
How To: Practice motorcycle safety
Motorcycle fatalities are on the rise. Make sure you're doing all you can to protect yourself. Practice good motorcycle safety.


Motorcycle fatalities are on the rise. Make sure you're doing all you can to protect yourself. Practice good motorcycle safety.

The herpes simplex virus (HSV) can cause devastating complications for infected newborns whose mothers have genital herpes. Understanding risk and research can help you, and your baby, when the time comes.

Malware attacks on mobile phones are reaching an all-time high and it looks like companies like Samsung are doing all that they can to prevent any unwanted hackers from accessing its sensitive user data.

When you hand your unlocked iPhone to somebody so they can use the internet real quick, check out some cool photos, or do whatever, there's a possibility that they could snoop around where they don't belong. If you have some secret recipes, login credentials, intellectual property, or other sensitive information in your notes, you'll want to add some protection to them.

While you may not have loads of secret files hiding on your computer, there might be one or two items that need a little extra security, like a file of website logins or a folder of risqué photos.

In the weeks before Apple officially released iOS 8, consumers were abuzz over rumors that a new feature would password-protect your photos and text messages from prying eyes. Unfortunately, this ended up being untrue, though we did cover some alternatives to protecting your important information using some built-in features and a third-party app. Now, there's a new iOS app that can do it all.
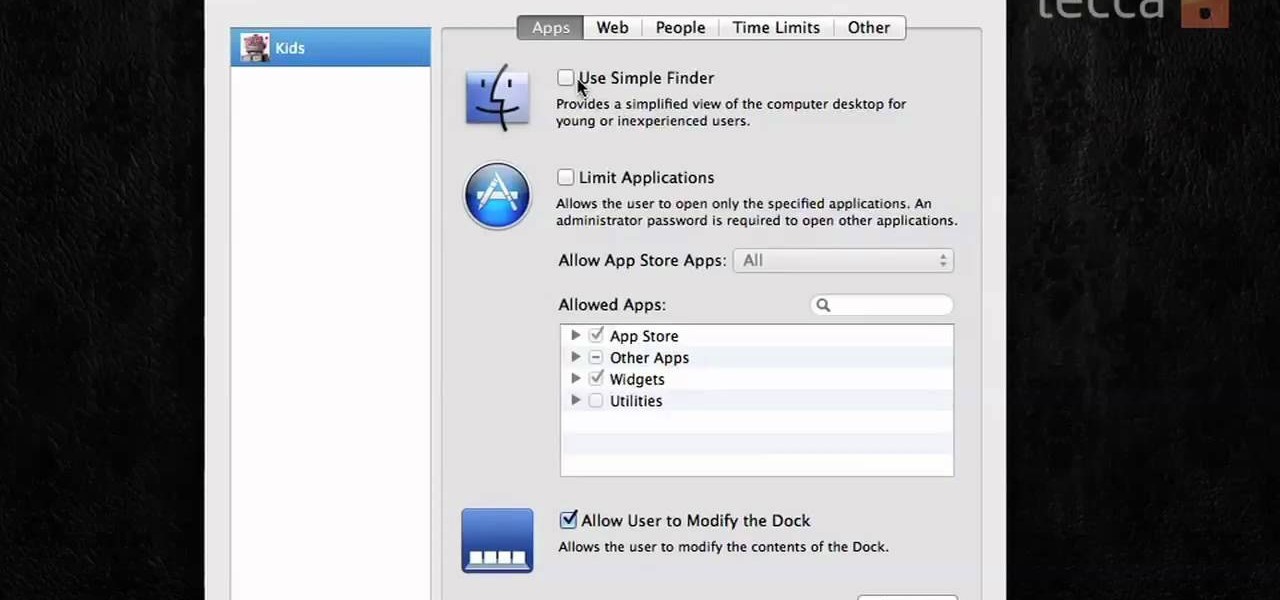
If you want to protect your children from seeing something you don't want them to see, and they happen to be using Mac OS X, take a look at this walkthrough on how to set up parental controls on their Mac computer.
To test how fast your internet speed is an intermediate level skill. Start by picking an internet speed test. You can use Google or another search engine to find one. A service that is recommended in the video is DSLreports. This site does not require you to know a lot of information about your service. To test your speed start by picking a city that is near to you. Then shut down all tabs and every application that you have running. It's important to do this on every computer on your home ne...

