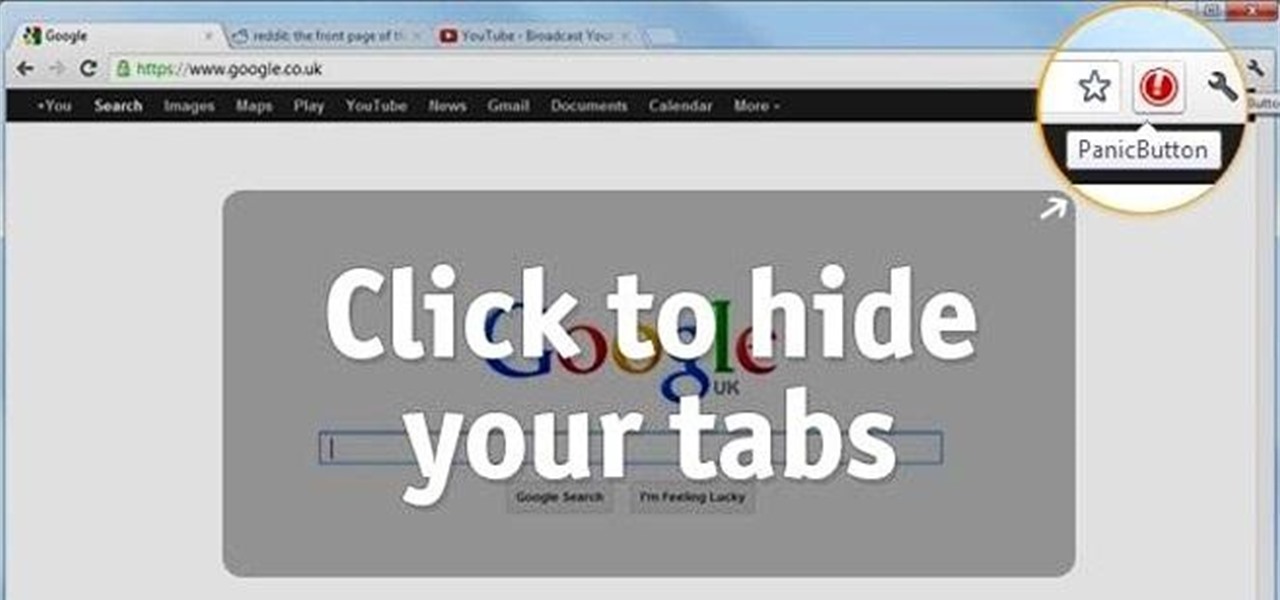
At some point or another, we've all been in that awful situation when someone walks up behind you while you're looking at something you don't want them to see. Whether you're tweeting during class, shopping for gifts online, or looking at something a little more NSFW, there are times when it would be nice to just click a button and have all your open tabs disappear.
No matter how many PSAs are published on the topic, studies continue to show that we are generally terrible at creating secure passwords and PINs. Using the same password (or variations of it) for multiple sites is another huge no-no that the majority of people ignore, and even though you should change your passwords frequently, most of us don't.

Here's a technique I used to whip up a batch of super cheap and easy to make smoke flares! WARNING: Ignition of an incendiary or explosive material may not be legal in your area, so check local laws before attempting. Use of this video content is at your own risk.

Microsoft's updated web browser, Internet Explorer 10, has only been out for a few days on Windows 8, and there is already a storm of controversy surrounding its launch.

So you've decided to go as Captain America for Halloween and you've got everything from the helmet to a sweet pair of red boots. You've even managed to get your hands on some Super-Soldier Serum (or a realistic set of inflatable muscles), so you've got the physique, too. But what's missing? His shield! In order to make your Captain America costume legit, you cannot skip the shield. Fortunately, it's pretty easy to make yourself a DIY shield—so you can fend off enemies and look good doing it. ...

If you've ever logged on to the popular music application Pandora, your password is saved onto that computer in the local storage...for good.

