Alphabet's moonshot factory, X (formerly "Google X"), is a secretive place, but it seems that when they are close to graduating a project, then they need to staff it up quickly. Watching for these job ads is one easy way to know they're close to budding off a baby.
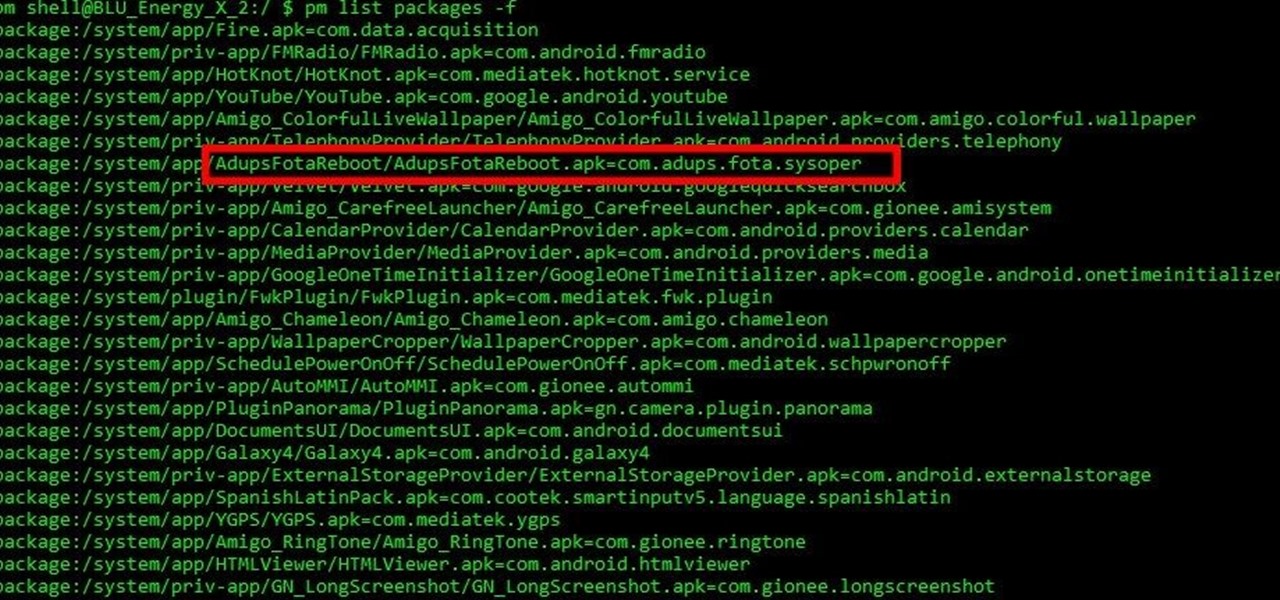
Mobile security researchers at Kryptowire recently uncovered spyware preinstalled on hundreds of thousands of Android smartphones by FOTA provider Adups which was gathering personally identifiable information (PII) such as call logs, app usage data, and even the full contents of text messages and sending these to a third-party server—all without the users' knowledge.

Starting with the Priv, BlackBerry's become an Android manufacturer. This move gives BlackBerry's phones access to Google's sizable app store, but it also presents several hurdles to keeping the security brand they've built intact.

When the Samsung Galaxy S7 and S7 Edge came to market in 2016, they were universally praised as being the pinnacle of Android smartphone design, even topping Consumer Reports' smartphone ratings.

Welcome back, my novice hackers! You have probably heard of the Panama Papers hack by now. This was a hack of the servers at Mossack Fonseca, a major law firm in Panama. This law firm specializes in assisting the rich and powerful to hide their wealth from taxes and scrutiny by creating tax havens overseas.

Plastic wrap is, arguably, man's greatest invention—or at least, the 2000 Year Old Man thought so. Its primary use is to protect food from getting dried out in the fridge or on the counter; but if that's all you're only using it for, you're missing out.

Welcome back, my budding hackers! Digital forensics is one of IT's most rapid-growing disciplines. All hackers should be familiar with digital forensics if for no other reason than to protect themselves. More than one hacker has been apprehended because they were unaware of the evidence trail they left behind.

