When Apple announced its new iPhone 7 and iPhone 7 Plus models in San Francisco, one of the biggest new features was an "IP67" water-resistance rating. Couple that with a few official renderings that show the new iPhone covered in water, and you'd probably arrive at one logical conclusion: The iPhone 7 is waterproof.

While it may not sound scary right off the bat, Blue Coat Systems now has an intermediate certificate authority. If you don't know what a certificate authority (CA) is, or who Blue Coat is, who cares, right? But you should... whether you use Mac or Windows.

Today's pollution, hectic lifestyle, inadequate sleep and no time for pampering can leave your skin lackluster resulting in drying skin and making dry skin drier ultimately causing the early appearance of wrinkles and aging. A good fruit facial helps relax your skin from deep inside and the proper messaging gives it a rosy glow by increasing blood circulation imparting your face with a luminous glow. These are even better because they are natural and chemical free unlike the artificial facial...

A VPN service is almost an essential these days. Good ones can block ads, prevent tracking cookies, encrypt your internet traffic for better security, and even spoof your device's location to bypass geo-restrictions — all things you should be concerned about in the age of NSA snooping and Facebook data mining.

When Google released the Nexus 5X and Nexus 6P, they added official support for fingerprint scanning to Android's main code base. On the surface, this was done to ensure that the fingerprint scanner in their own devices could be used to its full extent, but because it was added to AOSP, this meant that the new Fingerprint API could be used by any Android manufacturer.

One of the best qualities about fresh bread (such as sourdough) is a thick, crispy crust—which is easy to create in a commercial oven, but can be tricky for home cooks to replicate. Luckily, the the trick to baking a professional-style crust is a simple one—just bake your loaf with steam using one of these three methods to achieve the perfect, crispy crust.

In this series you will learn how to use PHP to perform attacks, gather information, and setup backdoors. Along with performing attacks you will learn how to protect yourself from them. In this part you will learn about PHP as well as install Apache and PHP. What you'll need for this series

In a letter dated February 16th, Apple CEO Tim Cook responded to the FBI's demand that Apple create a "backdoor" to bypass the encryption on an iPhone used by one of the perpetrators of last year's terrorist attack in San Bernardino, CA. Cook began the letter by stating that Apple has "no sympathy for terrorists" and has cooperated in giving the FBI all of the information that it has available.

SentrySafe puts all sorts of measures in place to protect your valuables and important documents. This particular SentrySafe has an electronic lock, four 1-inch bolts to keep the door firmly in place, pry-resistant hinges, and it's able to withstand drops of up to 15 feet. That all sounds great, until you find out that you can open this safe—and pretty much every safe like it—in a matter of seconds using only a magnet. A rare earth magnet, to be precise.

Samsung trademarked the name Gear 360 a few weeks ago, and today it has been confirmed that the Gear 360 is a spherical virtual reality camera that will accompany the much-anticipated Galaxy S7.

Screenshots are an indispensable tool when it comes to relaying information about what's currently showing on your monitor. Whether you need help troubleshooting an issue or you just want to save and share a protected image, screenshots are often your best bet.

Winter is already here, and when Jack Frost is nipping at your nose, he tends to nip on your wallet, too.

Cake decorating is one of those activities that used to leave my hands sticky and my spirits dampened. No matter what I seemed to do, the final result always ended up looking like a preschool art project.

Computer system authentication is critical to keeping systems safe from unwanted users, intruders, and abusers. Basically, authentication is the process of the potential user proving they are an authorized user.

In an age where restaurants can charge $20 for eggs Benedict at brunchtime (if you're lucky enough to even get a reservation on a Sunday), many people long for a way to create this classic dish at home. But once you've taken pains to perfectly poach an egg and gently crisp your sourdough, the problem of the hollandaise still lies before you. The key to any good hollandaise sauce is to apply enough heat to cook the egg yolks, but not enough to scramble them. The minute the eggs begin to solidi...

The increased sophistication of smartphones and apps have allowed us the luxury to never leave our homes. Everything from coffee to food to dry cleaning can be delivered straight to your door without ever leaving your couch, which can can be a godsend during the winter months when you'd rather not risk leaving your warm bed. But during the summer, you gotta ditch the comforter and go enjoy outdoors.

When you think of bivalves, such as manila clams and oysters, you tend to think of the meat as being nicely tucked in the shell. Anything else would be scary, right?