A shield makes a fantastic defense in boffer combat. If your character uses a shield, you're going to want to make sure to get the most out of it. This video shows you a variety of shield techniques you can use to protect yourself in boffer combat or fighter practice.

In this clip, you'll learn how to save your images as PDFs when working in Photoshop CS5. Whether you're new to Adobe's popular raster graphics editor or a seasoned designer looking to better acquaint yourself with the new features and functions of the latest iteration of the application, you're sure to benefit from this free software tutorial. For more information, watch this video guide.

You can buy heavy cream or whipping cream at the grocery store, and then mix it in an electric mixer at home. Set your mixer to medium high (and make sure you've set up a shield of plastic wrap to protect against spatter!) and mix for five minutes. Then pour and drain, and you've got homemade butter!
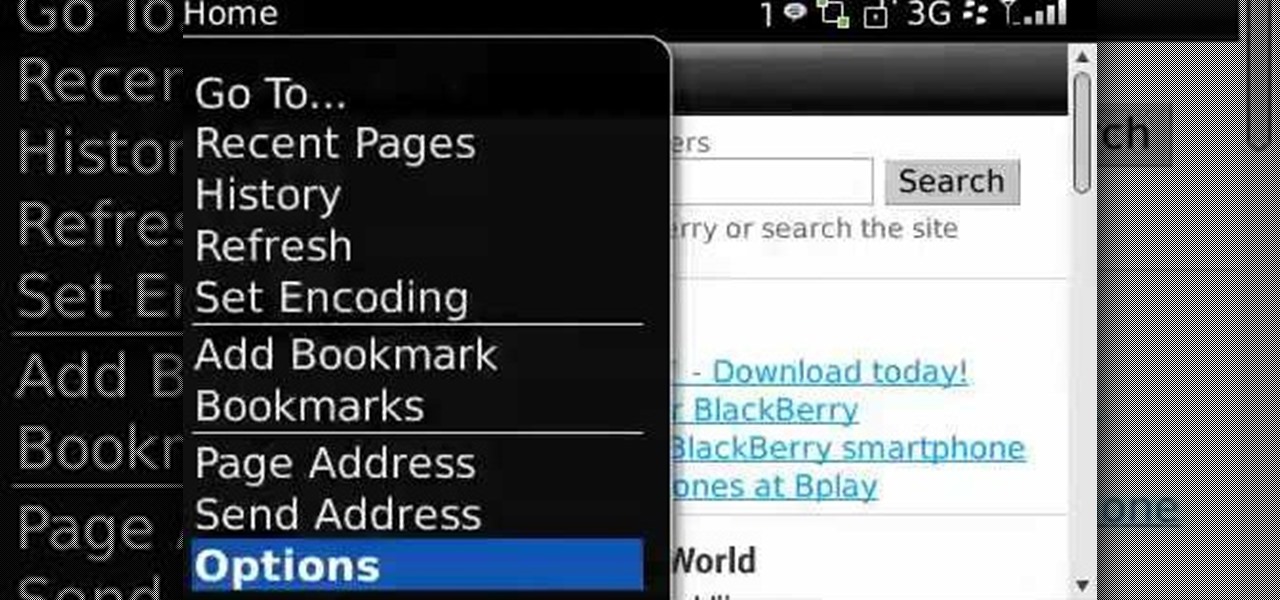
Protect yourself against would-be snoopers. Learn how to clear your temp Internet files on a BlackBerry phone. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.
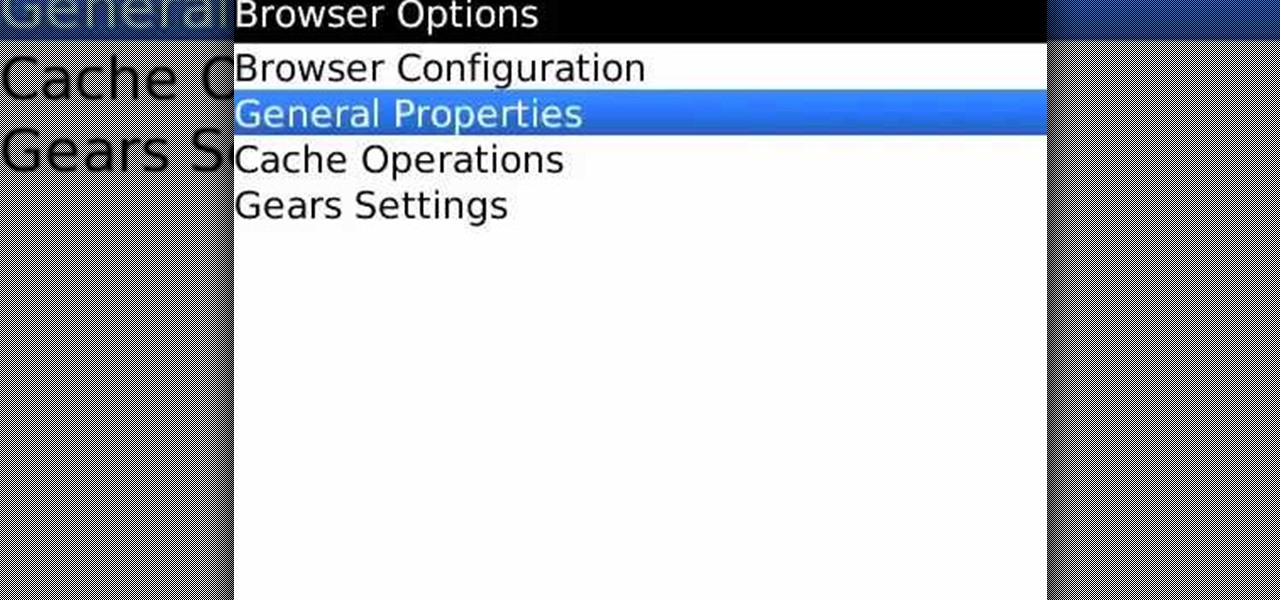
Protect your privacy by deleting the temp Internet files on your BlackBerry phone. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