If you're tired of your roommate stealing your Cheetos out of the pantry or simply want to indulge in something creepy, then keep reading. With the iPhone 5 finally released, many people will soon be selling or giving away their older iPhones. But should they? Instead of ditching your old iPhone, why not use it to engage in some Big Brother type espionage? There are some really awesome ways to use your old iPhone, but spying on people is definitely the most bang for your buck. First, you'll w...

Think your roommate's been using your computer while you're not around, but don't have any proof? Worried your little brother or significant other is snooping through your stuff? Here's how to check on both Windows and Mac OS X so you can catch and confront anyone who's logging onto your computer without your permission.

Facial recognition software is being more widely used with every passing day. Your local law enforcement is probably already using it, and it will be even easier for them now that the FBI handed out its own facial recognition software to state authorities. Even the fine folks at Facebook are using this technology. Obviously, this brings up some pretty serious privacy concerns amongst most people, because honestly, who wants to be tracked? Right now, there's not a lot we can do about it being ...

There are tons of situations that require you to give out your phone number, and I think just about everyone has regretted doing so at some point. It can be incredibly convenient to have a secondary or temporary number on hand, so if you don't want to provide your real digits, you can still get the call without revealing your true numbers. And that's where Burner comes in. Burner is a mobile app for iPhone and Android that lets you create alias phone numbers that you can take out of service a...
As a pale white boy growing up in Florida, you learn how to deal with sunburns. Most people will say to take cool showers to relieve the heat, but that only temporarily alleviates symptoms. The problem is that the sun has evaporated the moisture from the skin. The answer to relieve the stinging and pain is to re-moisturize the skin. I've done this countless times and it always works.

I'm not admitting to anything, but let's be honest, most of us download content on the Web from time to time. With copyright holders laying down the law more and more often, it can't hurt to do so with caution. And even if you aren't downloading copyrighted material, you still don't want companies snooping in on your online activities. So just how do you protect yourself when torrenting? Avoid "Open Communities"

If you've read anything in the news about Skype recently, it probably hasn't been good. First, there was the controversy over the company listening to and recording users' conversations. Now, there's a new spam tool for Skype that can harvest usernames, see whether or not you're online, and even parse your log files. Image by Lloyd Dewolf

If you use Ubisoft's uPlay browser extension, you should probably get rid of it right now. An Information Security Engineer at Google discovered that the plugin has a hole in it that allows programs to be installed through uPlay, essentially letting anyone who feels so inclined to take over your computer. How the Exploit Works

Do you own an HP printer? If so, it may be vulnerable to malware attacks. Researchers at Columbia University discovered that 25% of Hewlett-Packard printers have significant vulnerabilities that put your printer in danger from hackers—even your home. With a budget of just $2,000, researchers Salvatore Stolfo and Ang Cui were able to hack into the printers using remote firmware to install malware, and in some cases even cause the printer to catch on fire. The main issue is with the printer's c...