Creamer, milk (whole or skim), sugar, or even butter—you've probably added at least one of these to your coffee to improve its taste at some point. If you're looking for something different, though, try a new twist with a dash of cinnamon. This sweet, sharp spice can do so much more than improve coffee's taste, and I've got 10 examples for you to consider.

Alright so last time I gave you a homework assignment. This week we're gonna look at my version of the UDP-Flooder.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

Greetings fellow hackers. This tutorial is about creating "safe" passwords. This is different from strong passwords. Safe passwords is just creating a password that is not used by someone else or colleague, my definition. But how do you prevent something like this from happening? Of course you won't ask your friend if s|he is using the password you are about to create. Before I show you some of my tele-psychic powers like Professor Xavier, you might want to read this for advice on creating "s...

If you're completely new to Android, you're in for a treat with all of the software tweaks and customization options that your smartphone or tablet offers out of the box. But if you really want to take things to the next level, the ability to mod your device expands exponentially when you're rooted.

You want to become anonymous, and dont want your IP to be logged on websites? Well read along here. Continuing This Series:

Welcome to the Part 2 of the series 'Cryptocurrency'. It has been late because of some errors, where all I typed was lost.

CEO's of IT companies doesn't know this because they are not a hacker. Only a true hacker can become a successful Security head officer.

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

There is something so satisfying about dipping your spoon into a perfectly smooth slice of cheesecake. There is something a bit less satisfying about it if the top of the cheesecake is cracked and cratered.

Depending on your child's age, their first smartphone may be a little too open for them, or you, to handle. With essentially a world of information—both good and bad—available at their fingertips, it can seem like a huge hurdle to instill parental controls on their device.

Whether you are sending your phone in for repairs or finally selling it to upgrade to a new flagship, you are going to need to make sure all of your personal data is removed from your device.

Welcome back, my rookie hackers! As most of you know, Mr. Robot is probably the best hacker TV show ever! This is a great show about a cyber security engineer who is being enticed to hack the very corporation he's being paid to protect. This show is so good, I began a series to demonstrate how to do the hacks he uses in the show.

Researchers at the cyber security firm Zimperium have recently uncovered a vulnerability in roughly 95% of Android devices that has the potential to allow hackers to take total control over your phone with a simple picture message (MMS). The gritty details of this exploit have not been made public yet, but hackers now know the general framework for this type of attack, so you can be certain that they'll hammer out the details in no time.

Welcome back, my tenderfoot hackers! A number of you have written me telling me how much you enjoy the Mr. Robot series on USA Network. I am also a huge fan! If you haven't seen it yet, you should. It may be the best show on TV right now.

Hi all, Pro Hackers/Crackers, Let's see how we can use batch for our own Protection instead of exploiting someone with it.

Any beer aficionado who's been to Ireland will always talk about how the Guinness there "just tastes different." But save your eye rolls, skeptics: it turns out your favorite lagerhead actually has a valid point.

Even if you've put aside your percolator and have gone the way of the pod coffeemaker, there are still dozens of ways to use your leftover coffee filters. Incredibly cheap, absorbent, and shaped with a ruffle, coffee filters are useful in the kitchen, garden, and around the house.

The internet is forever. When you put something out there, it can easily be re-shared, floating from server to server indefinitely with no way of taking it back. It's a scary thought when you consider that a young adult's grandchildren will one day have access to their drunken party pics.

There are certain foods and beverages that can actually brighten your smile or improve your dental health when you chew or sip them. Once you understand their chemical properties or textures, you can look to items you already have in your cupboards or refrigerator to help keep your teeth looking and feeling their best.
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