Thwart would-be snoopers by protecting your Apple iPhone with a passcode. Learn how to set one up with this clip. It's easy! So easy, in fact, that this free video tutorial can present a detailed, step-by-step overview of the process in under a minute. For more information, and to get started setting up a passcode on your own iPhone, take a look!

A great way to get picture perfect shots and protect your camera in the process is to use a lens hood. When shooting on your DSLR outdoors, a lens hood will definitely come in handy. In this tutorial, learn how to get the best and most affordable lens cover for your camera and make sure you take an amazing shot every time.
Wish there were an easy way to protect one more browser cookies when sweeping out the rest? With the Selective Cookie Delete Firefox add-on it, it's easy! So easy, in fact, that this guide can present a complete overview of the extension and its various features in just over two minutes' time. Manage your cookies more effectively with this how-to.

Want to protect your privacy when surfing the Internet? Thwart would-be snoopers with this free video guide from CNET TV, which presents an overview of a number of services and good practices one can observe to project one's privacy when using the web. For specifics, and to get started surfing the Internet anonymously yourself, watch this free video guide.

Want to protect your investment and add some personal style to your cell phone, but aren't quite sure how to install that cool new skin? We've got you covered - just check out this quick video on how to install and remove an iPhone case. If only getting ready for work could be so easy!