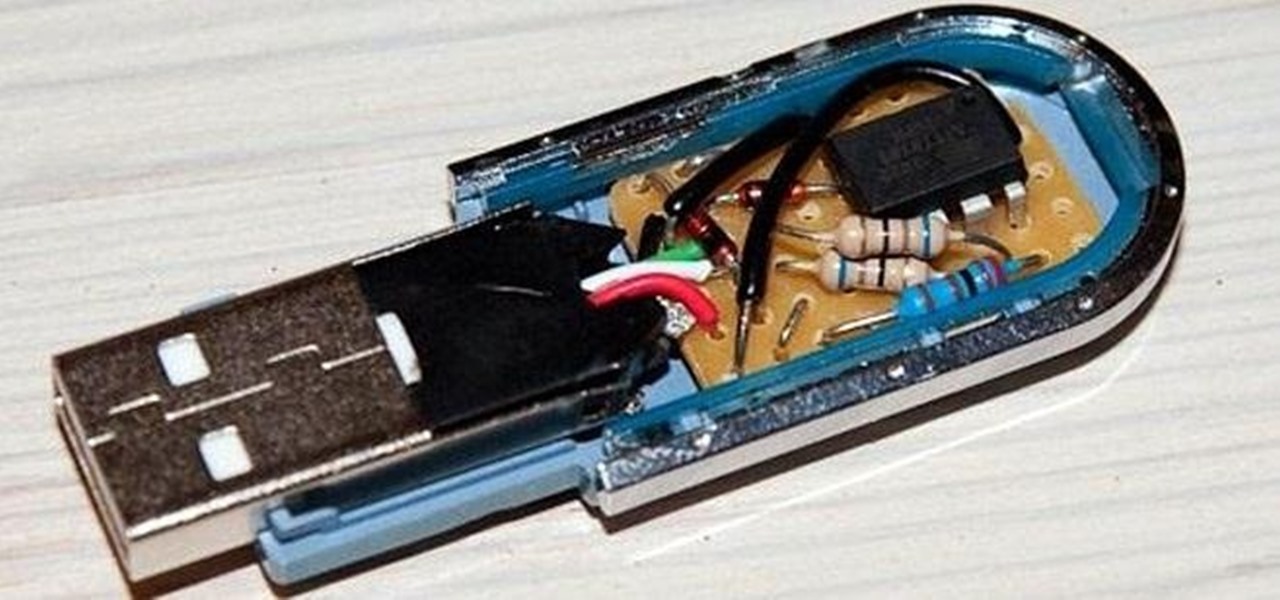
It used to be that you only had to worry about maids rummaging through your belongings in your locked hotel room. But now anyone with 50 bucks of hardware and some programming skills can hack their way in—as long as it's locked by keycard.

There's a strange grey area for "guerrilla filmmaking" on YouTube. Generally, someone shooting a video needs to get permission from the people in it to show their faces. But on YouTube, that "rule" is more of a suggestion (and sometimes not even that).

These days, news papers, online editorials and magazines are filled with news on Iran and Syria. Of course, that is expected, as such sources need to stay current to stay in the game. My concern is that most of these articles talk about what to do about these situations.

If your going to be on stage or filmed on screen you may want to wear a little makeup. Men can use subtle makeup to look young and refreshed while evening out skin uneven tones. Your eyes will really pop with a little liner smudged into the lash line.

If you want to shake up your style or pay tribute to the 90s, then bust out that crimping iron. You will bring the party with this fun and funky style that can worn down, up or added to bring a little flare to more traditional styles.

Moles can be a real problem in gardens. Unfortunately, there is no easy answer to get rid of them. The best way is to try several methods until you find one that works. Even then if you manage to catch or deter a mole it's not always the end of the problem. For much of the year moles are solitary, and have their own territory. If you catch the little fellow, his neighbor will take advantage of the tunnel system and move in. This how to video give you some ideas of how to get rid of those pest...

To much of the United States, Zika seems like a tropical disease that causes horrible problems in other countries but is nothing to be worried about stateside. It may make you rethink your beach vacation abroad, but not much more than that. However, if you live in Florida or Texas, the possibility of getting a Zika infection where you live is real — and local outbreaks are more and more a possibility.

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...

Welcome back, my rookie hackers! Now that nearly everyone and everyplace has a computer, you can use those remote computers for some good old "cloak and dagger" spying. No longer is spying something that only the CIA, NSA, KGB, and other intelligence agencies can do—you can learn to spy, too.

At one point in the '90s, about fifty percent of the CDs produced worldwide had an AOL logo. About fifty percent of the CDs in my home still have that AOL promise of 500 free hours on them. Though they never got me to join their internet service, I did get a lifetime supply of coasters. Thanks to the rise of high-speed internet access and bigger and better hard drives, there's no reason for companies to snail mail any more of those obnoxious plastic discs.

