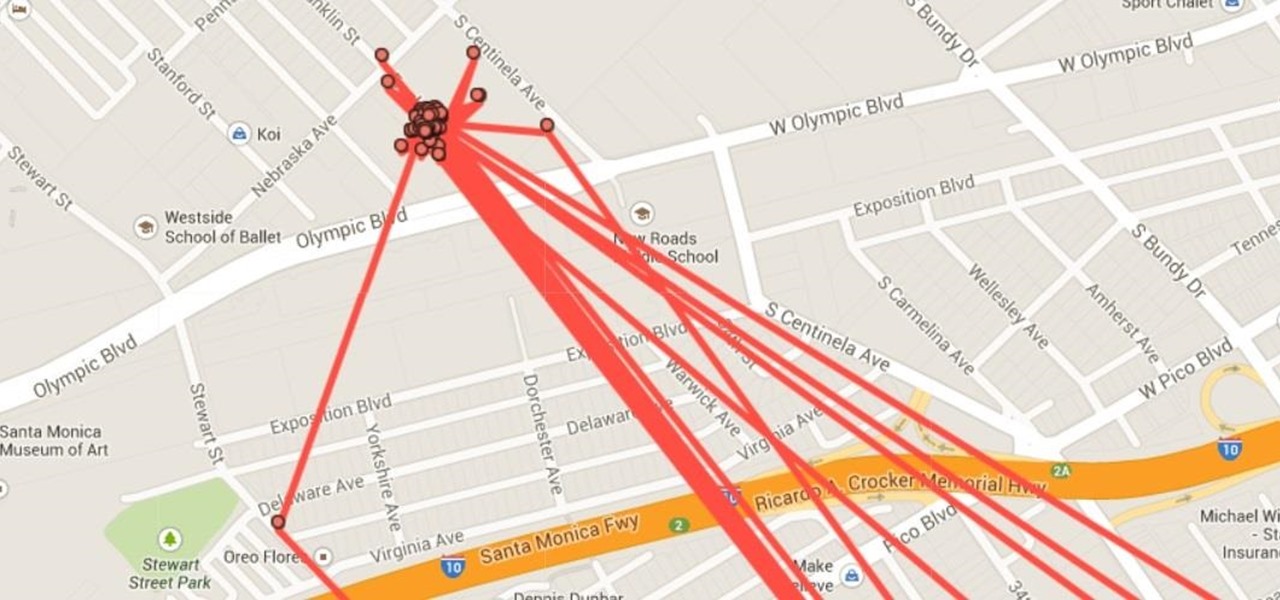
PSA: Google's Keeping Tabs on Your Location & Here's How to Stop Them
We're only years away from a complete Robot Revolution and Google Inc. will surely be leading the charge.


We're only years away from a complete Robot Revolution and Google Inc. will surely be leading the charge.

In spite of the degree of difficulty it is to install, CyanogenMod has steadily climbed the ladder to become one of the most popular third-party firmwares for Android devices.

Last summer, Universal Pictures released the sequel to the popular 2010 animated film Despicable Me, bringing back everyone's favorite characters—the Minions. They're adorable, yellow, and they speak a gibberish "Banana Language." What's not to love? If you're planning on dressing yourself (or your kids) as Minions for Halloween this year, you'll be in good company. There are tons of costumes out there you can buy or make, and here are five of the best DIY options for you.