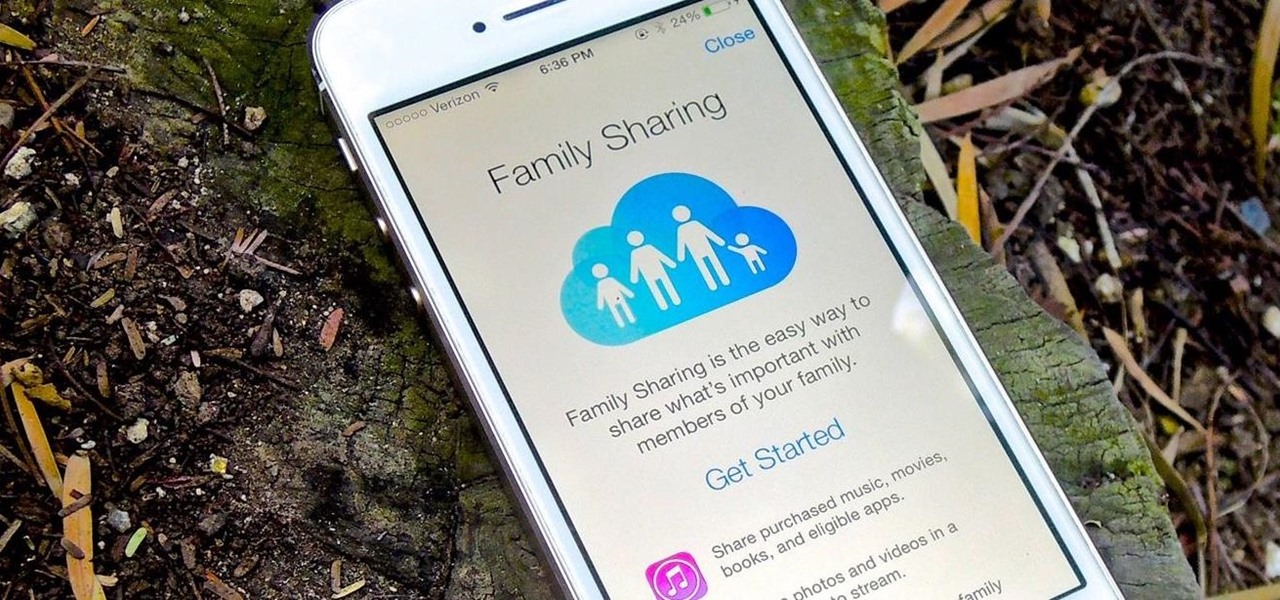
There are a ton of great new features in iOS 8, and one of the most interesting (and perplexing) ones is called "Family Sharing."

Depending on who you ask, internet connectivity should be a basic human right. With Google recently embarking on a project to provide internet capabilities to remote corners of the world using balloons and satellites while Facebook attempts to do the same with unmanned drones, the concept of free web access is steadily gaining steam.

With all of the personal data that's stored on our smartphones, it's of vital importance that we have some sort of lock screen security enabled. One of the Galaxy S5's killer features is obviously the fingerprint scanner. It makes the process of dealing with a secure lock screen a bit easier than typing in a password or PIN.

There are over 60-something Android apps cluttering my app drawer. While I'm constantly on the look out for new mods and apps to install, the default way of managing them is cumbersome and just feels unintuitive. I mean, who on Earth would wants to individually manage each app on their device?

If you're anything like me, your day doesn't start until you've sloughed away your grogginess with a scalding hot shower. That perfectly-heated water can clear stuffed sinuses, relax the muscles, and make pretty much anyone feel squeaky clean. However, a cold shower can do even more for you if you can stand the low temperatures.

Fish is delicious, and as the Harvard School of Public Health points out, incredibly good for you. There are many studies that show regularly consuming a couple of servings of fish per week can help prevent heart disease and may well reduce your chances of stroke, depression, and getting Alzheimer's. After all, there's a reason why fish is called "brain food."

Humans in general are great at keeping things about themselves private, from feelings to personality traits. While smartphones and social networks are making these secrets more open, narcissists have and always will love being out in the open with everyone's attention on them.

Fasting—or the practice of regularly abstaining from ingesting anything except water—is a pretty drastic move. I tried to fast for two days and made it to the 12-hour mark, which is when I broke down and ate a quart of ice cream.

If hearing the names of classic PC games like Commander Keen, Fallout, Master of Orion, and Wolfenstein 3D send you into a fit of nostalgia, then DosBox Turbo is the perfect app for your Android device.

Having a dust- and water-resistant phone is truly useful, but it comes with a price. In order to achieve this functionality, Samsung had to literally plug up any holes in the Galaxy S5, and this included the charging port.

Are you searching for a homemade cat repellent solution? This article will cover natural indoor and outdoor deterrents for every scenario where cats are causing trouble. The first part will cover home remedies for training cats to stay away from furniture and other restricted areas inside your house. The second part will cover outdoor repellents for keeping cats away from your garden, plants and yard. Step 1: Indoor Repellents for Training Cats