At its core, grilling is the simplest form of cooking. You create extreme heat, you put a piece of food on top of the heat, and then you sit back and watch the magic happen. Yet despite the inherent simplicity in grilling, there are a million ways to make it more complex, more unique, and, yes, even more flavorful.

Here at Food Hacks, we're very fond of finding ways to regrow food. That means taking things like carrot tops and leftover bits from garlic, onions, chives, and other herbs and aromatics to create mini reusable herb gardens.

Tomatoes are the perfect barometer for kitchen knives and knife skills. If you've ever watched an infomercial for a set of knives, you've surely seen the enthusiastic host waxing about how well the knives cut tomatoes. And if you've ever had your knives sharpened, you've most likely tested them out on a tomato.

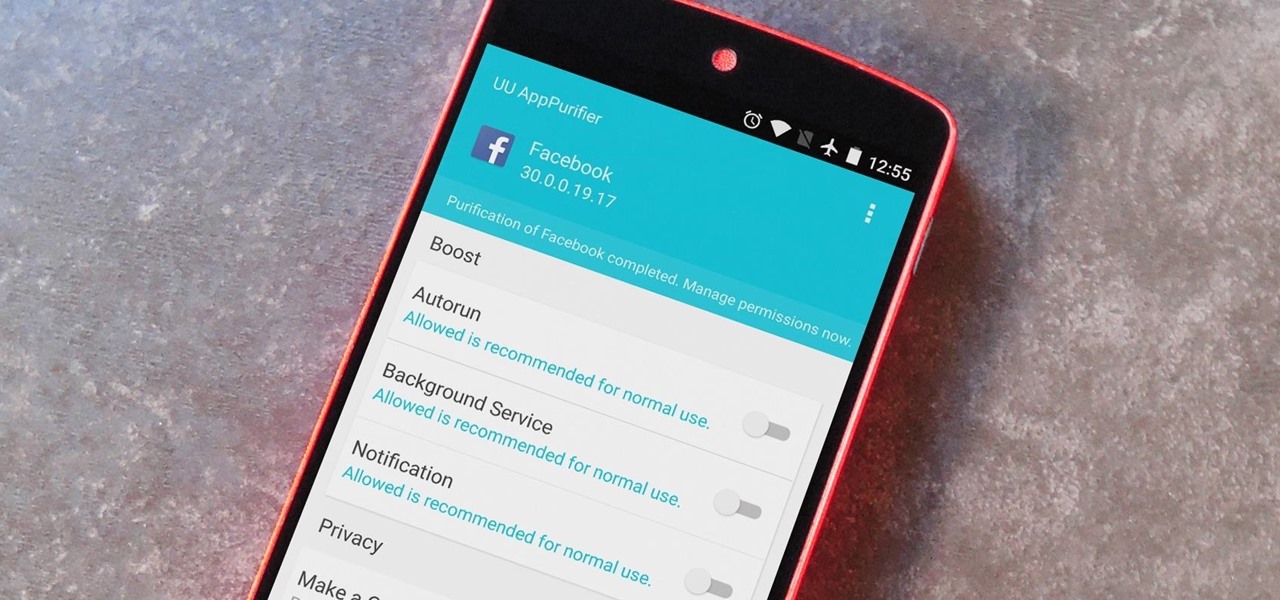
When it comes to app permissions, Android takes an "all or nothing" approach. You have no granular control over what data apps can access, so the only way to prevent an app from seeing your location or starting up on boot, for instance, is to not install the app in the first place.

Some people are of extremely secretive nature. They do not like sharing their personal events in their lives with anyone. Thus people around that person wont be able to figure out details on their life's personal matters. It is not like they want to hide some mysterious secrets from the world, but it is just their nature that they do not want others to know much about them or are too shy to share their feelings with others. Being secretive is neither good nor bad, it is just how they are.

Smartphone users often wish for a privacy, where no one is able to poke his/her nose in their personal stuff. Unfortunately, none of the smartphones have been able to guard their privacy in this fashion. Smartphones usually come up with none or almost negligible built-in security to serve your purpose.

When you have a parent who cooks—and has you act as sous chef—the kitchen automatically becomes a less intimidating place. In other words, kids who know their way around the kitchen will most likely become adults who cook for themselves, which also means that they'll eat more unprocessed whole foods, save money, and maintain a healthy weight.