The closest I've ever been to first class was when I was a young kid running up and down the aisles on a long international flight. I remember being in awe of how big the seats were and how much food was available. Ever since that moment, I've made it my life goal to earn enough money to make first-class flights a regular occasion.
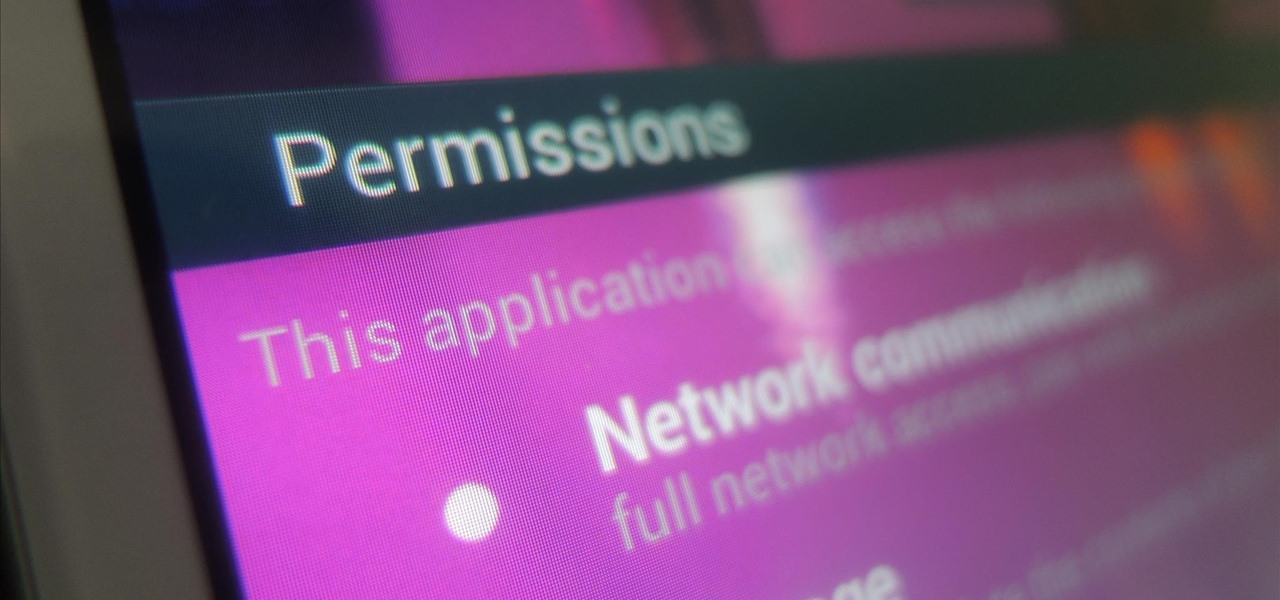
While we're usually responsible for leaking our own private information through mediums like Facebook, there are other times when we mistakenly and unwillingly allow certain applications to scour through our personal data. Some apps may have enabled permissions for internet access, thus allowing it to share said data with its external servers.

The transition from an iPhone to a Samsung Galaxy Note 2 or other Android device can be a tough one. A vastly different operating system and the ability to customize anything and everything might be too much for some people. Taking in all that new, while having to let go of the old, can be as daunting as climbing Mount Everest.
A wave of shock and anger swept across the country after Edward Snowden released private documents recounting the U.S. government's secretive mass surveillance programs. Although some of the fear was unwarranted (they don't read your emails or listen to your calls), many scrambled to find privacy of new heights for protection from the all-watchful eye. While the government may not be tracking you down, there are a myriad of other candidates that fill that Big Brother role—and I'm not talking ...

Whether or not you believe that the government is snooping around in our private emails, texts, and phone calls, it wouldn't hurt to protect ourselves a little better in the digital realm.

You know that sinking feeling you get when know you've just done the unthinkable? It's the worst. Sending that ridiculous text message to the wrong number or posting a shameful tweet during a weekend bender.

Wondering how to get long hair naturally? How do you grow your hair? In this video Rachelle and Sam give you 10 tips to get those long locks naturally!

Most people wouldn't think of butter as a flammable substance, but in this project—it definitely is! We're making emergency candles that burn for hours using just some toilet paper and a bit of butter!
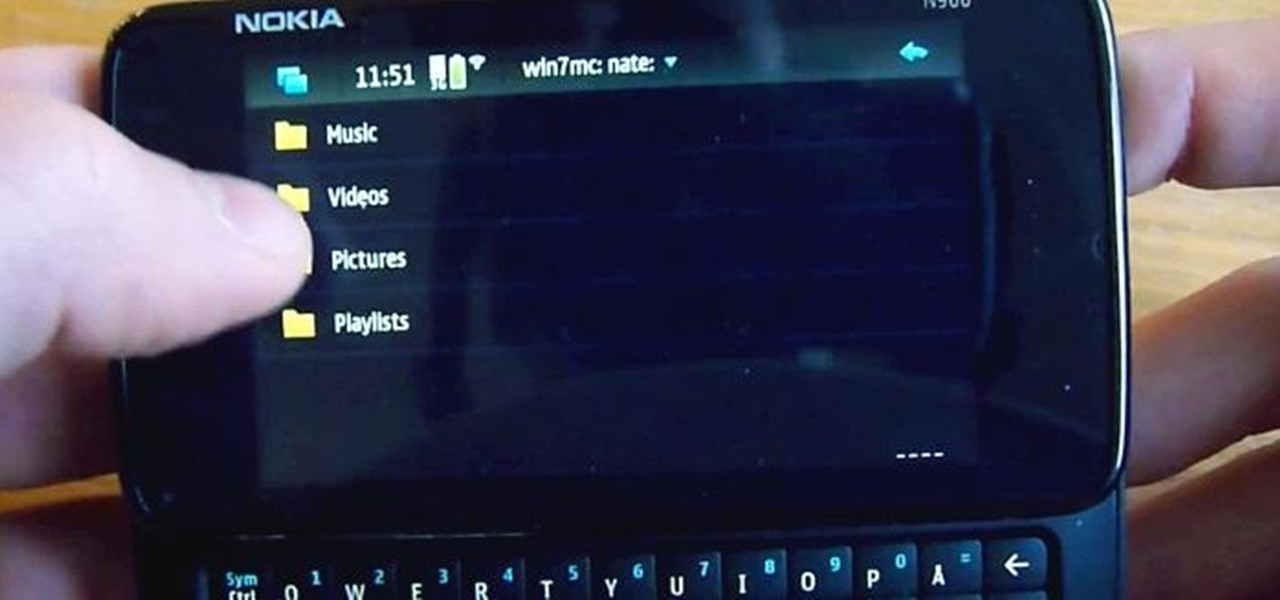
Having access to your computer from your cell phone is an extremely useful feature. Whether you need to edit documents or send files that are on your home desktop, or you simply want to watch movies you have saved on your computer, access is key.