This instructional video will show you how to remove the bumper sticker of a failed candidate, such as McCain/Palin. Now you can stop broadcasting failure without leaving a sticky residue.

Domestic and foreign kidnapping is on the rise, and when in captivity, there are a few things that will keep you alive. Nearly 8,000 citizens are kidnapped each year, so while it may not feel like a likely possibility, protect yourself. Watch this video survival training tutorial and learn how to survive a kidnapping.
Authorization allows you to copy your music store purchases to other computers and burn them to CD and protects the artists. Each computer you use to play your purchase must be authorized using your music store account. You can authorize up to 5 computers; yours is automatically authorized.
The purpose of this video is to show an e-mail security flaw using telnet that allows hackers to send e-mails using anyone's e-mail address. Thankfully, many major e-mail providers have software that blocks this. My intention is to make people aware of this flaw so that other e-mail providers can protect themselves as well.

Keeping secrets out of the wrong hands warrants desperate measures—or maybe just sensical. If you have a secret, the best way to protect it is with a code—and the best way to transfer that secret message is via an electronic telegraph system. This video will show you how to make your own homemade electronic telegraph machine, so that you can send those encrypted Morse code messages to your friends without fear of prosecution.

'Without a search warrant, I cannot let you inside'. These words will protect you from an officer manipulating his way into your home.
Did you know that malicious people can use scanners to read the Radio Frequency Identification (RFID) chips in your credit cards and identification documents and steal your personal information? Learn to protect your personal information from hackers and scammers with this simple method involving aluminum foil.

If you want to become a great robotics engineer, then you need to start out small, and this robot is a great first-time project. It's the simplest kind of robot, with only one motor and a gear box, but it moves really interesting, capable of shimmying across a rope. You can send this rope-shimmying robot tospy on your neighbors for you (when you're too lazy to do it yourself). See how it's done!

In this tutorial, we learn how to protect a Windows PC from spyware & malicious software with Dave. You can get spyware from downloading random things, so a great way to make sure you don't download these things, is to use Firefox and search your items before you download them. If you do happen to get these, use SpyBot to find and destroy the viruses you have downloaded. It's free to download, you just have to search it on Google, then download and install it. This will help save your compute...

Quinten shows us how to protect your hands in boxing using a correct hand wrap in this video. When you punch something, you put a lot of pressure on your hands and wrists so wrapping your hands before this is highly recommended. First, start on one end of the wrap and put your thumb through the loop at the end. Go over the top of the wrist first, then go over the top of the hand over the knuckles. Keep your fingers parted so the wrap doesn't become too tight at the end. Go between the knuckle...
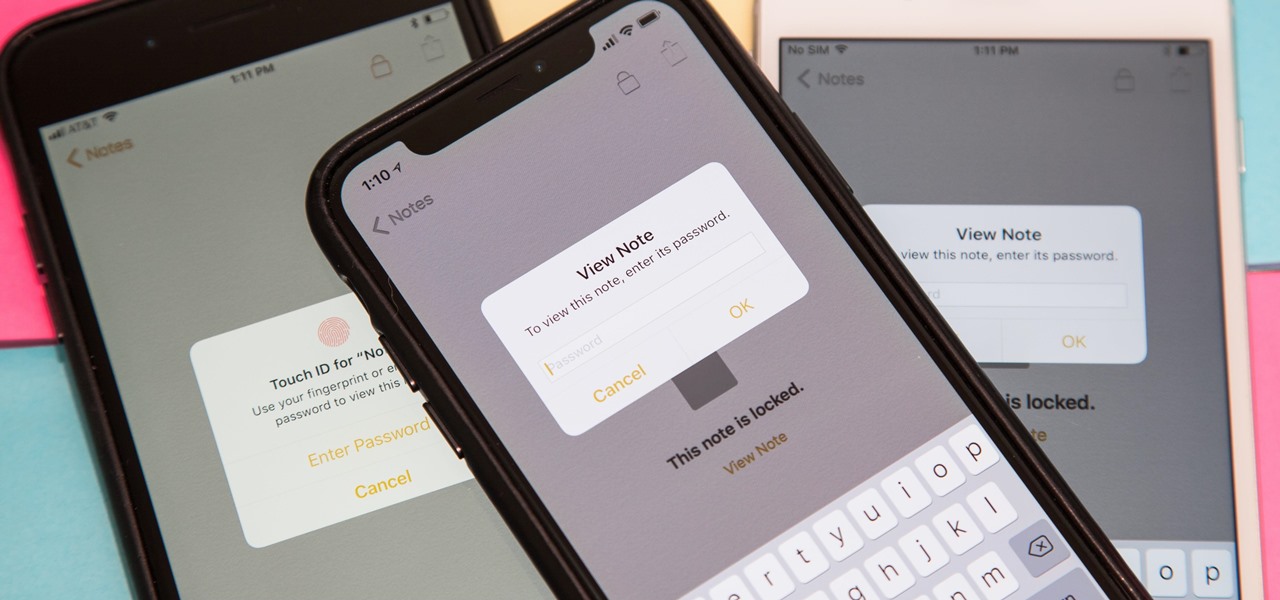
It's no secret that you can protect notes on your iPhone with a password, but one thing that most people don't know is that you can actually set unique passwords for each note instead of a blanket password for all of them. It's not obvious at all in the Notes app, but it's easy to do once you've got the hang of it.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.

Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.

The Fish Contamination Education Collaborative (FCEC) has made this video to reach the public about fish preparation safety, to make su. It's important to prepare fish in a certain way, because some species of fish have contaminants that pose health risks. Those contaminants are stored in the fatty portion of the fish, so by cleaning and cooking the fish in a certain way, you can reduce your exposure to those toxins.

Kipkay's ingenuity is enough to amaze us all, especially all of you indie filmmakers. These five tips for aspiring filmmakers will help you keep your sanity and avoid frustrating times. Have you ever got stuck in the rain while shooting? Have your recorder tapes ever gotten disorganized? Is your camera's display getting scratched up more than you want? Kipkay answers all of these questions with his five ingenious video tips.

New techniques may improve a swimming pool workout from Masters coach Nancy Kirkpatrick Reno. Before sticking a toe in the water, consider this advice: * Swim in a pool that's at least 20 to 25 yards long; those pools can usually be found at high schools and some gyms. A 50-meter Olympic-size pool is best, but not everyone has access to that. "If you're going to become a lap swimmer," Kirkpatrick-Reno says, "you can't go any shorter or you'll be constantly turning." An outdoor pool is prefera...

This week, Etsy How-Tuesday presents Kari aka ikyoto and Stella aka lookcloselypress of The {NewNew} York Team. Today we're going to learn how to screenprint our own snowflake gift wrap for the holidays. Kari and Stella remind us that recycling paper bags is a great source for materials for this kind of project.

They are after you from all over the globe. Looking for ways to exploit you. Ways to hurt you. Not political terrorists, but rather "info terrorists." Each month thousands of websites get hacked into and have hidden links inserted into the pages by people wanting their spam sites to rank highly in the search engines.

Got some valuables that need to be protected in your Minecraft world? Watch this video to learn how to build a seriously secure, heavy duty, combination lock. This video will show you what materials to use to make this combination lock.

Worried about the MAC Defender that's been going around? Don't let your Mac get infected, watch this informative video to learn how to keep it virus free. If you are concerned with malware attacking your OS X Mac, you should watch this video.

Pawnshops aren't exactly the most sacred places, so is it any surprise that one of the Street Crime missions in L.A. Noire is Pawnshop Holdup? Help protect the stuff people had to hawk when they were in a bind by watching this walkthrough video.