Apple's Touch ID, introduced on the iPhone 5S, has definitely made my life a little easier. Not only can I unlock my device, I can use the tech to log in to websites, make purchases through iTunes, and buy groceries at Walgreens using just my fingerprint. Still, as awesome as Touch ID is, it's pretty limited as to what it can do on native apps.

I misplaced my iPhone 6 just a few weeks ago, so I know firsthand that losing an iPhone sucks. Luckily, my tale didn't have a bad ending.

As far as wallets go, mine is as full as they come; think something like George Castanza's overstuffed wallet on Seinfeld. I've got receipts, pictures, and tickets jammed inside, but what takes up the bulk of the space are all of the cards—credit, debit, gift, rewards, customer loyalty... I've got pretty much any card you can think of squeezed in. While it is a strain on my rear end, there's nothing I can do besides keep some of the cards elsewhere. However, looking for them when I need them ...

Our workdays are typically filled with one thought: get as much completed as possible. Whether you face an inbox filled with tasks or just a project or two, both our bosses and our inner workhorses encourage us to knock out as many tasks as we can each day. But is being super-productive the best course of action for our minds and our employers?

App-locking apps have been around for a while, but none have had quite the panache of developer Fazil Kunhamed's latest offering, Oops! AppLock. While others use a PIN or password to restrict access to apps that are installed on Android, AppLock uses a stealthy volume button combo.

It's a shame that one of the world's tastiest foods can be such a pain to prep. Most cooks are familiar with this conundrum: chopping or crushing garlic releases a pungent liquid that causes bits of garlic to stick your knife and hands, creating a messy affair. So what is going on here? The common assumption is that the garlic is releasing some kind of oil, but the truth is that this liquid rinses away easily in water. Yet one of the basic precepts of chemistry is that oil and water don't mix.

One of the biggest improvements in Mac OS X Yosemite came to the Spotlight search feature, allowing users to not only search through their applications, but also their emails, text messages, iCloud, and the web.

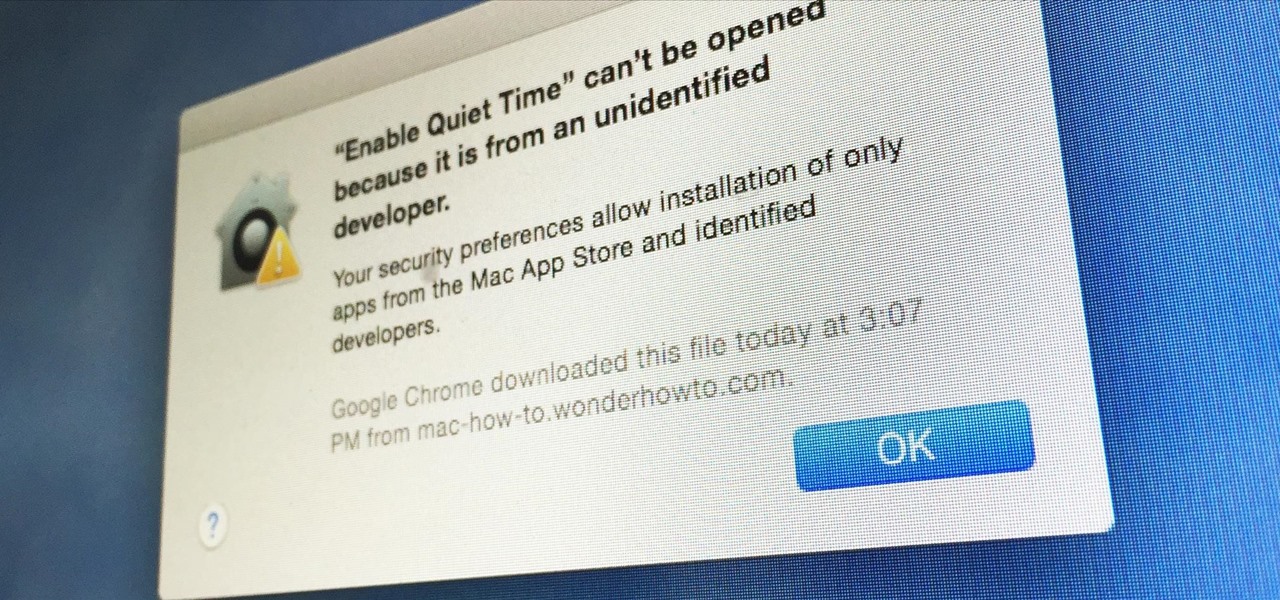
Apple has a built-in way to protect you from opening up potentially malicious apps on your computer in Mac OS X Lion, Mountain Lion, Mavericks, Yosemite, El Capitan, and macOS Sierra. This setting, named Gatekeeper, will never stop you from installing apps from the Mac App Store, but it could from anywhere else. If it's an app you're sure you want to install on your system, here's how to do it.