Skype is a great way to stay in contact with friends and family over the internet, and people tend to share a lot in their chats, so why not try and find a way to hack it! Once a Skype account is hacked, you can view all conversations within the last three months, see how long each video call was, and even access files that were shared through chat.

You've probably noticed how we like to stress the importance of a strong password. After all, there are still people out there who continue to use passwords like 123456 and even just "password". But passwords aren't the only barriers that protect your information.

RFID chips are everywhere. They're in passports, credit cards, and tons of items you've bought in the last 5 years or so. Big retailers like Walmart started using tracking products with RFID as early as 2004, and today, they're used in everything from mobile payments to hospital record systems. Chances are, unless you're a hermit (in which case you wouldn't be reading this anyway), there's an RFID tag within a few feet of you. Photo by sridgway

For those of us with small children, bath time can be very fun. Kids usually love splashing about and playing with their toys in the water! One thing they don't love however, is getting water in their eyes or on their face.

Hello! I want to share a few hints about staying literally cool when the temperature of the air outside rises incredibly. So, if you're in a very hot area, please continue reading!

A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).

This video tutorial shows how to hack FarmVille (05/06/10). At this point, it seems like people are more interested in hacking FarmVille than they are in actually playing the thing. This video will teach you how to use Cheat Engine 5.6 to get unlimited tractor fuel, improving your farm's efficiency and increasing your profits. In the game, of course. You'd have to do work to get real money.

Mentoring is a way to help others and improve your community. There are established mentoring organizations to join or you can go seek out those already in your life who you can help with your time end knowledge.

Do you want to sell your car? It's important to make sure that you have everything in place before you hand off your car. Do your research, and everything will fall in place. Watch this video to learn how to cancel your license tags when you sell your car.

Is your fridge getting out of control? Can't identify that raunchy smell that has invaded your ice box? Can't find your ketchup? The best way to alleviate these problems is by organization. Organizing and keeping your fridge tidy is the best way to go, but it could be hard in a roommate situation where one said roommate will never give a damn. Nonetheless… chill out! Use these helpful tips to get your refrigerator organized.
If you like to shop online then it is extremely helpful to have a PayPal account to safely make your online purchases. Help reduce your risk of identity theft by using protected methods like PayPal when your credit card information is involved.

This how-to video demonstrates how to use a copper wire stripper.

Apple's Notes app has an important feature many users overlook, yet it's arguably the most crucial thing you should use for all your notes synced across iOS, iPadOS, macOS, and iCloud.com. And Apple makes the feature much easier to use than years before, so there's no reason you shouldn't be using it.

After updating to iOS 14 or getting a new iPhone with iOS 14 preinstalled, you'll notice orange and green dots that occasionally appear at the top of your iPhone. These dots appear on all supported iOS 14 devices, from the iPhone 6S to the iPhone 12 Pro Max, and are there to protect you, but how?

Apple announced four different iPhone models during its Oct. 13 web-only event, but only two of them can be purchased this month: the iPhone 12 and iPhone 12 Pro. Preorders have already started for the two smartphones, and you could have one in your hands as early as Oct. 23, if you're lucky. To help keep your shiny new iPhone protected from scratches and cracks, try one of these cases.

If it has an internet connection, it's got a huge attack surface for hackers. But what makes your phone even more dangerous is its portability and the collection of sensors it houses that can be just as good at tracking you as the camera and mic.