This is an instructional video on how to wrap your hands with wrapping tape in preparation for boxing. The instructor shows you how to use tape to wrap, and where to place the tape. You start by wrapping your wrists multiple times. Then you go over the base of the thumb and back over the wrist twice. Then you wrap your knuckles. The instructor suggests that you can use some foam in this stage to protect your knuckles further. Finally you go between your fingers, back over the thumb and then r...

John, with Your Guide to Pro Wrestling, demonstrates how to do a butterfly suplex. The butterfly suplex should only be done with supervision by trained professionals. To do a butterfly suplex, lead in with a toe kick and bring your foot up into your opponent's stomach and then down. Hit your opponent in the classic bent over position. The set up for the move is similar to the pedigree. The difference is that you want to get your opponents head on your side instead of between your legs. Hook y...

This video explains how to put an over grip on your tennis racket. To begin you need to remove the plastic that is protecting the grip that you plan to put on your tennis racket. On the other side of the grip there should be a paper that you can remove so that you have a stick mark. Place the sticky mark on top of the handle and start to wrap in line with the end of the handle. Wrap clockwise if you are a right handed player or counter clockwise if you are left handed. Stretch the grip a litt...

With Apple's Photos app, you no longer need a third-party tool on your iPhone, iPad, or Mac to blur or pixelate faces in your photos, helping you safeguard identities when sharing online.

Many of us choose to use an iPhone — as well as other devices in the Apple ecosystem — because of the company's dedication to user privacy and security. If you need more proof of that commitment, look no further than iOS 14.5, released April 26, which adds new tools to protect our data while browsing the web and more control over the data installed apps collect on us.

Your sensitive personal data should be strongly protected, and it's never more vulnerable than when you are online. The internet connection is a prime avenue of exposure, and email is one of the least secure forms of communication. Fortunately, there is an easy solution to both of those problems.

We all know that using a VPN not only has a ton of benefits but is essential in our digital age. But did you know that you can get access to your own industry-leading VPN for life with one one-time payment? Even better, we've found an amazing deal on one right now: for a limited time, a YoData VPN: Lifetime Subscription is on sale for just $17.99. That's 69% off the regular price of $59.

Now that more people are working from home on unsecured networks and personal devices, hackers are having a field day accessing everything from private browsing histories to personal banking information. A virtual private network (VPN) is the first and most important line of defense when it comes to protecting all of your devices from digital intrusions, but not all VPNs are created equal.

Mobile privacy is one of the most pressing security issues in existence. Since we carry our phones with us everywhere we go, we need to ensure that we're safe from prying eyes.

With millions of people working from home as a result of the coronavirus outbreak, hacking is on the rise. Nefarious black hats are taking advantage of the fact that workers have been forced to abandon their secure office networks in favor of home wireless connections. And white hats are spending even more time at home trying to be the next great ethical hacker.

The only thing better than programming MicroPython is programming MicroPython over Wi-Fi. So once you set up MicroPython on a microcontroller and have it on its own power source, you won't need to use a data cable to connect to it whenever you need to interact with it, program it, upload files, or grab data.

As protests surge in the wake of George Floyd's murder by a Minneapolis police officer, powerful photographs and videos from the demonstrations have gripped the world, putting our nation's very real and very justifiable widespread civil unrest out into the digital world. Unfortunately, these pictures could put you or others in danger if precautions aren't taken before uploading them online.

The Los Angeles Rams are the latest NFL franchise to introduce new or modified uniforms for the 2020 season, joining the Atlanta Falcons, Cleveland Browns, Indianapolis Colts, New England Patriots, Tampa Bay Buccaneers, and their neighbors, the Los Angeles Chargers.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

MIT artificial intelligence researcher Lex Fridman recently asked SpaceX and Tesla founder Elon Musk possibly the best question he's ever been asked: What would he ask a hypothetical AGI system (an AI system with human-level intelligence and understanding) if he only had one question?







