Losing your phone is a much bigger ordeal today than it was just 10 years ago. Our smartphones carry with them lots of sensitive data that, in the wrong hands, is capable of being used for identity theft and fraud.

One thing I absolutely cannot stand is lag when I'm gaming. Every time I'm about to beat my killstreak record on Call of Duty, my internet connection drops and I'm a goner. It never fails. This usually happens because someone else on my Wi-Fi is streaming a movie or downloading a huge file.

It started in Australia, and now seems to have made its way statewide—hackers are remotely locking iOS and Mac devices, holding them for a $100 ransom. Users awoke to the loud "lost iPhone" ringtone, with a message on their lock screen stating that "Oleg Pliss" has hacked their device, and that "they" will unlock it after being sent $100 through PayPal.

It's been rumored ever since the 2012 release of the Kindle Fire, and now Amazon's first smartphone is set to debut a little later this year.

Whether it's embarrassing pictures and videos on your smartphone, or files you just don't want anyone reading, there are plenty of ways to hide them. For most devices, that means installing third-party apps like Gallery Plus - Hide Pictures, Sectos - Photo & Video Vault, TimeLock, or Hi App Lock.

No matter how careful or decent you are, there will always be pictures or videos that you want to keep private. They say a picture is worth a thousand words, but if someone were to go through my photo gallery, only one word would be coming out of my mouth—"%@&#!!"

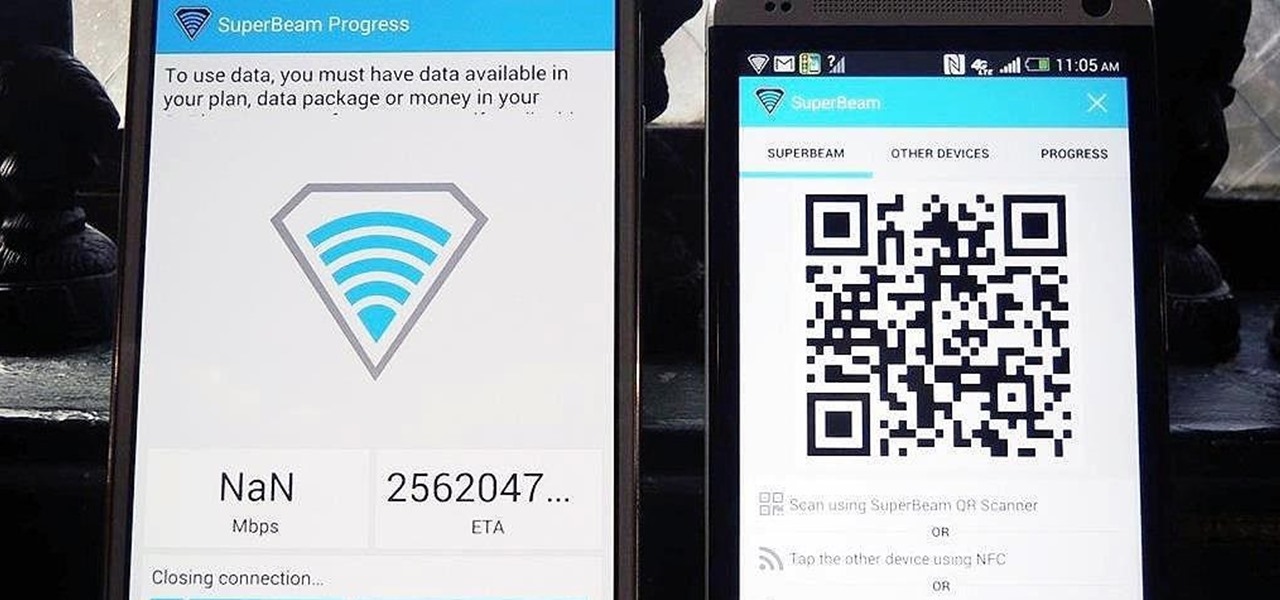
Sending and receiving files between Android devices has no shortage of options—Bluetooth, email, MMS, and Wi-Fi are just a few of the more popular ones that we use.