VPNs add a protective layer between your data and your internet service provider (ISP) or bad actors (hackers), so it makes sense they've become so popular lately. Probably the most common one of these is NordVPN, so we explored its mobile app to find all the options worth checking out.

With protests springing up across America, there's a chance you may have your first interaction with law enforcement. Many demonstrators will have their phones in-hand to film the action, which, sadly, could prompt an officer to demand the device and any self-incriminating data it may contain. Before this happens, you should know there are tools at your disposal to protect your data in such situations.

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

You need a break from gloomy coronavirus updates. We all do. The unrelenting stream of doom and negative news is both helpful in terms of keeping ourselves and our families safe, but it also has the unfortunate effect of increasing our anxiety. When will this end? How bad will it get? Is there reason to be hopeful?

While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

In a time where we're more connected than ever, privacy and security have never been more important. Maybe you're not concerned, but I'm sure there's someone in your life who is, and shopping for them can be daunting. However, with these gifts, you can provide them the tools they need to enhance their protection.

The Files app received a big update in iOS 13. Before, it was limited to local and cloud-based files, but now you can access data from external storage devices, including SD cards and USB drives. But before you try to connect your favorite card or drive to your iPhone, there are a few things you need to know.

You may have recently seen a plethora of Instagram users, including celebrities and politicians, sharing a screenshot declaring that the platform will implement a new "rule" where it would own and could use your photos and videos however it wishes. The screenshots are part of an internet hoax, one that's been around in one way or another since 2012, but what can Instagram actually do with your media?

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

Planning a vacation overseas can sometimes feel overwhelming with the number of things you need to remember before heading out. Since smartphones keep us connected at all times, it's essential that you have everything you need here as well. Unexpected events can arise while on your trip, and you should be prepared for anything like a survival expert.
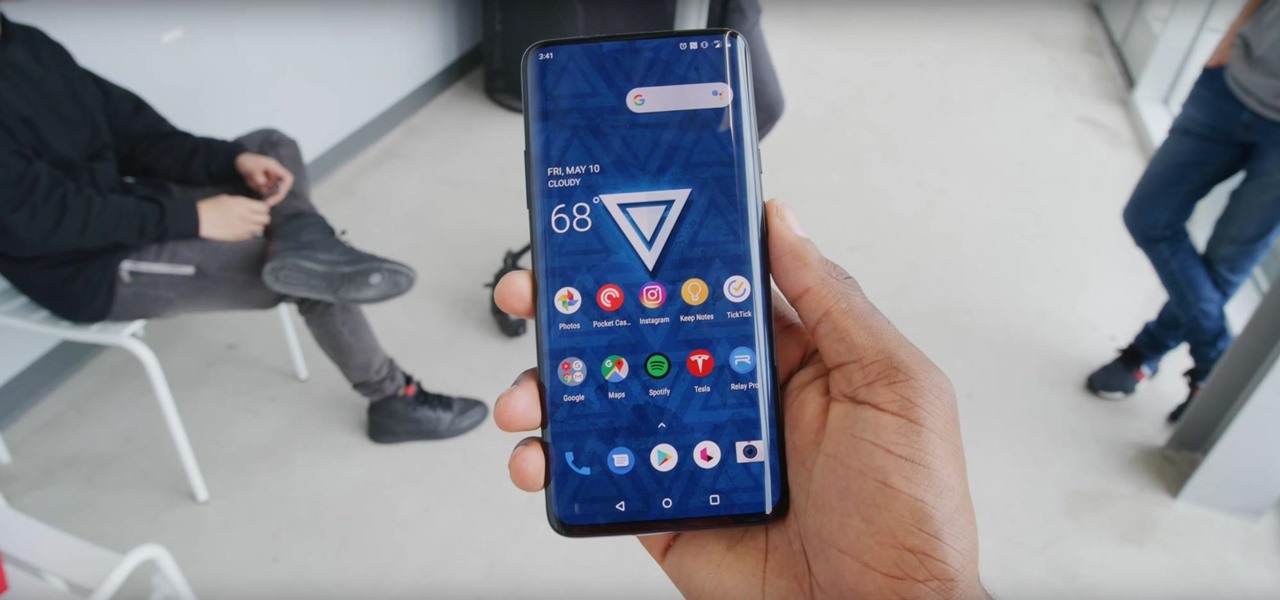
The OnePlus 7 Pro is definitely a beast on paper. With a specs page that ticks virtually every box and a price point that undercuts the competition by hundreds of dollars, it's hard to overlook this phone. But before you get too excited, know that OnePlus has repeatedly shown to be misleading with their official specs.